A new study published on April 12 in Medscape gives us an update on the Hantavirus genus of pathogens, which spread viruses via rodents that can cause fatal diseases in humans, such as hantavirus pulmonary syndrome (HPS).

It be would the ideal morning commute—sit back, drink some coffee, and read the news as your car drives you to your destination. That reality isn't quite here yet, but Cadillac is offering something close with "Super Cruise" on the CT6.

It may seem strange to find the director of engineering at a question-and-answer site all of a sudden pick up and lead a new driverless startup, but to Kah Seng Tay, both engineering tasks require building the right infrastructure to handle large amounts of AI data.

For all of its drama, Uber's driverless program has states like Arizona excited for the future of self-driving vehicles. But it's not Arizona alone that supports the driverless craze; the Illinois House of Representatives will hear a bill that would allow driverless cars on the road with or without human operators.
As a society, we seem to be moving backwards toward communicating by pictures only. Emojis and GIFs are today's cave paintings, and I, for one, am totally okay with that. To make this transition even more amazing, photo-editing app Facetune created a tool that lets us change our very own faces into moving emojis.
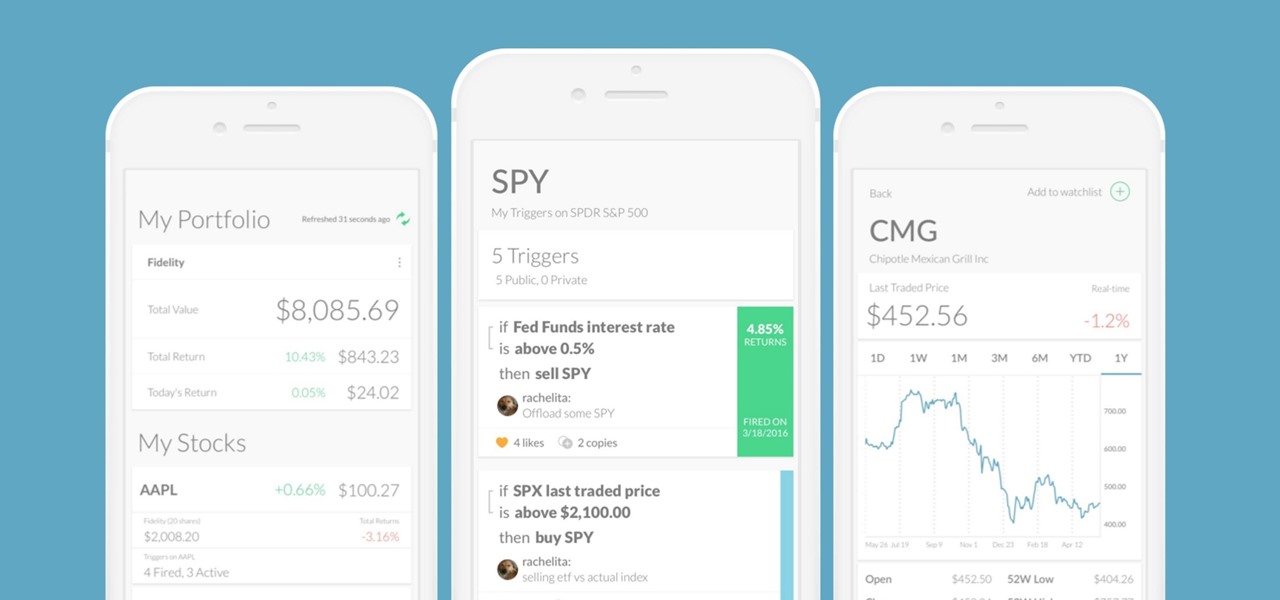
Every time Donald Trump tweets about a stock you own, Trigger Finance, or just Trigger—the app founded on the "if this, then that" rule to track and invest in the stock market—alerts you with a notification for real-time analysis of financial data.

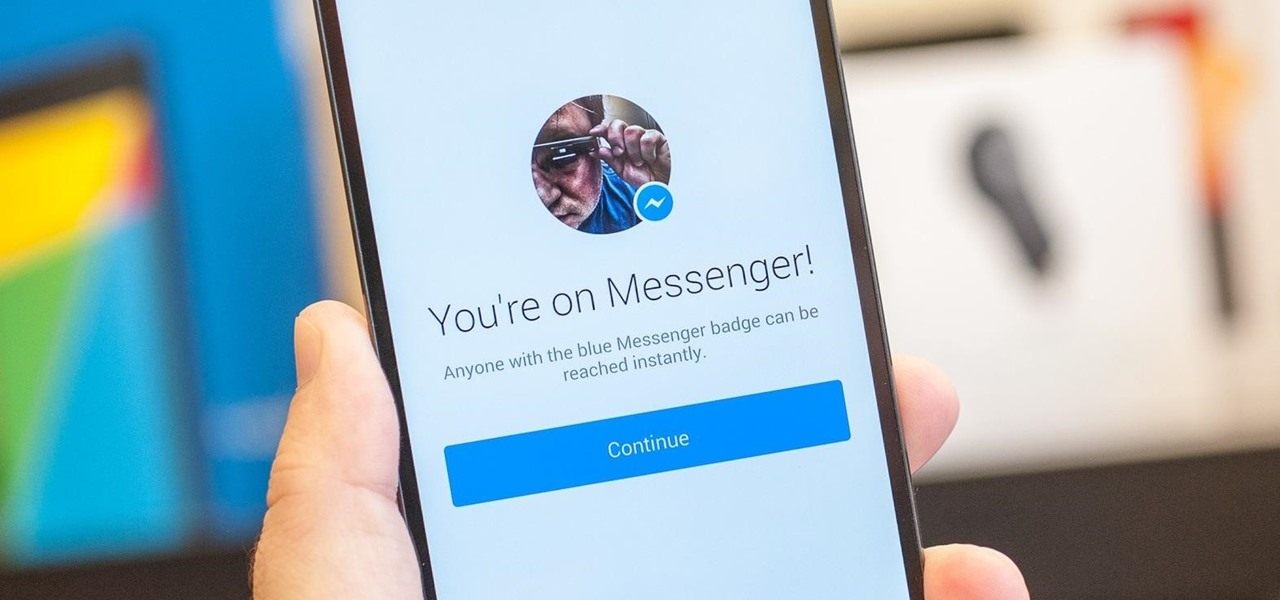
Facebook Messenger has now incorporated a live location sharing feature, one week after Google Maps revealed its own real-time location tool. On Monday, the social media giant announced the new feature, which will allow users to share their live whereabouts with friends at the press of a button.

Baidu Inc, the "Chinese Google" search engine and technology company, which has been actively pursuing self-driving cars, reported that a gang of hackers recently attempted to steal its driverless car technology.

In a press event this past week at the Game Developers Conference in San Francisco, California, Unity Labs, the experimental and forward thinking arm of Unity, announced an upcoming toolset for developers in the augmented, mixed, and virtual reality space called the XR Foundation Toolkit (XRFT).

Sky Zhou, also know as Matrix Inception on YouTube, is no stranger here on NextReality. We loved his Pokémon concept game for HoloLens, as well as his D3D Keyboard that lets HoloLens users leave notes around the house. He just can't seem to stop creating cool mixed reality apps, and he's already got another one in the works.

If you're in the Windows Holographic community of developers, make sure to mark your calendar and set your alarms for February 8, 2017 because it's Windows Developer Day.

Last month, Dr. Sung-Hoon Hong, Vice President of Samsung Electronics, announced at the Virtual Reality Summit in San Diego that Samsung would be moving into the augmented reality market. According to a recently published patent application, that move has begun.

Remember back in 2011–2012 when "Little Talks" by Of Monsters and Men was the bumping new single being played everywhere? Well, thanks to this robot created from a LEGO Mindstorm EV3 kit, and an acoustic guitar, you get to get the iconic "hey!" stuck in your head for the rest of 2017. You're welcome.

People have been transforming mud into art, aka pottery, for thousands of years. This is not a new phenomenon, but often the finished product has a certain utilitarian aesthetic, such as a bowl or vase.

Halloween is this weekend, so if you're looking for a last-minute big batch cocktail that will keep your guests properly hydrated—and might turn them into mutants—look no further! (Note: This will not actually hydrate anyone, just so we're clear. Priorities, people!)

Blue light (like that from our smartphone) tricks the human brain into thinking it's still daytime, even if it's coming from something as small as a screen. So while you're playing around with your new Pixel or Pixel XL after dark, subconscious signals to be awake are preventing you from getting to sleep as early as you should.

Some of the best Android apps are not hosted on the Google Play Store, and that means you have to sideload them if you want to get their awesome functionality. But without the Play Store, these APKs are never automatically updated, so your only choice has been to scour the internet for a newer version when you need a bugfix.

When it comes to hacking guides, most are written from the perspective of a Linux user. There are a few outliers, but it's mainly Linux, which leads to the idea that Linux is the only OS that's viable for hacking. This couldn't be further from the truth. A properly set up Apple machine can do quite a bit of heavy lifting.

Security journalist Brian Krebs recently suffered a record-breaking DDoS attack to his his website, clocking in at or near a whopping 620 Gbps of traffic. Krebs' site was down for over 24 hours, and it resulted in him having to leave his CDN behind.

Fall is here, and it's time for warm, filling meals... that don't involve a lot of effort, because it is getting cold outside and you spent a full day at work wishing you were on the couch with a blanket over your head, dammit.

When Facebook purchased WhatsApp for $19.3 billion back in 2014, we all knew this was coming—it just took longer than we thought. But starting today, the data mining became official, and now, information from your favorite messaging app is no longer out of reach for the world's biggest social media site.

The HTC Vive and Valve's SteamVR make for one of the more compelling virtual reality experiences, mixing in real-world motion tracking with the immersive headset. But third-party manufacturers couldn't tap into the Vive's full potential and make creative new peripherals—until now.

Keyboards and mice work fine for computers, but in a holographic environment you'll want to do more than just point, click, and type. While we can still benefit from these input devices, complex hand-tracking methods are necessary for the evolution of mixed reality user interfaces.

Want to actually catch 'em all? Pokémon GO has long-teased the opportunity to hunt for Pokémon in the real world through augmented reality, but few have had the opportunity to actually see it in action.

Nintendo rolls out its first smartphone-specific game in the U.S. on March 21st, and the main protagonist is... you. Well, your Mii, and it's not a game, but a social app.

Logan's Run is one of my favorite movies of all time. The dialog is cheesy, the set design and special effects are wonky, and the main villain looks like he was conceived and built by an eighth grader in shop class—oh, and his name is Box.

Apple's once flawless mobile operating system has seen its fair share of bugs recently. From Messages and Wi-Fi settings crashing to having your photos and contacts exposed, iOS has been standing on shaky ground for a while now.

A lot of things have been changing over at Microsoft recently. Not only did they acquire the ever-popular Android keyboard SwiftKey and give away Windows 10 for free, but they've started a Google X-like experimental division called Microsoft Garage, and they've actually released quite a few awesome Android apps.

In this article I will show you how to obtain victim's credentials without cracking any hashes. There are a couple of ways to perform this task (for example dumping the SAM file and cracking the NTLM hashes), but here I will explain how to do it using PowerShell and a bit of social engineering. We are going to create a fake login popup.

The dock in Mac OS X is intuitive, customizable, and aesthetically pleasing, which is a stark difference from its clunky Windows alternative. In fact, in Windows, it takes both the Start menu and taskbar to accomplish what Apple's dock does—but it doesn't have to be like that. Below, I'll show you how to add an OS X-inspired dock on any PC running Windows XP or higher. Step 1: Install Aqua Dock

In Minecraft 1.9 New Command Blocks can be used to make elevators. You types different commands to achieve controlling the elevator for movement you like. This tutorial tells in Minecraft 1.9 how to use command blocks to make elevator. Lets just have a look at it!

Hackers are claiming money for a security flaw in Apple's new update. Quick Summary:

After a few months, I get so fed up with hearing the same ringtone go off alongside each new notification that I'm forced to switch things up—only to end up repeating this whole process when the new one gets played out. And I'm sure people around me are equally sick of listening to that tired old tone towards the end as well. I mean, a decade later, I'm convinced that Nokia tone is permanently implanted in my brain.

The new iPhone 6S and 6S Plus models have a really cool feature called 3D Touch that lets you perform app-specific Quick Actions from the home screen for apps that support it. The only downside is that this awesome new feature is not available on older iOS devices.

Hello, my web huggers! In today's tutorial we will learn how to use the Google Hacking Database (GHDB) developed by Exploit Database, to find vulnerable web servers and "juicy" information.

Greetings, hackers and friends! I know it has been a while since I posted a tutorial, and hopefully I can make up for that by posting a series.

If you have a specific app you want to lock so that others can't access it, the most secure way of doing so is with biometrics. While there are options to lock apps with either a PIN or pattern, these can easily be figured out with a simple glance over your shoulder. It's much more difficult for someone to crack your fingerprint ID, unless they chop off your finger, of course.

Windows has always been pretty customizable, and there are a ton of ways to change up the way your PC looks—though, it hasn't always been easy. In the past, changing anything other than wallpapers, titlebars, and fonts involved long hours of switching out system files with modified versions and changing icons to no end, but that's not the case with SkinPacks.

You must have read news about hackers dumping the data online, recent one was Ashely Madison. It's only the big companies' data, which gets noticed once it is out. There are many other small leaks which don't even get a mention. So this article is the first one of my series which will help you to find hacked accounts. Some of you must already know about this, but this post is intended for the new learners. This also serves as an example of my learning how a good service can be used in other w...

When security firm Zimperium discovered Android's biggest security risk in years, it sent shock waves through the ecosystem. As a result, Google, LG, and even Samsung decided to change the way they issue updates to their devices, by pledging to release monthly security patches to plug up loopholes exactly like this one. Yeah, it's that big of a deal.