
How To: Understand the basics of electronics with a 28-280 kit
In this five-part video tutorial series, you'll learn the fundamentals of working with electronics. To follow along, you'll need a 28-280 Electronics kit from RadioShack.


In this five-part video tutorial series, you'll learn the fundamentals of working with electronics. To follow along, you'll need a 28-280 Electronics kit from RadioShack.
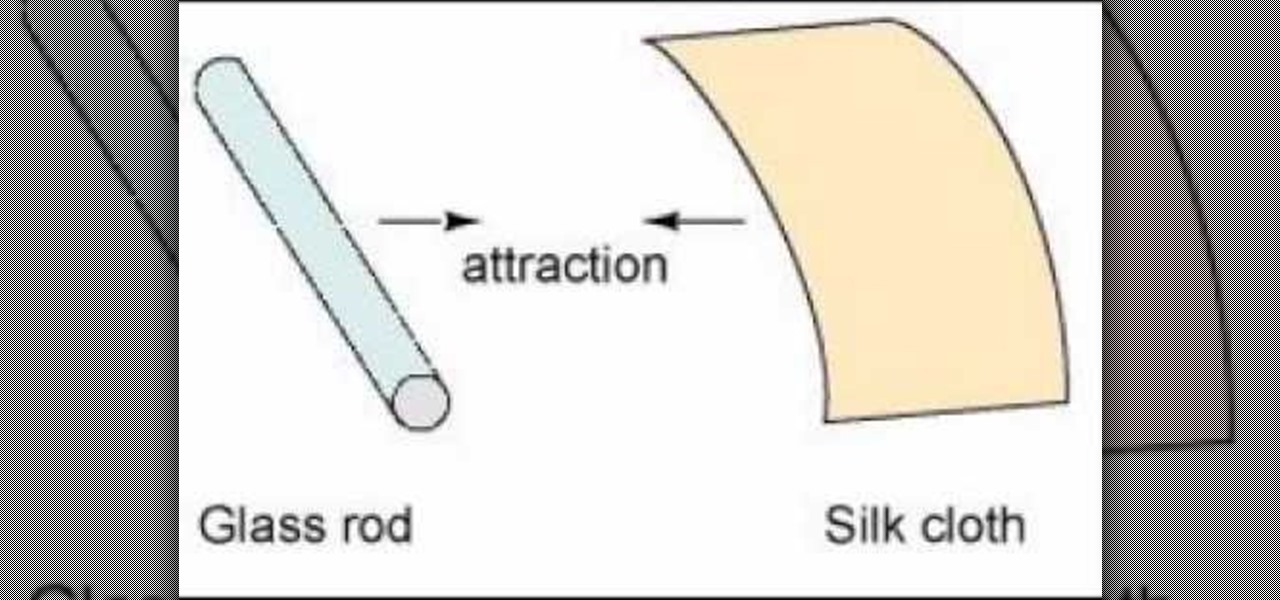
In the first video, you'll see how contact between different materials can result in attraction or repulsion. Experimental results are discussed that led to Ben Franklin's one fluid theory of electricity. It explains how clues were found from rubbing different materials together.

While privacy and security are cornerstones of Apple's ecosystem, your iPhone isn't bulletproof. Creating a strong passcode will protect you from most threats, but there exist tools that can break through even the toughest passcodes via the Lightning port. Luckily, Apple has implemented a new security feature to disable your Lightning port and keep your data safe and secure.

While Meta Company has agreed to a settlement in its lawsuit against a former employee and his company, they find the tables have now turned on them in the form of patent infringement allegations from another entity.

If the recent "state sponsored" Yahoo hack wasn't enough motivation for users to stop using their services, the latest news about Yahoo should be. Joseph Menn, a reporter at Reuters, just revealed that Yahoo created a custom email wiretap service for the US government.

Greetings my fellow aspiring hackers,


Welcome back, my nascent hackers!
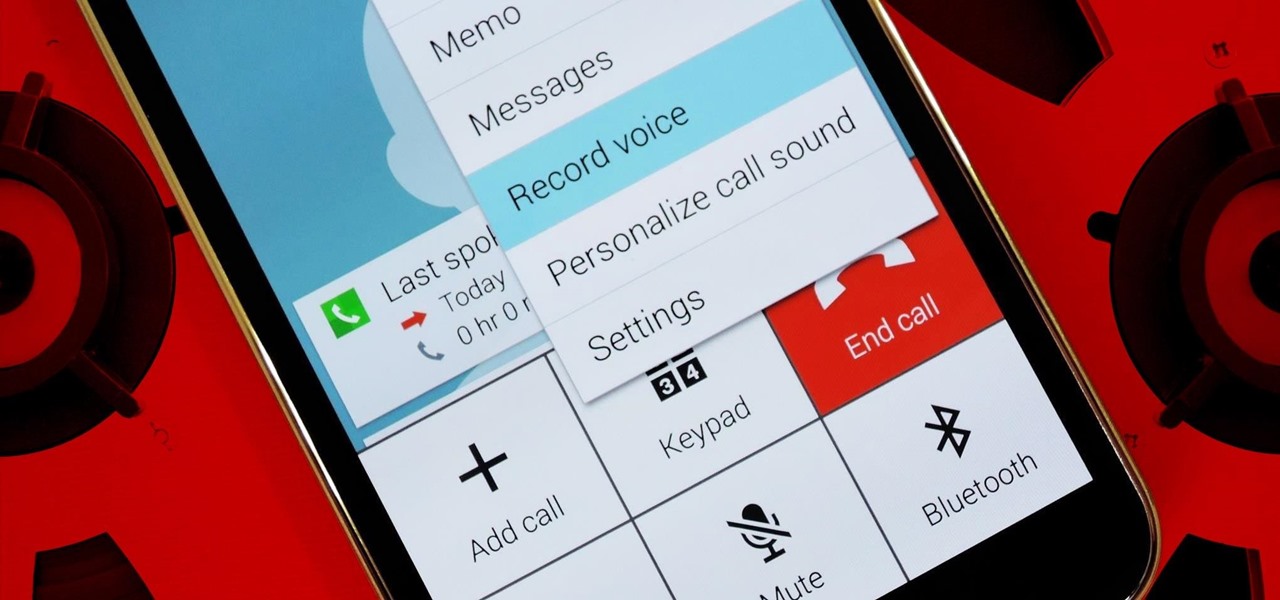
Before your carrier got its grubby little hands on your Galaxy S5, there was less bloatware installed and more functionality offered by the Samsung flagship device. Case in point: the GS5 that Samsung designed was capable of recording phone calls, yet the one that you own probably isn't.

Welcome back, my greenhorn hackers! Lately, much of the discussion here on Null Byte has revolved around evading detection and not getting caught hacking. Several of you have written me asking for a series on evading detection and forensics, and while I began a series 5 months ago on just that, we have changed hacking platforms from BackTrack to Kali, which has a much more highly developed forensic toolset.

If there's one way to get a visceral response from someone, it's bringing up the DMV. Regardless of the reason, whether it's the long lines, disgruntled employees, or just general inefficiency, I have yet to meet a single person who doesn't mind the trip. Just look at all those happy faces.

At a very early age, I would go on summer camping trips. I remember every night being handed a pack of sparklers that were my own, to swing around wildly, which gave me many valuable life lessons on cause and effect.

Starting an independent record label, like starting any other business, requires a well-conceived plan with clear goals. Check out this tutorial and learn how to take your love of music and turn a profit.

After you start drawing people, you will undoubtedly want to dress them. Drawing clothing is all about knowing how clothes fall, fold and wrinkle. Check out this tutorial, and you will be drawing realistic folks in no time.

There's nothing more disappointing than finding yourself all packed and ready to travel when you find your flight has been canceled. You can make the best of the situation by finding out just what you are entitled to or how to best ameliorate the situation.

The hottest outfits you could rock at a party or gala is a strapless dress. In order to keep that strapless dress up, you probably need a bit of cleavage, but what else can be done to make sure it looks right and works? The key to looking sexy in a strapless frock? A flawless fit.

Want to supply your head with a little extra jazz factor? Why not tie a scarf around it? You have only one head, but any number of ways to decorate it with a scarf.
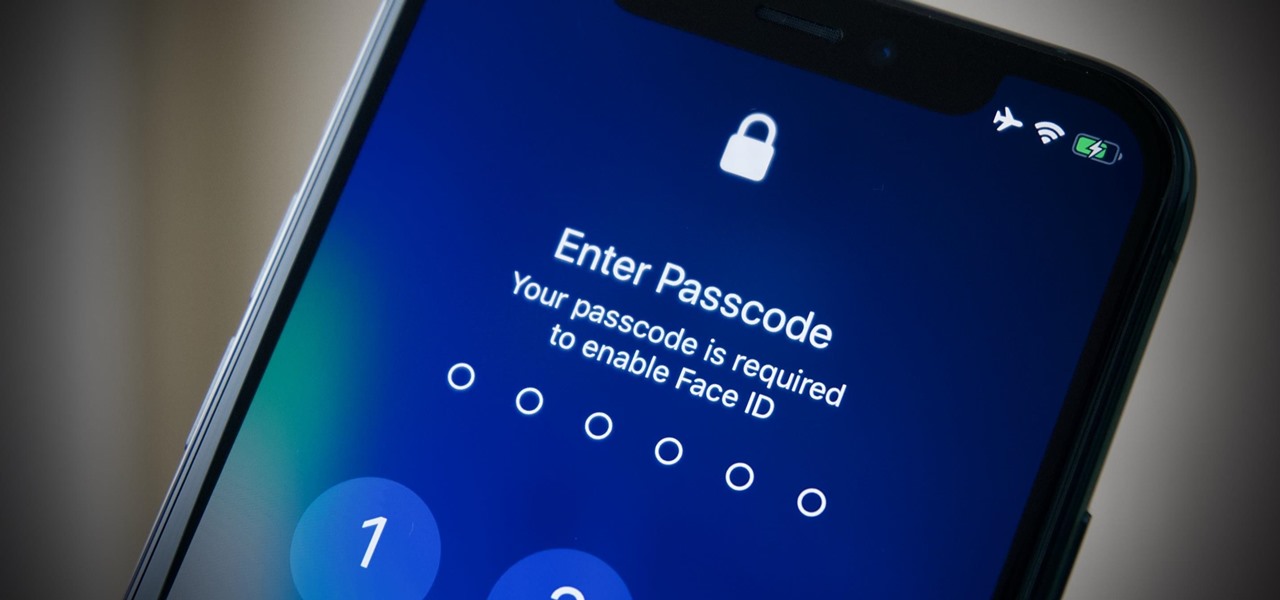
Here's the situation: you need Face ID or Touch ID disabled, yesterday. You don't have time to dig around in your settings, slowly working through an authentication reset. If you find yourself in a place where you think your own face or fingerprint will be used against you, use this trick to instantly protect your iPhone.

You may have recently seen a plethora of Instagram users, including celebrities and politicians, sharing a screenshot declaring that the platform will implement a new "rule" where it would own and could use your photos and videos however it wishes. The screenshots are part of an internet hoax, one that's been around in one way or another since 2012, but what can Instagram actually do with your media?

After North cut the base price of its Focals smartglasses, Vuzix is now testing the waters of a lower price point for its Blade smartglasses.

While the story of augmented reality headset maker Osterhout Design Group has come to an end, the epilogue of its demise continues.

In the realm of internet security, it's becoming clear that augmented reality is not immune to the increasing wave data breaches plaguing users.

Despite less than glowing reviews from critics, the latest installment from the Harry Potter spinoff movie series, Fantastic Beasts: The Crimes of Grindelwald, is winning at the box office.

The latest augmented reality feature from The New York Times gives readers a close-up view of the damage left behind by the eruption of Volcán de Fuego in Guatemala earlier this month.

Flying under the radar during Magic Leap's big week at the Game Developers Conference, the company settled a potentially ugly lawsuit with a former employee.

All the cash Magic Leap is amassing is probably going a long way toward hardware development and manufacturing, but it's also becoming increasingly clear that a large portion of that cash will be devoted to content. The latest proof is a new partnership between Magic Leap and the UK's Royal Shakespeare Company (RSC).
When it comes to making smartglasses that look more like regular eyeglasses and less like sci-fi helmets, Corning International might be among the suppliers to make it happen.
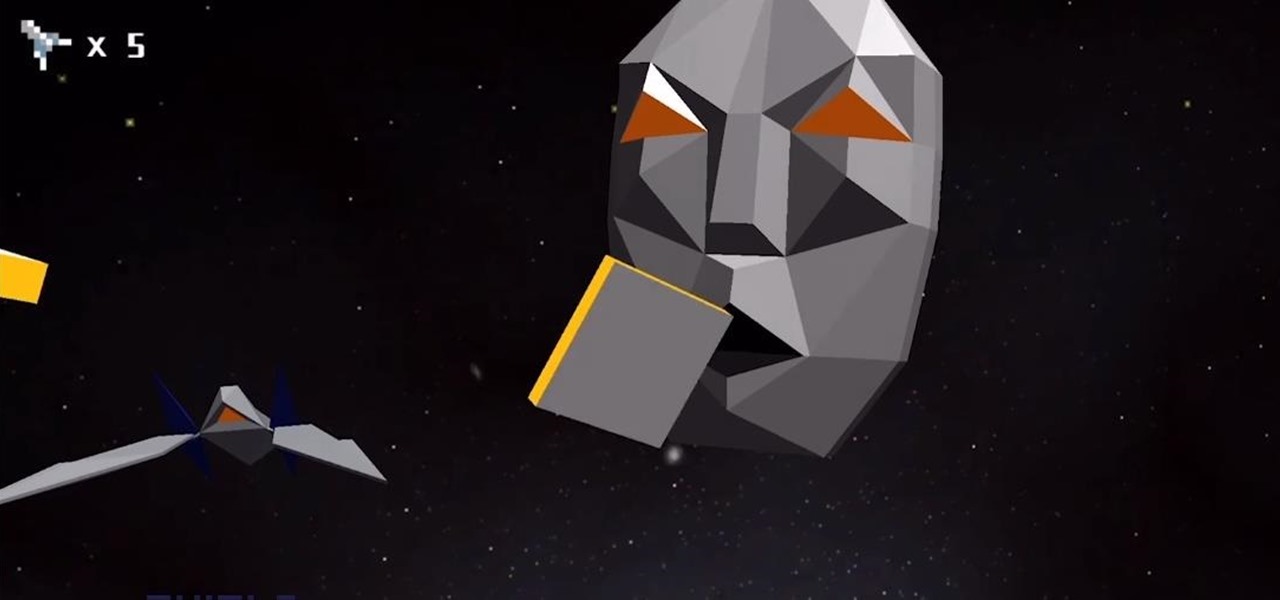
An AR/VR developer has managed to use the iPhone X to transport players into an emulation of the classic '90s video game Star Fox as the game's antagonist.

You would think most people would agree that you shouldn't use your smartphone while driving. Apparently, most people would be liars, according to recent data from the National Safety Council (NSC) and Zendrive.

Australia is looking to the future and finding driverless cars and other autonomous vehicles to be a top priority. Spacial Source reports that the state government has put AU$10 million into their Future Mobility Land Fund "to drive local development of autonomous vehicle technology."

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.

How to Make Homemade Carmel Cake. My Late Mother In-Law use to Always make this Cake

Here's how to make a simple form of a slow burning fuse from materials around the house. WARNING: Ignition of an incendiary or explosive material may not be legal in your area, so check local laws before attempting. Use of this video content is at your own risk.

Cooking isn't something that interests me much, unless it results in a fast burning fuel and a successful rocket launch!

Did you know that the average cost to make a penny is about 2.4 cents?!? That's why the Obama administration asked Congress earlier this year for permission to change the metals in the penny, hoping to get the cost back down where it makes sense.

Security researcher Nadim Kobeissi has discovered that the Windows 8 SmartScreen feature, meant to screen downloads for malicious software, actually reports the data about which applications users are installing to Microsoft. He also says that "the Microsoft server is configured to support SSLv2 which is known to be insecure and susceptible to interception." The two main concerns are the ability of law enforcement to subpoena Microsoft for the information and of hackers to intercept user data...

This video teaches the method to find the area of triangle using law of cosines and law of sines together with the area formula. Law of cosines is used when you have the length of three sides. It states that the square of side 'a' is equal to addition of the squares of sides 'b' and 'c' minus the product of 2, b, c and cosA. The values of sides are substituted and angle A is found. This is substituted in the area formula which states that the area of a triangle is equal to the half of the pro...

Learn how to pronounce the OUGH sound in American English. This video language lesson from Rachel's English provides a basic guide for pronunciations for ESL students. Say "ough".

Reading the augmented reality news lately has felt a bit like reading a John Grisham novel, as the business side of things has dripped with legal drama.

There has been significant debate over law enforcement's right to access our digital devices in recent years. New tools from Grayshift and Cellebrite are popping up faster than ever to help government agencies, as well as traditional hackers, break into iPhones. If you're concerned, you can take steps right now to beef up your passcode and prevent outsiders from gaining access to your device.