Want to forget about always pulling out your credit card to purchase something on your BlackBerry? There's a little application that can do it all for you? But how? Best Buy has answers. The Best Buy Mobile team explains how to use the BlackBerry Wallet application. This application can store personal information such as credit card information and shipping addresses on a secure website for easy access when shopping online.
Own a BlackBerry Curve 8330? Need a custom ringtone? Best Buy has answers. The Best Buy Mobile team explains how to set custom ringtones for contacts in your address book on the BlackBerry Curve 8330. There are many different ringtones to choose from and you may set a different one for each one of your contacts.

Have you become a Jedi in your Star Wars delusional mind? If so, break out of the the asylum with a Jedi lightsaber. Oh, but you don't have a lightsaber yet, okay. Well, this video tutorial will show you how to make a very inexpensive LED light saber with the most basic parts you could find. Novastar will shares his Jedi wisdom on LED light sabers, so pay attention, or you could never get out of that loony bin.

Big business is on the web these days and you don't have to build a shopping website or blog to get involved.

Want to learn how to play Led Zeppelin on the guitar? With this three parttutorial you can learn how to play "Stairway to Heaven" by Led Zeppelin on the acoustic guitar. This version is a simplified version of the song and is not exactly how Led Zeppelin plays it. This lesson is geared towards intermediate guitarists because it assumes prior knowledge of guitar playing. Watch this how to video and you will be able to sing and play along to "Stairway to Heaven" by Led Zeppelin.

An incredible amount of devices use Bluetooth or Bluetooth Low Energy to communicate. These devices rarely have their radios switched off, and in some cases, are deliberately used as trackers for lost items. While Bluetooth devices support MAC address randomization, many manufacturers do not use it, allowing us to use tools like Bettercap to scan for and track Bluetooth devices.

ARP spoofing is an attack against an Ethernet or Wi-Fi network to get between the router and the target user. In an ARP-spoofing attack, messages meant for the target are sent to the attacker instead, allowing the attacker to spy on, deny service to, or man-in-the-middle a target. One of the most popular tools for performing this attack is Ettercap, which comes preinstalled on Kali Linux.

When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.

Format strings are a handy way for programmers to whip up a string from several variables. They are designed to save the programmer time and allow their code to look much cleaner. Unbeknownst to some programmers, format strings can also be used by an attacker to compromise their entire program. In this guide, we are going to look at just how we can use a format string to exploit a running program.

Sometimes you need a password to gain access to an older running Windows system. Maybe it's a machine in your basement you forgot about or a locked machine that belonged to a disgruntled employee. Maybe you just want to try out your pentesting skills.

Hello, this is my first post on Null-Byte. This is made for those who have an interest in writing into another processes memory. Why would you want to do this? Who knows, personally I just wanted to mess around with games on my computer(have unlimited health).

What's up readers? Today I'll be introducing to you a new vulnerability called the Format String vulnerability (in case you missed the title). It won't be much, just a little motivation to keep you guys going. A little teaser, if you may.

Man-in-the-Middle attacks can prove to be very useful, they allow us to do many things, such as monitoring, injection, and recon.

Doxing is the act of finding one's personal information through research and discovery, with little to no information to start with. You may have seen doxing in the news, for instance when not so long ago, hacker team Anonymous doxed and reported thousands of twitter accounts related to ISIS. Doxing can be useful for finding the address of a coworker, or simply investigating people on the internet. The tutorial I will provide to you now will teach you the basics of doxing and how you can prot...

Welcome back, my novice hackers! Reconnaissance is one of the most important preparatory steps to hacking. As I have emphasized many times before here on Null Byte, you must know the operating system, the ports, the services, the applications, and sometimes even the language of the target to be effective. If you haven't taken the time to gather this info, then you are likely wasting your time.

Welcome back, my hacker novitiates! Finding vulnerabilities in systems can be one of the most time-consuming tasks for a hacker. There will be times, though, when you'll find yourself in a position that you know that a particular port represents a vulnerable application or service.

Welcome back, my hacker apprentices! My recent posts here in Null Byte have been very technical in nature, so I thought that I'd have a little fun with this one.

Newsletters, subscriptions, and receipts are all necessary evils that come along with online services and shopping, and they take up a significant amount of space in a lot of people's inboxes. If you've ever signed up for an account on a website, chances are you've gotten an email from them.

Spammers are the bane of every email user. No matter what you do, junk mail always breaks through the spam filters. And some of the best ones seem to come from legit companies, and that's because they aren't legit companies— they're spammers masquerading as legit companies.

Your XBox 360 is a big part of you life. Probably about as big as your significant other. Make it your own by giving it some sweet case mods! This video will show you how to cut a window into the side of your console, install blue LED lights in it, and paint it. If you are one of those lucky XBox 360 owners whose real friends come see them sometimes, they will surely be impressed by this impressive mod.

If you have any Google applications, like Gmail or Google Calendar, that you want to sync to your new Android enabled mobile phone, it's a simple task to complete. There's nothing hard about it, but if you think you need help, Best Buy has answers. The Best Buy Mobile team explains how simple it is to sync Google apps with your Android cell phone.

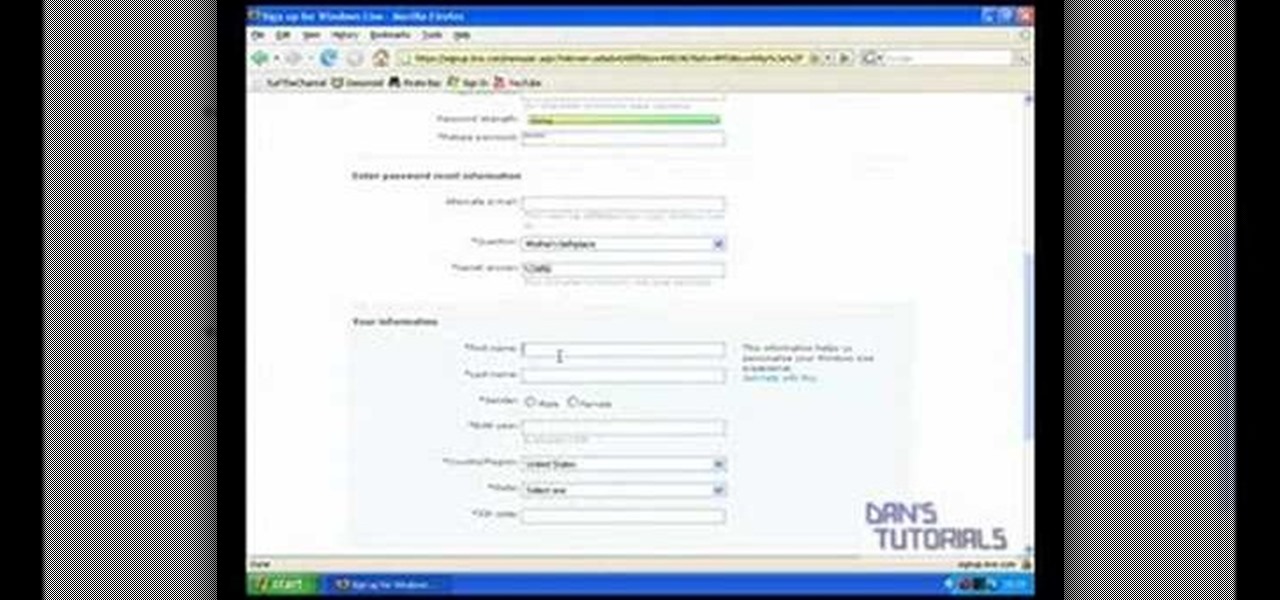
This tutorial shows how to create an email account in Windows Live. Use Google search to find the Windows Live Hotmail page. When you get to that page, click on the button that says, "Get it Free". On the next page, you can choose your email address, ending with either @live.com or @hotmail.com. If the email address is already in use, pick something else or add some numbers. Next, choose a password. There is a bar that shows how strong your password is. You can set a security question that ca...

The often-requested men's styling for salsa dancing has arrived! Once you have a solid basis for your cross body leads, the next step is to be able to do variations of it. In this salsa video, we teach ways to spice up your salsa by adding style to your cross body leads. Anthony will teach you how to do a monkey move and a hook step into a cross body lead, and at the end how to add a shimmy.

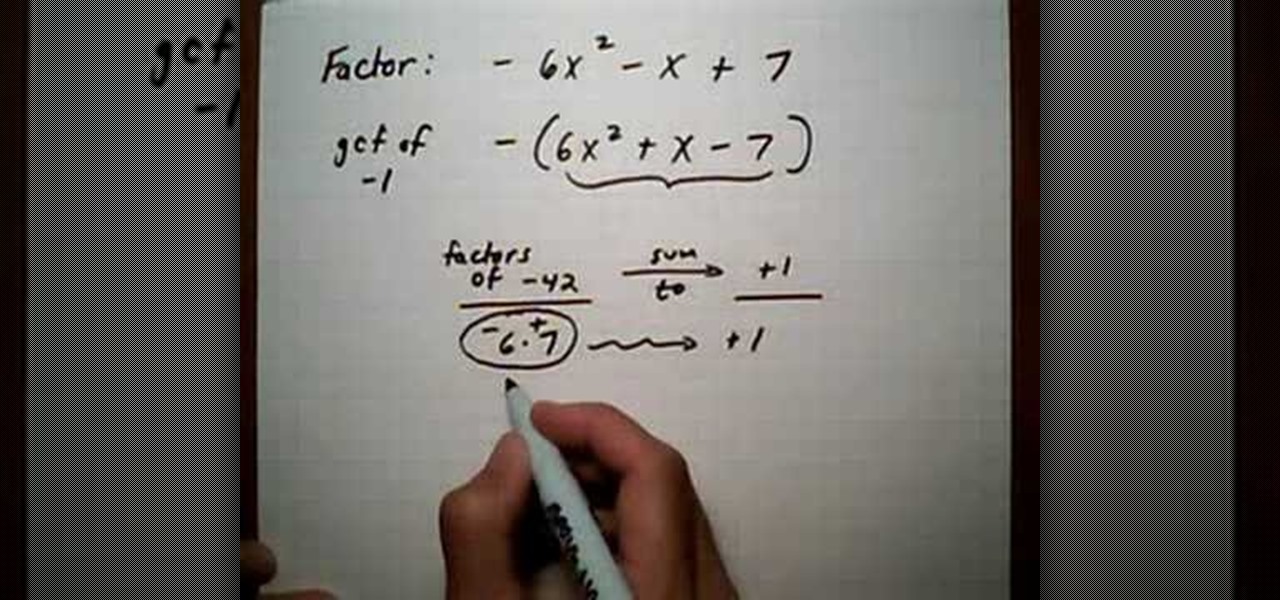
In this video the instructor shows how to factor a trinomial with negative leading coefficient. Most of the students are confused when they have to factor a trinomial with a negative leading coefficient. But there are many ways to solve these kind of problems as shown in this video. One way you can do is that take out the greatest common factor (GCF) of -1 from the equation. So pulling the -1 gives you the original trinomial with all the signs of the terms changed. Now go on and factor the ne...

This video by makemagazine demonstrates a weekend project on how to make a LED light brick. The materials required for this project are listed on the link to the make magazine page in the info box or it can be orders as a kit from the make magazine store. Take the PCB (printed circuit board) and first solder the Resisters and Capacitors as shown. Next test the LEDs and separate them using a button cell batteries. Solder the LED, PIC micro-controller, DC power connector and tilt switch followi...

• Start by warming and relaxing the lower back of the person you are looking to massage. Warm some massage oil in your hands, and spread it evenly over their lower back.

It might seem easy to a few, but some of us out there grew up with email and consider "the letter" an artifact. However, writing a letter is the ultimate in class and shows someone you took the extra time to get in touch with them. Whether you are writing a business letter or a friendly letter, these tips will guide you in properly writing that letter to a special someone, friend, or client.

Want to mix and scratch like a professional DJ? To be a good DJ you need to understand the concepts of mixing tracks, adding cool effects, and of course you need a good sense of rhythm to line up the beats. This how to video explains how you can use the KAM LED Swingfire sound to light unit. This demonstration shows you how to optimize its performance. With 63 LED's, 7 lenses, and sound to light, watch the beams of light as the instructor controls the lights with some funky music. Watch this ...

Want to play lead guitar in a rock band? Well first you have to learn techniques from the masters. This guitar lesson teaches you how to play the riff from "Misty Mountain Hop" by Led Zeppelin. Once you get a hang of these popular guitar chords and tunes, you can start incorporating them into your own songs. With this lesson and a bit of practice you will be able to play "Misty Mountain Hop" by Led Zeppelin on the guitar. The next time you are with your friends you can impress them by whippin...

Check out this home repair tutorial video that demonstrates how to repair a lead on a Dyson vacuum cleaner. After a long period of time, the lead will get metal fatigue within it and the machine will work intermittently. Follow the step by step instructions in this domestic appliance repair video to properly troubleshoot the Dyson vacuum's switch unit. Please note that all work should be performed by a qualified person. Make sure to take the necessary precautions to ensure a safe repair of yo...

In this tutorial, we learn how to solder a 0603 LED. First you will get a business card or card with a piece of masking tap. Then, place our LED on the masking tape and apply posts to it. From here, you will apply some solder to the LED as well. Make sure you apply enough pressure to the LED so it will not pop up. Use just small touch of solder and put it on the top of the iron. Touch both sides of the contact and you will have enough solder on the LED. This will finished your soldering, just...

Take a lesson in architecture from renowned architect Doug Patt by watching this video tutorial. If you want to learn about drawing and designing, without going to school, Doug's just the teacher. Watch to see how to design and draw with lead like an architect.

Playing popular songs on the guitar is not as difficult as it seems. With this tutorial you can learn how to play "Stairway to Heaven" by Led Zeppelin on the electric guitar. This lesson is geared towards intermediate guitarists because it assumes prior knowledge of guitar playing. This lesson covers the finger picking as well as the chord structure for "Stairway to Heaven." Watch this how to video and you will be able to sing and play "Stairway to Heaven" by Led Zeppelin.

RC Car Action Magazine Editor Kevin Hetmanski shows us how the pros shorten servo leads. Sometimes the servo leads come to long, so trimming them better suits the need. Watch this video tutorial and learn how to shorten servo leads on an RC car.

Even though Samsung has features like the always-on display, you still might miss some notifications now that the alert LED is gone. But baked in One UI is the ability to turn the rear camera flash into a notification LED. Any incoming alerts or calls will cause the camera LED to blink, so you won't miss a thing.

Businesses leave paper trails for nearly every activity they do, making it easy for a hacker or researcher to dig up everything from business licenses to a CEO's signature if they know where to look. To do this, we'll dig into the databases of government organizations and private companies to learn everything we can about businesses and the people behind them.

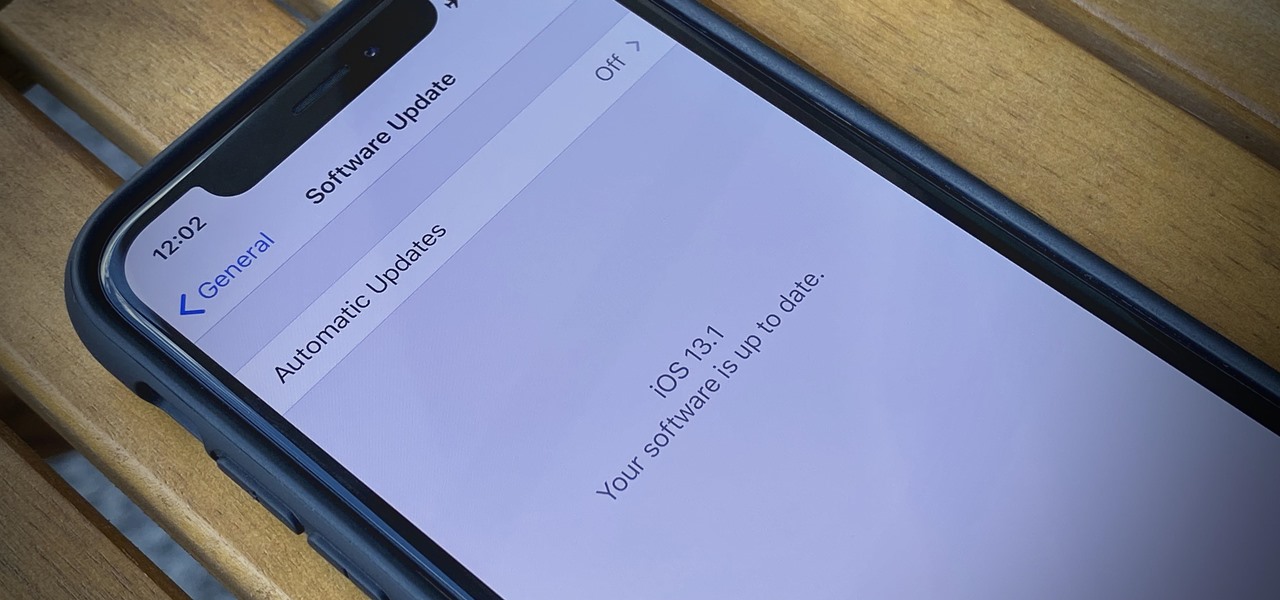
If you're still working your way through the hundreds of features and changes that iOS 13 brings to your iPhone, you might be a bit surprised to learn that your device is now out of date. While Apple only dropped the big update for iPhones on Thursday, Sept. 19, the company has already released its successor. All iOS 13-compatible iPhones can now update to iOS 13.1, out today, Tuesday, Sept. 24.

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.

Over the last few years, the virtual reality space has earned a welcome reputation for fostering better representational balance with regard to gender compared to the general tech industry, with women like Nonny de la Peña and many others leading the charge.

In the world of technology, there's often a trade-off between convenience and security. The Java Remote Method Invocation is a system where that trade-off is all too real. The ability for a program written in Java to communicate with another program remotely can greatly extend the usability of an app, but it can also open up critical vulnerabilities that allow it to be compromised by an attacker.