Welcome back, my greenhorn hackers! As hackers, we often take for granted that nearly all of our hacking tools and operating system are free and open source. I think it's important to examine a bit of background on how we arrived at this intriguing juncture in the history of computer software. After all, we pay for nearly all of our other software (Microsoft, Adobe, etc.) and nearly everything else we use in life, so how is it that Linux and all our hacking tools are free?

With a root bounty of over $18,000 up for the taking, developers were highly motivated to get the AT&T and Verizon Wireless variants of the Samsung Galaxy S5 rooted. Legendary hacker George Hotz, aka Geohot, has won the race and can now step up to claim his prize.

This is evil and it destroys people. Let's just get that out of the way. Nonetheless, suppose you need to make someone distrust their own memory and perception of reality. Suppose you want someone to believe in you more than they believe in themselves.

As practically the entire Steampunk world knows by now, IBM has predicted that Steampunk will be the big new trend from 2013 to 2015. They based this prediction on their computers, which sift through broad swathes of the internet in order to see patterns that may help commercial industries. According to them, Steampunk has been on the rise for the last few years, and they predict that it will explode into peak popularity within the next two years. But what does that mean and how will it impac...

People take their Black Friday shopping seriously. Some of them are even willing to fight over it. Every year the stories get crazier and crazier, and someone always gets hurt (or even killed).

Most people have tons of gadgets laying around the house these days, and they all need to be charged. Let the Wood Whisperer take you through the process of building a gadget station for all your favorite electronics. From laptops to cell phones, this gadget station will hold them all. Be sure to watch the entire 12-part tutorial from beginning to end for the whole experience.

The environment window is the heart of MIDI management in Logic 2.0. This tutorial from Emagic and ETV shows you how to use this environment window with your midi audio in Logic 2.0.

A professional Roulette trainer explains in detail and through live demonstrations the rules of the game, explaining the differences between single and double, money management, and percentages. You will get to understand possible mistakes.

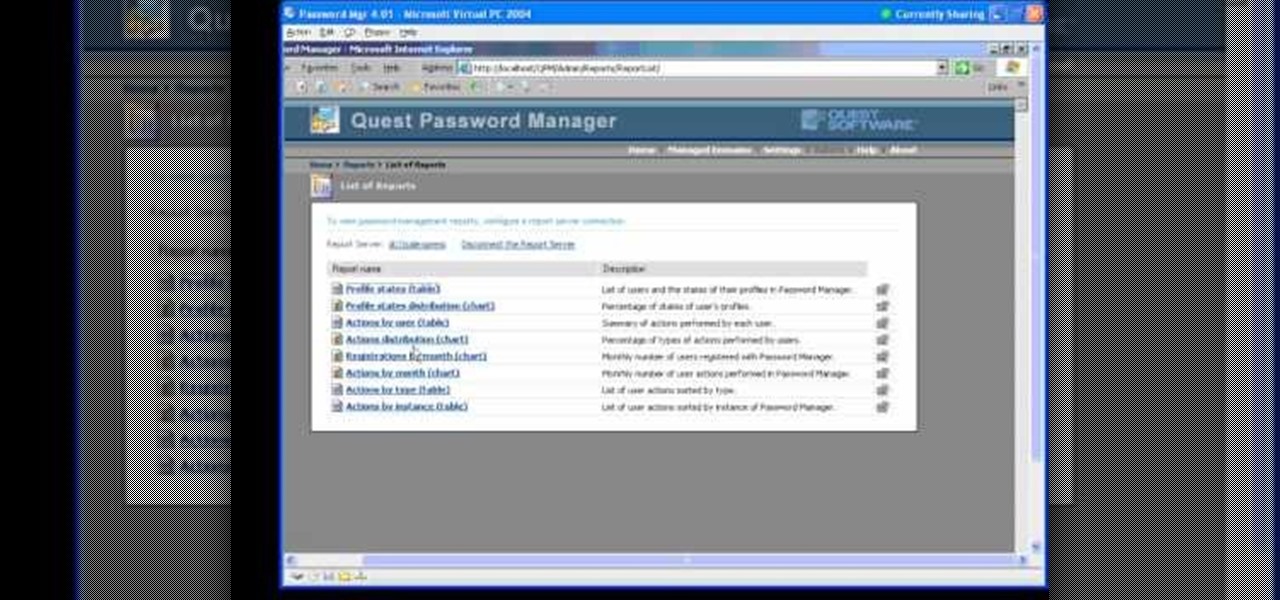
In this Webcast, Password Management for Windows and Beyond, you will learn how to: Increase security standards cross-organization by easily customizing and enforcing password policies for Windows, Unix, Linux, and Java users.

Watch this demonstration on Spotlight on SQL Server Enterprise by Quest Software. Spotlight on SQL Server Enterprise is a part of the Quest Management Suite for SQL Server as well as standalone offering. This demonstration shows the use of Spotlight on SQL Server Enterprise within the Management Suite

Hotels are anonymous and while this is a great thing, you should also be careful about the nameless folks who've used your room before you. Follow this tutorial to make the most of your hotel and ensure a great vacation experience.

Getting angry makes you look weak, especially in an argument. Defuse your temper with these helpful tips.

Okay, Mr. Thrifty, you reserved the least expensive hotel room that you could. But your inner Donald Trump doesn’t want to settle for low-frills. Go ahead, it never hurts to ask. Watch this video to learn how to get a hotel upgrade.

Project managers — and those hoping to become one — should rejoice at this killer deal. The Project Manager's Essential Certification Bundle Ft. Scrum, Agile & PMP usually runs for $1,990 but is only $49.99 for a limited time.

If you're interested in becoming an in-demand project manager or leader in today's data-driven world, you need to know more than just a few generic management strategies to lead teams and companies successfully.

While there are many advantages to working from home, properly managing your time can be a real issue. Working remotely requires a particular skill set, including an ability to focus, self-motivate, and communicate from a distance. Thankfully, all of these skills are teachable.

For a decade, Microsoft Azure has been transforming businesses across the globe. The cloud-computing service is leading the way in software as a service (SaaS), platform as a service (Paas), and infrastructure as a service (IaaS) protocols.

Invented by Motorola engineer Bill Smith in 1986, Six Sigma's methodology defines a series of steps with specific value targets. These targets can be used, for example, to eliminate costs and process cycle time while increasing profits and customer satisfaction.

Another year, another battle between Samsung and Apple. We recently saw what Samsung is bringing to the table this year with the release of the Galaxy Note 10+, and now it's Apple's turn. For those who want a truly large device, Apple is offering the iPhone 11 Pro Max. Let's see how they match up.

In order to increase the security and harden the integrity of an email account and its content, you'll want to use PGP on your Windows, macOS, or Linux computer. This is usually the first thing security analysts do to protect communications with encryption, and everyone else should consider it too, especially since there's an easy way to incorporate PGP that anyone can follow.

While ARKit and ARCore are poised to bring AR experiences to millions of mobile devices, one company is poised to anchor those experiences anywhere in the world with just a set of geographic coordinates.

While IKEA is collaborating with Apple for its ARKit furniture app, Marxent is ready to help the rest of the interior decorating and home improvement crowd with their apps.

While the world is only recently becoming aware of its existence, augmented reality has been around in some form or another since the '90s. In the last decade, with the advancement and miniaturization of computer technology — specifically smartphones and tablets — AR has become far more viable as a usable tool and even more so as a form of entertainment. And these are the people behind mobile AR to keep an eye on.

Over 6,500 waterfowl—mostly ducks—have died in Canyon County, Idaho, stricken by avian cholera. The outbreak started in February, and before it's over, it may not only be Idaho's largest outbreak, but one of the largest in the country.

In this article, we will build a parallel password cracker using the techniques explained in the previous part. As SHA-512 is the digest function that Kali (and most modern Linux distributions) use to store our passwords, we will make a SHA-512 password cracker.

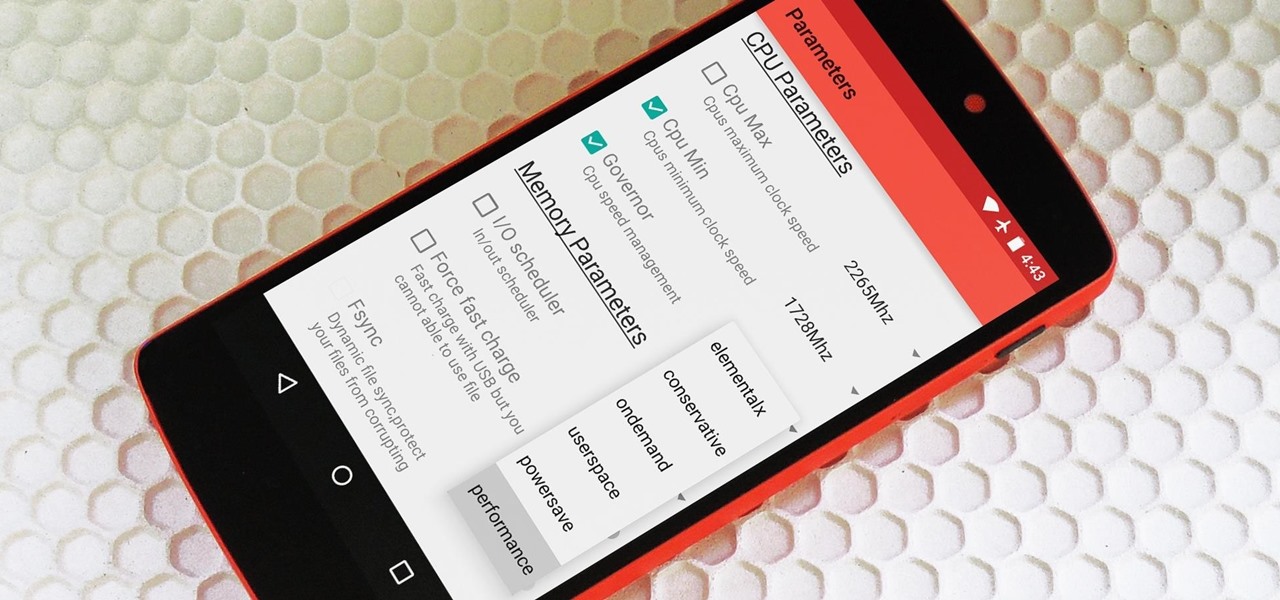
Deep down at the core of Android lies the system kernel, which serves as a bridge between software and hardware. Custom kernels can be installed in place of the stock offering, and these are generally optimized for better performance or increased battery efficiency.

In the aftermath of the unindicted police killings of Michael Brown and Eric Garner, we've been told that the system worked as intended. When our legal system's outcome is at conflict with what a majority of Americans believe is just, it's clear that some changes are needed. But what specifically needs to change? And what can an average citizen with a moral and just cause do to prevent these kinds of tragedies from repeating themselves again and again?

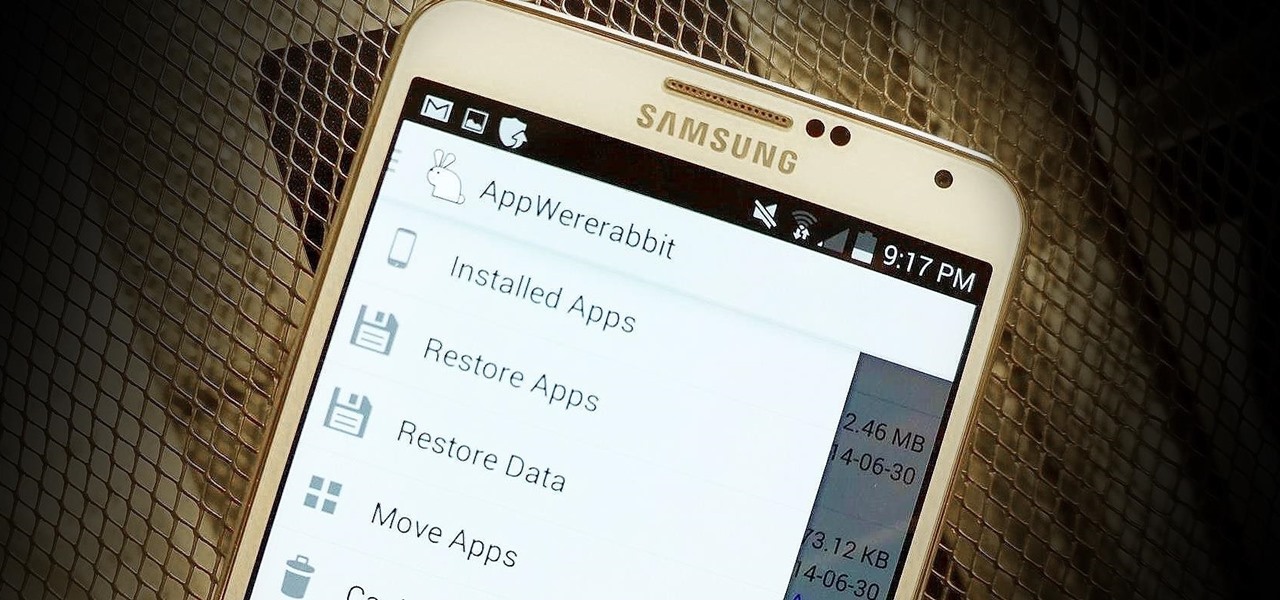
There are over 60-something Android apps cluttering my app drawer. While I'm constantly on the look out for new mods and apps to install, the default way of managing them is cumbersome and just feels unintuitive. I mean, who on Earth would wants to individually manage each app on their device?

If you think you might be a likely target of a black-hat hacker, there's a new iOS security feature that offers extreme protection for your iPhone against spyware, phishing attempts, and other highly sophisticated cyberattacks.

Undo. Redo. These two actions are forever intertwined, but they're missing from the standard keyboard on Android. Accidentally delete a word, and there is no Ctrl + Z to undo this mistake. But there is finally a solution available on Samsung Galaxy phones.

Few things are more important than being well-versed in data analytics and interpretation when it comes to succeeding in today's increasingly data-driven world. As a data scientist, these skills are the key to a high-paying career. For hackers, there's no better way to defeat the enemy than to become the enemy.

You've spent untold hours playing your favorite games. You know what you love. More importantly, you know what can be improved upon. The distance between vision and reality is not as far as you think. You just need a bit of training.

Sure, it's the giving season, but sometimes you've just got to treat yourself to some cosmetics. If you're shopping at Walmart, L'Oreal just made that a shade easier when shopping for Garnier hair color products with an assist from Google Lens and the Modiface AR platform.

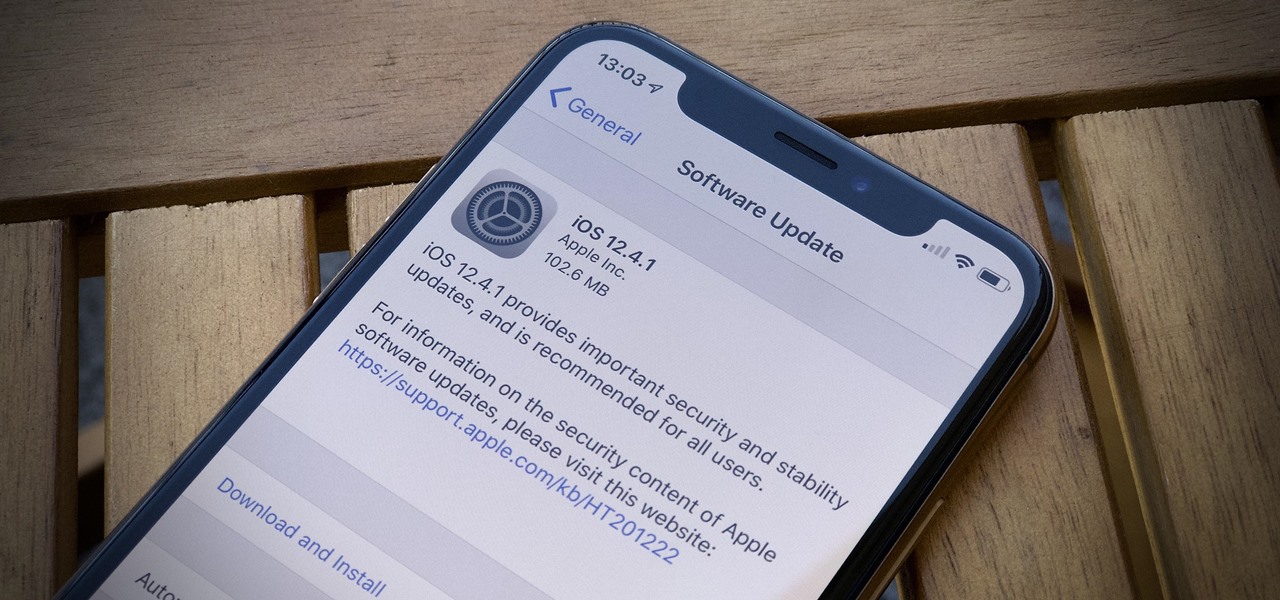
While all eyes might be on the next beta release for iOS 13, Apple is still pumping out updates for iOS 12. The company released iOS 12.4.1, the first update since iOS 12.4, on Aug. 26. The latest update includes a patch for the jailbreak vulnerability recently discovered in 12.4. One month later, on Sept. 26, iOS 12.4.2 came out for older iPhone models.

It's no secret that the enterprise sector is hot for augmented reality, but the move into the enterprise AR software market by one of the biggest names in industrial engineering announces the technology's arrival loud and clear.

Smartglasses maker Vuzix rushed out of the gate to be the first company to announce hardware powered by the Qualcomm Snapdragon XR1 for augmented reality wearables, but now the company is buying time until the product is ready to ship.

As the tech world patiently waits for the advent of mainstream consumer smartglasses, Google is content to stick to the business world (for now).

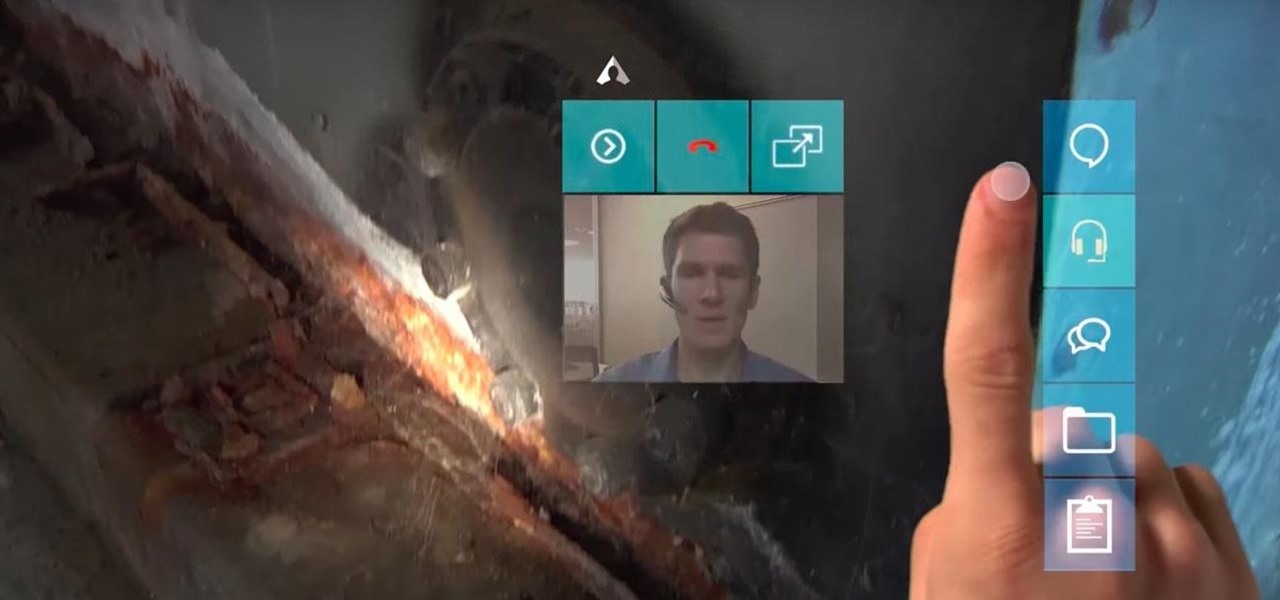
Not all enterprise augmented reality tools require a high-end headset and heavy computing power. Sometimes, a smartphone can do the job just as well. Along those lines, software maker Atheer is now bringing its workforce AR platform to iPhones and iPads via a native app.

After entering the UK's version of bankruptcy last month, Blippar's assets are up for sale, and bidding ended today.

Due to weaknesses in the way Wi-Fi works, it's extremely easy to disrupt most Wi-Fi networks using tools that forge deauthentication packets. The ease with which these common tools can jam networks is only matched by how simple they are to detect for anyone listening for them. We'll use Wireshark to discover a Wi-Fi attack in progress and determine which tool the attacker is using.