Here you will see how to add a contact to the address book of a Nokia N97. Follow these steps to add a contact to your Nokia M97's address book: From the home screen, tap the "Contacts" icon and then tap "Add New Contact". Enter in the contact information and tap "Done". Tap "Exit" to return to the home screen. To set a contact as one of your favorite contacts, tap "Add to Favorites", and select the contact you wish to add as a favorite. Tap "OK" You can also do things such as add a called ID...
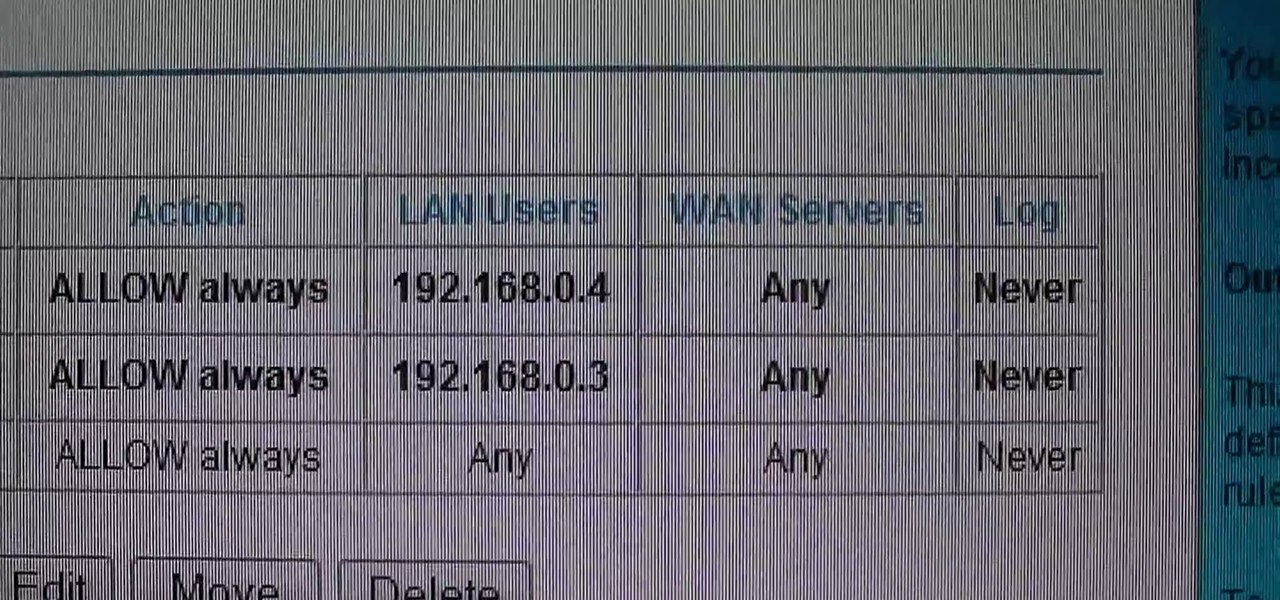
This video shows how to change the NAT type on a PS3. Go to connection settings>network settings>internet connection settings>OK>custom>wired connection>auto detect>manual. Choose an IP address that is different from your router, any other consoles, etc. Click right>automatic>do not use>enable. Press x to save settings, and test your connection. In this example, NAT type is 2. Now go to your PC and open IE. In the address bar, input router IP address, username and password. Go to Firewall Rul...

On your iPhone, your phone number and Apple ID email address are the default ways in which somebody can contact you on FaceTime. While you can't remove your phone number as an option, you can withdraw your Apple ID email account. More importantly, you can add any other email addresses you'd like to the list, so you never have to worry about a friend, family member, or coworker not being able to audio or video chat with you.

Google's personal messaging service Allo could reveal your search history and other private information to friends if the Google Assistant bot is called upon in chats, according to a story from Re/code.

In previous tutorials we have encountered these things called pointers and addresses but we still don't know what they really are. Let's learn a bit more to clear things up.

Over the past decade the Internet community has been witness to the rise of many new forms of online interaction. These new technologies have given rise to anonymous networks (like TOR), black markets within the deep web network (like the Silk Road), and even forms of digital currency, or more accurately crypto-currencies, such as Bitcoin. All of these technological advancements have contributed to securing users around the world and protecting their privacy. Therefore it is no surprise that ...

New to the Ubuntu Linux distribution and interested in setting up an address book for to keep track of your contacts? In this how-to, you'll learn how to make maximum use of the address book built into the Evolution email client. Take a look!

If you're putting your email address online on your own website, or sites like facebook or myspace, you may want to be a bit clever about it. Check out this tutorial and see how to protect your email address from spam.

Check out this video to learn how to search more effectively in the Google Chrome browser. This video will explain how to manually enter keyword searches in Google Chrome and Chromium, which will allow you to search using any engine from the address bar.

Your manuscript is complete, and you have a list of your favorite agents and a strong query letter... but how do you properly address letters to agents? You neither want to be too formal nor too casual - strike the perfect balance.

In this clip, you'll learn how to reinstall an accidentally-deleted system application like TextEdit, Preview, iCal, Address Book or QuickTime without reinstalling OS X. With a little know-how, it's easy. So easy, in fact, that this video guide can offer a complete overview of the process in a matter of a few minutes. For more information, including a complete demonstration and detailed, step-by-step instructions, watch this home-computing how-to from MacMost.

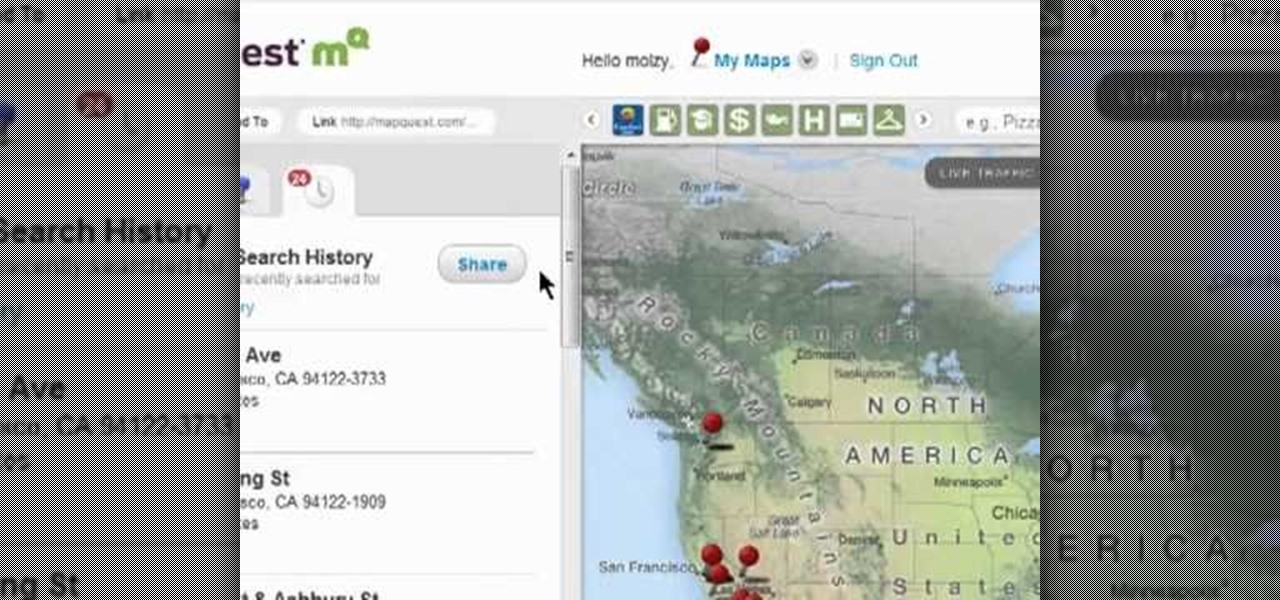
In this clip, you'll learn how to view the list of your previously searched addresses on MapQuest Maps. It's easy. So easy, in fact, that this home-computing how-to can present a complete, step-by-step overview of the process in about two minutes. For more information, including detailed, step-by-step instructions, take a look.

Need some help figuring out what your IP address is? It's easy. And this brief video tutorial from the folks at Butterscotch will teach you everything you need to know. For more information, including detailed, step-by-step instructions, and to discover your own IP address, take a look.

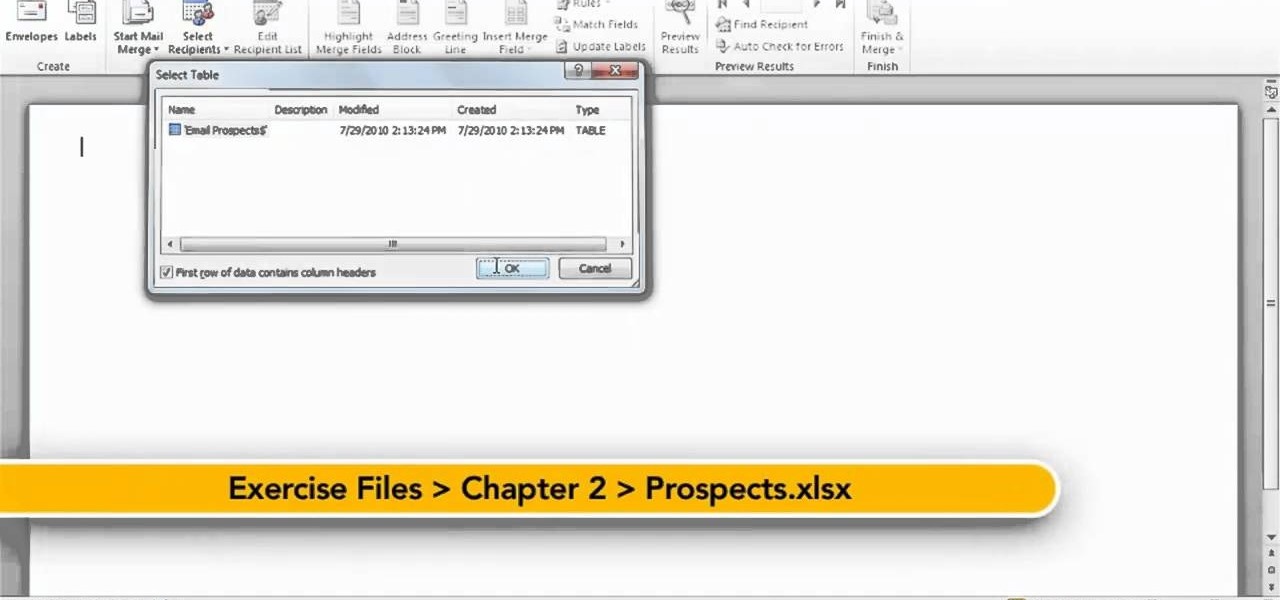
In this quick clip, you'll learn how to insert address blocks and merge fields when using Mail Merge within Microsoft Office Word 2010. Whether you're new to Microsoft's popular word processing application or a seasoned professional merely looking to pick up a few new tips and tricks, you're sure to benefit from this video tutorial. For complete instructions, take a look.

Trying to find your friend's Yahoo! mail address so you can send them a letter or tell them about a cool new website you found? Yahoo! directory makes it easy to find someone you're looking for. All you need is is their name.

Want to get involved with the information superhighway? E-mail is the best technology to stay connected with friends and family. Use these tips to create your own email account in Gmail, MSN or Yahoo! mail. Keep track of addresses, improve your networking and learn the basics of instant messaging.

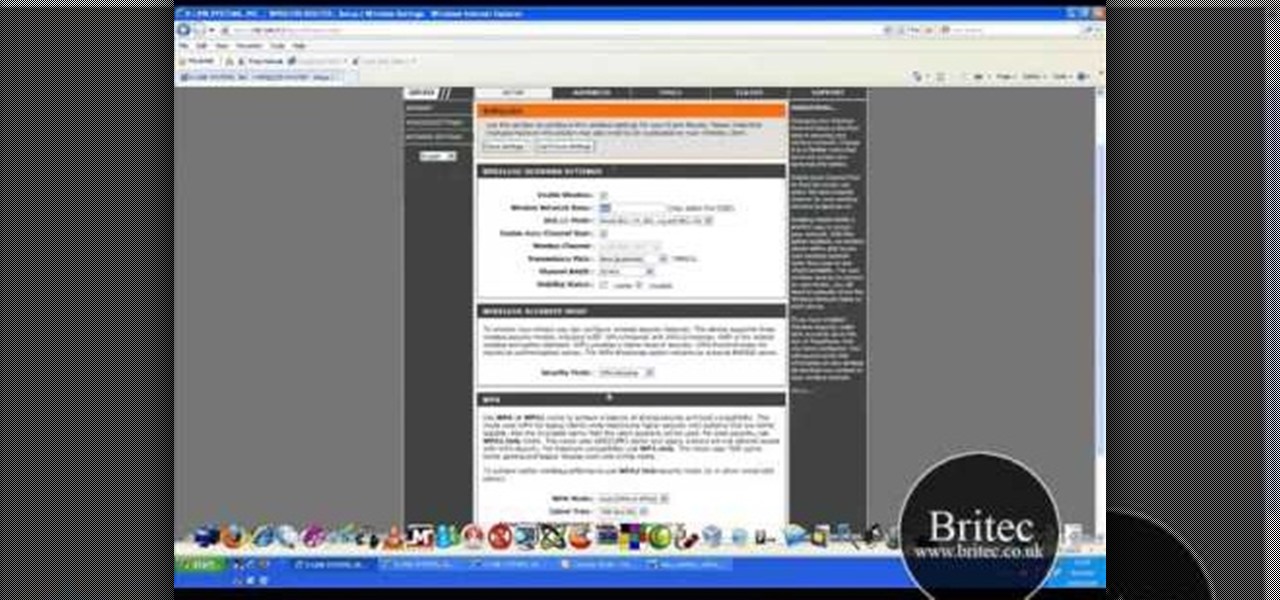
In this tutorial, Brian teaches us how to make your wireless network secure. First, go to the start menu, then go to run and type in "cmd", then type in "iconfig /all". Now a new window will pop up and you will look for the default gateway. Find the IP address to log onto the routers you have. Now, type in your IP address into your address bar on your internet browser. You will be asked to log into your account with your password and user name, which you can find at the manufacturers website....

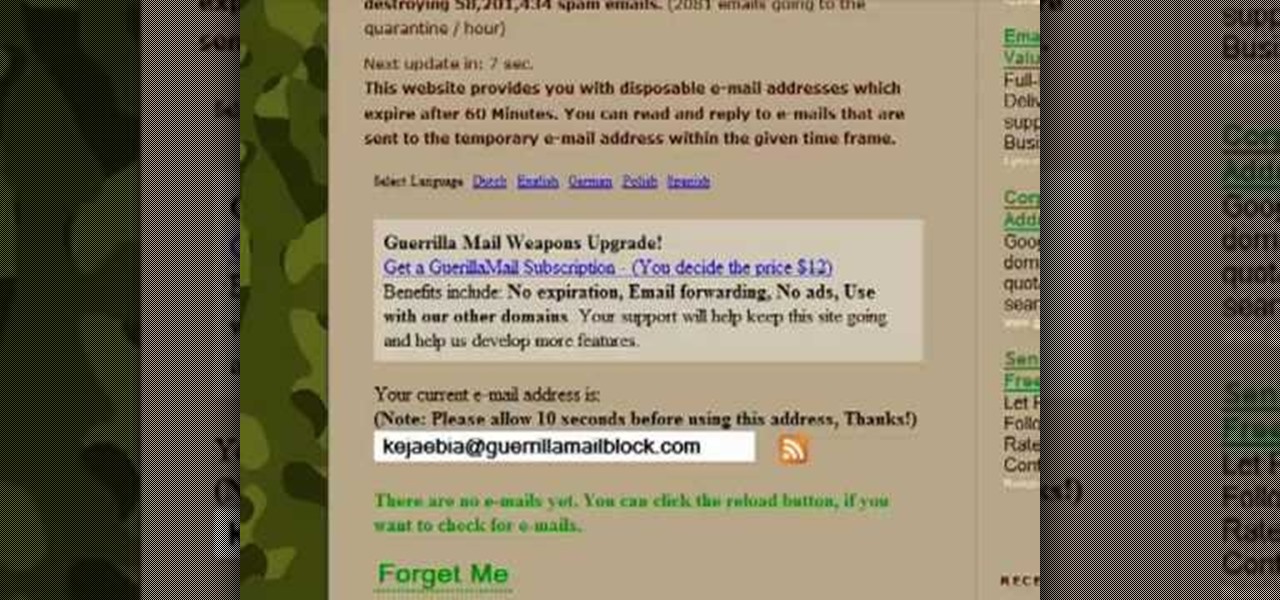
Thwart would-be spammers by creating temporary, disposable email addresses at GuerillaMail. This clip will show you how it's done. It's simple! So simple, in fact, that this home-computing how-to can present a complete, step-by-step overview of the process in about two minutes. For more information, including complete, step-by-step instructions, take a look.

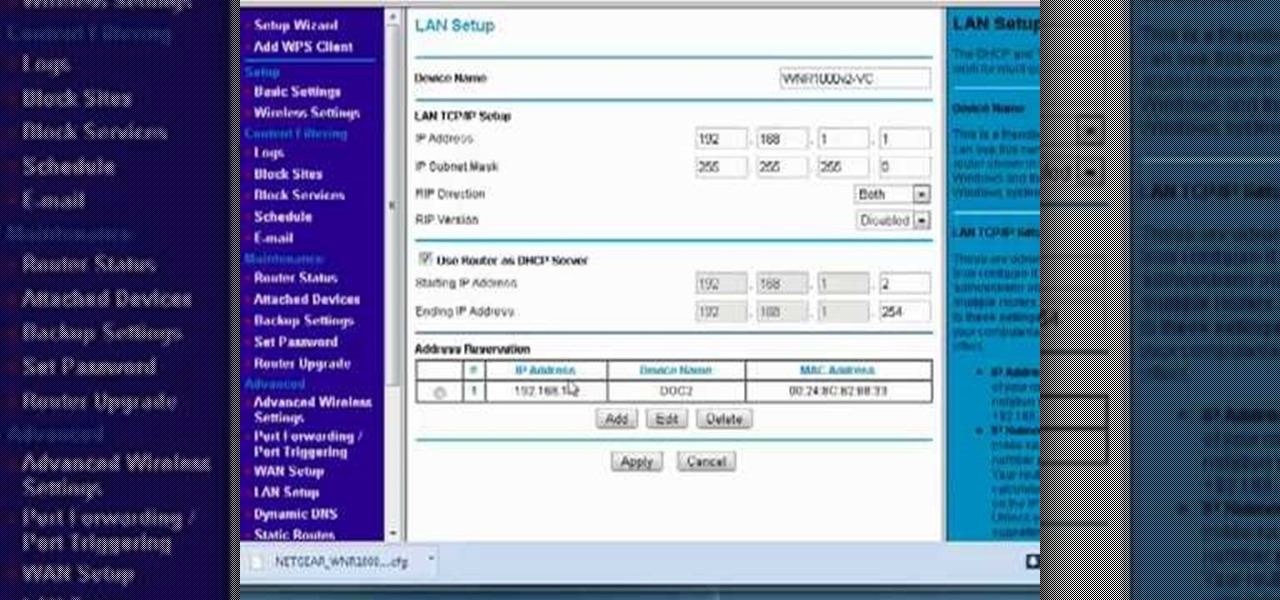
Interested in reserving a specific IP address on your Netgear wireless router? This clip will show you how it's done. It's simple! So simple, in fact, that this home-computing how-to can present a complete, step-by-step overview of the process in just over three minutes. For more information, including complete, step-by-step instructions, take a look.

In this video tutorial, viewers learn how to get more room in a web browser. Users will need to use the Mozilla Firefox web browser. Begin by going to the Firefox add-on website and search for "status address bar". Then click on Add to Firefox to install the add-on. Once installed, any link that is moused over will appear in the address bar. This means that users are able to hide the address bar clicking on View and deselecting Status-bar. This video will benefit hose viewers who use the Mozi...

How to Use COD4 Cracked Servers.

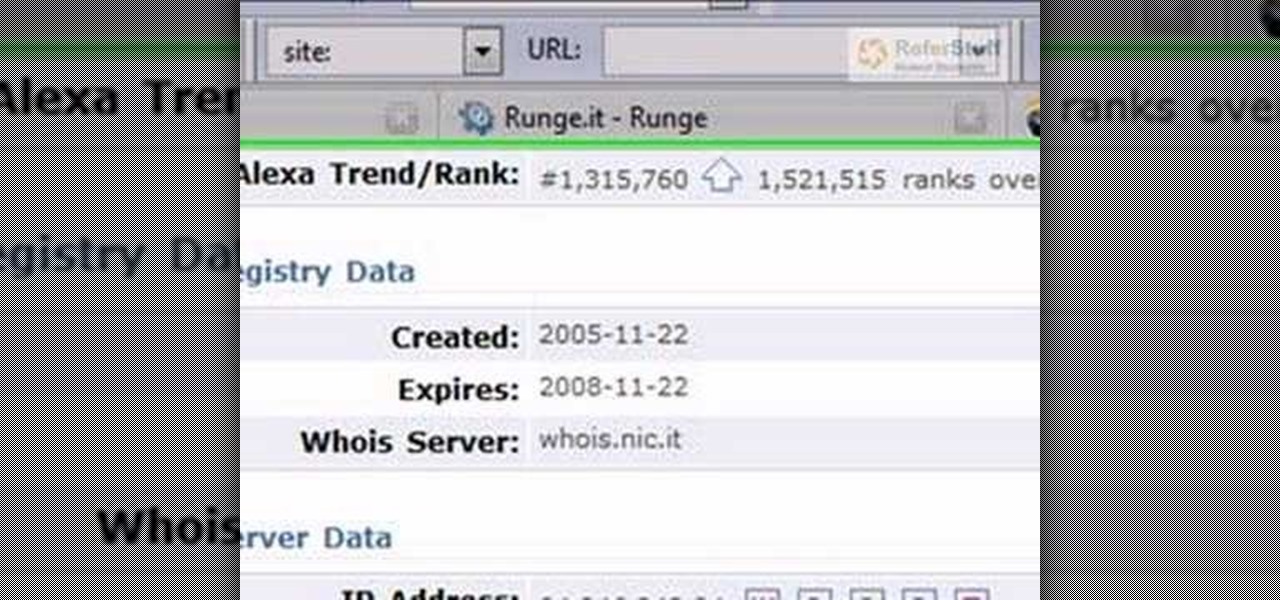
In this video from richardfallah we learn how to track a scam email. You can tell a scam from an email that looks a bit funny. So if it's an email that looks like it's from Bank of America, you might see a link to click that actually would take you to another site which is an exact clone of the Bank of America website, but it has a different web address. This is NOT Bank of America! They will try to steal all of your information if you type in your personal information. Whois is a great tool ...

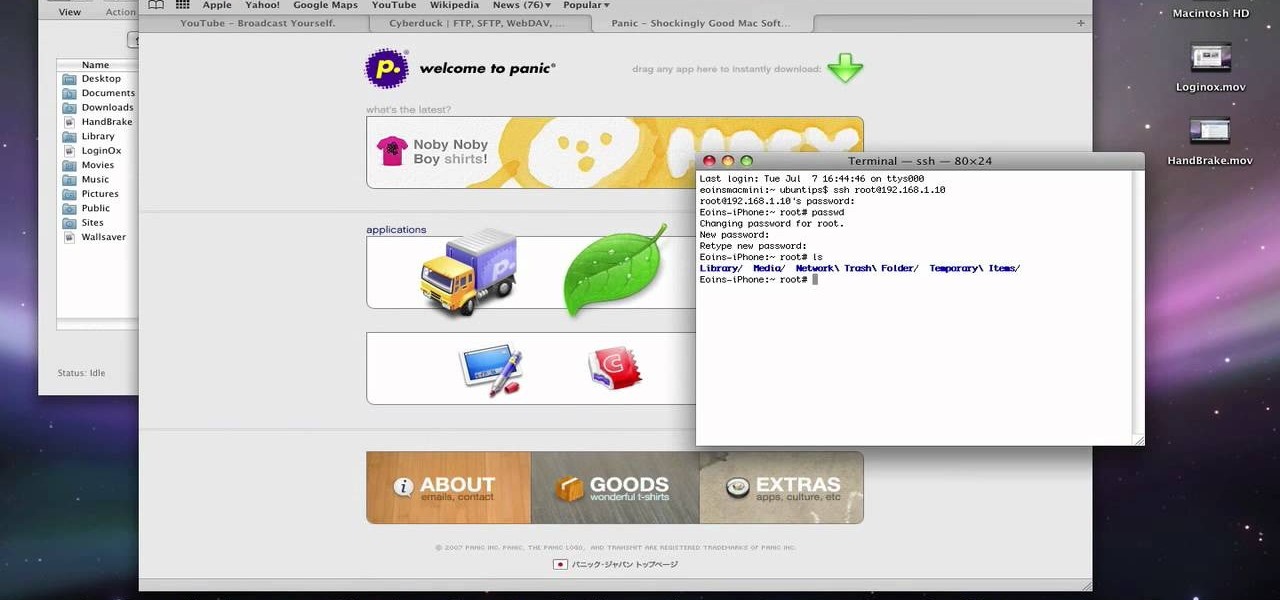
This video describes about accessing an iPhone in Ubuntu using open SSH, cyber-duck, Netatalk. For accessing using SSH, make sure your iPhone's Wi-Fi connectivity is on. Now open your terminal and type "SSH root@'address'". Here address refers to the IP address of your iPhone. You have to type a password to access the iPhone contents. Once you are authenticated type "ls" and you will be shown with the contents of the iPhone. The second method is using cyber-duck. In it, choose SFTP as the con...

If you're feeling unappreciated, underwhelmed, or just plain trapped, taking some time off may help.

Herbert Midgley, the Internet Legend, shows you how to text message to an email address! Need to email someone back, but don't have internet or email on your phone? This is a clever way to send emails to people using sms text messaging. Communication has never been easier.

Learn to create a script in Windows XP that will find the IP address of a network PC.

If you use Apple's email services and the "From:" field in your iPhone's Mail app is cluttered with @Mac.com, @Me.com, and @iCloud.com variations of the same address — along with third-party accounts — there's an easy way to declutter things and hide the addresses you don't use anymore.

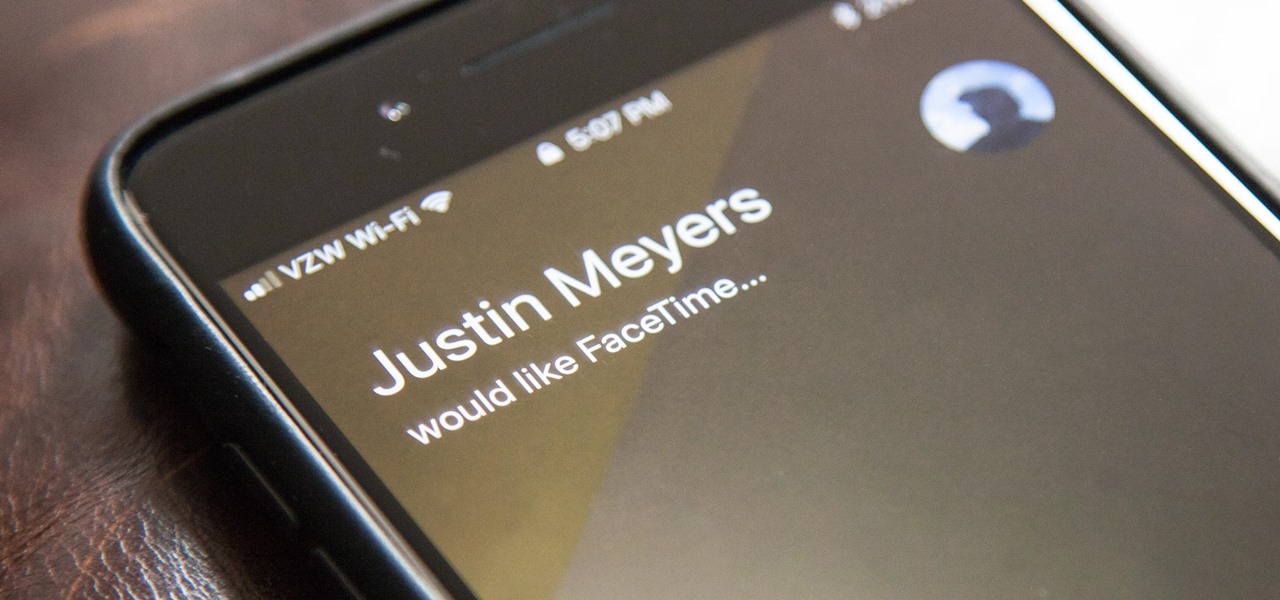
Whenever you make FaceTime audio or video calls from your iPhone, Apple automatically uses your phone number or Apple ID email address as the caller identification. So when someone that you're calling sees the incoming call, they'll see it's from your phone number or email address. But what if you'd rather it be a different identifier?

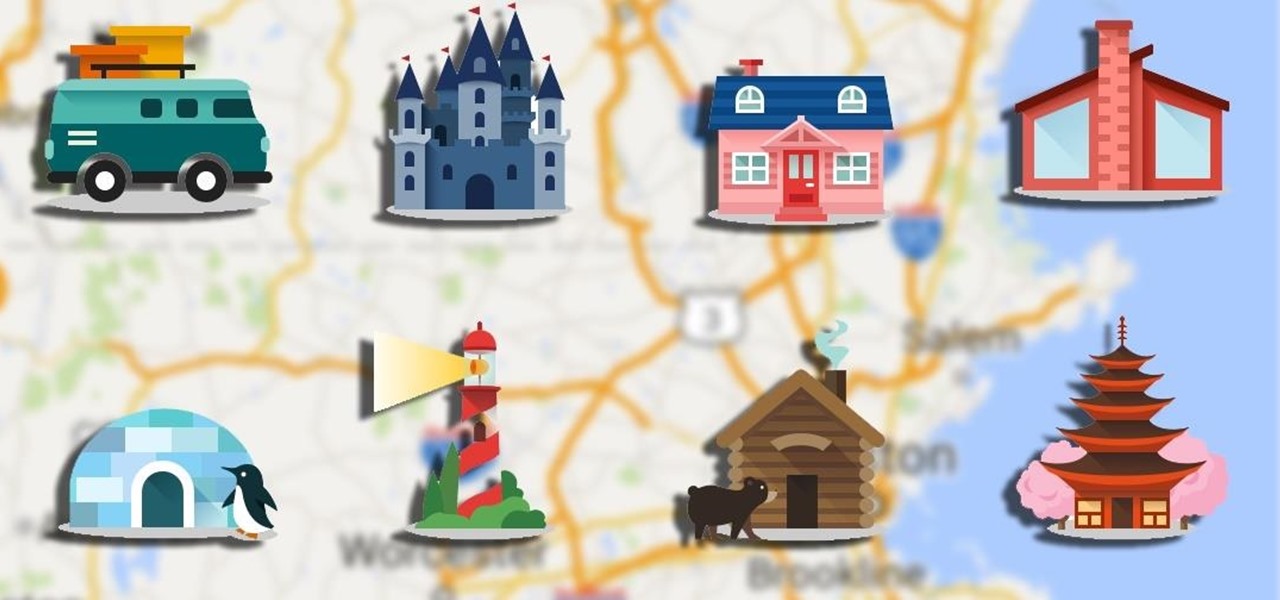
If you're using an up-to-date version of Google Maps on your Android device, there's a little-known feature you can use to apply stickers to saved places, making them visually easier to find while you're looking at the map.

In most cases, when the free trial of software is over, that's it—you're left to either pay for it or find an alternative. But what happens if the trial wasn't long enough to sell you on the product? It'd be nice if there was a way to test it out again without having to whip out your credit card.

I rarely receive spam mail, but every now and then I’ll get an email from Cat Fancy Magazine. I’ve never read an issue of Cat Fancy Magazine or been to their website. Actually, I’m allergic to cats. So how did they manage to get my information?

Want the convenience of a throwaway email address without all the hassle? How about anonymous text messaging so you can get to know someone before giving them your real information? Gliph has you covered. Gliph is a service that lets you create an identity around a set of three to five symbols called "artifacts" instead of your name, phone number, or email address. You choose how much information you reveal, and anytime you communicate with someone else who has Gliph, the data is protected us...

In this video we learn how to find your IP address with the Command prompt. First, go to the start menu on your desktop. Then, find the run box and type in "cmd". After this, hit "enter" and then a black command prompt will show up on your screen. Next, type in "ip config" and then hit the enter button again. Now, a list of information will appear on the black screen. Look down the list to find the IP address listed on the page. Once you have this, you should write down your IP address and th...

This is how to hack a computer for educational purposes. First you need its IP address, radmin viewer 3.3 or later, and an open port scanner. Okay so first you need the IP and scan the IP address of the computer. Now find what open port it has. Ok then open up radmin viewer and put in the IP address and open the port you found. Now right click after you enter the computer's IP address and the open port. Select full control or view only and there you go. The computer has been successfully hack...

CC, which stands for "carbon copy", is a familiar phrase in email, but can also be used in business letters and legal documents. This can be especially useful for letters you want to spend up a company or organizational chain, letting each recipient know exactly who else received the same document.

This detailed video series shows you everything you need to do to install an LED lighting gauge cluster in your Volkswagen MK4 (Jetta, Gulf, or GTI). Part 1 starts with disconnecting the battery, Part 2 has you remove the interior cluster, Part 3 you disassemble the instrument cluster, Part 4 covers LED ring installations, Part 5 goes over the interface removal, Part 6 covers the gauge face installation, Part 7 is 6 videos long (video 7 to 12) covering preparation for installing the cluster, ...

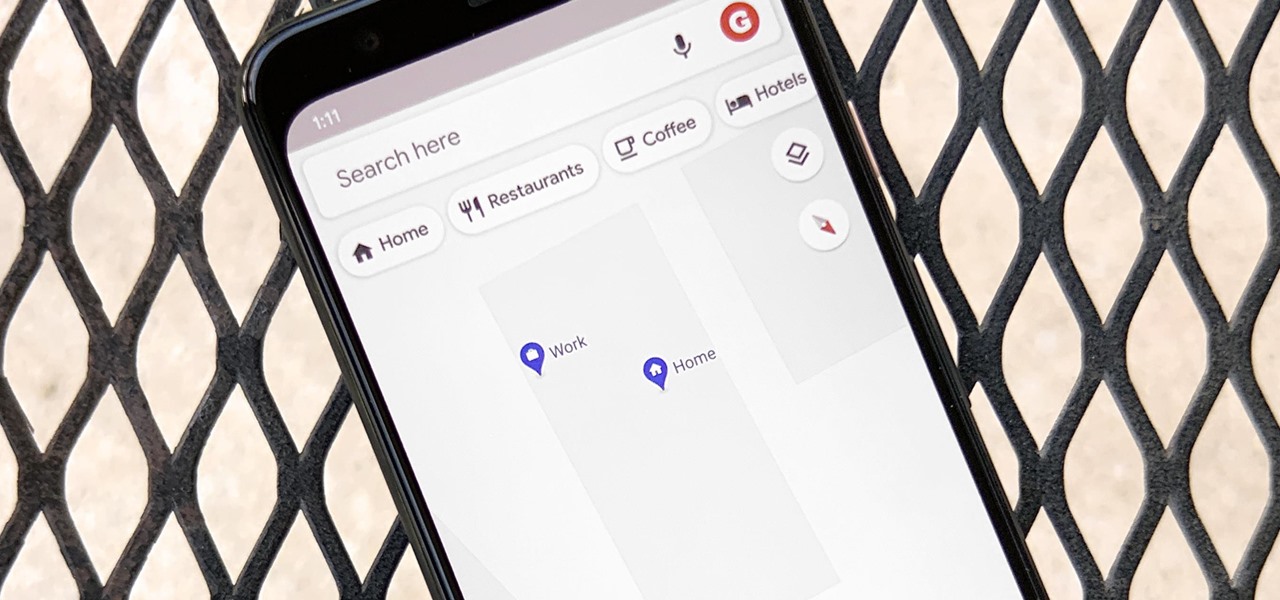
Google Maps lets you set home and work locations for quick access to navigation. In fact, these two locations are so central to the Maps experience that if you don't have both saved, the app can be a little naggy about it. But if you work from home, there's just one address to use, so what are you supposed to do?

For anyone interested in using cheap, Wi-Fi-connected microcontrollers like the ESP8266, the Arduino programming language can be a barrier to entry. Based on C++, Arduino requires knowledge of more computer science than languages like Python. Fortunately for beginners, setting up MicroPython on an ESP8266 allows anyone to write Python on affordable microcontrollers in a matter of minutes.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

Whether you're white hat, black hat, or some shade in-between, navigating through a network is a core part of hacking. To do that, we need to be able to explore a network to discover the addresses of gateways, interfaces, and other attached devices. When ifconfig just isn't enough, you can steer your way around a network with a convenient tool called Ship, the script for everything IP.