Many new parents will tell you how hard it is to name a baby. Some have stories of how they knew what the name of their child would be from before conception, only to change their mind when they were born. Sometimes new babies can go weeks without a name since there is an endless selection to choose from.

In recent weeks, some people have been shunned from the Null Byte community because they expressed "black hat" aspirations. This is because Null Byte is the "white hat" hacker training/playground. Although most of us think we know what that means, it does beg the question; "Who and what is a white hat hacker?"

With the brand new SMS-based ordering service called Magic, anyone with a mobile phone can order whatever they want—really, anything—by sending causal text messages. Who says magic isn't real?

Welcome back, my budding hackers! People often ask me, "Why are you training hackers? Isn't that illegal?" Although I usually give them a short version of this post, there are MANY reasons why YOU should be studying hacking.

In this video tutorial, viewers learn how to draw a skull. Begin by selecting a skull image to draw from. Then draw a circle and sketch a few lines to position the eye sockets, nose and mouth cavities. Now erase the guidelines and re-sketch the drawing. Then start toning the eye sockets and nose cavity by shading. Now tone the other parts of the skull. Finish by shading the background. This video will benefit those viewers who are interested in drawing and art, and would like to learn how to ...

Watch this video demonstration on crocheting one row of a baby ripple afghan. With these visual guidelines, you can quickly accomplish the most difficult step in crocheting an afghan; the beginning.

This unique instructional slide show will show you how to sculpt tiny, delicate baby feet out of polymer clay. You will need polymer clay, sculpting tools, a paintbrush, and blush makeup. These guidelines can be used for sculpting baby feet on clay dolls. Polymer clay hardens in the oven, so it is convenient to sculpt baby feet at home.

RC Car Action Magazine Editor Paul Onorato explains how to submit your RC car or truck to RC Car Action to be featured in Readers' Rides. RC Car Action magazine showcases readers' own cars, but the pictures need to meet certain guidelines. Watch this video tutorial and learn how to submit photographs of your RC car or truck to be featured in RC Car Action magazine.

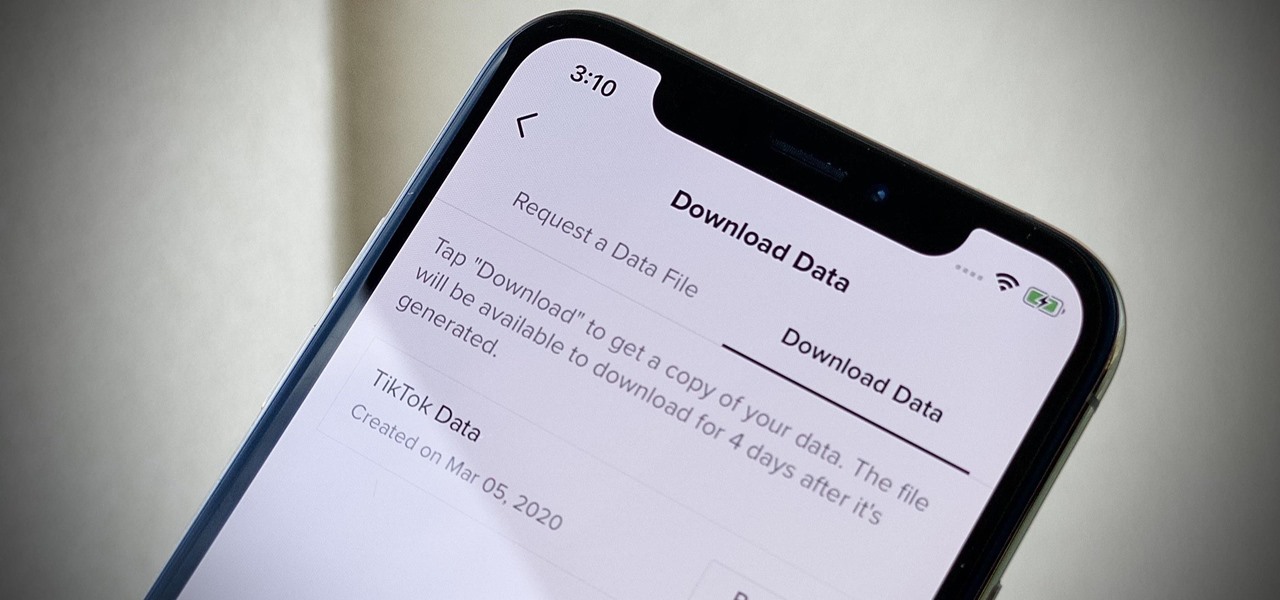
If you're concerned about your privacy, TikTok might not be the app for you. Its shady practices with user data have been the subject of concern, criticism, and even legal action by the US government. Then again, it's just so addicting. If, like me, you're not going to stop using TikTok anytime soon, you should at least know how to view the personal data it has collected on you.

This week, Snapchat parent Snap came closer to fulfilling its smartglasses destiny by adding new 3D content capabilities to its third-generation Spectacles. At the same time, the now defunct Meta Company continued its fall from grace, as a judge ruled in favor of the plaintiff in the patent infringement case against the Meta 1 and Meta 2 headsets.

In case you thought the long and unfortunate story of ODG was over, hold on, there's one last chapter to tell.

I was today years old when I first heard of Bhad Bhabie, but I'm told she is apparently a rapper with a rags-to-riches story.

Depending on your region, you may not be offered the same call recording option other OnePlus users have. But, as with most things Android, where there's a developer with a will, there's a way regardless. And the method we are about to describe is one of the easiest, most stable, and undetectable ways to do it. Perhaps we should discuss why OnePlus has been holding out you when it comes to this feature, though.

Just a year after facing trade secret theft allegations from his former employer, ex-Meta Company employee Kevin Zhong and his new company are ready to ship the product that triggered the lawsuit.

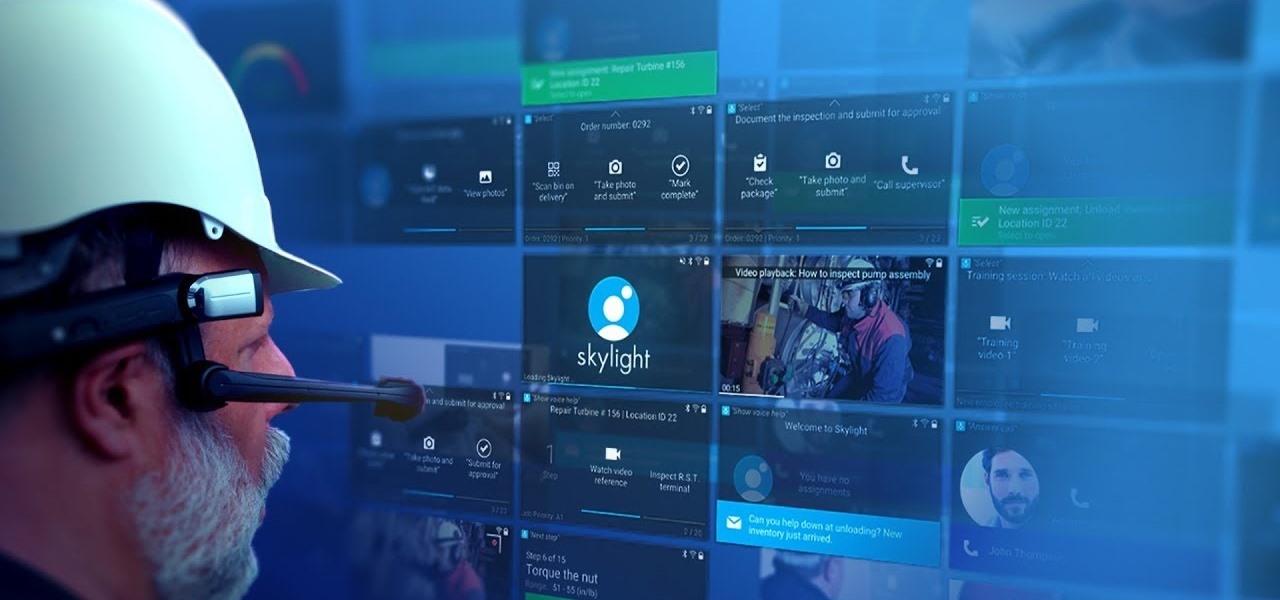
Augmented reality business followers, we've got good news and bad news. First, the good news: Upskill closed another round of funding, this time led by strategic investors Cisco and Accenture. (Well, this is probably bad news if you're competing with them on the enterprise AR front.)

Meta Company has filed its response to allegations that the user interface for their augmented reality headsets infringe on six patents owned by a mostly-unknown company.

While Apple's tech used for Face ID on the iPhone is impressive, it's debatable whether it's more convenient than Touch ID. There are also concerns that your face could be used to track shopping patterns or be seen during mass surveillance by intelligence agencies. More importantly, it could be easier for law enforcement, and even thieves, to force you to unlock your iPhone.

While Meta Company has agreed to a settlement in its lawsuit against a former employee and his company, they find the tables have now turned on them in the form of patent infringement allegations from another entity.

Cruise Automation follows Waymo's and Uber's lead with its debut of a beta version of an app-based driverless ride-hailing service for its employees in San Francisco, ahead of a possible launch of a full-fledged commercial offering within four years.

Volvo Cars' "all-electric" announcement last week was seen as a direct threat to Tesla's electric vehicle (EV) and driverless lead, but German auto giant Volkswagen (VW) says it is in a better position to challenge Tesla.

Waymo claims in court documents filed yesterday in its lawsuit against Uber that ex-Uber CEO Travis Kalanick knew that former Google engineer Anthony Levandowski was in the possession of stolen documents while employed at the troubled ride-sharing firm.

Cruise Automation is actively seeking to recruit a lead engineer to head its development efforts of 3D maps with expertise in city environments, signaling the GM driverless unit's move towards a mobility-as-a-service business model.

Uber's struggles are expected help Lyft get ahead in driverless development as it confirms its third partnership with autonomous tech company nuTonomy today.

Yep, Google just put in place a new thing called the dun dun duuuun .... "Device Catalog!" No, not like the Macy's catalog of your smartphone dreams. This is quite the opposite.

Uber's year is going from bad to worse, and they may be subject to a potential criminal probe in the ongoing Waymo legal battle.

All Galaxy S8 models apparently weren't created equal. According to numerous user reports, it appears that Snapdragon-powered Galaxy S8 variants are using an older flash storage standard than what Samsung was originally advertising.

WhatsApp sneakily made some security changes to iCloud backups without your knowledge, ladies and gents. Not that strengthening security is a bad thing, but still!

Since the dawn of time—well, that maybe a slight exaggeration, but let's roll with it—sly entrepreneurs have been swindling the general public with inferior products for the sake of saving a few cents. Nothing is sacred when it comes to saving money: caviar, cheese, or even baby formula. Hell, there's even an entire book dedicated to the history of food swindling.

I mentioned in 2015 I wanted to start a 'DoXing' series, and since I havent seen this on Null Byte, I am now going to introduce this to the community.

Those of you who have been a part of the Null Byte community for even a short while know that I sincerely and firmly believe that hacking is the most important skill set of the future.

Welcome back, my novice hackers! As most of you know by now, a notorious commercial, legal hacking group named "Hacking Team" was recently hacked. As part of the hack, thousands of emails and other material on their servers was divulged. Among the material released were three zero-day exploits. In this tutorial, we will walk through the steps to load one of them, which has become known as the CVE-2015-5119 exploit.

Welcome back, my nascent hackers!

When Google Play Music launched a few years ago, I ditched iTunes and began using the service as my one and only source for listening to my personal music library. While All Access is great, I still prefer the radio feature on Spotify, so I still use that to discover new music.

Investing is like exercise—we all know we should be doing more of it, but we often just can't find the time. I mean, really, who's got the hours, inclination, and skill to pour through volumes of data and put together a balanced yet sophisticated portfolio of investment vehicles tailored specifically to optimize their returns while mitigating potential risks. Not me, that's for sure.

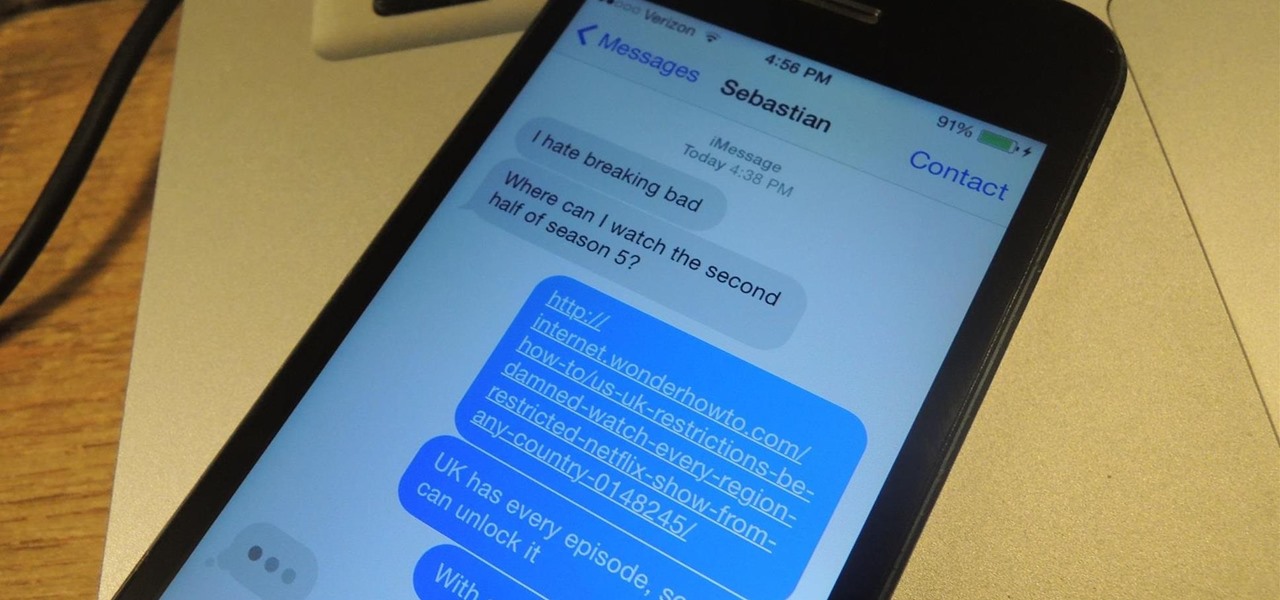
NSA aside, Apple makes it difficult for users to extract and download text messages from their iPhones onto a computer. For whatever reason (legal, devious, neurotic, etc), we've all found a time where we'd like to save backups of certain meaningful, important, or perhaps incriminating conversations (including all MMS or iMessage pictures and videos). While there are a handful of third-party applications that can help with this process, the majority of them cost money and implement certain te...

My favorite type of video game is first-person shooters, and the one that started it all for me was GoldenEye 007. There was just something about the controls, fast-paced action, and free-roaming environment that got me hooked.

The 8-bit NES may have ruled the late-eighties, but the SNES took over the early-nineties with its 16-bit graphics and 3D-like gameplay on titles like Star Fox and Dirt Racer. When 32- and 64-bit consoles came out in the mid-nineties, the Super Nintendo took a hit, but with the rise of the Internet, created a huge emulation community in the aftermath.

This week, Silk Road was shut down for good when the FBI seized the anonymous online marketplace after Ross Ulbricht, aka Dread Pirate Roberts, was arrested. This comes just two weeks after another illegal marketplace called Atlantis shutdown. However, there are plenty of other black markets hiding within the Deep Web, freely and anonymously accessible using the Tor browser.

Why unlock your Samsung Galaxy S3 to use with a different SIM card? One possible reason is that you love your phone, but not your cellular provider because of the poor service or an unreliable connection. If you purchased a Samsung GS3 with AT&T, T-Mobile, etc. on a contract, it might be locked for a specific amount of time called the contract period.

Unlocking your Samsung Galaxy S4 so you can use a different SIM card isn't the easiest thing in the world. In the states, unlocking cell phones was actually illegal, despite the White House's disapproval, though, a recent bill has making its way to the House floor and has made it legal again.