Sudo is a necessity on most Linux systems, most of which are probably being used as web servers. While the principle of least privilege is typically applied, sudo misconfigurations can easily lead to privilege escalation if not properly mediated. Which brings us to SUDO_KILLER, a tool used to identify sudo misconfigurations that can aid in privilege escalation.

Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.
Whether you love Motion Sense or think it's a gimmick, one thing we can agree on is that its functionality is limited. It's currently limited to switching tracks on a playlist, snoozing alarms, silencing calls, lowering the volume of alerts, and checking notifications. But a new mod will help you do so much more with it.

Chances are, your favorite websites run on ads. That means the sites rely on those ads to fund their operations. Without ads, your laughs, news, and guides don't happen. That's why it's helpful to disable content blockers (often called whitelisting) for sites you support. In the past, it wasn't possible directly in Safari, but in-app whitelisting becomes a reality with iOS 13.

Things that are supposed to make life easier for developers and users are often easy targets for exploitation by hackers. Like many situations in the tech world, there is usually a trade-off between convenience and security. One such trade-off is found in a system known as Distributed Ruby, which can be compromised easily with Metasploit.

Hundreds of Windows 10, macOS, and Linux vulnerabilities are disclosed every single week, many of which elude mainstream attention. Most users aren't even aware that newly found exploits and vulnerabilities exist, nor that CVEs can be located by anyone in just a few clicks from a selection of websites online.

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.

After about 40 days of beta testing, Apple pushed out iOS 11.4.1 to everyone as a stable build on Monday, July 9, exactly one week after the final beta appeared.

With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

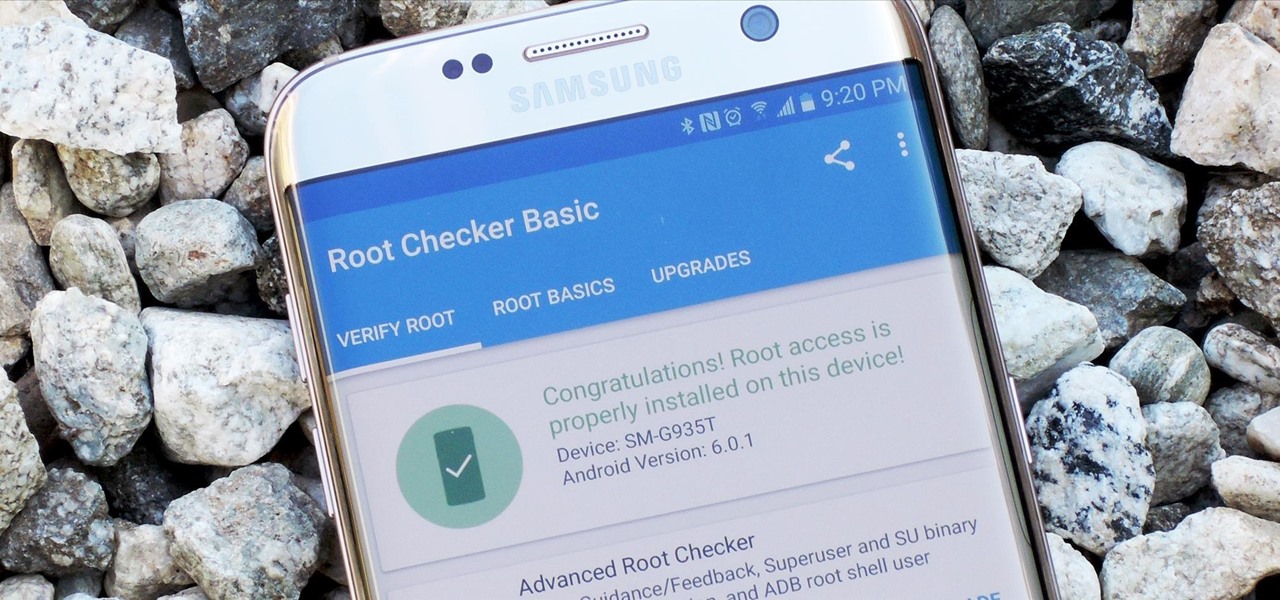
If you ever want to root your OnePlus 6, install TWRP, get Magisk and Xposed, or flash a custom ROM, the first thing you'll need to do is unlock your bootloader.

Backdooring a powered-off MacBook is easy when a few minutes of physical access is allowed. That attack works well if the hacker also shares a Wi-Fi network with the victim, but this time, I'll show how to remotely establish a connection to the backdoored MacBook as it moves between different Wi-Fi networks.

Before Google I/O 2018, the Google Assistant for Android and iOS had only two available voice options to choose from — a robotic female and male voice. But there are now six additional voices, and these ones sound way more natural than any other mobile voice assistant (plus, John Legend's voice is coming later this year).

Maybe you thought sitting behind a Mac gives you special protection when it comes to getting hacked. Thanks to a a new report from Check Point, you can kiss that theory goodbye. The cyber security company just uncovered the latest strain of malware — OSX/Dok — infecting all versions of macOS (previously Mac OS X).

Bitcoin, the decentralized cryptocurrency notorious for its status as the currency of the dark web, seems to be shedding its shady past and is now enjoying soaring highs not seen since 2014. The highly volatile online commodity reached parity with an ounce of gold back in March amid speculation of a pending ETF approval from the Federal Trade Commission. Since then, Bitcoin has doubled in value and analysts predict a bitcoin could reach $100,000 in value in 10 years.

The V20 is an amazing phone from LG powered by Android. Packing impressive features such as a removable battery, expandable storage, and the latest Android version straight out of the box, the V20 is a tough phone to beat.

It seems like a new, dangerous Android exploit is uncovered every month or two. The latest headliners are NightMonkey and Chronos from the list of CIA hacks reported by Wikileaks, which have been billed as gaping security holes in the world's biggest mobile operating system.

GitHub is an extremely popular site that allows developers to store source code and interact with other users about their projects. Anyone can download public, open-source files on GitHub manually or with Git, and anyone can fork off someone's project to expand or improve it into its own project. It's a really great site for programmers, developers, and even inspiring hackers.

Since I recently had this problem and fixed it, I might as well share the solution. This is actually REALLY simple to fix but will impact your cards' performance.

Samsung's 2016 flagship devices are some of the most beautiful, powerful smartphones ever made. And amazingly enough, thanks to legendary root developer Chainfire, the Samsung Galaxy S7 and Galaxy S7 edge are about to get even more powerful.

Very often we have processes in Linux that we want to always run in the background at startup. These would be processes that we need to start at bootup and always be available to us.

Welcome back, my budding hackers! Metasploit, one of my favorite hacking/pentesting tools, has so many capabilities that even after my many tutorials on it, I have only scratched the surface of it capabilities. For instance, it can be used with Nexpose for vulnerability scanning, with Nmap for port scanning, and with its numerous auxiliary modules, nearly unlimited other hacking related capabilities.

Last month, it was revealed that Juniper Networks' routers/firewalls were hacked. It was reported that a backdoor was implanted in the operating system of their routers/firewalls and that attackers could listen in on all encrypted communication. There are now fears that all confidential communications by U.S. government agencies and officials could have been compromised over the last three years.

While I frown upon any form of uneaten cookie, sometimes we overestimate our late-night cravings for baked goods leaving us with extra cookie dough at 4 a.m. If you're in the privileged dilemma of not having enough excess dough to make another batch of cookies but just enough left over that you can't justify tossing it, don't fret. Here are five effortless and unexpected ways to salvage it.

Hi there, Elites Welcome to my 6th post, This tutorial will explain how to hack windows, using a program (No-IP)

Hi, dear co-apprentices and wise masters. I've been recently trying to learn the basics to hacking here, and I've read all guides on Wi-Fi hacking and noticed no word is dedicated to this awesome script that comes bundled with Kali!

The Xposed Framework offers many great customization options for your Galaxy S5. S Health, with its ability to read your heart rate through a built-in monitor, is one of the main selling points of the GS5. Trouble is, the two don't seem to play nice together.

What if someone asks you to do a Nmap scan but you left your pc at home? What if a golden opportunity shows during a pentest but you were walking around the building, taking a break?

Android's permissions system is simple, transparent, and straightforward. When installing an app, you get a chance to review all of the permissions that the app has requested. These can range from accessing your location data to holding a "wakelock" in order to prevent your phone from entering sleep mode. But your only choice in this matter is to accept all requested permissions, or not install the app.

Because of Android's massive array of supported smartphones that carry vastly different display sizes and resolutions, the operating system uses a value known as DPI to determine the size of icons and visual assets that will best suit a given screen.

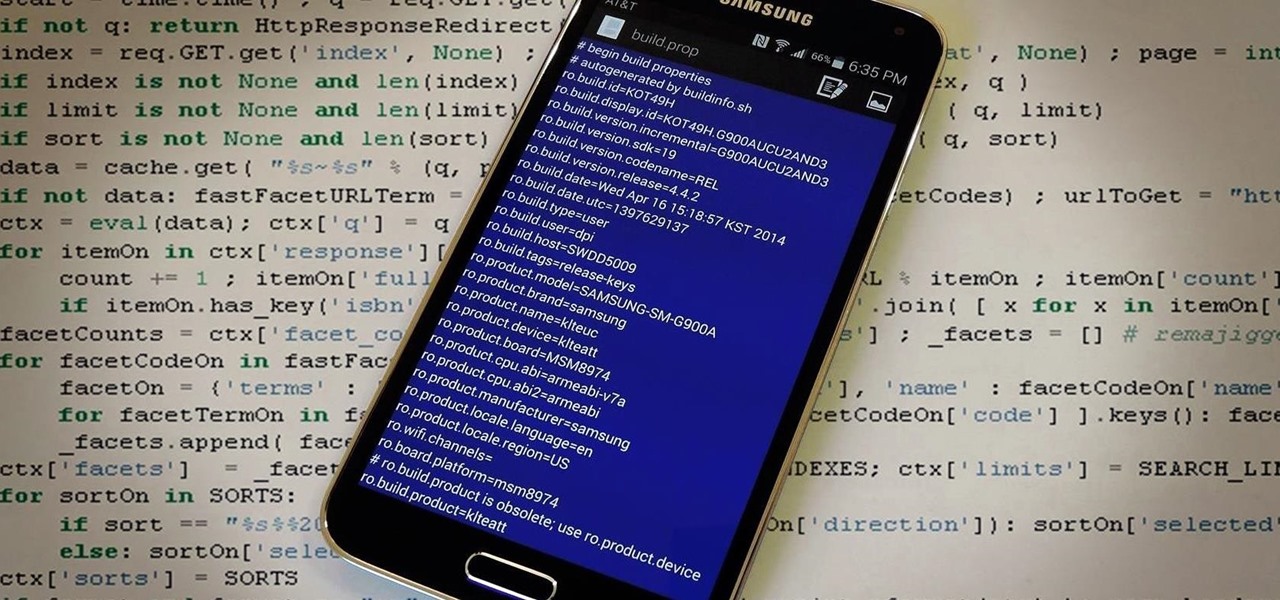
The build.prop file in an Android device is home to many system-level values and settings. Everything from screen density to video recording quality is covered in this file, and people have been editing these entries to get new functionality and better performance since Android has existed.

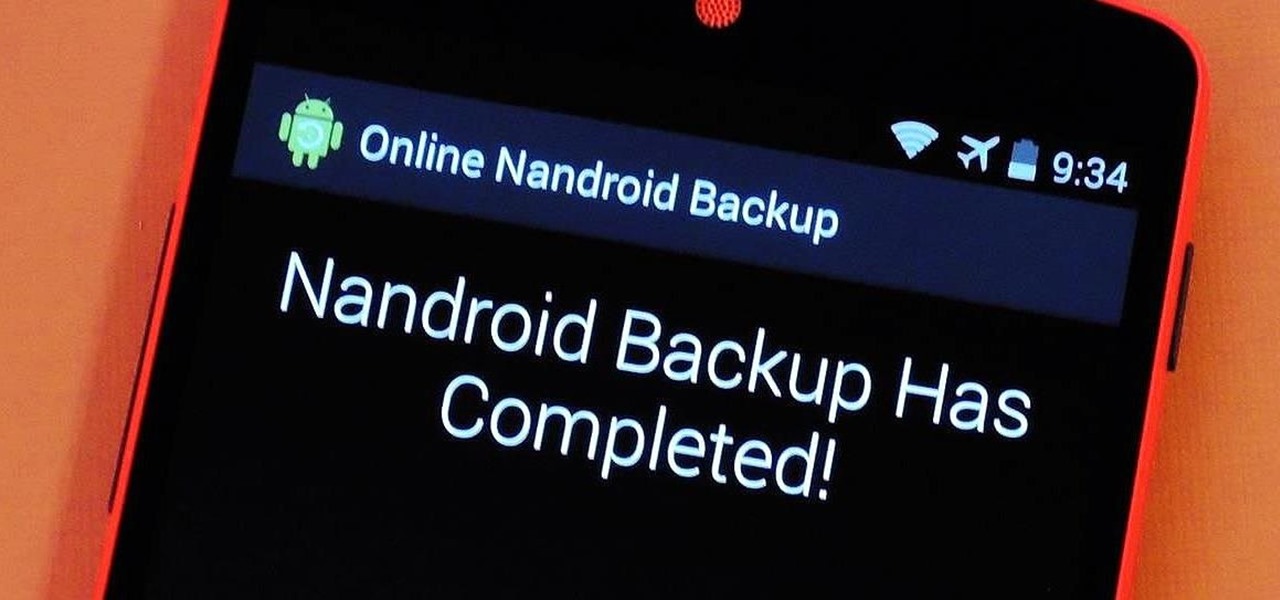
If you have a custom recovery installed on your Android device, the first thing you should have done as soon as you finished installing it was to create a Nandroid backup. But if you didn't, I'm not here to judge—I'm here to show you a much easier way.

Surely you've heard of the wildly-popular custom ROM CyanogenMod, right? As the longest-tenured third-party firmware for Android devices, CM has been able to maintain its popularity by supporting a wide array of devices and offering many customization options.

Android uses a set of permissions that apps can request to perform certain actions, and you're notified of these permissions each time you install an app. The problem here is the fact that you aren't given any built-in way to deny apps these permissions (although Danny just showed a workaround for this).

When it comes to theming your Android device, it's the little touches that count the most. That's why developer SArnab created the Android Theme Engine, an Xposed Module to theme those hard-to-reach corners of the Android System that often go untouched with other themes.

One of the best things about the Nexus line of devices is the ease with which one can achieve root. Plug your phone into your PC, download a couple files, type a few commands, and you can be rooted within 30 minutes. No muss, no fuss, no carrier-locked bootloaders.

The Nexus 5 has a known issue with its display. Affecting all models from the first manufacturing run and most models thereafter, this display issue is easiest to notice on something with a white background. A yellowish tint, most noticeable when compared to other devices, seems to emanate from the Nexus 5's screen.

Greetings. This how-to on hacking Windows 7/8/10 etc. admin account passwords using Windows Magnifier is focused on adding, changing, or deleting an admin level account on a Windows 7/8/10 etc.

You've unlocked your bootloader and rooted your HTC One running KitKat, but there's still one lingering aspect of security you've yet to rid yourself of—S-On—the extra security measure HTC implemented into Sense.

With the release of the Samsung Galaxy S5 right around the corner, the first full system dump has been released by Sammobile. As the inevitable ports of functioning apps slowly begin to leak, today we've got a non-app aspect of the system and the one that tends to leak first—ringtones.

Welcome back, my fledgling hackers! It's been awhile since we did a Metasploit tutorial, and several of you have pleaded with me for more. I couldn't be happier to oblige, as it's my favorite tool. For the next several weeks, I'll intersperse some new guides that'll help expand your Metasploit skills and keep you abreast of new developments in Metasploit, so look for them in the near future.