Much to the chagrin of the National Wildlife Humane Society (and a long list of others), Tuscon restaurant, Boca Tacos y Tequila, will be serving African lion beginning February 16th. For $8.75, patrons can sample the second most deadly animal in the world in a taco. The Mexican restaurant specializes in exotic game; other menu selections include python, alligator, elk, kangaroo, rattlesnake, and turtle. However, the latest addition has caught restaurant owner Bryan Mazon a lot of flack.

Just the other day, we featured Perry Watkins' "Wind Up" mini car, plus his extreme lowrider, the "Flatmobile". Both impressive.

Upon first glance, one may think Mark Suppes is just another thirty-something-year-old dude living in Bed-Stuy, Brooklyn. However, the Gucci web designer by day has a significant (to say the least) project-in-progress by night. The amateur scientist bicycles to a non-descript building in Brooklyn to chip away at his homemade nuclear fusion reactor. BBC reports:

Don't get too excited. The answer? It's not. However, this James Bond inspired road rage mod is still prettttty awesome. Colin Furze's scooter can shoot up to 15 foot flames. Furze, a plumber, built it because he was sick of other drivers cutting him off.

The second patent trial between Apple, Inc. and Samsung Electronics has effectively ended, with a jury ruling that Samsung did in fact infringe on two of Apple's patents. The reward of $119.6 billion is far lower than the $2.2 billion in damages that Apple seeked.

Rooting your Android phone offers more features (like overclocking). I am not responsible for anything you do. M'kay? I don't know if this will work for all phones, but hopefully it works for you.

Itching to make your own guerrilla-style street art on the side of buildings, freeway overpasses, and abandoned billboards? The beauty of street art is that you don't need an expensive canvas or frame to display your creative expression.

Starting in 1961 the FBI and an army of other non-believers, wiretapped MLK. All found nothing but gossip. No one was able to nail him with any evidence of sedition.

No matter what word game you're playing, whether it's Scrabble or one of its near-homogeneous counterparts like Lexulous, Wordfeud or Words with Friends, one of the easiest ways to stay on top of your opponent is knowing all of the legal two-letter words you can play. You're not going to win by only playing two-letter words, but there are definitely occasions when the game could slip from your hands by not playing them.

www.jailbreakme.com has recently created a new way to Jailbreak any iPod Touch, iPhone, or iPad, regardless of the firmware it is running. It is EXTREMELY easy! If you were thinking about Jailbreaking, but were afraid you did not have the technical abilities to do so, now you can! What is "Jailbreaking?"When someone says that their iPod, iPhone, or iPad is "jailbroken," they mean that they have installed Cydia, a third-party app store.Why Jailbreak? Why not just stick with the original App St...

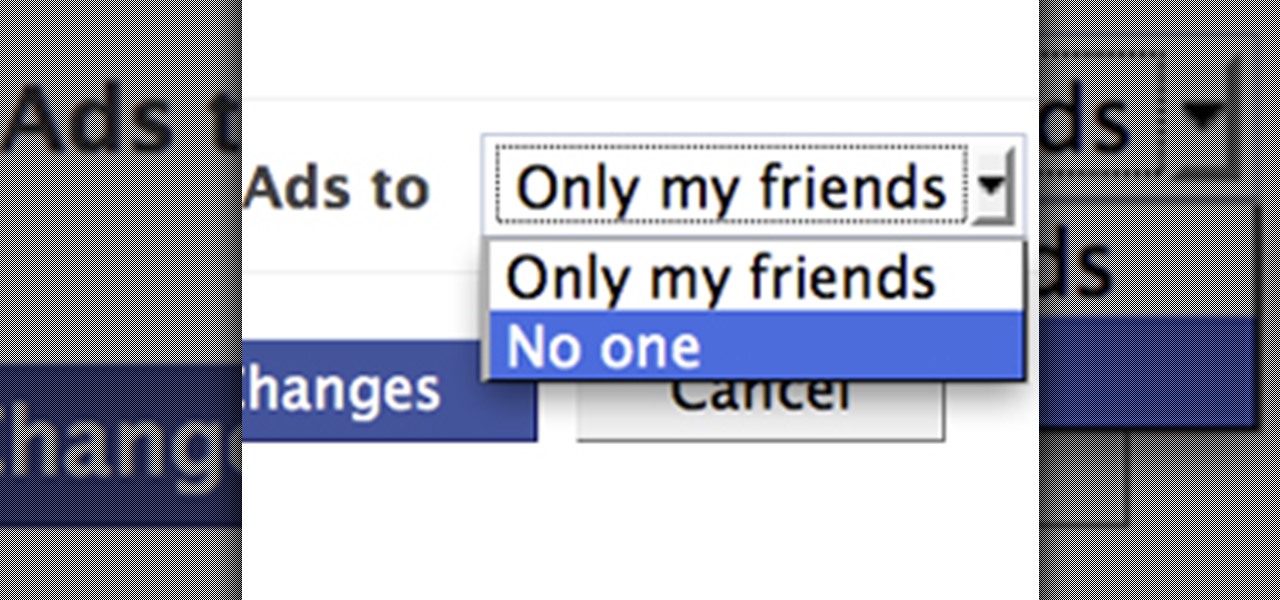
Facebook is constantly evolving, and lately it seems like a bad thing, at least for its users. First, you had to opt out of Instant Personalization, which shared your personal information with Facebook's partner sites. Then, you had to take drastic measures to secure your home address and mobile number from third-party apps and websites. And now?—Now you need to opt out of Facebook Ads.

I remember a time when I had to rent a VHS from the local video rental store. It wasn't all that bad, with the only real annoyances being the trip to and fro, having to rewind the movie and the possible malfunction of my VHS player, which liked to eat tape from time to time.
Collapse At Hand Ever since the beginning of the financial crisis and quantitative easing, the question has been before us: How can the Federal Reserve maintain zero interest rates for banks and negative real interest rates for savers and bond holders when the US government is adding $1.5 trillion to the national debt every year via its budget deficits? Not long ago the Fed announced that it was going to continue this policy for another 2 or 3 years. Indeed, the Fed is locked into the policy.

Last Friday's mission was to accomplish solving HackThisSite, realistic 2. This second mission in a series of realistic simulation missions was designed to be exactly like situations you may encounter in the real world, requesting we help a friend take down a racist hate-group website.

Last Friday's mission was to accomplish solving HackThisSite, realistic 1. This is the first in a series of realistic simulation missions designed to be exactly like situations you may encounter in the real world. This first mission, we are asked to help a friend manipulate the website voting system for a Battle of the Bands vote count in his favor.

How many people use the big search engines here? I'm going to estimate 90% of everyone on WonderHowto uses one of the following on a regular basis: Google, Bing or Yahoo! Search. The question is: are you in that 10%? You should seriously consider dumping Google search for DuckDuckGo. Why? DuckDuckGo does not track you.

Welcome to the Goodnight Byte for HackThisSite, Basic Mission 4. In Friday's session, we tackled some coding in Gobby. Nothing special, just a few modifications to the NullBot script we made a few session ago, and some education on regular expressions. Apart from coding, we did our scheduled HackThisSite mission. We had to take on some JavaScript, which was a new thing for Null Byte. This mission taught us about client-side HTML manipulation through JavaScript injections. This just means that...

Welcome to the closing of the second HackThisSite and programming Community Byte. First and foremost, I would like to ask that people start showing up on time to the Community Bytes. If you need help converting your time zone to PST, go to Time Zone Converter. When users do not show up on time, we have to go backwards and catch everybody up. This wastes time and will also make other users' experience less enjoyable when they have to watch and listen to the same thing 100 times. Punctuality as...

With the rather large success of the Community Byte activities, both programming and HackThisSite, I have decided to continue to do both activities every session! With that said, when programming sessions occur, they will be lead by Sol Gates in Gobby. Also, the programming mission will no longer be to code a tool, we have changed it to be even more "noob friendly". This means that instead of coding a tool, you will be walked through puzzles and challenges that must be solved by coding a scri...

This is the Windows OS counterpart to my tutorial on how to burn the new XDG3 formatted games on Xbox 360. Microsoft invented a new disc format system to trump piracy, it's called XDG3. XDG3's standard is to burn a whole extra gigabyte of data to the disc, to allow more content, but more importantly for stopping piracy. This extra gigabyte of data makes it impossible to burn or rip a game the traditional way. So how on earth can we burn our fully-legal back-ups that we should rightfully be ab...

Our mission for this week's Community Byte was to create a Python program to crack web-based passwords, like the ones you would see on an email or router login. I wanted it to be universal in the sense that it could be easily modified and adapted to another website just by changing a few variables. That was a success! Even though people weren't on time to the coding session, everything went well.

This is Null Byte's fourth part in a series about fully securing our computers (Part 1, Part 2, Part 3). In our last Null Byte, we went over how to encrypt an entire operating system to protect our data, however, this doesn't fully protect us. In the case of legal extortion, the government can actually make you give up your cryptographic key to your computer so that they can look through it.

Welcome to the second Goonight Byte! Our second coding session was kindly hosted by th3m, so props to him for letting this happen.

One of the biggest advantages iOS has over Android as a mobile platform is how readily and fully it has embraced mobile gaming. There are over 200,000 games available in the Apple store, compared to approximately 100,000 in the Android Marketplace. As an Android-using gamer, this has always bothered me.

For most street artists, it takes a considerable amount of time to paint large art installments on the walls of urban structures. The more time it takes, the better chance there is of getting caught, since nearly all of the rogue artwork is slapped on the sides of city and privately owned buildings.

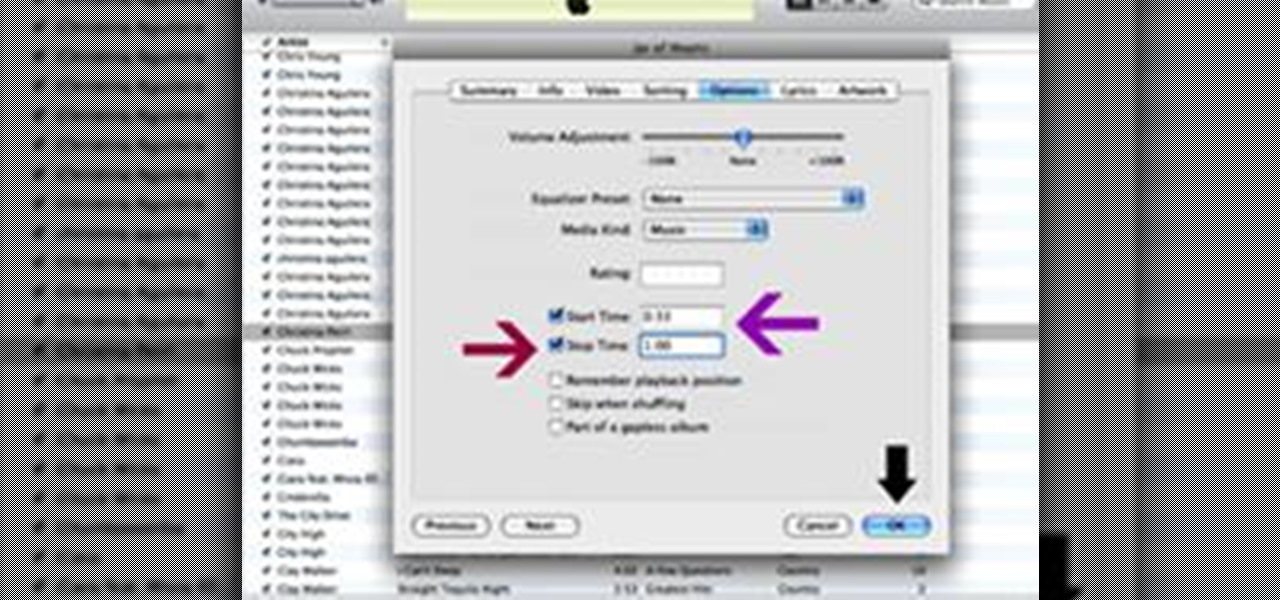
Granted the iPhone is an awesome phone... but their choice for default ringtones kind of, well, stinks. They have plenty of apps you can BUY to PURCHASE ringtones... but why waste money when you can make an unlimited amount of ringtones yourself forFREE? At first glance, it looks complicated and confusing, but I'll break it down so simply, you'll be making ringtones for everyone in iTunes.

In the dojo, what ISN’T said is often as important as what IS said. To most of us who’ve been raised in the USA, the reticence we encounter in the dojo can be off-putting. American society is very “content” oriented. Our legal contracts, for instance, run for pages and pages. Everything needs to be spelled out. In “context-oriented” societies there is far less reliance on such a literal approach. Much more importance is placed on the relationship between the two parties entering into an agree...

And Dumbfounded Most Watching Game 1 of 2010 World Cup I just finished watching the Mexico - South Africa 2010 World Cup opener and boy was it a good one. The finish of a tie, wasn't totally cool to me, until I realized what I missed.

If you're a frequenter of Null Byte, I bet you have at least some interest in information security. Furthermore, you have a hobby that if applied in certain ways, will get you arrested. I've received quite a few messages from the community here about federal cybercrime law and how it applies to them, so I decided to get together with my lawyer to come up with some answers.

Eventually, we plan on doing some root the box competitions here at Null Byte, but we're still looking for a server to play on. Anyone want to donate one? You won't regret it. Root the box is like 'king of the hill', except you have to hack a server and maintain access. Each server will have numerous known security holes, but until then, let's get back to the regular weekly coding sessions and realistic hacking missions on HackThisSite.
Does this video prove that otherworldly intelligent life has visited Earth? No. It does not prove anything other than there are designs ‘etched’ onto the surface of a field. Does the video immediately above prove that otherworldly intelligent life hasn’t visited Earth? Yeah, you saw it coming; no, it proves nothing more than humans are able to ‘etch’ designs in a field of grain.

We'd like this to be one of the last HTS mission announcements, at least for now. As soon as Null Byte finds a server to play with (anyone want to donate one?), we are going to start doing root the box competitions, which is like king of the hill, except you have to hack a server and maintain access. Each server will have numerous known security holes. But for now, back to the normal flow of things...

Technology in computers these days are very favorable to the semi-knowledgeable hacker. We have TOR for anonymity online, we have SSDs to protect and securely delete our data—we can even boot an OS from a thumb drive or SD card. With a little tunneling and MAC spoofing, a decent hacker can easily go undetected and even make it look like someone else did the hack job.

We're aiming for this to be one of the last HTS mission announcements, at least for now. As soon as Null Byte finds a server to play with, we are going to start doing root the box competitions, which is like king of the hill, except you have to hack a server and maintain access. Each server will have numerous known security holes. But, for now, back to the normal flow of things...

In this series, I'll be exploring electromagnetic weapons, how to build them, their function and application to the future, and the amazing possibilities electromagnetism has to offer. First, the electromagnetic pulse generator, or EMP. You've probably heard of these before, and their devastating effects on electronics. A simple EMP consists of a capacitor, transformer, trigger, and coil of copper wire. This, when triggered, would produce an intense magnetic field for a brief period, similar ...

The community tore up the first realistic mission last week. You've applied the techniques learned in the basic missions to a real scenario, so I'm pretty content. The realistic missions are where the learning gets intense and where we can apply real knowledge to extremely realistic situations. We will also be continuing the normal Python coding and hacking sessions. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, f...

Community byters, it's time to get serious. We are finally moving on to the realistic missions in HackThisSite. This is where the learning gets intense and where we can apply real knowledge to extremely realistic situations. We will also be continuing the normal Python coding and hacking sessions. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers to aspiring hackers.

Before you start snapping away and submitting your photos, please take some time to read the official rules below!