Welcome back, my greenhorn hackers! Lately, much of the discussion here on Null Byte has revolved around evading detection and not getting caught hacking. Several of you have written me asking for a series on evading detection and forensics, and while I began a series 5 months ago on just that, we have changed hacking platforms from BackTrack to Kali, which has a much more highly developed forensic toolset.

Amongst the trove of high-end features on the Galaxy S5, the display may be the most impressive. Sporting a 5.1-inch Full HD Super AMOLED (Samsung's version of OLED) display with 1920 x 1080 resolution and 432 pixels per inch, Samsung's flagship has one of the best smartphone screens currently on the market.

With apps and games getting bigger and more memory-hungry every year, storage space is at a premium. High-definition videos and photos of innumerable pixels certainly don't help the matter, either.

Team Win Recovery Project (TWRP) is a custom recovery for Android devices and the one used by most softModders, mainly because it has touch-based actions, as compared to the more time-consuming button-based approach that ClockworkMod (CWM) uses.

It can be a pretty exasperating ordeal to hunt for one image on your tablet when you have hundreds and hundreds of photos in your gallery. Luckily, there are ways to make this a pain-free process on your Nexus 7, as well as make sure it's never a problem in the future.

As far as lock screens go, your Samsung Galaxy S4 and other Android phones offer quite a few options. You can use the classic PIN unlock, the novelty facial recognition, or the reliable pattern lock. But what if you get tired of entering the same old PIN or pattern every day?

Welcome back, my neophyte hackers! In today's hack, we're going to have a bit of Halloween fun. Have you ever had a boss who made you miserable with his micro-management and nagging? Maybe you thought he unfairly fired your friend/colleague? Well, now here's your chance to get a bit of revenge and keep him or her off your back!

A man once told me to never complain about gas prices. With the average price of regular unleaded gas at $3.34 a gallon, it's hard not to, even if it is the holiday season. Since my car averages about 22 mpg, the man offered me this proposition: "If I offered you $3.34, would you walk 22 miles?"

Of all the places you'd think to check for bed bugs, I doubt that library books would be at the top of your list. As odd as it sounds, though, libraries and library books are some of the most common places for bed bug infestations. Libraries all over the country have reported bed bug problems this summer, and some have even had to temporarily close to take care of the problem. But before you vow to never set foot inside a library again, here's a little primer on how to check your books for be...

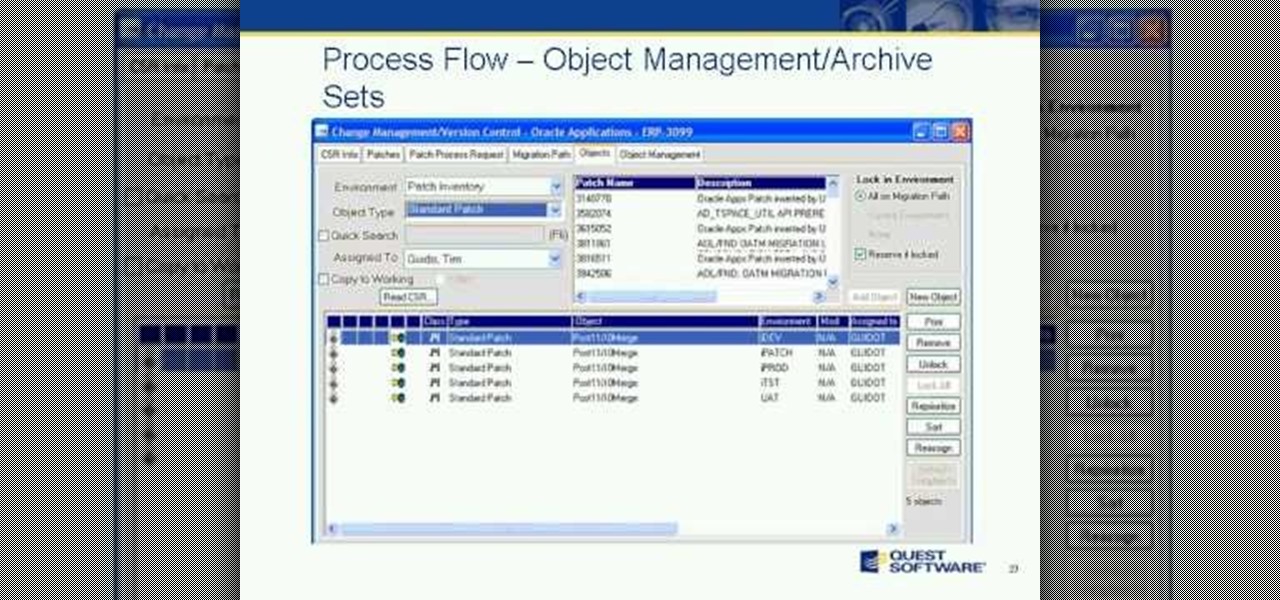
Join us and guest speaker, Cary Pochek - ERP Project Manager at Curtiss-Wright Corporation, as we discuss the importance of change lifecycle management when dealing with Oracle E-Business Suite implementations and upgrades. We will focus on best practices around:

Twitter's official iOS app is adequate if you're not much of a tweeter, but if you are, there's a lot of useful features that are missing. Luckily, there are plenty of free Twitter clients available that you can use on your iPhone. These third-party apps have features such as customizable interfaces, post scheduling, and different browser options for opening links, to name just a few.

Outside of plastic surgery disasters or costumes, augmented reality is the closest we can get to morphing our likenesses into those of animals.

With protests springing up across America, there's a chance you may have your first interaction with law enforcement. Many demonstrators will have their phones in-hand to film the action, which, sadly, could prompt an officer to demand the device and any self-incriminating data it may contain. Before this happens, you should know there are tools at your disposal to protect your data in such situations.

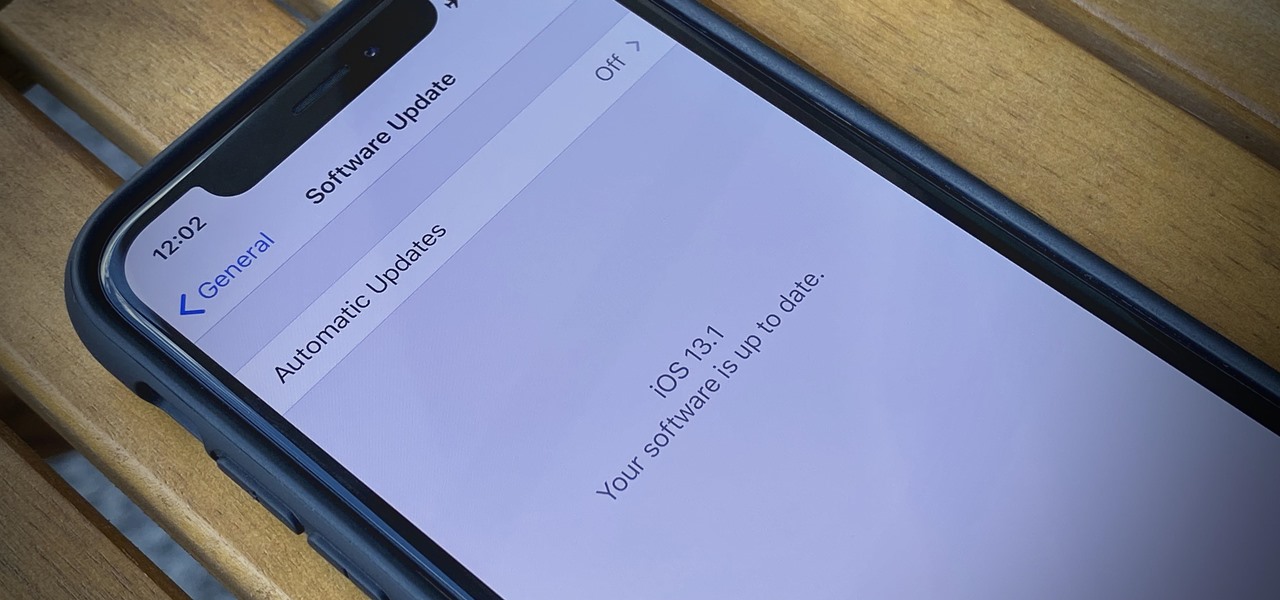
Apple released iOS 13.0 on Sept. 19 and announced on the same day the release of iOS 13.1 on Sept. 30. But that deadline was pushed up to Sept. 24, and that's why we have 13.1 just five days after 13.0. But that's good news since we don't have to wait any longer for some of the features promised in iOS 13 that didn't make the first cut.

Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private chat without clicking the link. Canary tokens come in several useful types and can be used even through URL shorteners.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

The world of investment and finance can be labyrinthine in its very nature — and even more complicated in regards to augmented and mixed reality. While these new emergent technologies are teeming with explosive levels of unrealized potential, there's still a big layer of uncertainty in terms of return — but these investors aren't afraid to take the leap.

One major component of Level 4 and Level 5 driverless cars is in very short supply. Venture capitalists and engineers from around the world are racing to fill the LiDAR production, price, and performance void.

It looks like Chris Urmson has spent the six months since he left Google's Self Driving Car Project trying to build a get-rich-quick self-driving unicorn, along with Sterling Anderson, formerly with Tesla Motors. At least that is one of several scandalous accusations in a Tesla lawsuit aimed at the pair, and their secretive startup Aurora Innovation, LLC.

Greetings aspiring hackers. I have observed an increasing number of questions, both here on Null-Byte and on other forums, regarding the decision of which USB wireless network adapter to pick from when performing Wi-Fi hacks. So in today's guide I will be tackling this dilemma. First I will explain the ideal requirements, then I will cover chipsets, and lastly I will talk about examples of wireless cards and my personal recommendations. Without further ado, let's cut to the chase.

These days, that pocket-sized computer we call a smartphone is home to your entire digital life. But with the onset of mobile payments and online banking, the line between your virtual world and the physical realm is becoming increasingly blurred.

In these videos our experts, two ladies who have been involved in city level water management and conservation for years, will show you how make your residence more water efficient. They’ll give you tips on where to look for leaks, both indoors and outdoors, as well as how to inspect the kitchen and bathroom for water overuse, adjust the hot water heater, and when to water your lawn for maximum effectiveness.

In this video series, learn how to work from home while raising children. Get important time management tips, and learn techniques for setting up a home office that’s far enough away from the children’s play area, while still being kid-friendly. Also learn about setting boundaries to help keep your workspace and your time on the job reserved for running your home business.

Microsoft Excel is one of the most useful tools you can bring into your professional life. However, as useful as Excel is, it can also be difficult to learn on your own. The All-In-One Microsoft Excel Certification Training Bundle is an incredible tool that will take you from Excel beginner to Master for $33.99, on sale for 98% off.

Whether you work in sales or want to become more persuasive and better at selling yourself, the art of selling can be transferred to nearly any career path or walk of life. Whether the gains are monetary or interpersonal, being a great salesperson is one of the most invaluable skills you can ever learn.

Have you ever admired those individuals that get so much accomplished in a day and wonder how the heck they do it? Now's your chance to learn their secrets. The Productivity & Motivation Master Class Bundle brings you everything you need to life-hack your way into leading a more productive lifestyle at home and work.

Amazon Web Services (AWS) offers over 200 services, including networking, computing, storage, analytics, blockchain, mobile, and developer tools. Not surprisingly, numerous companies rely on AWS's massive infrastructure. Instead of building their own server farms, they rent space and computing power from AWS's secure and robust system.

It's a common and unfortunate myth that you need to work in web or app development if you have a knack for coding and design. In fact, more and more development pros are entering the exciting and increasingly lucrative world of game design, thanks to a growing demand for strategy games that can be played on multiple platforms.

In the not-so-distant past, cloud computing was thought of primarily in terms of online storage platforms. Now, however, massive cloud infrastructures are used by virtually every major business to reach clients, manage data, and deliver services.

The career prospects for talented and trained IT professionals are nearly endless. As the world becomes more interconnected by the day, companies of all sizes are looking for people who can install, maintain, and troubleshoot a wide variety of networking infrastructures and web-based platforms.

The built-in Files app on your iPhone has only gotten better since it was introduced in iOS 11, with small improvements after each new iOS version. You can manage files on your internal storage as well as in iCloud Drive, but one of the best features is being able to manage media and documents from all of your cloud storage accounts in one place.

Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.

While consumer-grade smartglasses are the holy grail for tech companies, smartglasses maker Vuzix knows where its bread is buttered, and that's in the enterprise segment.

No operating system is stricken with as many vulnerabilities as Windows, and it's often a race to release the latest patches to fix things. From an attacker's point of view, knowing which patches are present on a Windows machine can make or break successful exploitation. Today, we will be covering three methods of patch enumeration, using Metasploit, WMIC, and Windows Exploit Suggester.

Investment in augmented reality remained robust in 2019. For the third consecutive year, we looked back on the biggest funding deals in the AR industry this week, and a familiar name came out on top.

The week in AR business news started out with a bang with two bombshell reports that cast a shadow on the AR industry as a whole.

Correctly identifying the underlying technologies that run on a website gives pentesters a considerable advantage when preparing an attack. Whether you're testing out the defenses of a large corporation or playing the latest CTF, figuring out what technologies a site uses is a crucial pen-tester skill.

If you're still working your way through the hundreds of features and changes that iOS 13 brings to your iPhone, you might be a bit surprised to learn that your device is now out of date. While Apple only dropped the big update for iPhones on Thursday, Sept. 19, the company has already released its successor. All iOS 13-compatible iPhones can now update to iOS 13.1, out today, Tuesday, Sept. 24.