Former Google and Uber engineer Anthony Levandowski's scathing accusations challenging the physics behind Tesla CEO and founder Elon Musk's claims about Autopilot should force Musk to make his case that self-drive cars don't need LiDAR in the next few months.
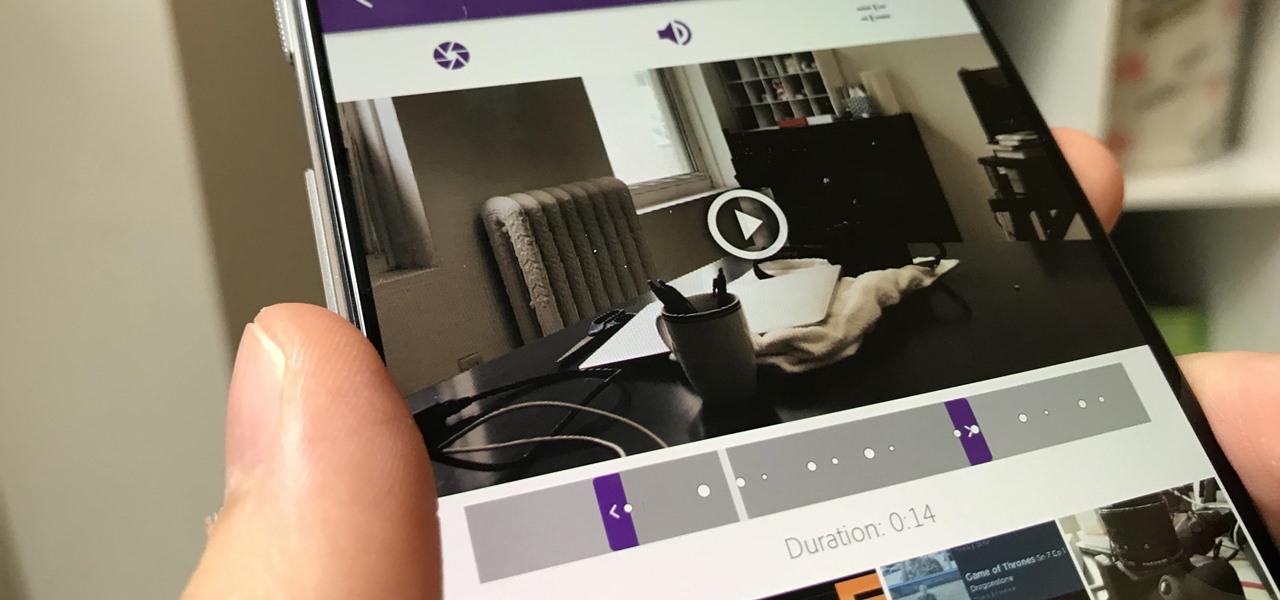
If you've just started a freeform editing project in Adobe Premiere Clip on Android or iPhone, what's next? The first thing you're going to want to do is trim down the video clips you imported into your draft, that way you can lay them out perfectly in your timeline and create the best video possible.

Cruise Automation is actively seeking to recruit a lead engineer to head its development efforts of 3D maps with expertise in city environments, signaling the GM driverless unit's move towards a mobility-as-a-service business model.

Much work needs to be done before laws and regulations no longer block driverless' rollout in the US, Rob Csongor, vice president and general manager of Nvidia's automotive division, said today during a US Senate committee hearing.

Augmented reality is quickly becoming a popular tool for marketing use cases, as demonstrated by new projects serving the automotive, entertainment, and tourism industries this past week.
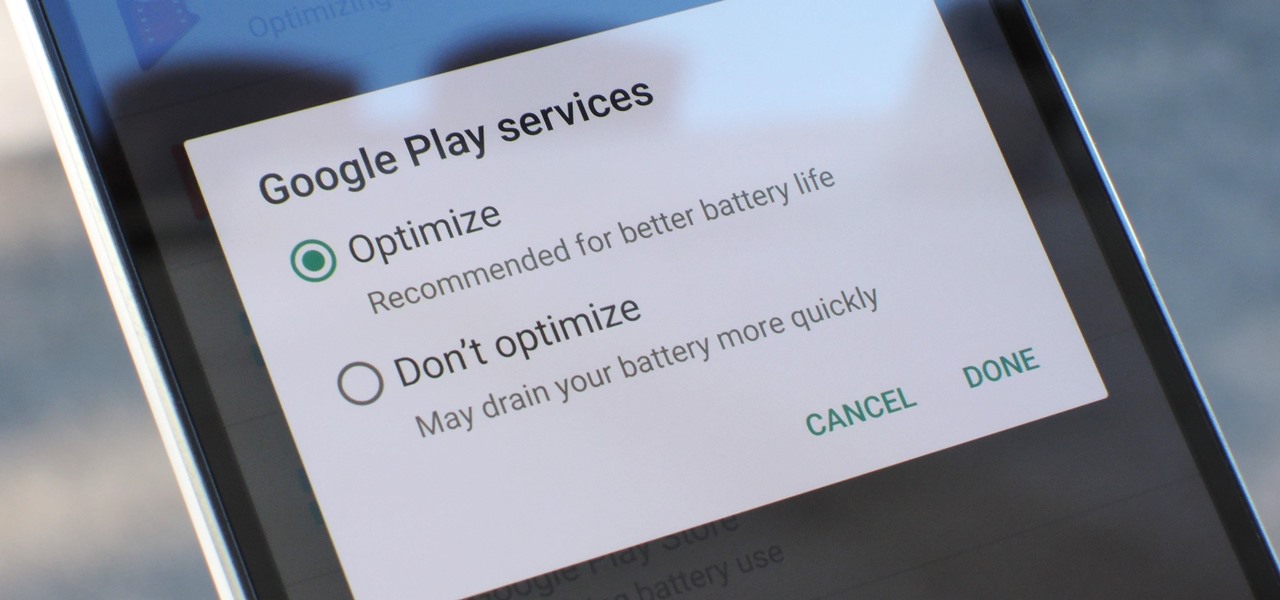
Google Play Services has been near the top of every Android user's list of battery-sucking apps for years now. It's a core system app, so you'd expect some battery drain, but for many folks, it runs rampant.

The drama continues! In the latest installment of the feud that has rocked the driverless vehicle industry, Waymo is now accusing Uber of withholding a secret LiDAR device.

Rooting a phone lets us install custom operating systems, known as ROMs, which replace the device's preinstalled OS. Most custom ROMs are based on code from the Android Open Source Project (AOSP), which gives them a look and feel similar to Google's version of stock Android. But every now and then, you'll see a ROM that isn't based on Android, though these are few and far between — at least, until now.

The Centers for Disease Control and Prevention (CDC) just reported some upsettingly high numbers of human papillomavirus (HPV) in adults. In data retrieved from 2013–2014, 22.7% of US adults in the 18–59 range were found to have the types of high-risk genital HPV that cause certain cancers.

The first public beta of Android O, (most likely to be called "Android 8.0 Oreo") was released on May 17, bringing tons of new features and goodies for Android enthusiasts with supported devices. However, not all of Android O's features were available to try out right off the bat. Possibly the single biggest feature announced during the developer preview of Android O, Picture-in-Picture mode, is nowhere to be seen.

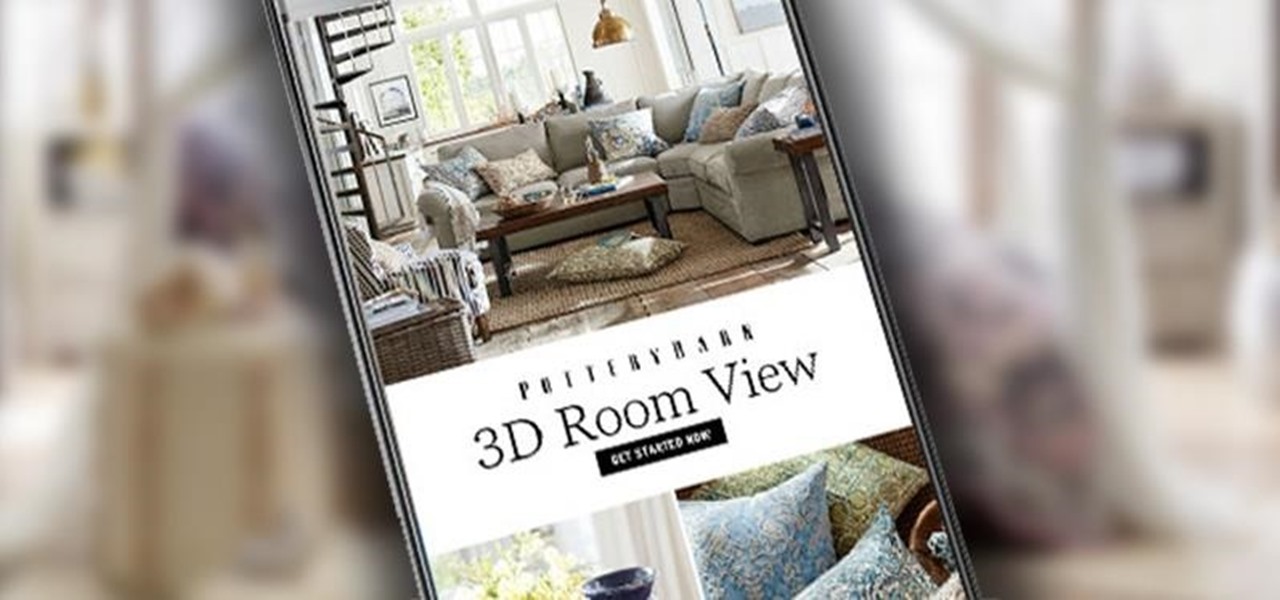
Pottery Barn has teamed up with Google to create 3D Room View, a new mobile app to allow all wannabe interior designers (like me) to pick out the perfect couch, table, or whatever, and then overlay it onto a spot in his or her house.

If anyone has every told you that they see music they listen to, they have synesthesia. It's a fascinating neurological phenomenon where people experience crossed responses to stimuli, and no one knows exactly how common this is. A rough estimate claims that one in every 5,000 to 100,000 people is a synesthete, but it could be far more common or rare. Nobody really knows.

We usually associate Salmonella bacteria with a dangerous type of food poisoning, but they actually are pretty good at seeking out tumors. That trait made the bacteria a great candidate to deliver a protein that would help knock tumors out.

No one can dispute the evolutionary success of bugs. The oldest insect fossils were found encased in crystallized mineral silica in Scotland in 1926, and they're between 396 and 407 million years old.

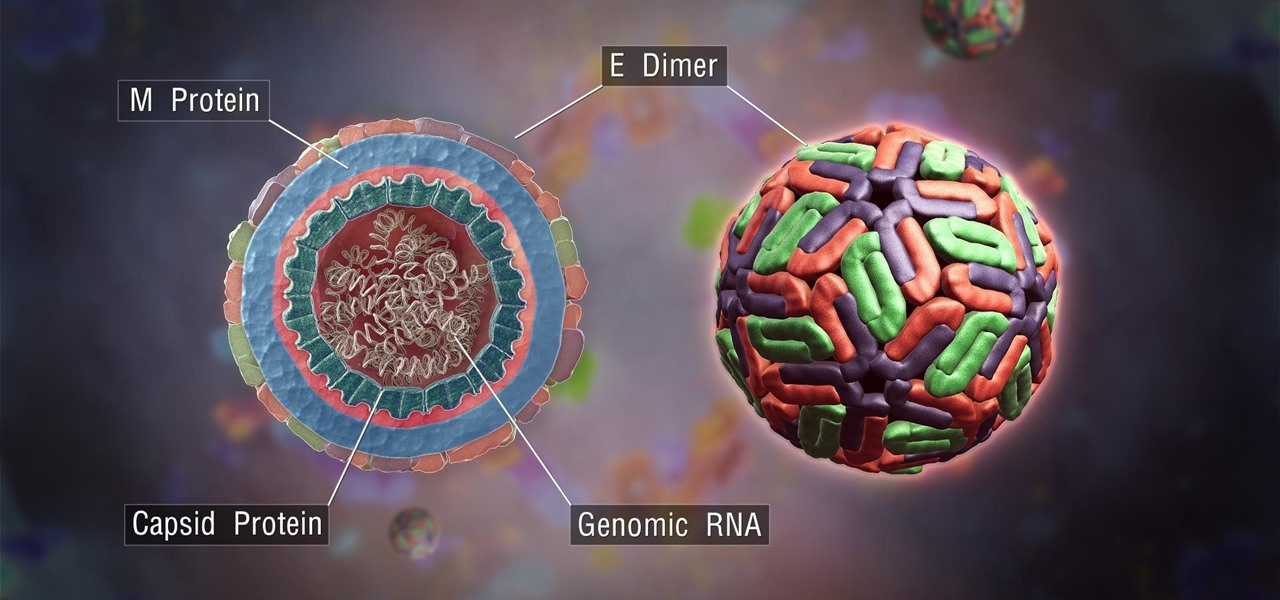
The mention of Zika can strike fear in the hearts of pregnant women. With infections increasing around the world, including in the US, researchers are fighting the clock to figure out how the virus can have such horrific effects in some people.

Metasploit is an extremely popular pentesting tool capable of enumeration, exploitation, and injecting shell code, and is a part of almost every hacking toolkit. So there's no way I could leave this out of our series on getting your Mac set up for hacking.

Fish are delicate, flaky, and can be damn tricky to cook; more often than not, you end up with a hard, dry block of flesh that makes your taste buds sad. And the best ways to cook fish that you know of—c'mon, who doesn't love a fried fish—take way too much effort for you to bother with on a weeknight. Or maybe you're looking for a healthier way to enjoy fish that doesn't require batter or frying at all.

Imagine you have mastered the perfect cherry pie for your annual work picnic but, upon taking it out of its airtight pie carrier, your heart sinks as you realize the crust has turned to mush thanks to the moisture from the filling. Sound familiar?

Verizon Wireless executives recently cooked up a plan so devious that it could have only come from one of the four major US carriers. Apparently, they aren't satisfied with simply loading every Android device they sell with their own bloatware, so now they're reaching out to big brands to see who would be the highest bidder for a spot on your home screen.

Sometimes the idea of cooking fish, especially for a group of guests, can be intimidating. There's the fear of the fish not cooking right, or sticking to the pan or grill. And even if you cook it right and the fish doesn't stick, you're left with the inevitable fishy-smelling cleanup. Not fun!

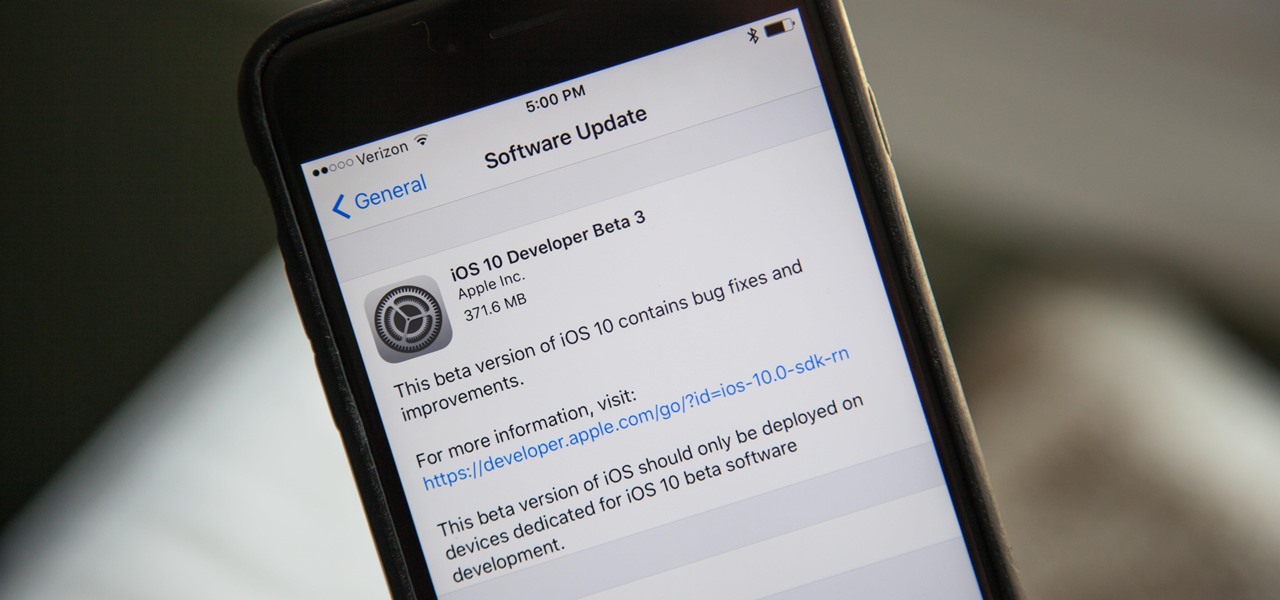
With the next iPhone release around the corner, Apple is hard at work getting iOS 10 squared away. On Monday, July 18, they issued the third beta of iOS 10 to developers, which should be released within a few days to those using the iOS 10 public beta.

Pokémon GO, the biggest augmented reality sensation ever, broke app store records this opening weekend. But it also did something even more important: it gamified physical activity.

Our brains do a magnificent amount of work to process visual stimuli, but they aren't difficult to fool. Optical illusions can trick our minds into believing what we're seeing is real, even if it's not—and virtual and mixed reality technologies take advantage of this little loophole in our brain to help us accept the unreal.

We used to saunter into the grocery store and gaze longingly at the pre-made roasted chickens, wistfully thinking of things we could do with the golden fowl if only we didn't already have dinner plans.

While it may not sound scary right off the bat, Blue Coat Systems now has an intermediate certificate authority. If you don't know what a certificate authority (CA) is, or who Blue Coat is, who cares, right? But you should... whether you use Mac or Windows.

Google seems to be growing tired of the way links appear in its Search results page, because they're currently experimenting with a color change (that's already causing lots of controversy).

When a craving for crunchy tacos hits, it's undeniable. Don't Miss:

A perfectly-roasted artichoke is a thing of beauty, but not everyone has the time (or patience) to deal with the extra fuss. So if you want an artichoke and you want it now, look no further than your ever-convenient microwave, which lets you steam one in only 10 minutes—no steamer basket necessary.

Pickling isn't rocket science. In fact, anyone can make their own speciality pickles using just about any fruit or vegetable. For example, I've pickled everything from lemons, watermelon rinds, and apples to red onions, carrots, radishes, and cucumbers.

A sphere of clear gelatinous goo may not sound all that appetizing. But to food fad fans on social media, the raindrop cake—a soft and lightly flavored edible blob—has gone insanely viral.

Video: . For the first prank you're going to need an empty container, preferably black, a smoke bomb and a lighter. I gotta say though this prank is not for just anybody so prank at your own risk. Let me show you how its done, first apply some hot glue on the bottom of the smoke bomb, then stick it inside the container.

What's up guys? Welcome to a sort of general walkthrough on how one might approach a reversing and analysis on a crypted malware. This is by no means a universal technique so don't assume that this will occur in every scenario, it's more of a demonstration than anything really.

What's good, peeps? I've been noticing some rather advanced tutorials slowly emerging here on Null Byte and I know that people want more of them but I've been reluctant to post something of such caliber because I fear that the information will just go over their heads, but hey, as long as it's there, people can always go off to research themselves and eventually understand. So here is my contribution to the gradual and inevitable progression of Null Byte!

Stock is a crucial ingredient for so many recipes: soups, gravies, and risottos depend on stock; quinoa and rice are both more flavorful when cooked with it, too. So, chances are that broth is a staple on your weekly shopping list.

I was fortunate enough to be visiting one of my college classmates in Columbus, GA last spring and saw two large bags of onions in his kitchen... but not like the ones you get at the grocery store. Two standing 50 lb. bags!

If you read my previous post, "How to Hack into a Mac Without the Password", you know that it is very easy to break into someone's Mac if you have physical access to the computer. Now the question that lies is, how do we protect ourselves from this happening to us? Well, here is a way that guarantees that no one will be able to change your password through OS X Recovery.

If you're careless and tend to leave your knives lying around or in the sink, chances are you've struggled with rusty blades.

If your smartphone is ever lost or stolen, it's a terrible experience. If you file a police report, chances are the responding officer will need your device's IMEI or MEID number if you want to stand a chance of getting it back. Same goes for making an insurance claim on a lost or broken phone, so it's definitely important to have this unique identifier handy.

Salad spinners are one of the more divisive kitchen tools out there. On one hand, they're incredibly easy, efficient, and useful. On the other hand, they're a single-use tool that takes up a lot of space.

So, how does someone keep their hacking life completely secret? What This Is: