
How To: Make the world's brightest LED flashlight: 3rd torch
The SSC P7 Flashlight is a tactical torch that's pretty bright at 900LM. But, it's totally possible to make it just a little brighter.


The SSC P7 Flashlight is a tactical torch that's pretty bright at 900LM. But, it's totally possible to make it just a little brighter.
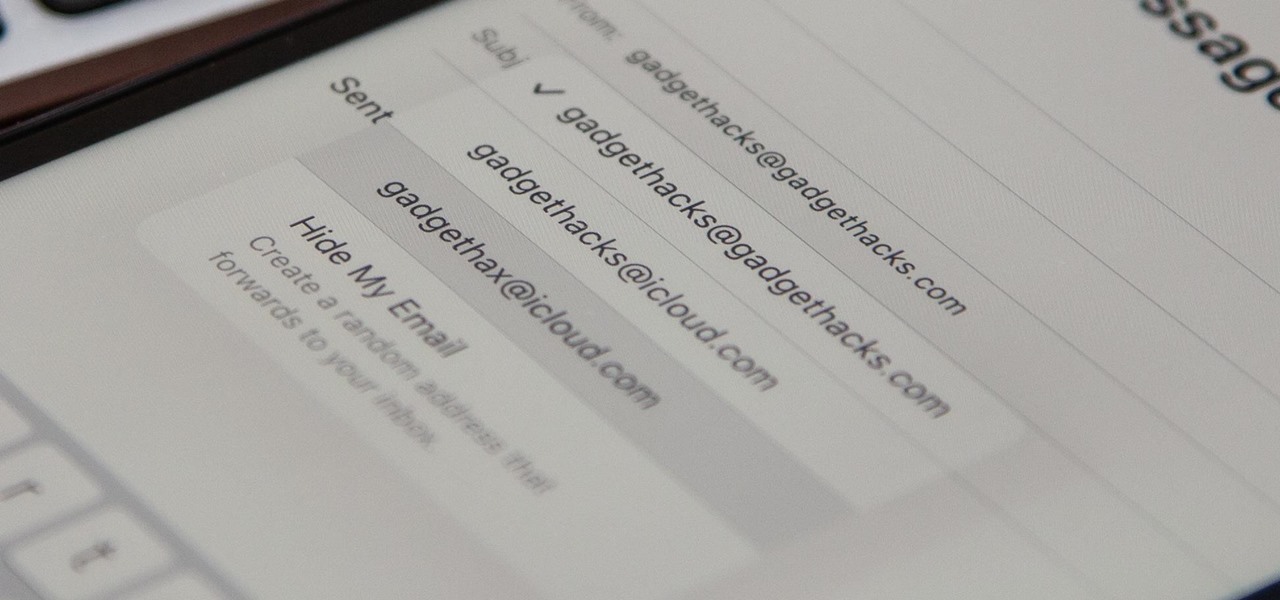
On your iCloud Mail account, you can easily use subaddressing to create hundreds of new iCloud email addresses to give to companies and other parties, all of which go straight to your primary iCloud email address's inbox. The problem with these types of alternative email addresses is that you can't ever respond to emails with the plus tag intact. But Apple has another alternative for you to start using.

For the most part, Google Wifi and Nest Wifi systems take care of themselves. But there are still a few manual features that might come in handy, like being able to check on network activity to see which devices are using the most bandwidth when your connection gets bogged down.

When it comes to sniffing Wi-Fi, Wireshark is cross-platform and capable of capturing vast amounts of data. Making sense of that data is another task entirely. That's where Jupyter Notebook comes in. It can help analyze Wi-Fi packets and determine which networks a particular phone has connected to before, giving us insight into the identity of the owner.
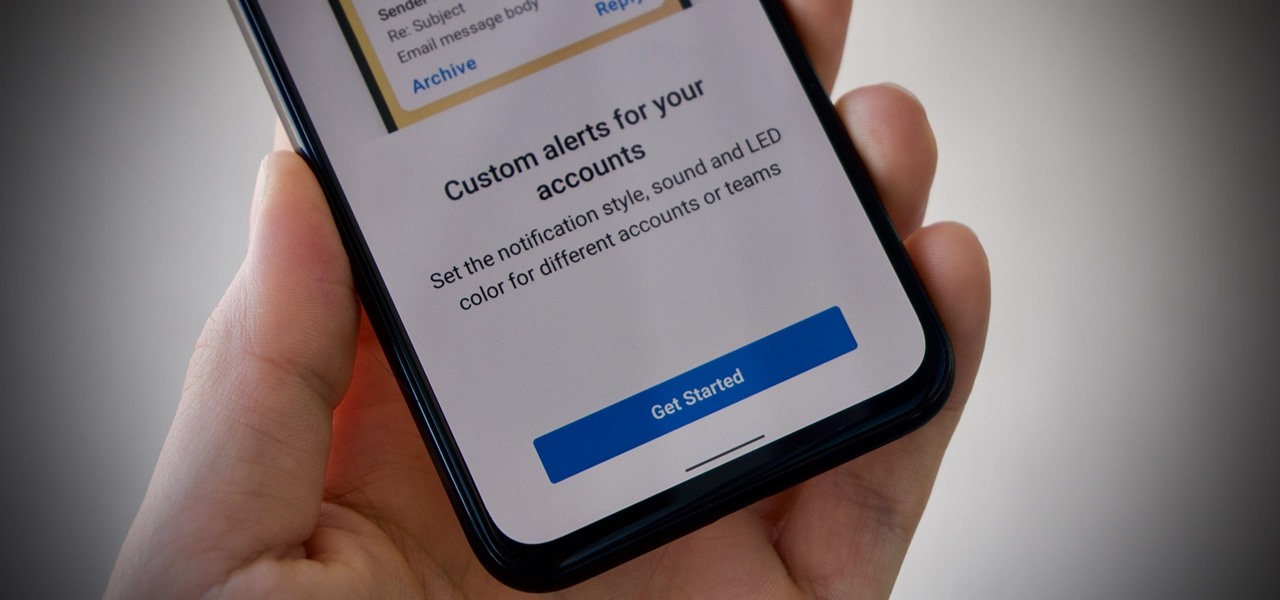
Android is all about customization. That's why it's entirely appropriate that Spark for Android's newest update adds a ton of customization options for your out-of-control email alerts. Now, you can add lights, sounds, and vibrations to notifications, and you can even set specific settings for all of your email accounts.
Most of us have had a cloud-connected address book for years now. The result of this is an ever-growing contact list that will continue to get harder to navigate and manage. With the increased size of our contact lists, it becomes more important to sort contacts in a way that works best for us.

Apple's Mail app has always been a stylish yet simple way to check and send emails. Third-party apps up the ante with powerful tools and features to help keep junk and spam mail out of your eyesight. But with iOS 13, you don't need them since Apple gave the Mail app some much-needed superpowers. One of those being the ability to block senders from emailing you.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

Samsung just announced the Galaxy S10 lineup, but we already knew each device's every nook and cranny. Thanks to leaks and hands-on demos, we know the OEM kept the coveted headphone jack, but omitted one treasured feature in its place — the notification LED. Why did Samsung strip the S10 of this light, and can users expect something to replace it?

A relay is an electrical component that works like a light switch, where it's turned on or off with an electrical signal. By connecting a relay to a Wi-Fi connected microcontroller like an ESP8266, you can build a connected switch that can be controlled from the web browser of any device connected to the same Wi-Fi network — all for just a couple of dollars.

In the realm of internet security, it's becoming clear that augmented reality is not immune to the increasing wave data breaches plaguing users.

If your iPhone XS or XS Max has been suffering from Wi-Fi connectivity and charging issues, Apple just released iOS 12.0.1 on Monday, Oct. 8, as an over-the-air update for all compatible iPhones. The main focus of the update is to give fixes for users going through "Chargegate" and experiencing Wi-Fi issues.

Hackers and makers are often grouped under the same label. While hackers draw on computer science skills to write programs and find bugs, makers use electrical engineering to create hardware prototypes from microprocessor boards like the Arduino. We'll exercise both sets of skills to program a $6 NodeMCU to display the status of a Wi-Fi link via an LED, allowing us to monitor for jamming attacks.

The one thing that separates a script kiddy from a legitimate hacker or security professional is the ability to program. Script kiddies use other people's tools, while hackers and security pros write their own tools. To that end, we're going to see how a stack overflow vulnerability allows us to flood a variable with enough input to overwrite the instruction pointer with our own commands.

The Essential Phone didn't have a hot start when it was released back in August. A delayed release, poor camera performance, and high price tag led many to avoid the otherwise well-received device. But after a few software updates and price drops, it's now a steal of a deal.

Instagram can be pretty exact when it comes to where you are located. That's why, sometimes, it's best never to geotag your precise location, but a broader area where you are less likely to get, well, um ... stalked?

With the British exit from the European Union looming, the UK is looking to the auto industry to help boost their economy and secure jobs through the upcoming years. Today, Business Secretary Greg Clark and Transport Minister John Hayes announced the government investment of $136.7 million (£109.7 million) across 38 different automobile projects, as a part of the Plan for Britain.

Japan is in the process of curbing its aging population and mature workforce. According to The Diplomat, the country's population has been declining at a steady rate. To meet future productivity demands in commercial and industrial sectors, local officials are turning to self-driving technology, including truck platooning, where three or five vehicles travel autonomously in a string formation. This practice, according to a study by MIT, can reduce fuel consumption by up to 20% (more about thi...

We've seen plenty of good, bad, and weird things that have come out of the worldwide augmented reality game Pokémon GO, including murder and location-based bans, but nothing on a large scale. That was, of course, until Iran decided to ban the game country-wide.
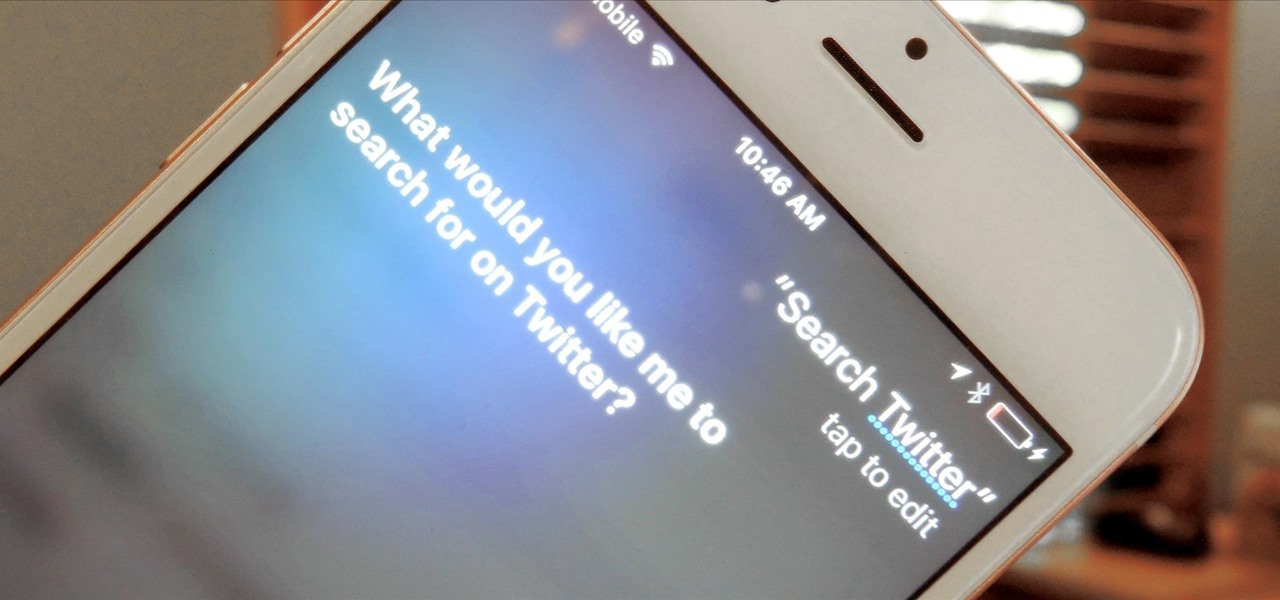
A new iPhone exploit has recently been discovered by YouTube user videosdebarraquito, who has found many other exploits and bugs in iOS over the years. This new exploit allows someone to bypass the lock screen and gain access to contacts and photos via Siri, Apple's digital voice assistant—but it only affects the iPhone 6s and the iPhone 6s Plus because it requires 3D Touch functionality.

In this how-to we will be sending an email with an image we get from a php script after running some fishy code. What you'll need

Unless you've been living under a rock or ignoring recent news headlines, Ashley Madison, the dating site for married people (or individuals in a committed relationship) has recently been hacked. Millions of their users are shitting their pants, and for good reason, as all of those accounts have just been leaked.

Welcome back, my novice hackers! Episode 6 of Mr. Robot has come and gone and, as usual, it did not disappoint. Once again, our hero, Elliot, has used his extraordinary intellect and hacking skills to awe and inspire us.

We previously showed you how to make your Android's LED notification light dance to music, but the app itself was limited in customization options, the devices it worked on, and the music apps and services it worked with. Now we'll be showing you a similar app that supports more music services and lets you select which colors will display through the LED.

In the wake of the NSA scandal and celebrity-photo hacks, lots of people scrambled to find more-secure ways to send text messages, share emails, and surf the internet. Known for their incredibly secure data networks, Germany's email services saw a remarkable increase in new users from across the world. Last year, we covered Sicher, a German app that lets you send and receive encrypted self-destructing messages on your smartphone.
Getting caught using your iPhone at school or work (when you're using it for personal reasons) can be a little bit embarrassing. Even worse, it can be detrimental to how you're perceived by your teacher or boss. But sometimes you just have to beat that next level of Candy Crush, view a risqué photo on Snapchat, or send an important WhatsApp message.

I can be pretty forgetful. If there's something important to remember, I need to jot it down right away or risk losing it forever.

Welcome back, my tenderfoot hackers! So many readers in the Null Byte community have been asking me questions about evading detection and hacking undetected that I decided to start a new series on digital forensics.

Spam emails are emails that are sent to you without your permission. They can quickly fill up your email account if you don't do anything about it. Each email server deals with spam in a different way. Gmail is good at separating the spam for you so that you can get rid of it more quickly. It is easy to delete the spam and if you want to take it a little farther, you can get some of the spam to stop coming all together.

When it comes to text documents and spreadsheets, Microsoft Office is the be-all and end-all office suite—but it's not cheap. Paying anywhere from $140 to $400 puts a big dent in your bank account, especially if you're a broke college student eating ramen for breakfast, lunch, and dinner. Something that I wish I would've known about during college is Microsoft's HUP (Home Use Program). With HUP, any employee or student of an organization that has a Microsoft volume license is eligible to purc...

In this article, I'll be continuing my series on microcontrollers. If you haven't read part one, I'd recommend heading over there and reading it!

Android has released a new application called ezNetScan, which is a free app that scans the wireless network you're connected to and gives you a full log of all of the devices connected to that network. This isn't new for smartphone users, let alone Android users. Fing has been around for a while and does practically the same thing that exNetScan does. It gathers information such as the IP and MAC addresses, device vendors, and ISP location. But while Fing is a great program, it does lack a f...

What's your Twitter handle worth? If it's considered "desirable" (aka short and simple), it'll get you around 100 bucks, or, if you prefer, the affections of a teenage girl.

LED throwies are cheery glow-dots you can make in seconds from simple components and stick to any ferro-magnetic surface. But that's just the beginning — here's how to hack and modify them.
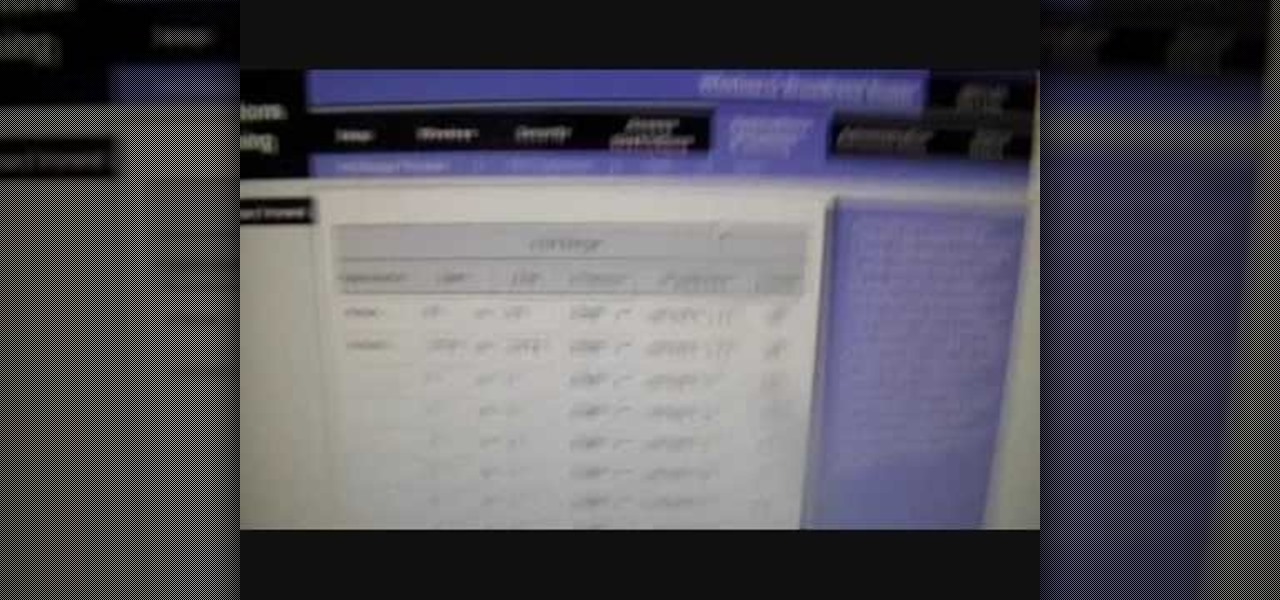
This is a Computers & Programming video tutorial where you will learn how to change your NAT to OPEN with a Linksys router. Go to your browser and type in 192. 168. 1. 1 and that will take you to the basic set up. The authentication dialog box comes up. Type in ‘admin’ for the username as well as the password. These are default settings. In the Linksys page, go to ‘applications and gaming’ and on the Port Range page fed in these information. Your application you can name anything. Start 80, E...
Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast.
How to hack Pet Society! Pet Society cheats, tricks, hacks. Watch this video tutorial to learn how to hack paw points and EXP in Pet Society (09/26/09).

This is a great solution if you need to get something off your computer, but you are not home. Want access to your files stored at home? How about hosting a home web server? Static IPs are expensive, if you can even get one. We set up Dynamic DNS instead!

This video includes instructions on how to get your PlayStation Portable (PSP) onto the BGSU wireless network.
There has been an update with the NES emulator, so you have to put the ROMs in the /var/mobile/Media/ROMs/NES folder, and not the /var/root/Media/ROMs/NES folder.