Many people find Steampunk problematic for a whole host of reasons, not least of which is the glorification of an era of Western history that featured institutionalized slavery, racism, sexism, elitism, and many more -isms.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

Firewall solutions for macOS aren't impervious to attacks. By taking advantage of web browser dependencies already whitelisted by the firewall, an attacker can exfiltrate data or remotely control a MacBook, iMac, Mac mini, or another computer running macOS (previously known as Mac OS X).

Android 9.0 Pie moved the status bar clock from the right corner to the left to accommodate phones with notches, but there's one major downside for Samsung users: since no Galaxy phones have a notch, all this did was take away space for the notification icons that would otherwise start from the left corner.

It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge.

After gaining access to a root account, the next order of business is using that power to do something more significant. If the user passwords on the system can be obtained and cracked, an attacker can use them to pivot to other machines if the login is the same across systems. There are two tried-and-true password cracking tools that can accomplish this: John the Ripper and Hashcat.

One of the most critical bugs to come out in the last five years was Shellshock, a vulnerability which allows attackers to execute arbitrary code via the Unix Bash shell remotely. This vulnerability has been around for a while now, but due to the ubiquity of Unix machines connected to the web, Shellshock is still a very real threat, especially for unpatched systems.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

Passwords and data stored in web browsers are extremely valuable to hackers. If not for financial gain, black hat hackers may still leak your passwords and personal information for amusement. Never undervalue what you're worth to a hacker.

While there are a variety of privacy-focused search engines available like StartPage and DuckDuckGo, nothing can offer the complete trust offered by creating one's own search engine. For complete trust and security, Searx can be used as free metasearch engine which can be hosted locally and index results from over 70 different search engines.

Deleted bank statements and private photos are still within an attacker's grasp, so don't think that emptying your recycling bin is enough to keep your files from coming back to life. It's possible for a hacker to recover compromising files and images from a backdoored computer completely without the victim's knowledge.

Recently, I ran across SecGen, a project which allows a user to create random vulnerable machines. I absolutely love vulnerable machines, since a vulnerable VM is a safe and legal way to practice hacking tactics, test out new tools, and exercise your puzzle-solving skills.

As the largest wireless service providers in the United States, AT&T and Verizon Wireless carry some serious clout. Sadly, they use some of this power to heavily modify the Android phones that they offer.

With a root bounty of over $18,000 up for the taking, developers were highly motivated to get the AT&T and Verizon Wireless variants of the Samsung Galaxy S5 rooted. Legendary hacker George Hotz, aka Geohot, has won the race and can now step up to claim his prize.

If you've ever seen one of those Samsung commercials from about a year back, you know that the Galaxy S series of phones come with a feature that allows you to do certain things by making gestures in front of your screen. They call this feature Air Gesture, and it enables you to perform certain functions without even touching your phone.

By now you're probably already an expert at creating cover images for your Facebook Timeline, especially if you've taken advantage of those free Facebook cards that were (and still are) being offered. But just in case you need some help making eye-grabbing cover images, there's a few tools you can try out to streamline the process.

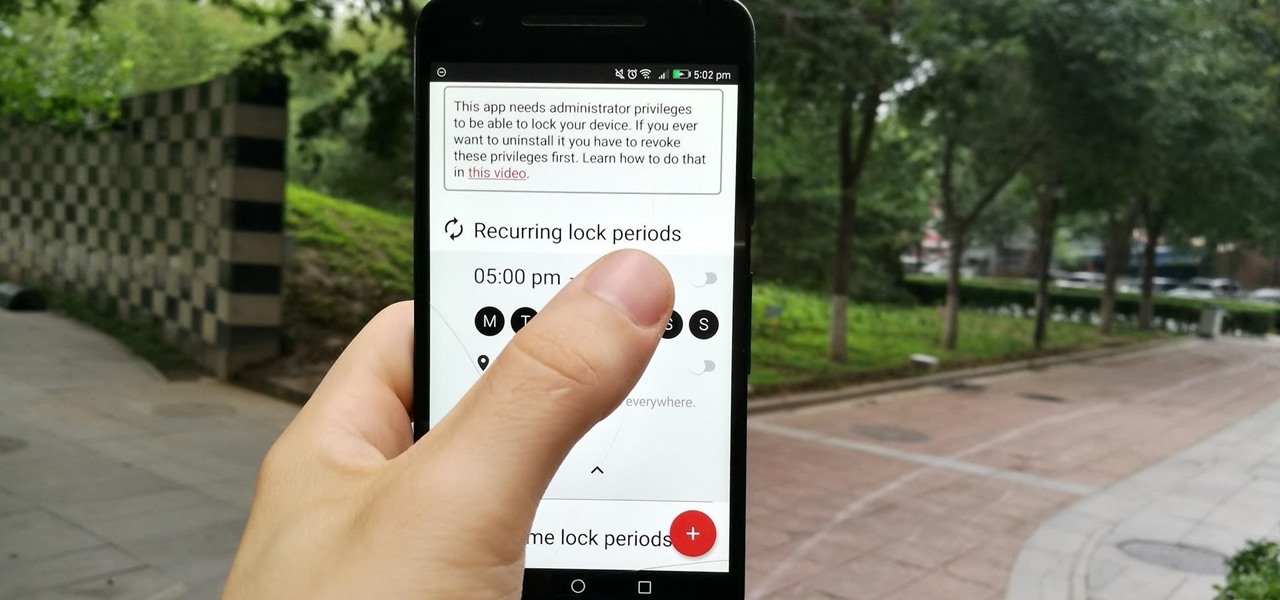
The OnePlus 7 Pro comes with a new Zen Mode feature to help increase your concentration and reduce distractions. It takes things a step further than Google's Digital Wellbeing by disabling your device and stopping sounds. But even if you don't have a OnePlus, you can now get this distraction-free feature on any phone.

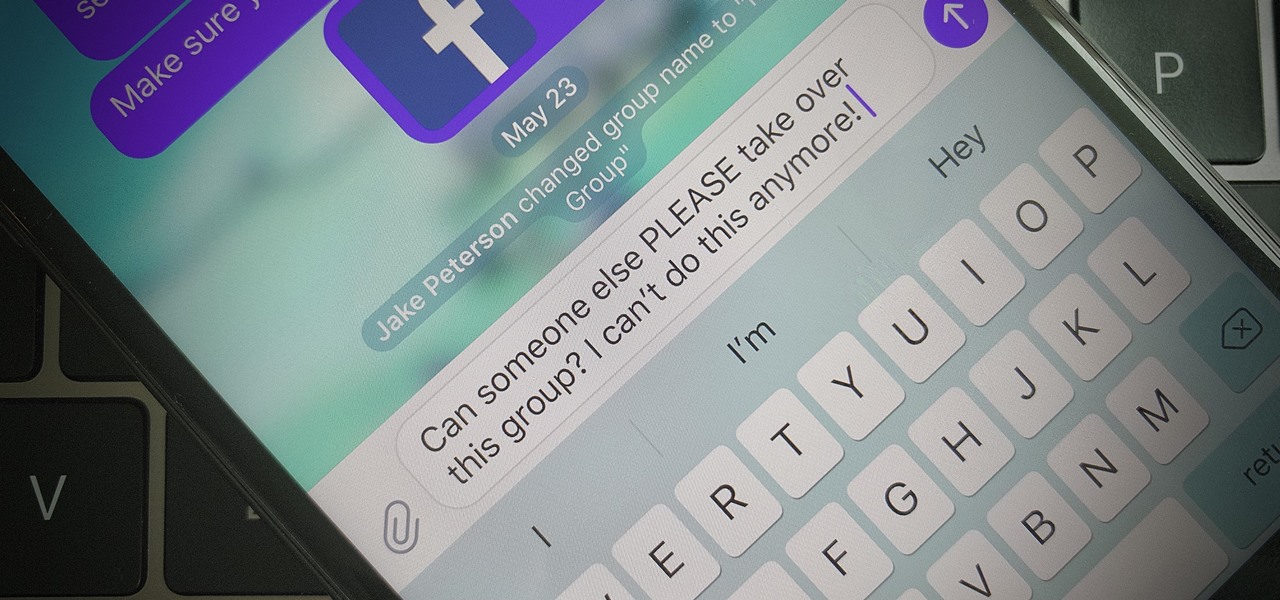
Group chats are fun, effective ways of staying in touch with the many people in our lives. Whether it's the local friend chat or the group from work, we rely on these groups to keep connected. Running one of these group chats, however, can be a monster task. If you're feeling overwhelmed with administrative responsibilities, why not pass on that burden to another member of the Telegram group?

In the first guide, we laid the groundwork for our ultimate goal of uploading and running the unix-privesc-check script on our target. We identified an input field vulnerable to SQL injection and utilized Sqlmap to set up a file stager on the server. Now, we're ready to upload files and execute the script, so we can identify any misconfigurations that could lead to privilege escalation.

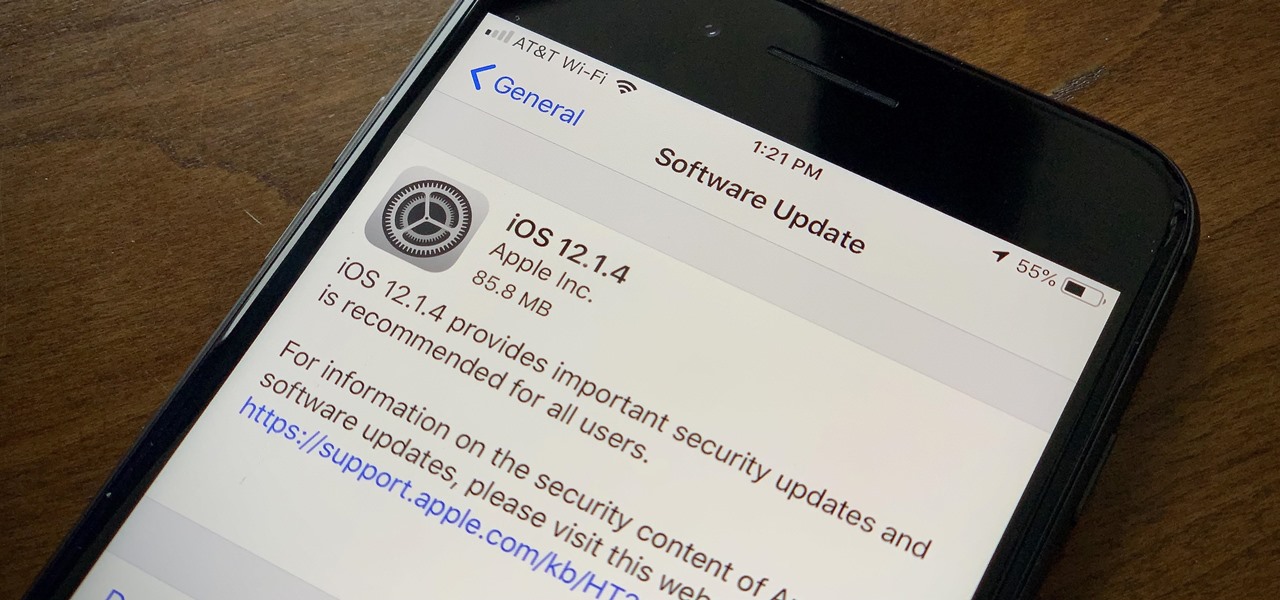
Apple found itself in serious trouble last week when a teenager discovered a critical FaceTime bug that threatened the security of nearly every iPhone user. The bug enabled a user using Group FaceTime to access either the microphone or the camera of a recipient before they answered the call. According to Apple, the issues have been fixed in an iOS 12.1.4 update released Thursday, Feb. 7.

Although next week will mark the late David Bowie's 72nd birthday, his fans and admirers are the ones receiving a gift in the form of an augmented reality app that explores the artist's career

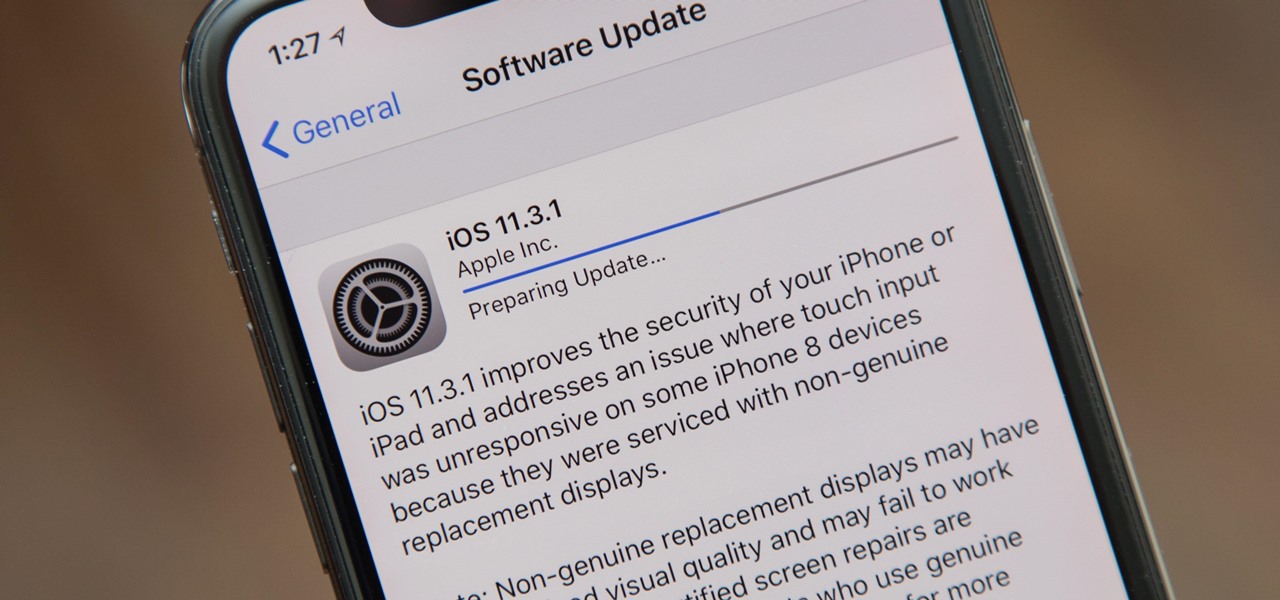
Apple released the iOS 11.3.1 update for iPhones on Tuesday, April 24, 26 days after the official release of iOS 11.3 and eight days after the iOS 11.4 beta 2 update. It is the first minor update to iOS 11.3, and the biggest thing in it is a fix that lets displays fixed by third parties work again.

It finally happened. Magic Leap has given the world its first glimpse at its debut device, the Magic Leap One Creator Edition.

It's long past time to face the facts: farts are funny. The first fart joke dates back nearly 4,000 years to the ancient Sumerian people. References to flatulence were also found in ancient Greece within the works of Aristophanes. (More like Aristo-fannies, am I right?) A standard in practical jokes, the whoopie cushion debuted way back during the time of the Roman Empire.

It looks like there is a fatal flaw in the current macOS High Sierra 10.13.1, even straight from the login menu when you first start up the computer. This severe vulnerability lets hackers — or anyone with malicious intentions — do anything they want as root users as long as they have physical access to the computer.

With chips in four out every five PCs made since 2010, few companies are as pervasive in modern computing as Intel. That's why an advisory released Monday, May 1, confirming a remotely exploitable vulnerability in all non-server business hardware made in the last seven years has sent shockwaves through the technology world.

As it turns out, your Android apps are pairing together to share your data without asking for your permission first. Researchers from Virginia Tech developed a tool called DIALDroid to monitor exchanges of data between Android apps over the last three years, and what they've found is quite alarming.

Google's Pixel phones have a feature that lets you swipe down on the fingerprint scanner to open your notification shade and Quick Settings panel. It's one of those features that make you wonder why it wasn't there in the first place, since it gives you another way to interact with your device, and your fingerprint scanner isn't being used while you're screen is on anyway.

Android device manufacturers may see the new Pixel "Phone By Google" devices as just another competitor, one that likely won't upset their entry-level margins. But that would be a mistake. Pixel is Google's call to action. With Google now offering as near to perfect an Android experience as we've had so far, OEMs that want to keep selling smartphones in a world flooded with them will need to start working for the privilege.

Although there has been much speculation about how much damage could be done if hackers were to take control of a country's SCADA systems, there have been few examples - until a few months ago, with the power outage in Ukraine caused by hackers.

Here I will show you how to properly dig information on the web that has already been published, you just dont know it.

Hello fellow Nullbytiens, I'm Washu, a long time commenter but first time poster. Today we'll be making an IRC bot, if you haven't seen OTW's post about the new IRC channel I would encourage you to go check it out. He does a good job at explaining what IRC is and how to get set up.

Hello! This is my first post on this awesome website! I know that Windows exploits are less common than the more advanced hacks, but I found something I deem pretty cool and figured why not share it with you all. Alright, enough about me, lets begin.

When you finally turn the privileged age of 21 in the U.S. (or 18 in most other countries), the first thing you'll probably do is sprint to the nearest pub, order a drink, and revel in your new freedom. Congratulations, you've survived two decades on Earth, you've earned that drink.

While a mobile game developer may have built something unique, they still have to go through an arduous process of fixing bugs, smoothing out gameplay, making sure it works on different screen sizes, and following Apple's rules before they can submit their game to the iOS App Store.

Hi Elite Hackers! Welcome! to my 4th post. This tutorial will explain, how to extend a (hacked) AP's range with a wireless adapter. I made this guide because after hacking an AP it was difficult to connect to it (poor connection) and further exploit it. You can also use this:

As technology continues to advance, we as consumers are privileged enough to be able to take higher quality photos and videos and listen to clearer and better-sounding music on our mobile devices. But sometimes we forget that there's a price to pay for that awesome content—enormous file sizes.

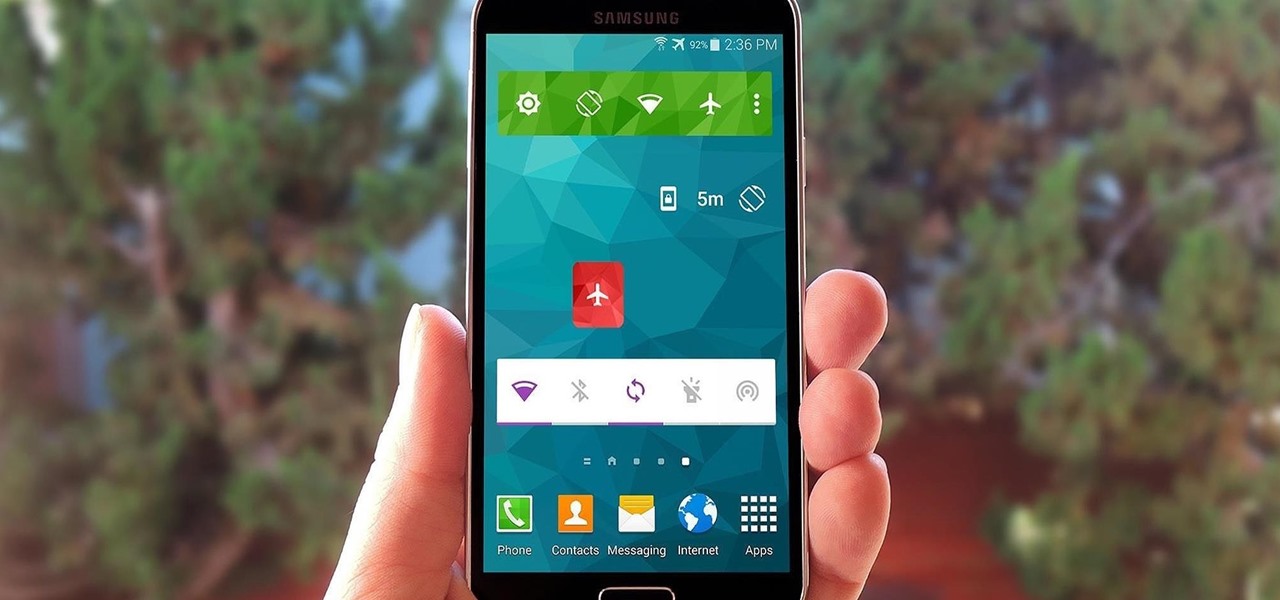
Widget toggles, or "power toggles" as they're often called, have been around for quite a while. They serve their purpose nicely as an easy way to add switches to your home screen or notification area for functions that don't come with the stock software on your device.

Google's latest Nexus device is big, bold, and beautiful—and now it's got root. Thanks to some quick work by legendary Android developer Chainfire, the Nexus 6 already had a clear-cut root method before most stores even had it in stock.

Losing important data is the modern-day equivalent of misplacing your wallet or keys. We have tons of vital information stored in our digital worlds, and losing any of it can be devastating. But if you've accidentally deleted something important from your Android device, there's still hope.