There's always an iPhone in our list of top phones for privacy and security, due in large part to advanced security measures like Face ID, consistent iOS updates, and easy ways to prevent unwanted access and excessive data sharing. However, some of those options actually do the opposite and hinder security. It all depends on how you use your iPhone, but you should at least know everything available.

Recycling your garbage is noble and, in many places, mandatory. But it also can be very confusing. This guide will clear up the rules.

Taco Bell's in the news for umpteenth time, and today the controversy is over their infamous beef taco meat. Gizmodo leaked a picture of Taco Bell's "Taco Meat Filling" and surprise, surprise— it's missing a lot of the "meat" that it claims in its advertisements. Taco Meat Filling Ingredients
If you think you can get all 242 stars in Super Mario Galaxy 2 on your own, you've got another think coming. It's a lot harder than it looks. Sure, getting those first 120 normal stars seem like an easy enough task, but finding all of the remaining 120 green stars is the hard part. But then you have those last 2 that are even tougher.

Archie Leach. It just doesn't have the same ring as Cary Grant, does it? Marriage, divorce, or just dislike of the name your parents gave you – all are reasons to follow these steps toward a new name.

If you think you might be a likely target of a black-hat hacker, there's a new iOS security feature that offers extreme protection for your iPhone against spyware, phishing attempts, and other highly sophisticated cyberattacks.

Outside of plastic surgery disasters or costumes, augmented reality is the closest we can get to morphing our likenesses into those of animals.

UPDATE: Entries are now closed. Thank you for participating! Next Reality is where we help you literally 'see' into the future of augmented reality, and to help with that mission we're offering three free pairs of Snap Spectacles 3 to three lucky readers who sign up for the Next Reality daily AR email newsletter.

People fundamentally distrust magicians. And they should. The illusions they proffer are just that, illusions meant to astound rather than tangible interactions and results that have weight and meaning in our real world. Our lizard brains know this, and, no matter what the outstanding feat of "magic" presented, we nevertheless hold fast to our survival-based grip on the truth: we just saw simply "can't be real."

Open-source intelligence researchers and hackers alike love social media for reconnaissance. Websites like Twitter offer vast, searchable databases updated in real time by millions of users, but it can be incredibly time-consuming to sift through manually. Thankfully, tools like Twint can crawl through years of Twitter data to dig up any information with a single terminal command.

Cruise Automation, the driverless car startup General Motors (GM) bought for $1 billion in 2016, is readying a formidable fleet of robo-taxis for rollout in cities throughout the US. But when it comes to details about how the company plans to realize these lofty goals, it's been fairly tight-lipped.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

One major component of Level 4 and Level 5 driverless cars is in very short supply. Venture capitalists and engineers from around the world are racing to fill the LiDAR production, price, and performance void.

It looks like Chris Urmson has spent the six months since he left Google's Self Driving Car Project trying to build a get-rich-quick self-driving unicorn, along with Sterling Anderson, formerly with Tesla Motors. At least that is one of several scandalous accusations in a Tesla lawsuit aimed at the pair, and their secretive startup Aurora Innovation, LLC.

Unruly customers. Crazy exes. Horrible bosses. When you need proof of insanity or just want it for your records, recording a phone call is a must. Problem is, it's not the easiest thing to do on an iPhone — but it's completely possible.

At some point in time on TV or in a movie we’ve all witnessed a person pull a tablecloth clear off of a table without spilling the items on top. This is not an illusion, it can be done. Don’t choose your mother’s fine china to start with but do try it out.

In this series of driving safety videos, our professional law officer shares his experience in dealing with road rage and similar unsafe driving situations. Corporal Shaun Appler gives you tips on how to recognize an overly aggressive driver and how to avoid confrontations with them if at all possible. If you do happen to get involved in such a situation, remain calm: never agitate the aggressive driver who is already upset. Countering someone else’s road rage with road rage of your own can l...

In this video series, watch as professional homemaker Vickie Pavone teaches how to iron clothes and other household items. Learn how to iron fitted sheets, how to iron flat sheets and pillow cases, how to iron a blouse, how to iron a skirt, how to iron pleats, how to iron a men's button down shirt, how to iron a men's polo shirt, how to iron slacks, how to iron denim, how to iron a law enforcement uniform, how to iron clothes using starch, how to iron, delicate silk fabrics, how to iron synth...

Recording phone calls has always been tricky due to legal, ethical, and technical considerations. With iOS 18.1, Apple brings your iPhone a native call recording feature that simplifies this process while addressing privacy concerns.

The first step to getting your life together? Getting your online security together. After all, security when you're shopping, video calling, and more means more than ever in a digital age when anyone can copy your info or try to pose as you on the web. This Premium Privacy Bundle featuring Zenmate and StartMail will give you a secure VPN and encrypt your emails, all at a bundled price. The security duo is on sale for 60% off for a limited time, which means it's just $44.99 (regularly $113).

While consumer-grade smartglasses are the holy grail for tech companies, smartglasses maker Vuzix knows where its bread is buttered, and that's in the enterprise segment.

While a viable version of consumer-grade smartglasses has yet to find mainstream success, two more contenders emerged this week, as Vuzix confirmed that a leak of a fashion-forward design is legitmate and Vivo introduced tethered smartglasses designed to pair with its new 5G smartphone.

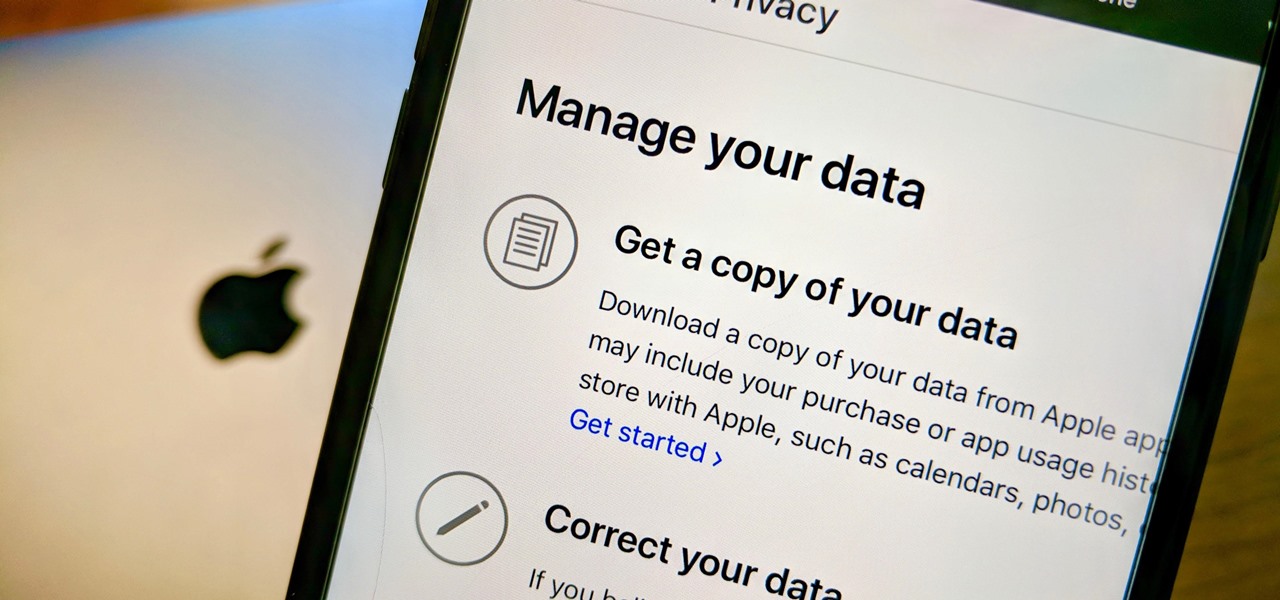
Personal data is a hot topic right now, and for good reason. Never before has the public been so on edge about how companies use their information. Services like Facebook and Google now allow you to download all of the data each has on file. Soon, you'll be able to see exactly the same for Apple as well.

OnePlus has now officially upgraded both the 5 and 5T to Android 8.1 Oreo. As implied by the version number, this isn't a huge update from Android 8.0 Oreo. However, OnePlus has included a few of their own features as well.

Messaging apps can be a double-edged sword. Not only do they let you interact with other people, but they also let you go back and reminisce on past exchanges. However, that same archive can be used against you in certain situations. Luckily, Signal can be manipulated to remove any record of past messages.

As of 2016, there are approximately 1.85 billion Android smartphones worldwide. This growing popularity has led to an increasing number hacks and cyber attacks against the OS. Unfortunately, Android users need more protection than what is offered by Google. The good thing is that there are a number of options available.

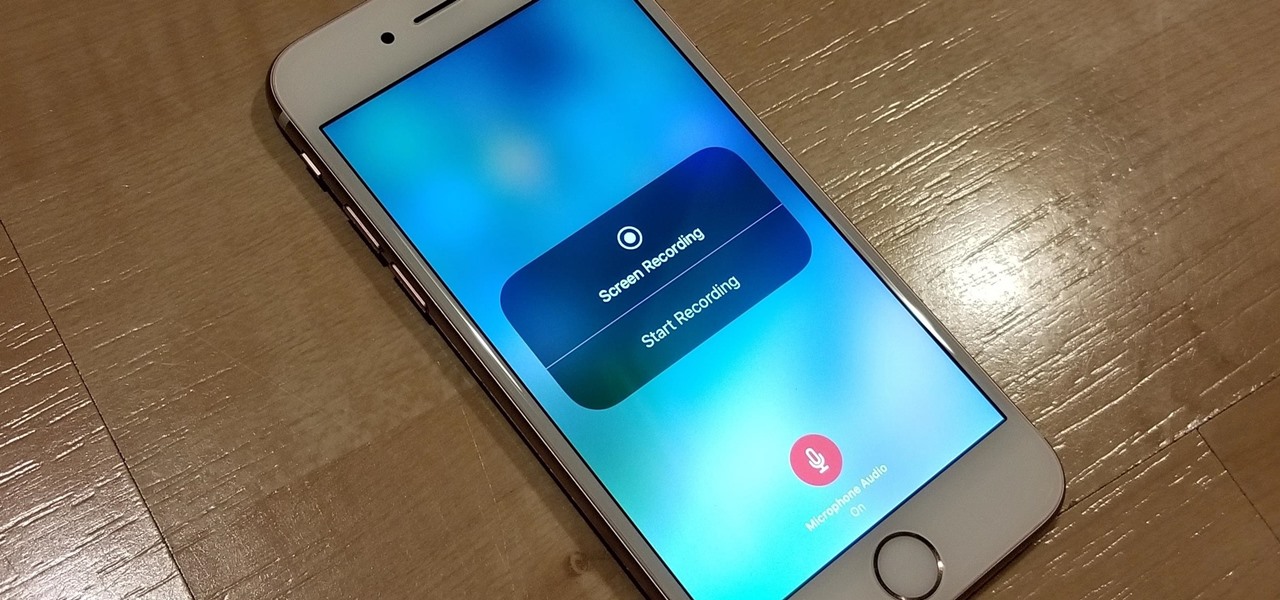
The only official way to record your iPhone's screen before iOS 11 was to hook it up to a Mac and use QuickTime Player to do the recording for you. If you wanted to record your iPhone's screen without an external device, there were unofficial apps you could use, like AirShou, but they required complicated installations. Now, in iOS 11, iOS 12, and iOS 13, Apple has an official, native screen recording tool.

New statements from Apple make it clear that they do not believe a hacker, or group of hackers, breached any of their systems. This comes after a recent report from Motherboard that a hacker gang called the "Turkish Crime Family" is threatening to remotely wipe up to 559 million iPhones by April 7.

A robust appetite for imported foods is leading to increased disease outbreak in the US. Despite the locovore and slow food movements, America's demand for foreign foods is picking up. According to a study published in the journal of Emerging Infectious Diseases, demand for imported fresh fruits, vegetables, and seafoods has jumped in recent years.

Marijuana is legal to use for medical purposes in 28 states and the District of Columbia, but the quick development of this new industry could have left some regulation issues in the lurch.

Last week it was announced that Waymo, the former Google Self-Driving Car project, had graduated from Alphabet's X innovation center. This graduation had been in the cards for many months with senior members of the project team and X hinting that it would be soon.

As Android's official app provider, the Google Play Store is packed with thousands of useful programs. But Google's terms of service is extremely restrictive, which means that countless apps simply don't qualify to be hosted on the Google Play Store.

Chestnuts are roasting on an open fire, which can only mean one thing: Christmas is nearly here. It's the time of year we're supposed to spend with family and friends, but usually we spend it stressing out over what to buy everyone on our list without going over budget, or shopping for decorations or holiday-friendly food items.

You want to become anonymous, and dont want your IP to be logged on websites? Well read along here. Continuing This Series:

As many of you know, processor's clock frequency improvement got stuck in about 2003, causing the origin of multicore CPU (and other technologies). In this article I'll introduce you on how to run code simultaneously in various processors (I suppose that all of you have a multicore CPU). When you write code without any parallel directive, it only executes in one CPU at the same time (see it below). OpenMP make simple to work with various cores (if not with all of them) , without so much heada...

Welcome back, my nascent hackers! Although my favorite TV show, Mr. Robot, had completed its first season already, I have not completed demonstrating the hacks that Elliot used in the show. (By the way, I can't wait for season 2!)

Welcome back, my fledgling hackers! In this series, I am trying to develop your knowledge of digital forensics, which is valuable whether you're choosing a career in it or just want to know how your hacker activity can be traced. Few professional digital forensic investigators have a hacking background, but the best ones do.

Big box stores love to sell gift cards, and as consumers, we snap them up almost as quickly as they can be printed. This industry has become rather profitable, though, because portions of the gift card balances often go unused.

Welcome back, my tenderfoot hackers! A short while ago, I started a new series called "How to Spy on Anyone." The idea behind this series is that computer hacking is increasingly being used in espionage and cyber warfare, as well as by private detectives and law enforcement to solve cases. I am trying to demonstrate, in this series, ways that hacking is being used in these professions. For those of you who are training for those careers, I dedicate this series.

We are living in a golden age of craft beers. Originally invented by the ancient Egyptians, every culture now has its own tastes regarding beer. The process of making beer is so multi-faceted, it's a miracle that any gets made at all.