
How To: Get a career in affiliate marketing
Big business is on the web these days and you don't have to build a shopping website or blog to get involved.


Big business is on the web these days and you don't have to build a shopping website or blog to get involved.

Have an opinion and want the whole world to know it? You're not alone! There are many online outlets for you to type up your review, whether it be for a restaurant, play, movie, book or anything else you have recently experienced. Check out this video for tips on how and where to post your exciting review.

You've boxed up and shipped all your other possessions for the big move and all you're left with is the little issue of how your getting your car there. There are companies out there that will ship your car to you, just make sure your car is prepped for the journey.

Wedding insurance, vacation packages, travel discounts – the American Automobile Association offers its members more than free towing.
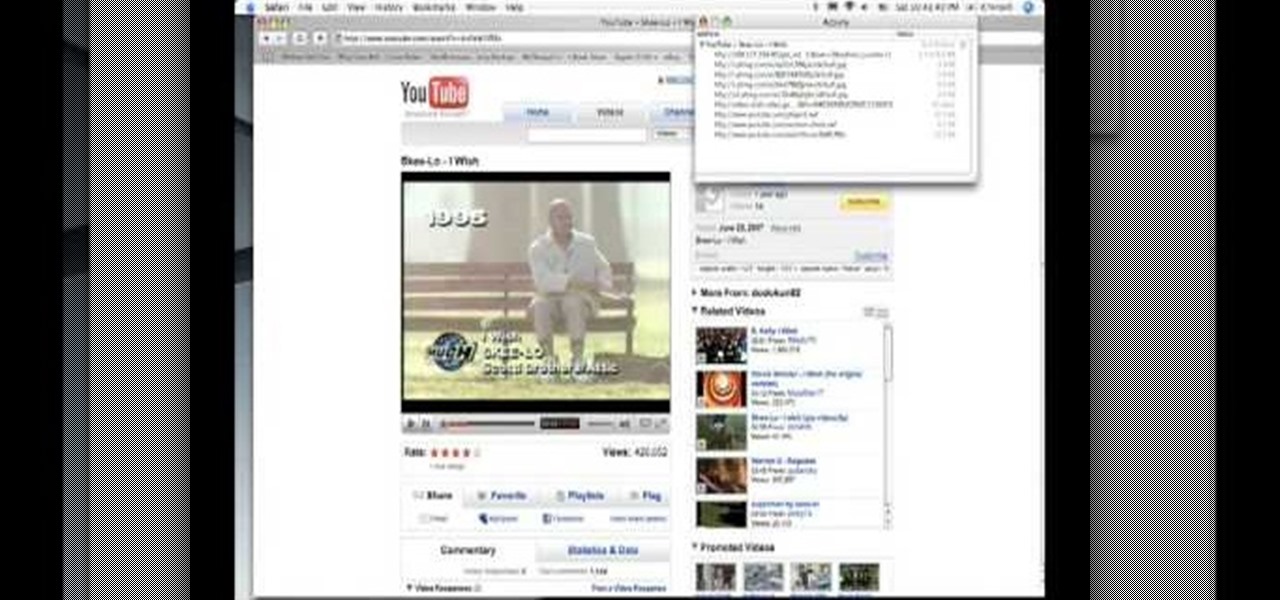
A quick video showing how to get free music online. May take a couple minutes per song. To prove quality I used the song i download in the video as background music. "I Wish" by Skee-Lo
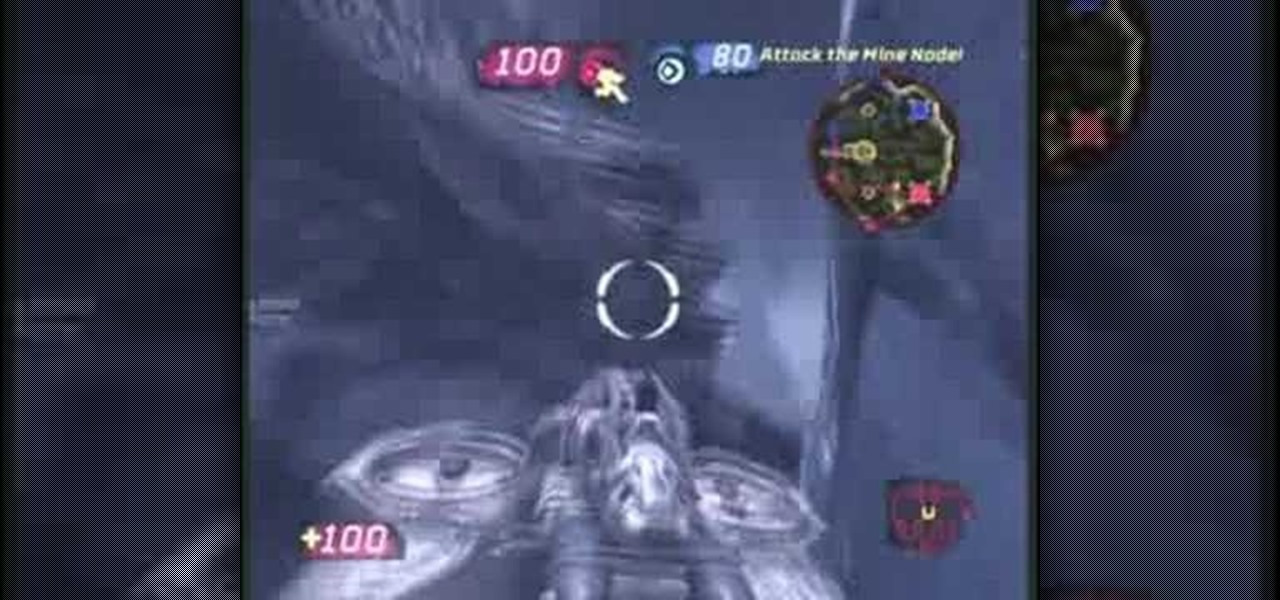
Glitches are everywhere in the video game world, and you can call them what you want... glitches, cheats, cheat codes, hints, secrets or tips. In order to find a glitch, you have to keep your eyes open or follow a recommendation from a gaming friend. Either way, to catch a secret glitch, you need to be ready; the cheats for the taking, whether a weapon or secret passageway, so take it, before it gets patched.

UPDATE: Entries are now closed. Thank you for participating! Next Reality is where we help you literally 'see' into the future of augmented reality, and to help with that mission we're offering three free pairs of Snap Spectacles 3 to three lucky readers who sign up for the Next Reality daily AR email newsletter.
Using a virtual private network (VPN) is one of the safest ways to ensure your identity and data remain secure. Choosing one from the hundreds of services that now exist is another story. How do you tell which VPN truly provides the best protection at a great price?

The life of a busy entrepreneur isn't easy. In addition to coming up with original business ideas and marketing strategies, you also need to be continually thinking about investors, overhead, the competition, and expanding your customer base — often with a limited budget.

It is well documented that what you say and do online is tracked. Yes, private organizations do their best to protect your data from hackers, but those protections don't extend to themselves, advertisers, and law enforcement.

Every single photo you take carries with it a considerable amount of seemingly "invisible" yet important information known as metadata. Although metadata is usually helpful to sort your photographs by location and date, that same information could potentially be used against you, especially if the pictures are taken during a precarious situation.
While sheltering at home has its downsides, one lesson we're all learning is how interconnected the world is. In that sense, it's a wonderful time to satisfy your curiosity about other cultures. There are many means of education like exploring music, cuisine, and fashion, but few things are as effective and beneficial as learning the native language.

Apple Card has generated quite the buzz since its March 2019 announcement. The iPhone maker's new credit card pairs with Apple Wallet on your device, is simple to sign up for, includes enhanced security over other cards, has zero fees, and provides daily rewards right to your Apple Cash account. And as good as that sounds, the fine print can complicate things real quick.

While modern browsers are robust and provide a lot of functionality, they can be unlocked to do some pretty spectacular things with browser extensions. For hackers and OSINT researchers, these tools can be used to defeat online tracking, log in to SSH devices, and search the internet for clues during an investigation. These are a list of my top ten favorite browser extensions for hackers — and how to use them.

In a legal brief entered on Monday, Florida-based startup Magic Leap has filed suit against the founder of Nreal, a former employee of Magic Leap, claiming that the company's Nreal Light smartglasses were built using Magic Leap's intellectual property.

Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. It can include the carrier, the owner's name and address, and even connected online accounts.

Shopping wasn't always this easy. Now, in a matter of minutes, you can order your groceries for the week, send your cracked phone in for repairs, get your holiday shopping done, and have everything delivered to your front door in just a few days — without ever having to leave your home. Online shopping is convenient, comfortable, and a blessing ... right? Well, it can also be a headache.

Although it's impossible (at least for now) to travel back in time to see the Big Bang, The New York Times has provided its readers the closest simulation of the experience via its latest augmented reality feature.

There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

Data breaches are all too common now, and the latest one you need to know about involves Timehop, a mobile app that makes it easy to reminisce over old photos. The breach, which took place on July 4, was revealed on Sunday, July 8. At the time, Timehop disclosed that 21 million users had been affected by the breach, but it now appears that all users were impacted in some way.

Even in augmented reality, Wile E. Coyote still can't catch the Road Runner. The latest AR experiment from developer Abhishek Singh brings the classic Looney Tunes duo into the real world.

Mere weeks after rumors surfaced that Apple may be working on a headset capable of VR and augmented reality, it appears that Samsung is taking the same approach, but with an assist from Microsoft.
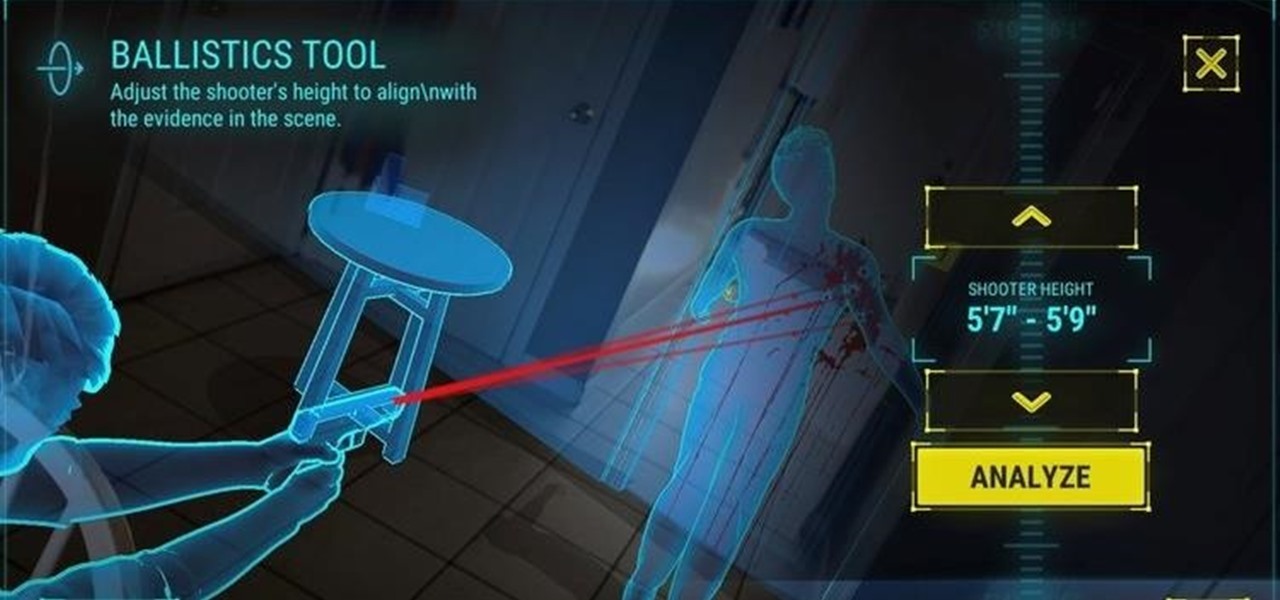
The crime procedural show is the perhaps the most direct path to the average TV viewer's heart. Could the same hold true for augmented reality games?

Augmented reality device maker Vuzix has filed a defamation lawsuit asking for $80 million in punitive damages, money damages, and interest against a short seller who has publicly claimed that the Amazon Alexa functionality of the company's Blade smartglasses is fraudulent.

The legal travails of Magic Leap appear to have no end in sight, as a lawsuit filed by an ex-employee further threatens to dampen the startup's 2018 launch.

Instagram updated its iOS and Android apps recently with an "Activity Status" indicator. This status allows your friends to see when you are currently active and when you were last active on Instagram. The problem is, Instagram was pretty quiet about this update, so many of you have it enabled without realizing it. Fortunately, it's simple to turn off.
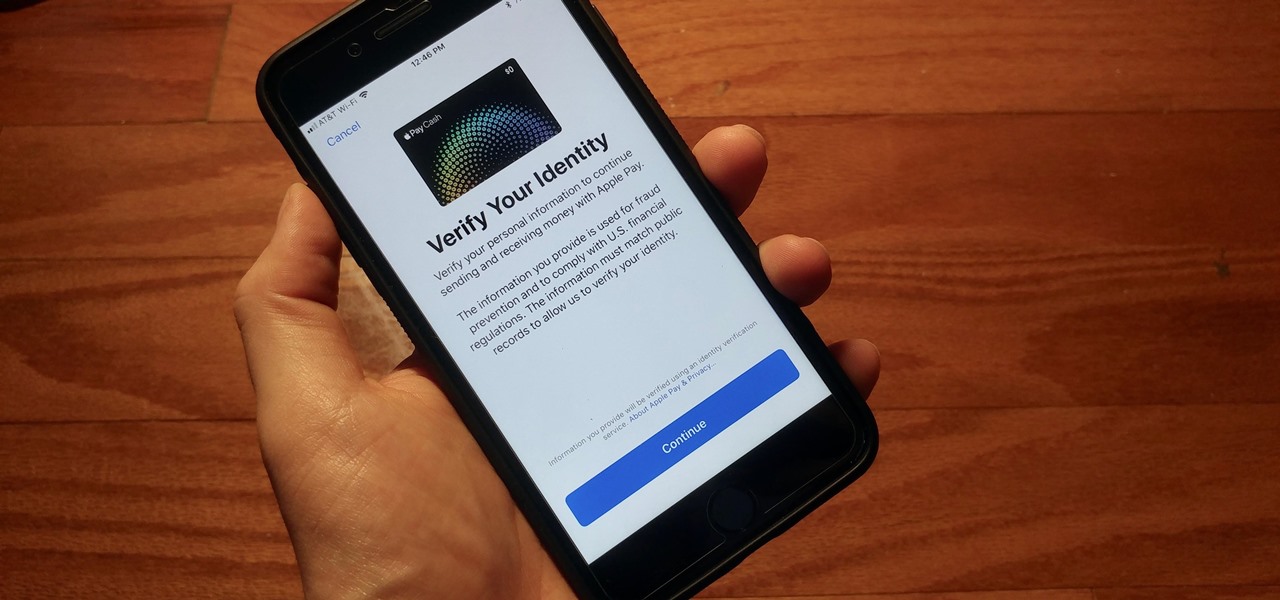
With iOS 11.2's introduction of Apple Pay Cash, you can send and receive money to others directly through iMessage, using the convenience and security Apple Pay is known for. However, if you want to make sure your efforts go uninterrupted, you'll want to make sure you verify your identity with Apple.
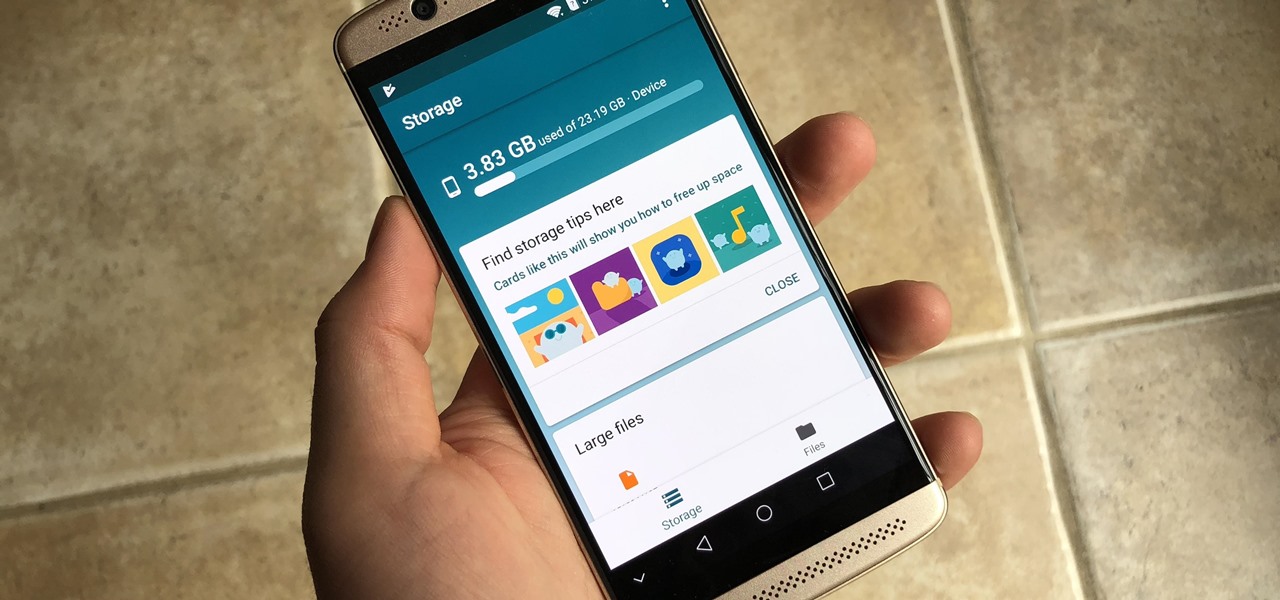
There may be many third-party file managers for Android to choose from, but until now, Google offered no proprietary option. Enter 'Files Go,' which, while initially anticipated for December, is now available for you to try.
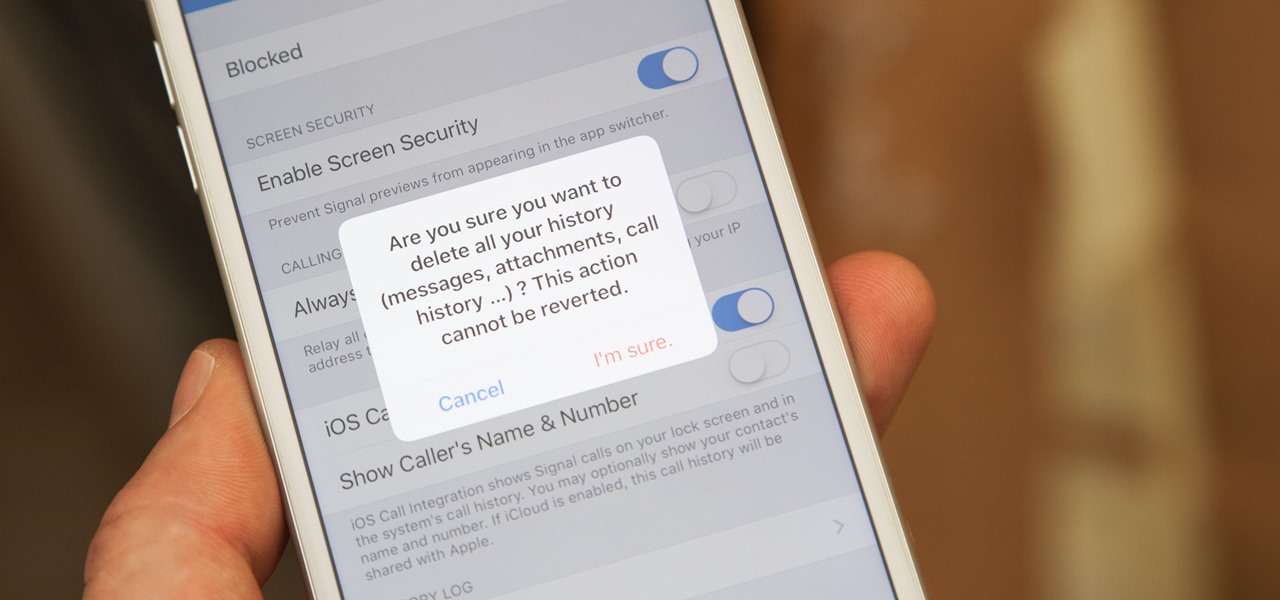
If thieves, hackers, law enforcement, or other would-be enemies should ever gain entry to your smartphone, they could also access conversations you've had in Signal Private Messenger. To better secure your encrypted communications, you can password-protect the whole app and its contents — but only on Android. Even then, it's necessary to perform data deletion on a periodic basis, if not immediately.

Smartglass maker ThirdEye Gen, Inc. has introduced an augmented reality solution for enterprises that includes their X1 Smartglass and a suite of software applications that enable completely hands-free computing.
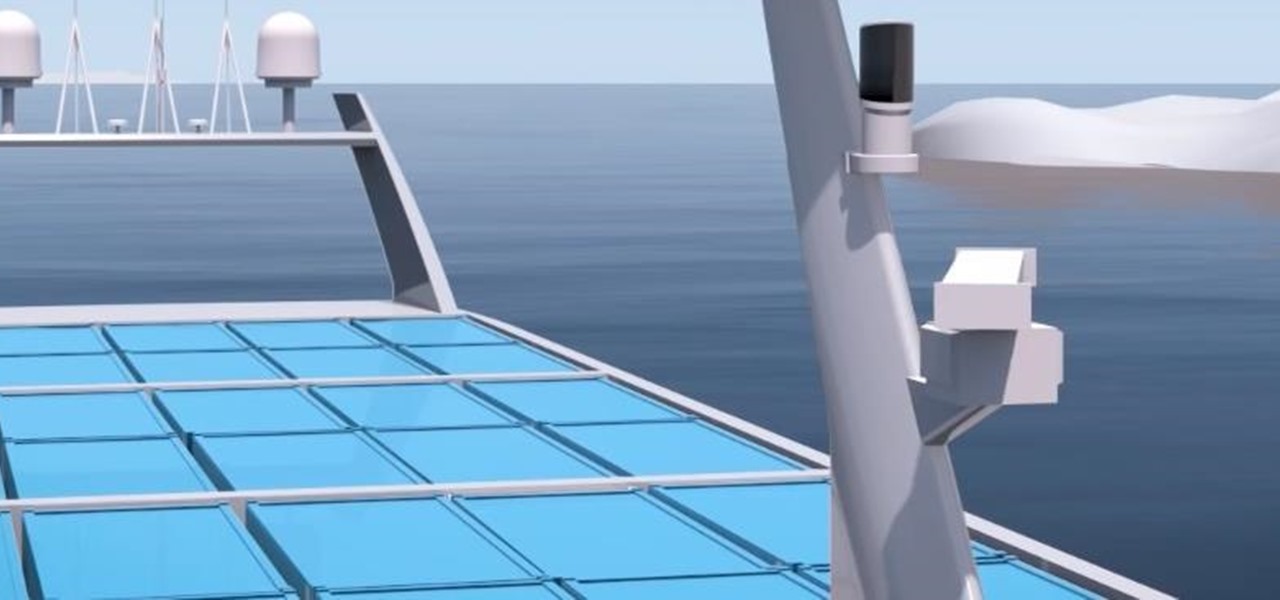
A Norwegian carrier's launch of a pilotless container ship next year could lead the way to a new era in sea transportation and shipping if successful.

Full disclosure — I have almost zero Street Fighter experience. The first time I played the game was at Barcade, way back in ... 2017. Yes, to the shame of gamers everywhere, this reviewer is a Street Fighter noob.
Getting your green card can be an extraordinarily complicated and difficult task. Often times it seems so daunting that it's hard to know where to begin. Thankfully, Facebook Messenger introduced "Visabot" last year, a chatbot in the app that helps with all things immigration. Now including applying for your green card.

Driverless transportation is definitely coming closer to the mainstream, but most companies developing the technology have said it will be another couple of years before we see autonomous vehicles being used as an alternative for typical transportation.

Uber CEO and co-founder Travis Kalanick is taking an indefinite leave of absence from the company, as Uber's recent upheaval has far overshadowed any developments in its driverless initiative during the past few days.

A Norwegian shipping company says it will launch an unmanned container ship within four years, as the shipping industry begins to apply driverless technology to commercial sea transportation.

Replacing your iPhone fingerprint sensor has been one of Apple's most cruel tortures. It's a slow and painful process made worse last year when Error 53 messages started appearing on the phones of users who had tried to repair their sensors outside of Apple. The error rendered the phones essentially useless. Since then, Apple has provided fixes but is now finally making it much easier to replace your iPhone fingerprint sensor with the releasing of "Horizon Machines" to official repair locations.

Despite a round of updates to Pokémon GO that patched and eliminated location spoofing, the game still has a difficult time dealing with the most hardcore cheaters. Like weeds on a grassy lawn, third-party bot makers still remain the biggest thorn in Niantic's side and continue to thrive despite the developer's best efforts to root them out. While the latest updates have blocked users from running modded versions of the game, like Pokemon GO++, that feature built-in joysticks to move your pla...

Apple staff will be put through their paces now that the company's "Automated System" for driverless cars is in motion.

Some Montana inhabitants have been making impassioned pleas to legalize raw milk this week. The debate took place during a hearing on House Bill 325, which was held by the Senate Agriculture, Livestock, and Irrigation Committee on Tuesday, March 21.