Augmented reality headset maker Meta Company unveiled Meta Viewer, its first software application, during its keynote at the Augmented World Expo in Santa Clara on Wednesday.

After backdooring a MacBook not protected by FileVault or using a fake PDF to gain remote access, an attacker may wish to upgrade their Netcat shell to something more fully featured. While a root shell allows attackers to remotely modify most files on the MacBook, Empire features some useful post-exploitation modules which make hacking Macs very easy.

Developed by Open Whisper Systems, Signal is a free, open-source encrypted communications app for both mobile and desktop devices that allows users to make voice calls, send instant messages, and even make video calls securely. However, a vulnerability was recently discovered for the desktop version that can be turned into a USB Rubber Ducky payload to steal signal messages with a single click.
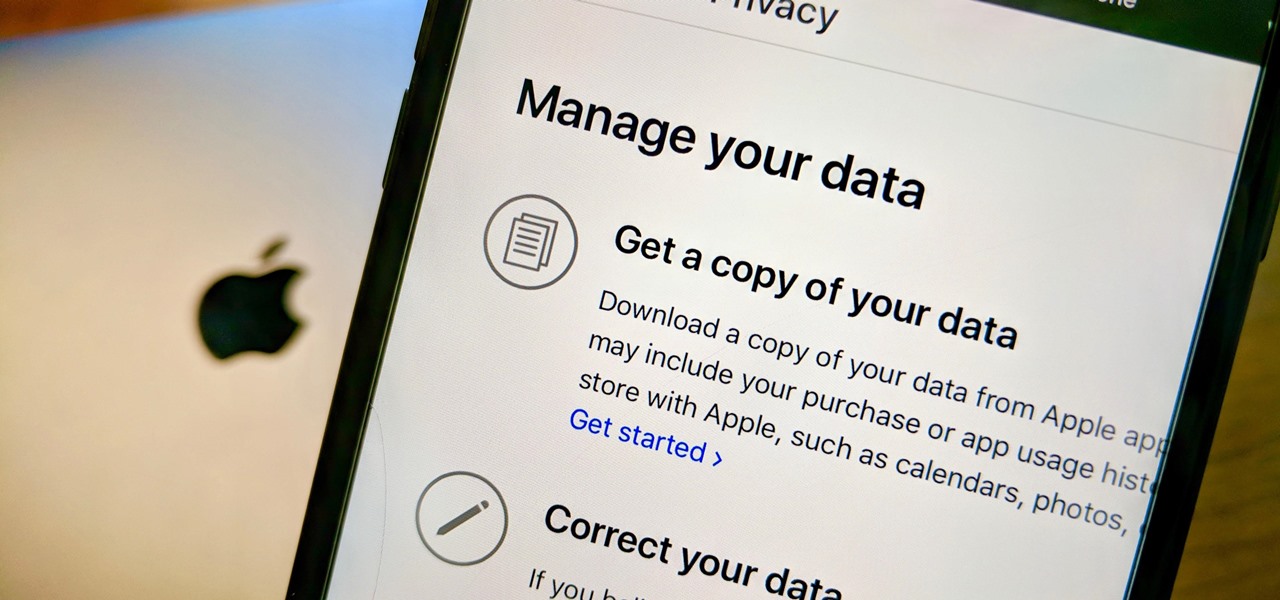
Personal data is a hot topic right now, and for good reason. Never before has the public been so on edge about how companies use their information. Services like Facebook and Google now allow you to download all of the data each has on file. Soon, you'll be able to see exactly the same for Apple as well.

Ever notice how some augmented reality apps can pin specific 3D objects on the ground? Many AR games and apps can accurately plant various 3D characters and objects on the ground in such a way that, when we look down upon them, the objects appear to be entirely pinned to the ground in the real world. If we move our smartphone around and come back to those spots, they're still there.
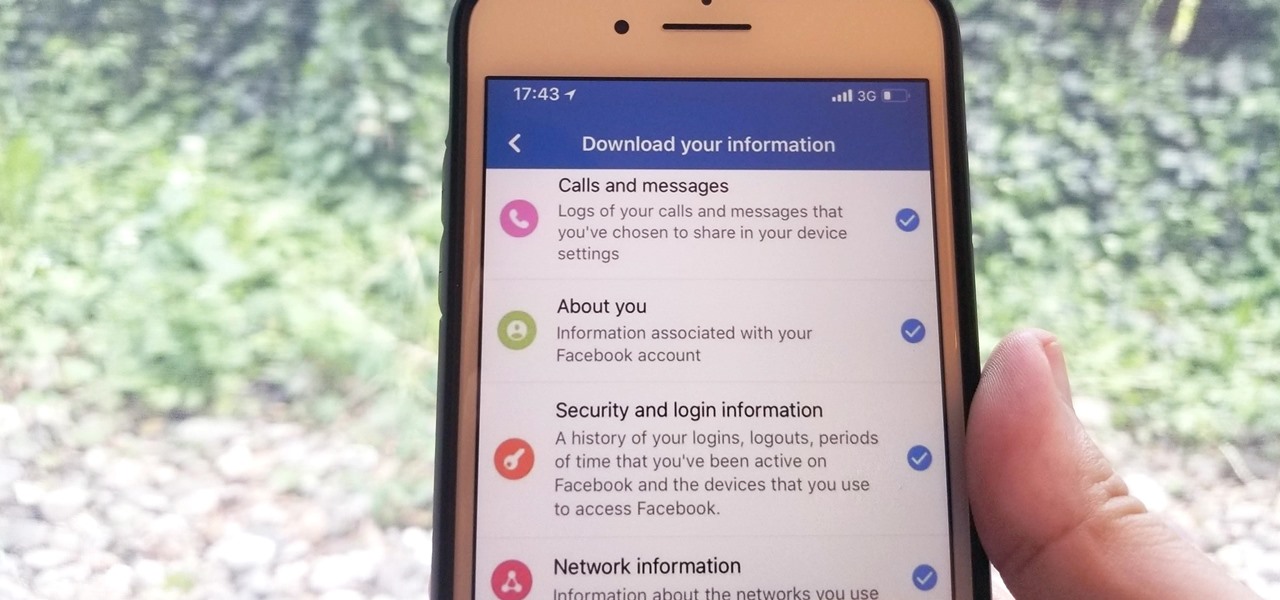
We've been able to download our Facebook data onto our computers for a while now, but now you can do so right from the comfort of your iPhone or Android phone. With it, you'll be able to integrate your data into other apps that support it or even just download it before you deactivate your account.

The conversation of which operating system is most secure, macOS vs. Windows, is an ongoing debate. Most will say macOS is more secure, but I'd like to weigh in by showing how to backdoor a MacBook in less than two minutes and maintain a persistent shell using tools already built into macOS.

For most carriers, "unlimited" data plans aren't really unlimited, and they still cost more than data limited plans. So while subscribing to music streaming services and storing your own music library in the cloud may be more convenient, it may eat your data up like candy. To keep that from happening, try downloading tracks from Apple Music for offline playback.

App updates bring new functionality, but they can also break old features or introduce changes no one wants. Unfortunately, if you're holding onto an older app version because you don't want to accept the update, it becomes a lot harder to keep the rest of your apps updated.

Magic Leap's recent flurry of patent applications prompted us to look around for any trademark movements from the company, and it turns out that the Florida-based company has been quite busy.

With an ordinary birthday card, we can introduce a physical device which contains malicious files into someone's home and deceive them into inserting the device into a computer.

Update: Monday, 11 p.m. ET: In a report from Bloomberg, eMagin CEO Jeffrey Lucas has contradicted what appeared to be investor information found in SEC filings that surfaced on Monday. Although Apple is listed among several other investors in the company in filing, Lucas told Bloomberg that Apple is not, in fact, an investor in the company. Offering further clarification, Lucas told the news site that eMagin "listed those companies in the filing because it had discussions with them at industr...

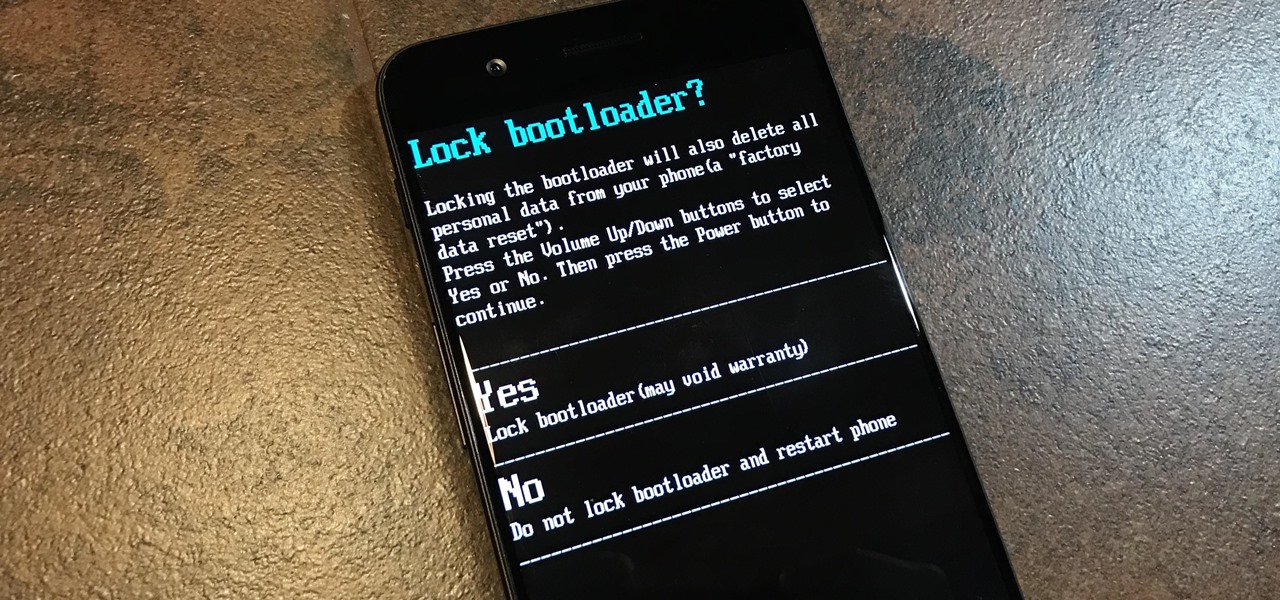
To please those of us who love to mod and root our Androids, OnePlus has made both the OnePlus 5 and 5T relatively easy to customize — so much so that the 5T topped our list for the best phones for rooting. Unfortunately, unlocking the bootloader and using root to modify the firmware on your OnePlus 5 or 5T makes it hard to update to a new firmware such as Oreo when compared to stock.

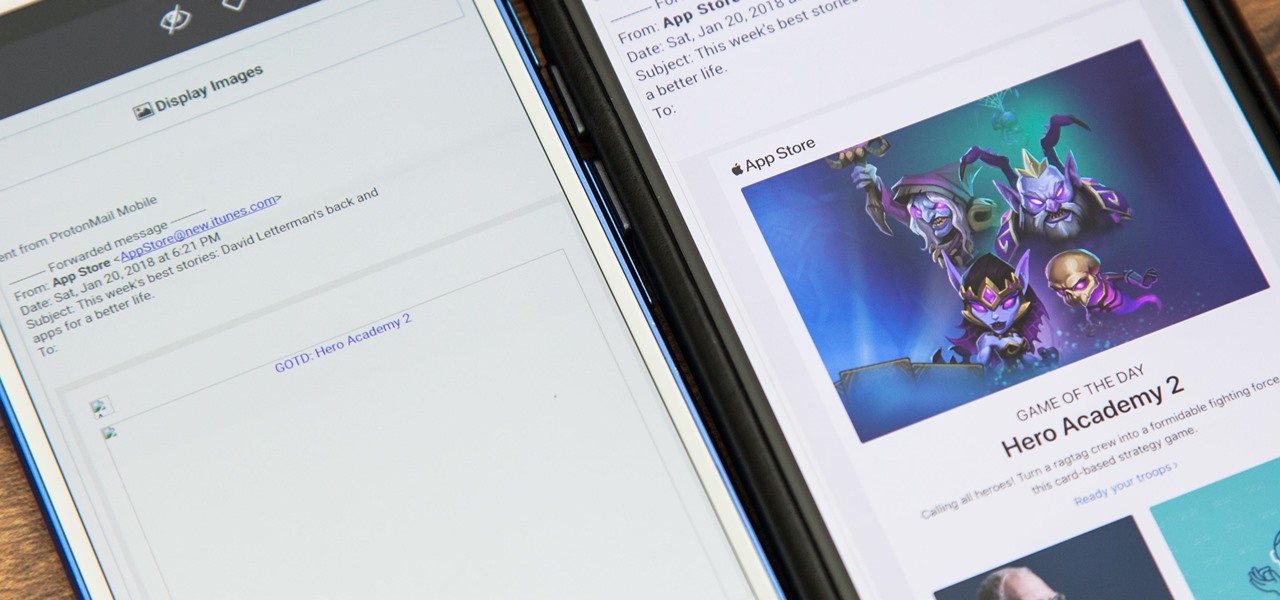
By default, images embedded using external links will not automatically load in any emails that you get with ProtonMail. This is a security mechanism that can prevent malicious code from being executed on your system, but it can also be fairly annoying to have to manually load images in email after email.

Whether you're a veteran augmented reality developer looking for a quick access point to add a new platform to your arsenal or just getting started with your first AR head-mounted display, get ready to start developing for the Meta 2.

PowerShell Empire is an amazing framework that is widely used by penetration testers for exploiting Microsoft Windows hosts. In our previous guide, we discussed why and when it's important to use, as well as some general info on listeners, stagers, agents, and modules. Now, we will actually explore setting up listeners and generating a stager.

When it comes to streaming services, Google Play Music is one of the best options for both Android and iOS. Perhaps its single greatest feature is the fact that you can upload as many as 50,000 of your own songs to Google's servers, then stream your library to any device without ever paying a dime.

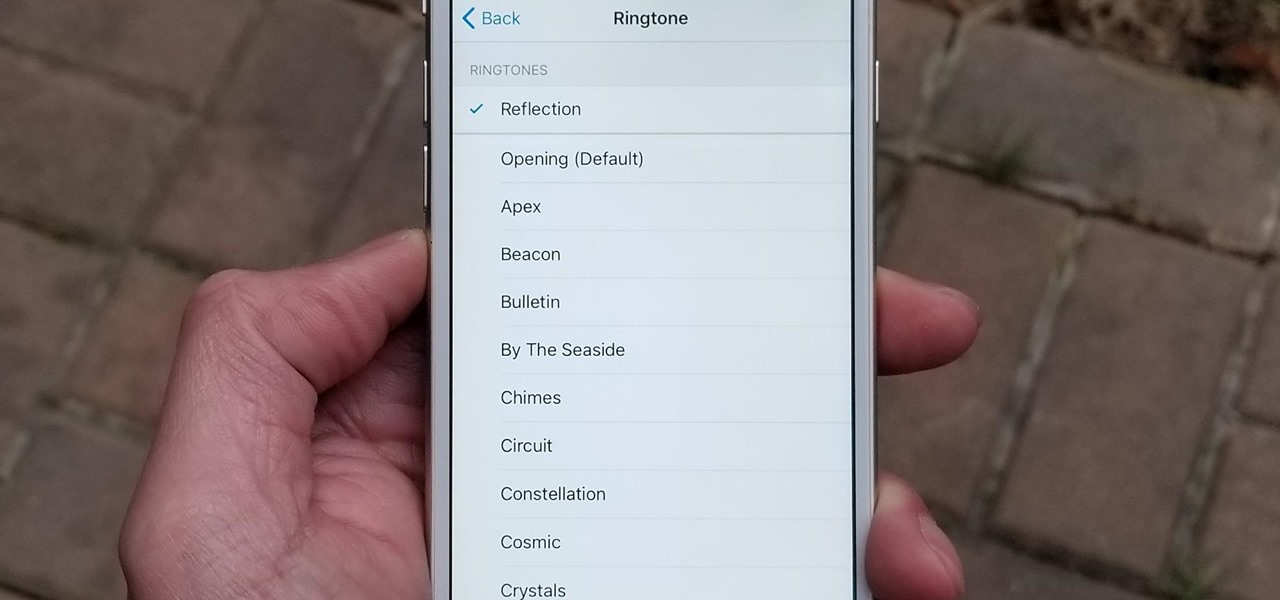
The new iPhone X sets itself apart from its predecessors not only as the first Apple smartphone to use an AMOLED screen, but also as the first iPhone to cost over $1,000. True to form as an exclusive device, Apple's latest flagship also features a distinct ringtone. With a little tinkering, however, you can make the new "Reflection" ringtone your very own, regardless of which iPhone you may have.

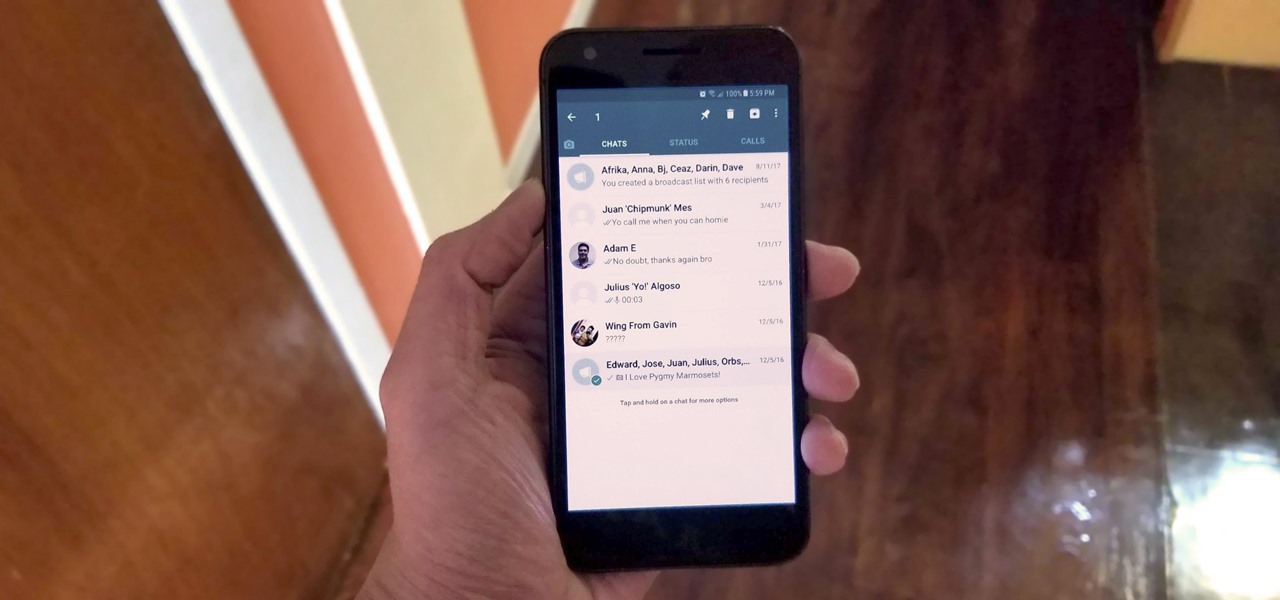
One of the downsides of living in an unprecedented age of connectivity is the near-constant bombardment of information. WhatsApp, the go-to messaging app for people the world over, is just as susceptible to buildup of useless media files, thanks to awesome features that allow us to communicate in multiple ways, such as broadcasting to friends and family. Luckily, the app makes it easy to remove old and unwanted data from your iPhone or Android.

When hacking into a network during a penetration test, it can sometimes be useful to create your own wireless AP simply by plugging a Pi into an available Ethernet port. With this setup, you have your own backdoor wireless connection to the network in a matter of seconds. Creating an AP is also helpful while traveling, or needing to share a connection with a group of people.

Virtual private networks, or VPNs, are popular for helping you stay anonymous online by changing your IP address, encrypting traffic, and hiding your location. However, common IoT devices, media players, and smart TVs are hard to connect to a VPN, but we have a solution: Turn a Raspberry Pi into a router running through PIA VPN, which will ensure every connected device gets the VPN treatment.

So you spent all day customizing your phone. You tinkered with all the settings, searched the web high and low for the perfect wallpaper, and found an ideal icon pack to complement the color scheme. You go to sleep, proud of the work you accomplished when the unspeakable happens — your phone freezes and tech support is telling you to do a factory reset to fix the problem.

In my previous article, we learned how to generate a vulnerable virtual machine using SecGen to safely and legally practice hacking. In this tutorial, we will put it all together, and learn how to actually hack our practice VM. This will provide some insight into the methodology behind an actual attack and demonstrate the proper way to practice on a VM.

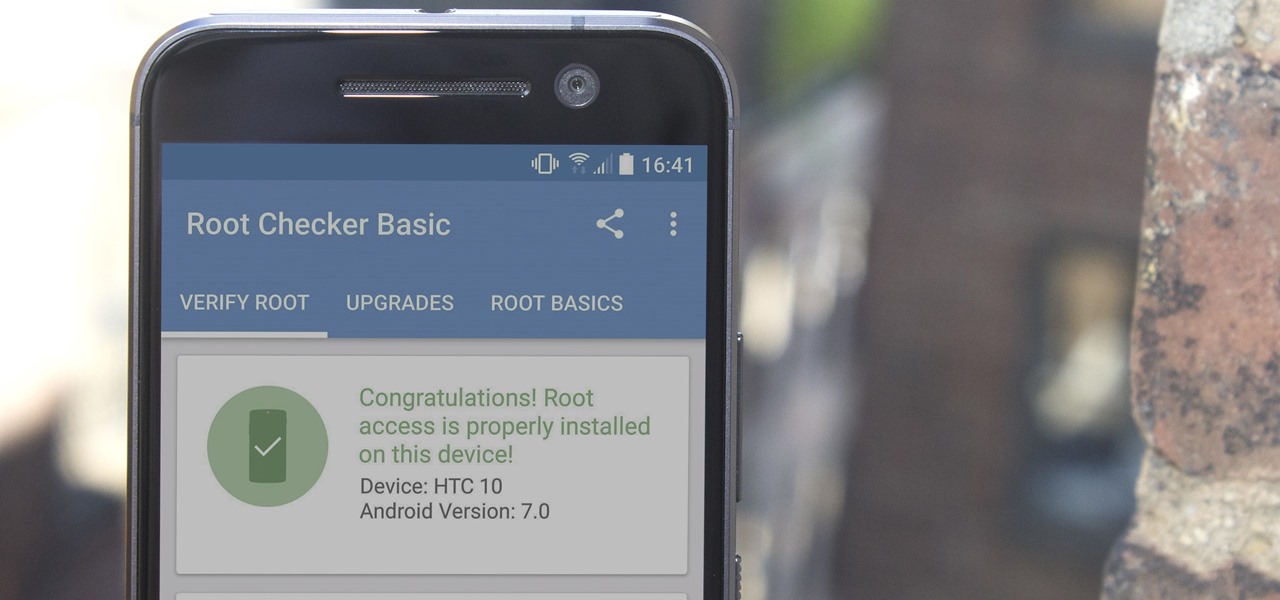
There are many great reasons to root your phone, but if you're not experienced with tools like ADB and Fastboot, it can seem like a daunting task. Fret not, because if you want to root your HTC 10, we're here to walk you through the process.

The Raspberry Pi loads an operating system from whatever SD card you insert, allowing you to keep different operating systems on separate SD cards depending on which OS you wish to run. A tool called BerryBoot cuts down on the number of SD cards needed by providing the ability to boot multiple operating systems from a single SD card, similar to Boot Camp for Mac computers.

The USB Rubber Ducky comes with two software components, the payload script to be deployed and the firmware which controls how the Ducky behaves and what kind of device it pretends to be. This firmware can be reflashed to allow for custom Ducky behaviors, such as mounting USB mass storage to copy files from any system the Duck is plugged into.

The popular RPG Death Road to Canada has finally arrived for the iPhone and iPad, and its impact is immediate. It's fast becoming a top contender for mobile video game of 2017, and it's very easy to see why. The game blends decision making and good old zombie bashing to create a refreshingly unique experience. Add to that the motley cast of survivors that you can recruit, plus the secrets waiting to be discovered, and this game is sure to suck up countless hours of your time.

The '90s were a great decade to be alive. Before the internet became a high-availability service, we were untethered from the bombardment of media present in today's culture. Children ran through the streets with levels of physical exertion beyond what's required to capture fictional creatures found in Pokémon GO. However, there were some video game consoles that kept kids indoors, such as the Game Boy, SNES, and more importantly—the first ever PlayStation.

It's been little over a month since the official release of LG's latest flagship phone, the LG V20. Despite a few minor hiccups, the V20 has been attracting attention from all over for being an amazing phone. But like with most Android phones, there's no better feeling than rooting and taking complete ownership of it.

We're nearly done getting our Mac set up for hacking. If you haven't checked out previous tutorials, I'd recommend you do so first before diving right into this one.

There were some new hurdles to clear, and then there were a few more, but legendary root developer Chainfire has created a fully-functional root method for Google's Pixel and Pixel XL flagships. Like past devices, this method relies on the SuperSU ZIP, but now, there's an additional file that needs to be flashed in order to bypass issues with Android Verified Boot (AVB).

With the release of the Mirai source code, botnets are back in a big way. In the early days of botnets, zombies (infected hosts) would report to IRC (Internet Relay Chat) channels for CNC (command and control) instructions. Modern botnets have evolved, but they continue to use the same concepts as their predecessors.

The international, Exynos-powered Galaxy S7 and S7 edge have had a working root method ever since a few days after release. But the North American variants—those using Qualcomm's Snapdragon 820 processor—have locked bootloaders, and have proven to be almost unrootable up until now.

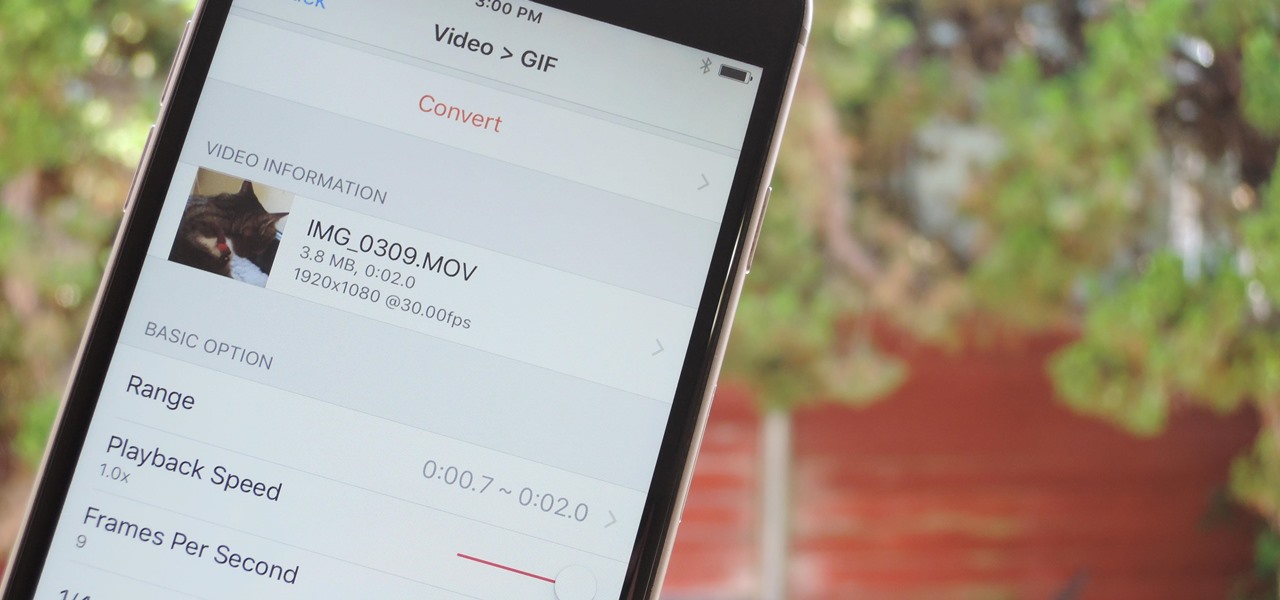
The internet has officially been taken over by GIFs—they're everybody's favorite method of communication these days, and nary a meme would exist without them. But even with the abundance of GIF-sharing websites, and even GIF keyboards, we're still a bit lacking in regard to creating GIFs on a mobile device.

Greetings fellow students! I'm currently reading a book called "Violent Python: A Cookbook for Hackers, Forensic Analysts, Penetration Testers and Security Engineers"

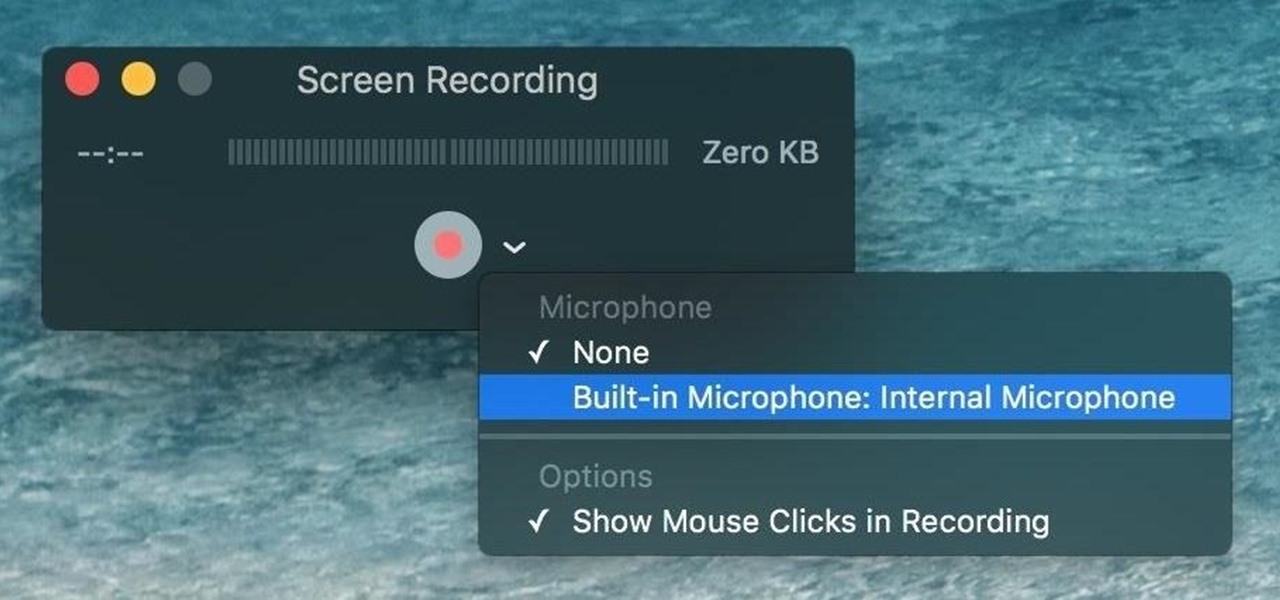
When a friend asks me what screen recording software is best to use, I always say the same thing—you don't need any! Even though it's been around since 2009, many Mac owners do not realize that they have a powerful screen recording software built right into OS X.

Since Ive started to learn about nmap and metasploit and other tools I was learning well but I had one problem,

While attempting to hack a web app, there may come a point where the attacker may have to escape the default directory in order to access unauthorized files. This is known as a directory traversal attack. Much as the name implies, this attack involved traversing the servers directories. But in order to move to an unauthorized directory, we need to know where those directories are. Today we'll be building a tool to brute force these directory locations based on HTTP response codes. Before we g...

Smartphones have become such a big part of our lives these days that they're now closely associated with our personal identities. No longer is it Ford versus Chevy, rock versus rap, or PC versus Mac—now, you're either an Android person or an iOS person.

In this how-to we will be sending an email with an image we get from a php script after running some fishy code. What you'll need