Instagram's controversial terms of service update this past month has spurred an onslaught of dismay and anger from users of the popular photo-sharing social network. The specific set of the new terms that set off this firestorm basically said that businesses could use your uploaded photos for advertisement, without you receiving any of the profit.

Before lead was removed from gasoline, lead from car exhaust got into the air, was breathed in by kids, lowered their IQs, and increased crime rates (there is a very strong correlation between IQ and criminal behavior).

Here's how to make a simple form of a slow burning fuse from materials around the house. WARNING: Ignition of an incendiary or explosive material may not be legal in your area, so check local laws before attempting. Use of this video content is at your own risk.

Cooking isn't something that interests me much, unless it results in a fast burning fuel and a successful rocket launch!

We all expect a little something on our birthdays, so why should those expectations drop when we are talking about our gaming systems? Microsoft has started handing out birthday gifts to its Xbox LIVE Gold members with their new MyAchievements rewards program. Those eligible for the gift will automatically receive the offer on their dashboard. To be eligible for the free gift, you must be:
The big question this week would be the controversial Obamacare mandate. And heres the answer: Yes. Obamacare passes Congress' filters and is now an official OK. Texas college hacks drone in front of DHS — RT.

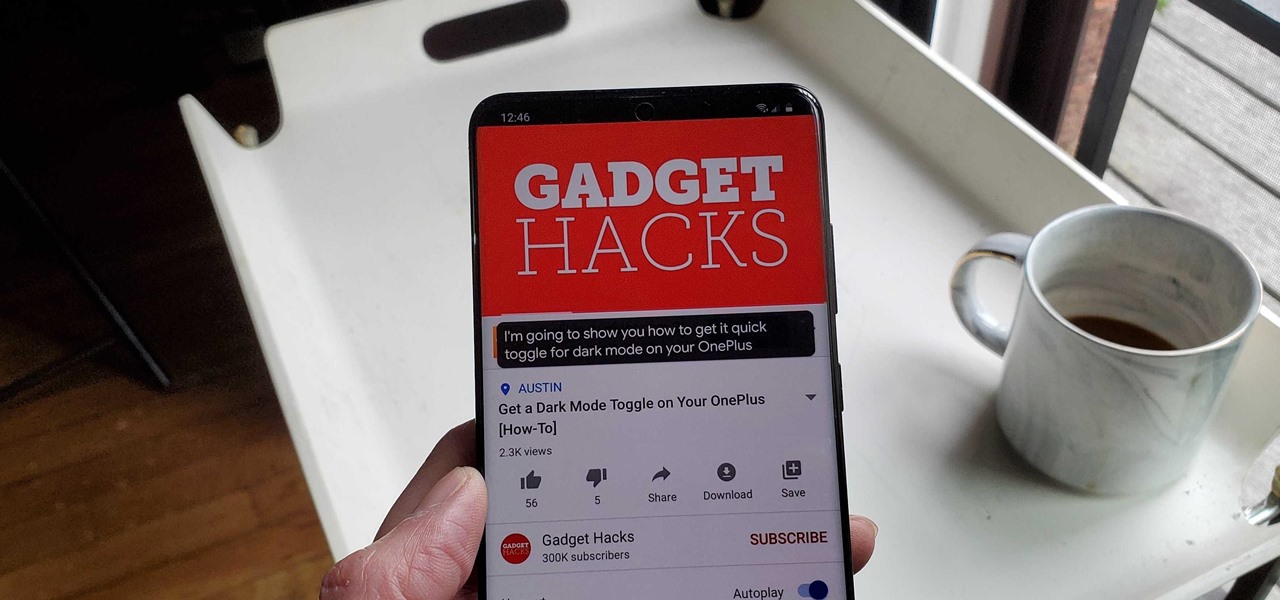
First of all you shall need a program called "Disk Inventory X". You can download this program from the link Once you have downloaded you have to install this program. Now launch "Disk Inventory X". This shall take some time to load because it processes your hard drive and looks at all the files and folders. This program provides you a visual representation of the files that are there in your hard drive. Therefore for every folder that is shown in this application it shows...

Since the days of Archytas, rocket propulsion has been the Holy Grail of aeronautics. Thanks to Galileo's inertia, Newton's laws of motion, and the "father of modern rocketry," Goddard, space is not a complete mystery anymore. Rocket-powered aircrafts have evolved from the first liquid fuel rocket in 1926, to the Soviet R-7 which launched Sputnik, to NASA's Saturn V that propelled Apollo 11 to the moon. Today, even billionaire tourists can enjoy space, like Microsoft's Charles Simonyi and Cir...

Learn how to convert from scientific notation to standard form by watching the above math video. To change a number from scientific notation to standard form, move the decimal point to the left (if the exponent of ten is a negative number), or to the right (if the exponent is positive). You should move the point as many times as the exponent indicates. Do not write the power of ten anymore.

The last time we heard from Meta, the makers of the Meta 2 augmented reality headset, things looked pretty bleak. Now, as several new facts have come to light, we have confirmation regarding the beleaguered company's fate: Meta is done.

Google just bought a huge chunk of HTC for $1.1 billion. They're bringing in around 2,000 employees, mostly from the hardware division, and these folks will presumably work under hardware chief Rick Osterloh. There's a massive patent portfolio involved, too, so stop me if you've heard this before — Motorola, anyone?

Most of us skip through documents like privacy policies and EULAs (end-user license agreements) because they're long and boring. But, as Congress just passed the SJR34 bill in early April, you're probably a little concerned about your personal data, so we summarized the privacy policies for major ISPs and mobile carriers in the US.

"It just ticked me off," he said. In March 2011, Neil Singh paid $50 to back the Hanfree iPad stand on Kickstarter. The project was funded at $35,000, but production stalled, and the delivery estimates kept getting pushed back.

In the recent hit movie Furious 7, the storyline revolves around the acquisition of a hacking system known as "God's Eye" that is capable of finding and tracking anyone in real time. Both the U.S. spy agencies and an adversarial spy agency (it's not clear who the adversary is, but the location is "beyond the Caucasus mountains," which could imply Russia?) desperately want their hands on this system.

Everyone loves the beach, but some like driving, too. The best thing is to only drive on the sands where it's legal. And you may need a permit to do beach driving. But driving on the beach is a hoot. Getting stuck in the sand – not so much. Keep moving forward with these tips.

Is your neighbor creating a ton of racket? Suffering in anything but silence? It can be hard to approach a noisy neighbor without starting a big riff. Follow these steps to get the quiet you deserve.

Doing a shot is more art than science. Here's one way to hone your barroom style. You Will Need

Drinking too much is bad for your health and your wallet. Here are a few simple strategies for cutting back and keeping it in moderation.

Learn how to pick a horse at the racetrack. Sure, you could just go with your gut. But if you want better odds, make your decision based on these factors.

A swamp fan is an air conditioning substitute that blows air over cool water to cool a room. If you live in an AC-free dorm room, house, or apartment, it's not too hard to build one yourself, and this video will show you how to do it.

The enterprise sector is where the money is for augmented reality at the moment, and remote assistance apps are the go-to app for many enterprise customers. We took a look at the leading apps and platforms from this category, from the top contenders to the underdogs with unique features.

To borrow from the canon of Game of Thrones, what is dead may never die. And while the Meta Company that we knew this time last year is no more, the patent infringement lawsuit filed against the company lives on.

Apparently, it's Google Week for the augmented reality business. Now that ARCore has a firm foothold in the app ecosystem, Google is making a case with educators and marketers that the apps should have a place in schools and campaigns, and the company is also encouraging developers to learn how to build apps using ARCore.

In what's becoming something of a regular occurrence, Magic Leap has yet another internal, unforced error on its hands. Thankfully, this time it's not about legal skirmishes or theft, but a rather unusual break from company protocol that has been quickly swept under the rug.

The next-generation Audi A8 to launch in July is expected to be the world's first Level 3-capable production car to go on sale in retail channels.

Stakeholders in the driverless industry are anxiously awaiting changes the US Department of Transportation (DOT) is making to self-driving vehicle guidelines.

Hello everyone! I hope you are having a great day so far. Today, instead of caring about networks we are going to talk about subnetting based on host requirements as promised in my first article about subnetting. Just like in the previous articles we will jump right into the examples because that's the best way to learn.

Before I continue with a topic on strings, we first require some fundamental understanding of how memory works, i.e. what it is, how data looks in memory, etc. as this is crucial when we are analyzing vulnerabilities and exploitation. I highly suggest that your mind is clear and focused when reading the following article because it may prove to be confusing. Also, if you do not understand something, please verify all of your doubts, otherwise you may not completely understand when we touch on...

Arcades have long faded away from popularity, but their legacy is being kept alive thanks to emulators and the avid fans who grew up loading quarters into all of those coin-op games. Although nothing beats an actual arcade environment, my favorite emulator from the early 2000s has found a new home on Android, and with it a second life.

The big fireworks day is almost here, but most of you are limited in what you can do when it comes to celebrating the Fourth of July with a bang. Unless you live in a dry area prone to wildfires, one type of fireworks you can probably still legally buy are sparklers.

BitTorrent—corporations hate it with a passion, but the people love it. The notorious file-sharing protocol was responsible for 36.8% of all upstream Internet traffic last year, as well as 10.3% of all traffic.

Video: . The author started with a written introduction of the importance of the executive summary as part of the business plan.

We've all seen the breathtaking, colorful photos of the Eagle, Egg and Cat's Eye Nebulae. You may not recognize them by name, but you've seen them, whether in astronomy textbooks, magazines, websites, album covers, or tee shirts. They are some of the most striking photographs ever taken from the Hubble Space Telescope (HST).

When it's hard to hear what's being said, subtitles give you clarity where audio falls short. Thanks to Android 10, your Galaxy S20 now lets you enable a live transcription of your phone's internal audio stream, meaning you can get closed captions in virtually any app — even if the app doesn't otherwise support them.

Augmented reality's status as a new storytelling medium has already led to the reinvention of filmmaking and journalism.

The international profile of augmented reality startup Nreal continues to quietly rise thanks to gradual updates and various strategic branding opportunities.

After entering into settlement talks with Epic Games over the gaming giant's trademark challenge, Nreal is now ready to open up the floodgates to potential early adopters in the augmented reality space.

What if you could combine the fun of Halloween with the process of learning? Well, if you were wise enough to have already snagged a Magic Leap One device, we have good news: the app you're looking for is here, and it's called Zombie Math.

When it comes to building luxury cars, Bentley certainly knows what it's doing. However, when it comes to building an AR app, Bentley is looking less Continental GT and more Geo Metro.

The longer it takes Apple, Snapchat, Facebook, and other tech giants to build their own version of augmented reality headsets and smartglasses, the longer runway of practical experience Microsoft gains with the HoloLens and its sequel. The latest example: AR cloning.