Sending Christmas cards via snail mail is so passé. Why spend the time and money for a bougie photoshoot, saccharine card design, and postage when you can use augmented reality to instantly dress up photos and videos to send to friends and family instead?

So you've been using iOS 13 for a little while and noticed your iPhone is pretty slow to charge. Using the 5-watt power adapter out of the box, in the time it used to take your iPhone to charge its battery to 100 percent, your iPhone is stuck at 80% or below instead. That's because Apple introduced a new feature in iOS 13 that slows down charging — but for a good reason.

When your iPhone goes missing, it's serious business. Depending on your usage, your whole life might be connected to your iPhone, not the least of which includes debit cards, credit cards, and Apple Pay Cash stored in Apple Pay. While it's nearly impossible for someone to use your money with Apple Pay, it's still a good idea to disable it until you find your iPhone, just in case.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

It always helps to be prepared for the worst. This applies to our phones now more than ever, as we depend on them to be our record keepers for text messages from friends, family, and coworkers. If you ever lose or severely damage your phone, having a backup of your precious texts gives you the peace of mind of knowing that you can always get them back.
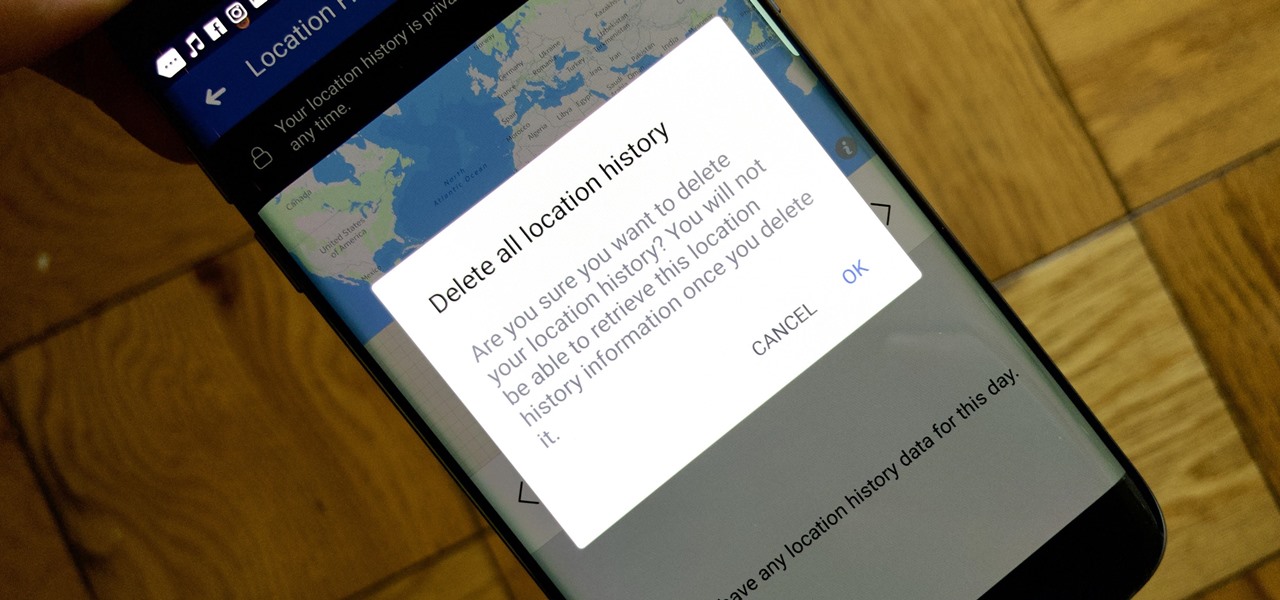
Facebook's shadiness when it comes to user privacy has never been much of a secret. The Cambridge Analytica scandal, however, has thrown the company and its practices into the limelight, with users taking their data more seriously than ever. If you're one of those users, you might want to check your "Location History" to see if and how Facebook's kept tabs on your whereabouts.

Your home has walls for privacy, but Wi-Fi signals passing through them and can be detected up to a mile away with a directional Wi-Fi antenna and a direct line of sight. An amazing amount of information can be learned from this data, including when residents come and go, the manufacturer of all nearby wireless devices, and what on the network is in use at any given time.

When traversing the web, you'll regularly come across websites that require you to create an account. With the majority of these accounts, protection is limited to a simple password. Despite this, many people are still using weak passwords such "123456." For these reasons, you really need a password manager, and our research has shown that LastPass is still your best bet.

Because of the way Google Play works, Android has a "bad app" problem. Google allows any developer to upload an app to the Play Store, regardless of if it works, how it looks, or whether or not it can harm users. Malware scanning happens primarily after apps are uploaded, and though Google has recently taken steps to safeguard users with its Play Protect program, you don't have to depend on them.

After learning that you'll need to spend at least $74 on a special charger and a USB Type-C Lightning cable to enable fast charging on the new iPhone X and iPhone 8 models, you may be wondering why you can't just use the standard Lightning cable. While we can't answer why Apple didn't include the USB-C cable in the box with their new phones, we can explain why you need USB-C to enable fast charging.

Recently, I ran across SecGen, a project which allows a user to create random vulnerable machines. I absolutely love vulnerable machines, since a vulnerable VM is a safe and legal way to practice hacking tactics, test out new tools, and exercise your puzzle-solving skills.

Elon Musk has repeatedly said Tesla models in production today have the requisite hardware to offer "full self-driving" capabilities. But for features more advanced than Level 3, Tesla will, in fact, have to revamp Autopilot's hardware to handle the extra computing load.

More often than not, road trips will include unforeseen pit stops that have to be made, no matter how well prepared you are. In the past, making an unscheduled stop may have led to headaches and delays when your navigation app got off track, but thanks to a feature in Google Maps, this is no longer an issue.

All eyes will be on Tesla CEO and founder Elon Musk tonight to see if he is reveals details about the status of Tesla's challenged Autopilot at tonight's official Model 3 launch party.

Nvidia's decades-long development of graphics processor units (GPU) for PCs has given it a major leg up in the driverless space.

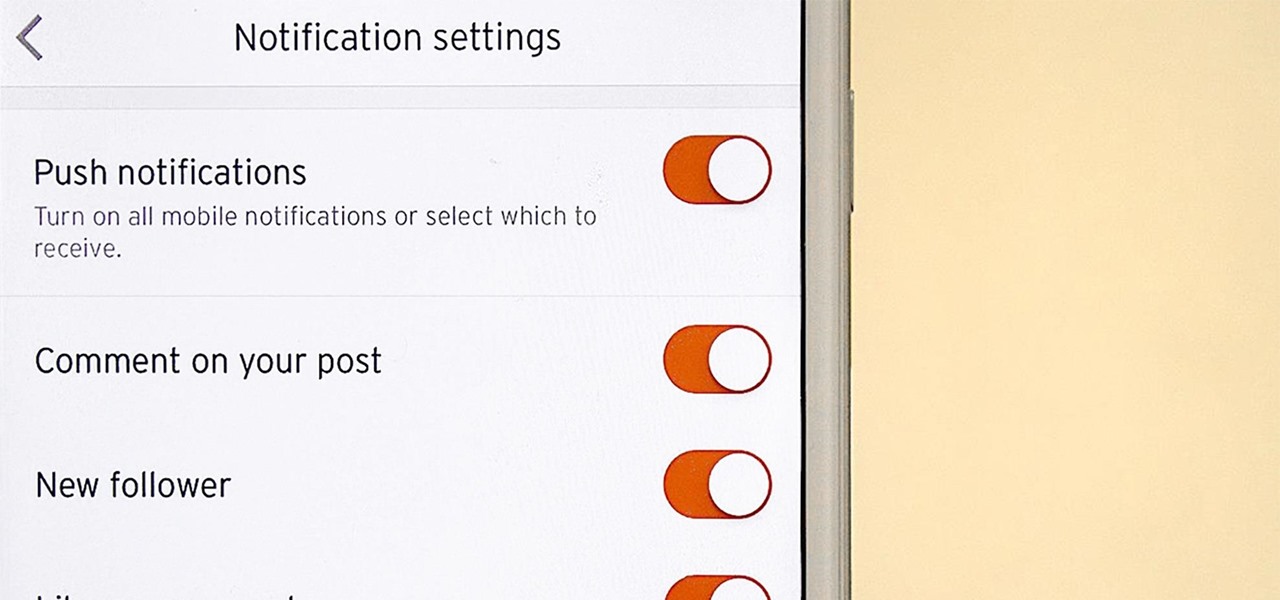
It's never fun when you install an app and then proceed to be bombarded with constant notifications. The SoundCloud app, while great in other regards, tends to have a bit of an issue on this front.

The primary method of activating Siri is done by pressing and holding either the Home or Side button, depending on the iPhone model, but there's a much better way to ask a question to Siri or command it to do something — and you don't need to touch your iPhone at all to do it.

Even before we are born, our immune system is hard at work. New research shows how the developing fetal immune system takes advantage of the time and opportunity of gestation — in the presence of mom's cells and tissues — to develop a sense of self.

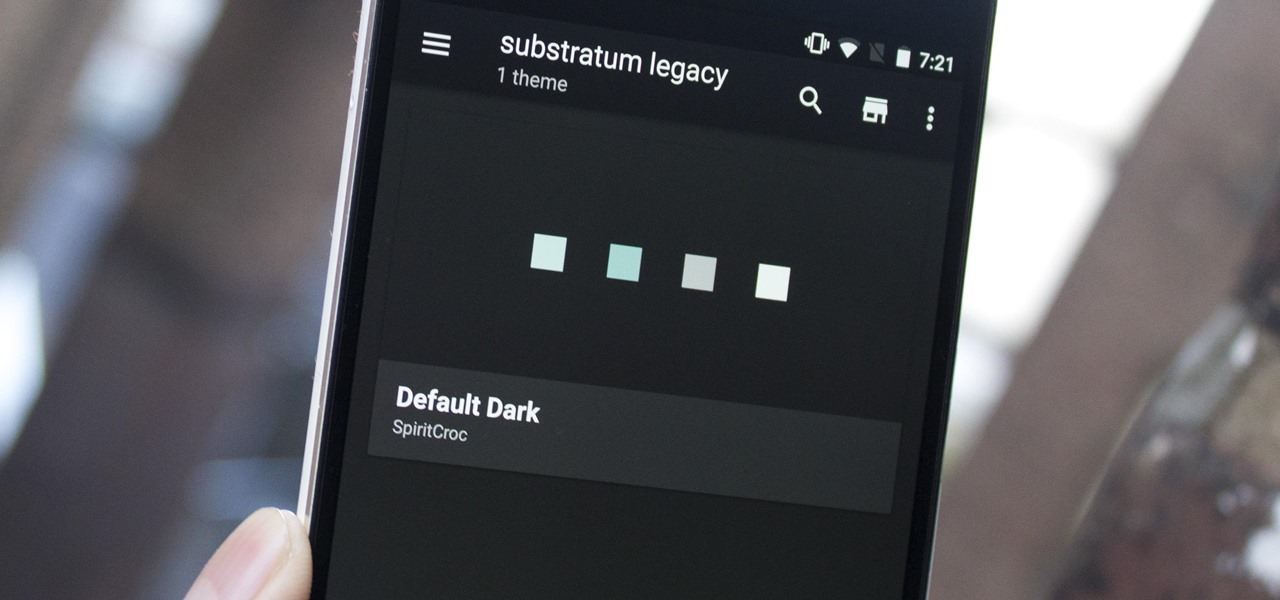
Perhaps one of CyanogenMod's greatest features was its built-in theme engine. It wasn't perfect, but it got the job done and gave users a unique look. Now that CyangenMod is defunct, and the developers behind its successor, LineageOS, have confirmed they won't be continuing the theme engine, users have to find another way to theme their devices. No need to fear, though, Substratum is here.

The Galaxy S8 has finally touched down, and it's an absolutely gorgeous device. Samsung's brand new flagship comes jam-packed with new features — some refined, and some that aren't. Luckily, we've compiled some major features to help you get started as quickly as possible so you can go about the rest of your day and show off your shiny new S8 to friends and coworkers.

Usually, the mucus lining of the female genital tract presents a barrier that helps prevent infections. But, somehow, the bacteria that causes gonorrhea gets around and through that barrier to invade the female genital tract.

Just days after the first Android O preview build was released, the development community had already started bringing some of the exclusive features over to older Android versions. For instance, the Pixel Launcher received an update in Android O, and developer linuxct quickly ported the new version to work on devices running Marshmallow or higher, and even managed to do so without requiring root.

By looking for the mechanism that allows influenza A to invade lung cells, scientists also discovered a treatment that might block the virus from taking hold there.

If anyone has every told you that they see music they listen to, they have synesthesia. It's a fascinating neurological phenomenon where people experience crossed responses to stimuli, and no one knows exactly how common this is. A rough estimate claims that one in every 5,000 to 100,000 people is a synesthete, but it could be far more common or rare. Nobody really knows.

The Snapdragon 820 and 821 were met with praise last year, receiving almost no complaints compared to their overheating predecessor, the Snapdragon 810. But now, all eyes are on Qualcomm to see what goodies they have in store for us this year, as their new SoC, the Snapdragon 835, will be revealed this week at CES 2017.

When the HoloStudy Demo app for HoloLens came out in September, it was a pretty impressive start to what could be a very valuable science tool for education. Now, Moscow-based HoloGroup, makers of HoloStudy, started an Indiegogo campaign to improve their modular teaching app.

Fish are delicate, flaky, and can be damn tricky to cook; more often than not, you end up with a hard, dry block of flesh that makes your taste buds sad. And the best ways to cook fish that you know of—c'mon, who doesn't love a fried fish—take way too much effort for you to bother with on a weeknight. Or maybe you're looking for a healthier way to enjoy fish that doesn't require batter or frying at all.

In-N-Out Burger uses only quality, fresh ingredients, and that means no frozen, prepackaged, or over-processed anything in sight. Because of this, their food is exceptionally tasty, and one of the first things tourists flock to when they visit the West Coast.

Google Now, Siri, and Cortana aside, the main way you interact with your smartphone is through the keyboard. Every app you use, every search you perform, every message you send—the most fundamental interface between you and your device is that handful of characters and those 26 letters on the bottom half of your screen.

How's it goin'? In this tutorial, we will learn about the security issues of the popen and system functions. I've seen a few people attempting to run command line utilities or whatever it is they require with calls to these two functions but may not know the security implications which come along with it. I will show you using an example from the wargame IO Smash The Stack.

Hello, Null Byte! Mkilic here. I doubt anyone knows I even exist on Null Byte, so hopefully this post will allow me to become more involved in the community and also help me learn even more.

My first ever post on here was 'Keeping your hacking identity secret' and it did very well, and its not something I see here on null byte. So read along.

Hello friends. This is actually my first how to.

When it comes to your baby and your time, nothing but the best and most efficient will do. These high standards carry through every aspect of your life as a new parent, from diapers to strollers and especially to food.

Everyone starts their mornings differently, but one common thread amongst the masses tends to be the consumption of coffee, albeit in many different forms—instant, pre-ground, K-Cups, Nespresso, and so on. And I'm sure that we all have our own preferred methods, as well.

There's only one day that can top the aftermath of Easter and its copious amounts of leftover candy, and that is November — the day after Halloween. As you come down from your sugar rush and realize you now own more chocolate than your stomach can physically hold in one sitting ... fear not! Here are several ways to turn your Halloween chocolate into delicious snacks and desserts that you can enjoy at your leisure.

Those of you who have been a part of the Null Byte community for even a short while know that I sincerely and firmly believe that hacking is the most important skill set of the future.
I see many people posting the same thing on the internet. "How do I become a hacker? Where do I commence?"

Malware often disguises itself inside of seemingly non-malicious files, such as installer packages, where it can then gain root access to your computer to track activity or steal your information.

Like most food lovers, I adore sushi. And like anyone who is a living, breathing human being, I'm a pretty big fan of sriracha sauce.