This is Null Byte's fourth part in a series about fully securing our computers (Part 1, Part 2, Part 3). In our last Null Byte, we went over how to encrypt an entire operating system to protect our data, however, this doesn't fully protect us. In the case of legal extortion, the government can actually make you give up your cryptographic key to your computer so that they can look through it.

Welcome to the second Goonight Byte! Our second coding session was kindly hosted by th3m, so props to him for letting this happen.
One of the biggest advantages iOS has over Android as a mobile platform is how readily and fully it has embraced mobile gaming. There are over 200,000 games available in the Apple store, compared to approximately 100,000 in the Android Marketplace. As an Android-using gamer, this has always bothered me.

For most street artists, it takes a considerable amount of time to paint large art installments on the walls of urban structures. The more time it takes, the better chance there is of getting caught, since nearly all of the rogue artwork is slapped on the sides of city and privately owned buildings.
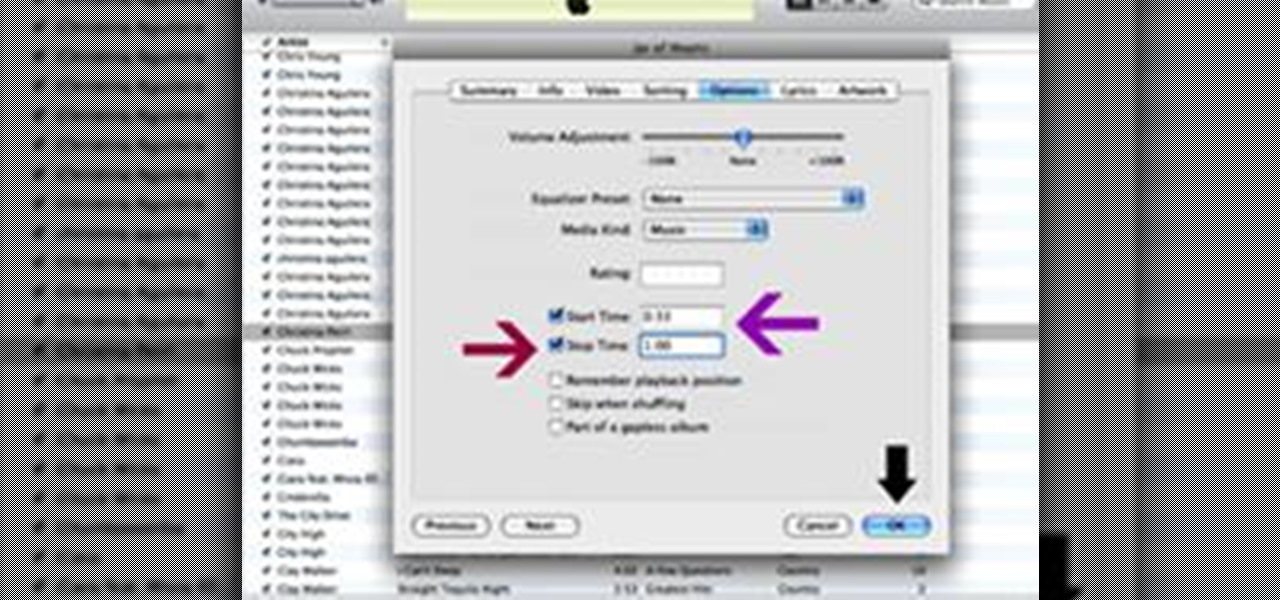
Granted the iPhone is an awesome phone... but their choice for default ringtones kind of, well, stinks. They have plenty of apps you can BUY to PURCHASE ringtones... but why waste money when you can make an unlimited amount of ringtones yourself forFREE? At first glance, it looks complicated and confusing, but I'll break it down so simply, you'll be making ringtones for everyone in iTunes.

In the dojo, what ISN’T said is often as important as what IS said. To most of us who’ve been raised in the USA, the reticence we encounter in the dojo can be off-putting. American society is very “content” oriented. Our legal contracts, for instance, run for pages and pages. Everything needs to be spelled out. In “context-oriented” societies there is far less reliance on such a literal approach. Much more importance is placed on the relationship between the two parties entering into an agree...

And Dumbfounded Most Watching Game 1 of 2010 World Cup I just finished watching the Mexico - South Africa 2010 World Cup opener and boy was it a good one. The finish of a tie, wasn't totally cool to me, until I realized what I missed.

Over the past couple of weeks, there have been a series of high-profile hacks and leaks. From the rooting of CombinedSystems, to a secret FBI conference call leak, all the way to the distributed denial-of-service (DDoS) attacks on U.S. government sites—with a lot in-between. As governments move to close their long fingers around the free speech that exposes their secrets, this shadowy collective of loose-knit, but like-minded individuals are hell bent on preventing them. Or are they?

Like the press covering film and many other specialized fields, video game journalists use all sorts of jargon to convey to their knowledgable readers as much information about a game as quickly as possible. For non or newbie gamers, this can be extremely confusing.

The most recent viral video on YouTube is just that. A viral video. After seeing all the hype and 'support' that the 'movement' is getting, I want to tell you that this is a misleading video and somewhat of a propaganda campaign. These are strong accusations against such a 'humanitarian' cause, but I'm here to show you why.

Eventually, we plan on doing some root the box competitions here at Null Byte, but we're still looking for a server to play on. Anyone want to donate one? You won't regret it. Root the box is like 'king of the hill', except you have to hack a server and maintain access. Each server will have numerous known security holes, but until then, let's get back to the regular weekly coding sessions and realistic hacking missions on HackThisSite.

We'd like this to be one of the last HTS mission announcements, at least for now. As soon as Null Byte finds a server to play with (anyone want to donate one?), we are going to start doing root the box competitions, which is like king of the hill, except you have to hack a server and maintain access. Each server will have numerous known security holes. But for now, back to the normal flow of things...

Technology in computers these days are very favorable to the semi-knowledgeable hacker. We have TOR for anonymity online, we have SSDs to protect and securely delete our data—we can even boot an OS from a thumb drive or SD card. With a little tunneling and MAC spoofing, a decent hacker can easily go undetected and even make it look like someone else did the hack job.

We're aiming for this to be one of the last HTS mission announcements, at least for now. As soon as Null Byte finds a server to play with, we are going to start doing root the box competitions, which is like king of the hill, except you have to hack a server and maintain access. Each server will have numerous known security holes. But, for now, back to the normal flow of things...

The community tore up the first realistic mission last week. You've applied the techniques learned in the basic missions to a real scenario, so I'm pretty content. The realistic missions are where the learning gets intense and where we can apply real knowledge to extremely realistic situations. We will also be continuing the normal Python coding and hacking sessions. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, f...

Community byters, it's time to get serious. We are finally moving on to the realistic missions in HackThisSite. This is where the learning gets intense and where we can apply real knowledge to extremely realistic situations. We will also be continuing the normal Python coding and hacking sessions. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers to aspiring hackers.

Before you start snapping away and submitting your photos, please take some time to read the official rules below!

Welcome to Minecraft World! Check out our advanced tutorials and come play with us on our free server.

Friday's Community Byte was weird. The intent was to do a HackThisSite mission, but upon time to begin, everyone in there was programming without my assistance, with the help of Sol Gates. This is great! It's really awesome that everyone enjoys programming that much and will make the effort to learn even when I am not present. So, a tip of my hat to Mr. Sol Gates and the rest of you fine people.

In these weekly Scrabble Challenges, so far we've covered two-letter words, double bingos, high scoring moves, triple-triples, last moves, parallel plays, phoneys and opening moves. For this week's puzzle, we're revisiting the strategy for opening moves.

A phoney word in a game of Scrabble is basically a non-valid word, either played or considered being played. Why? To fool the other player and go from losing to winning. It's perfectly acceptable in Scrabble play, but only if you don't get caught. If the other player challenges your play, then you'll be forced to remove it and your turn will be skipped. That right there—not fun.

Bourbon is the ultimate American spirit, considering the barrel-aged distilled spirit was originally produced in an area known as Bourbon County, Kentucky. To meet the legal definition of bourbon, it must be produced in the United States, must be created with at least 51% corn, and aged in new oak barrels. There are two types of bourbon whiskeys—straight and blended. Straight bourbon means that the bourbon has been aged for a minimum of 2 years, and has no other coloring or flavoring added. B...

The small size of most indie game development teams is a strength, but also a weakness. It allows them to take risks and explore revolutionary ideas that a larger company could never justify to its shareholders, but also means they must navigate the game development labyrinth with minimal help, taking much longer than those with big development teams. Some of the most exciting indie games currently in development have been so for years, or look like they will be.

Advancements in technology usually lead to the miniaturization of old technologies, and video games are no exception. Since at least 1990, game hardware manufacturers and enterprising DIY electronics enthusiasts have poured their efforts into making full-size video game consoles smaller, even handheld. And for good reason—who would have ever played a black and white Game Boy if they could have had an actual NES in their pocket?

Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills.

Do you remember when video games came on tiny chips in plastic cartridges? When the CD and 3D graphics just meant ugly games with long load times? Before epic cinematics, spoken dialog, or cordless controllers? Do you still have all of your old games and lament that the consoles, cords, and controllers required to play them have either been stolen by exes or broken while moving apartments?

West LA Seido Karate-do embeds its personal protection program into its on-going classes. Private instruction in this aspect of Seido can also be arranged with Kyoshi on an individual basis.

Hi OLers read the following article to gain some great insight into the mischevious advertising ways of food labels. Thanks to the New York Times for this great article below. Happy Eating6 Meaningless Claims on Food LabelsAlthough food labels are supposed to tell us exactly what’s in the food we’re buying, marketers have created a language all their own to make foods sound more healthful than they really are.Today’s “Consumer Ally” column on AOL’s WalletPop site explores misleading food-labe...

In Alan Wake, there are hidden messages hidden throughout the levels that are only visible with a flashlight. If you don't flash the light at a particular spot, you will not be able to see the message.

April NPD Video Game Sales Every month around the second thursday the sales chart for video games and consoles are released for the previous month. They are released by the NPD group, the main company tracking video games sales in the US. Here are the top twenty games in the month of april (courtesy of Gamasutra http://www.gamasutra.com/php-bin/news_index.php?story=28566 ):

On its quest for online domination, Amazon.com continues to expand past its basic web marketplace to fulfill the needs of everyone and anyone with a little cash to spend.

According to Amazon.com, Kindle was their best-selling item this year, which means many, if not all of you are playing with a brand new Kindle on Christmas Day. Of all of Amazon's Kindle models, the Kindle 3 (6") will be the most common eReader in everyone's hands, either the Wi-Fi version or the 3G model.

In the first part we differentiated the two types of control, mental and physical. In part 2 we will dig deeper into Physical crowd control and analyze examples that are present today.

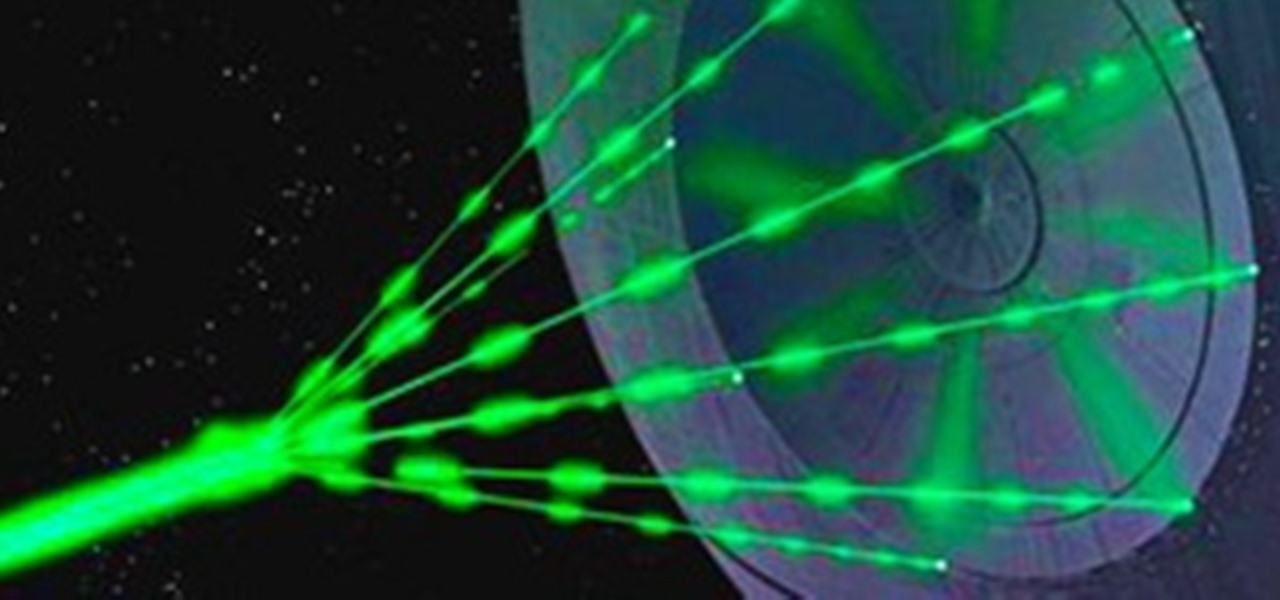
In this series on weaponized lasers, I'll be exploring the function, operation, strength and building instructions for three basic laser weapons; CO2, Diode, and Flashlamp. These laser types are just a few of many, selected because of their simplicity and basic construction (depending on your experience).

Hello and welcome to another InfoSecurity World tutorial. The intent of this article is to teach one how to encrypt sensitive files. When set up correctly with a strong password, it would be almost impossible to hack. Even the FBI have had issues decrypting this software. I'm here to teach you how to create a general encrypted container—not the complex hidden TrueCrypt volume.

Bluffing is one of the key components of poker. You may have a horrible hand, but if you can play it cool and raise the bet, you might just be able to convince your opponents otherwise and induce a few folds. But if you can't handle a little subterfuge, then you shouldn't be playing the game. Even the slightest tell could give you away. You have to maintain a poker face, no matter what.

WonderHowTo is made up niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

WonderHowTo is made up niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

It's a question I've been pondering a lot lately. Technically, children under the age of 13 are not allowed to join Facebook. But according to a Consumer Reports in May, 7.5 million children 12 and younger are already on the site. Currently, federal law prohibits websites from collecting personal data from children without parental permission. The Children's Online Privacy Protection Act, or COPPA, as it is more commonly known, has been in effect since 1998, but has not been updated since.