
News: Blood Blade Starfighter
Alter Evo on Flickr has created this amazing starfighter and service unit vehicle. This is what he says about it:


Alter Evo on Flickr has created this amazing starfighter and service unit vehicle. This is what he says about it:

The Job Board is a weekly entry of the most ridiculous Cinematography related jobs posted online. Interviewing DP's for Docu-short (SCV)

Wow, what can't Google do? Check out the winter Olympics, ride the Trans-Siberian railway, explore the world's largest airplane graveyard, and now, locate Chilean earthquake victims.

The X-Ray Vision-aries Blog has compiled a list of YouTube's 100 Coolest Science Experiments. I particularly enjoy their introduction to the selection:

Many new, emerging technologies are coming to our faces. Some are already here, and it's hard to tell what's what. We've taken a deep dive into the three main types (virtual, augmented, and mixed reality), but if you need a quick primer, this infographic will do the trick.

If you ever want to try rebooting your car batteries before calling a towing service, make a solution out of 1 ounce of epsom salt dissolved in warm water, and apply the solution to the battery cell before starting your car.
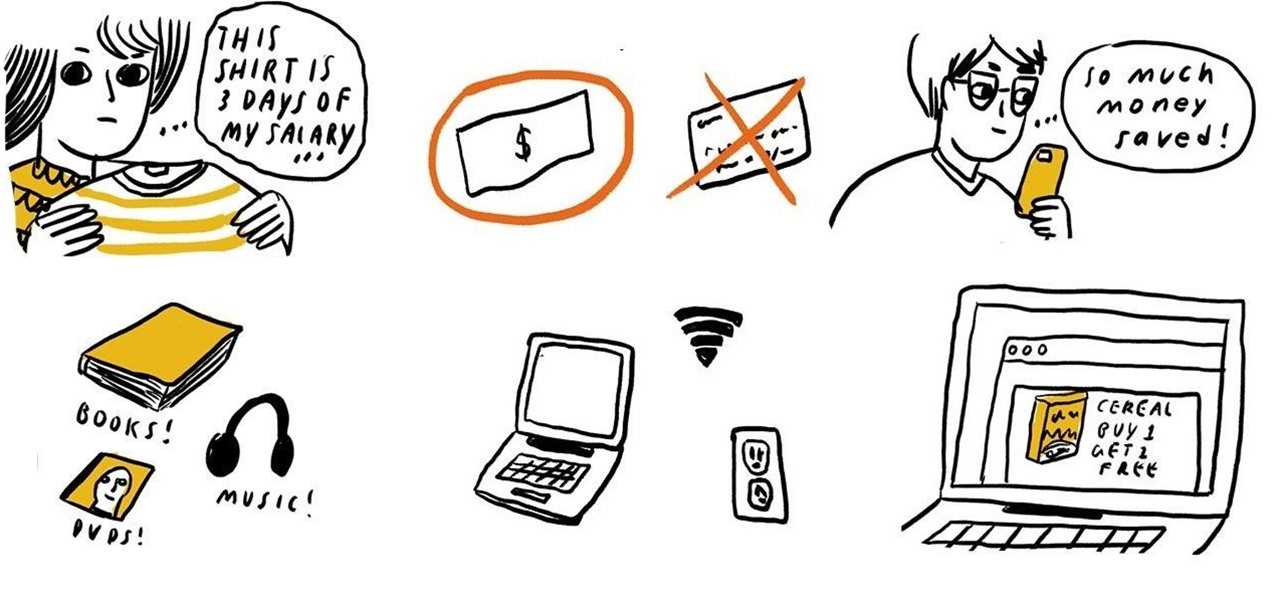
Are you tempted to splurge over your budget on an expensive restaurant meal or cool new jacket? Before you make an impulse purchase, imagine how much that indulgence costs in terms of hours of work based on your current salary.

We love Google Now around here (okay, maybe I do more than others), and today Big G snuck in a nice little functionality when searching for an artist. Exclusive to the US for now, when you enter an artist or band into Search, you'll be presented with listening options for apps you have installed on your device.

When Korean electronics giant LG debuted its next-generation flagship phone at a London press event 2 weeks ago, the only question that remained unanswered was the timing of its release. As the 5.5-inch qHD phone hits stores in Korea, folks in the U.S. market patiently awaited a stateside debut.

Samsung has announced that their latest flagship device, the Galaxy S5, will ship with over $500 worth of exclusive, pre-paid, and discounted subscriptions from leading mobile content and service providers.

Now might be as good a time as any to change over from the 'Uncarrier' to Ma Bell. For a limited time only, AT&T is offering T-Mobile customers 450 bucks in credit to change to their team. Folks jumping ship from the Big Magenta could earn up to $250 in credit for trading in their smartphone and another $200 credit for transferring service. AT&T sure is working hard to snag up new subscribers, and if you've been looking for a change in carrier and to save some money to boot, you might just wa...

We all hate spam. It is a waste of time and very troublesome. So here is a way i found to avoid spam. I am not responsible for anything that happens. M'Kay?
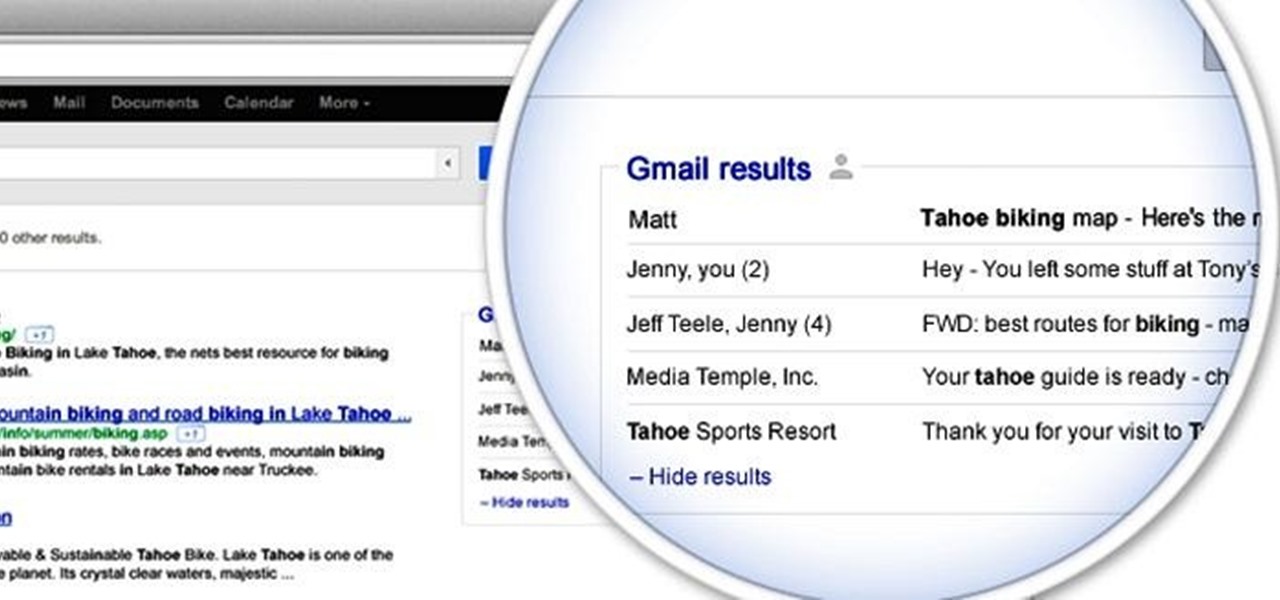
Google is rolling out a new feature that will integrate your Gmail account with Google searches. The feature will add results pulled from your email correspondences to create more "personalized" Google search results. Google is currently doing a test run of the service. To activate it for your account, head on over to this page to sign up. It's currently restricted to the English version of the site, and for those with @gmail.com email addresses (not available on Google Apps accounts). And be...

With Facebook and Twitter dominating the world, playing chess opposite a real, touchable person is no longer necessary. With the ChessBot, you can now play on a real chessboard remotely - the next best thing to in-person play.

We've all tried writing with lemon juice (a.k.a. invisible ink). It's a mess. And the main draw back is definitely efficiency.

Friggin' brilliant. This is hardly a viral video. No sound. Black and white. But it is 100% pure concept.

A cell phone is capable of all kinds of tricks, but you can use your cell for more than just photos, texts, and phone calls. Here are some of our favorite mobile phone services, such as Shazam and AQA. Use 5 different cool services on your cell phone.

Here at WonderHowTo, we are often presented with morally questionable HowTo's. When it comes to stocking our library, we have to weigh in the community value of indexing tutorials with potentially negative repercussions. Where is the line when it comes to areas like weapons, sex, and drugs?

In my recent Darknet series, I attempted to connect the dots on the Deep Web. I covered the two largest anonymity networks on the Internet today, Tor and I2P. While my initial four articles were meant as an introduction, I ended up receiving a lot of interesting comments and messages asking the technical differences between the two. I'd like to thank all of you for letting me know what was on your minds, as you should always!

Eventually, we plan on doing some root the box competitions here at Null Byte, but we're still looking for a server to play on. Anyone want to donate one? You won't regret it. Root the box is like 'king of the hill', except you have to hack a server and maintain access. Each server will have numerous known security holes, but until then, let's get back to the regular weekly coding sessions and realistic hacking missions on HackThisSite.

We'd like this to be one of the last HTS mission announcements, at least for now. As soon as Null Byte finds a server to play with (anyone want to donate one?), we are going to start doing root the box competitions, which is like king of the hill, except you have to hack a server and maintain access. Each server will have numerous known security holes. But for now, back to the normal flow of things...

Technology in computers these days are very favorable to the semi-knowledgeable hacker. We have TOR for anonymity online, we have SSDs to protect and securely delete our data—we can even boot an OS from a thumb drive or SD card. With a little tunneling and MAC spoofing, a decent hacker can easily go undetected and even make it look like someone else did the hack job.

We're aiming for this to be one of the last HTS mission announcements, at least for now. As soon as Null Byte finds a server to play with, we are going to start doing root the box competitions, which is like king of the hill, except you have to hack a server and maintain access. Each server will have numerous known security holes. But, for now, back to the normal flow of things...

The community tore up the first realistic mission last week. You've applied the techniques learned in the basic missions to a real scenario, so I'm pretty content. The realistic missions are where the learning gets intense and where we can apply real knowledge to extremely realistic situations. We will also be continuing the normal Python coding and hacking sessions. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, f...

In this article, I'll show you how to send SMS messages with Python. You'll need Python 2.7 or later, urllib and urllib2. The code basically uses an online text messaging service to "POST" html data, as if a person was entering the data themselves. The uses for something like this are unlimited. For example, I modified the basic code so I would receive a text message letting me know every time someone rang my doorbell. The program could interface with Arduino through a serial port, and send d...

Community byters, it's time to get serious. We are finally moving on to the realistic missions in HackThisSite. This is where the learning gets intense and where we can apply real knowledge to extremely realistic situations. We will also be continuing the normal Python coding and hacking sessions. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers to aspiring hackers.

Friday's Community Byte was weird. The intent was to do a HackThisSite mission, but upon time to begin, everyone in there was programming without my assistance, with the help of Sol Gates. This is great! It's really awesome that everyone enjoys programming that much and will make the effort to learn even when I am not present. So, a tip of my hat to Mr. Sol Gates and the rest of you fine people.

In these weekly Scrabble Challenges, so far we've covered two-letter words, double bingos, high scoring moves, triple-triples, last moves, parallel plays, phoneys and opening moves. For this week's puzzle, we're revisiting the strategy for opening moves.

A phoney word in a game of Scrabble is basically a non-valid word, either played or considered being played. Why? To fool the other player and go from losing to winning. It's perfectly acceptable in Scrabble play, but only if you don't get caught. If the other player challenges your play, then you'll be forced to remove it and your turn will be skipped. That right there—not fun.

This Null Byte is the first part in a mini-series on the art of Social Engineering. I will be teaching you how to effectively defend yourself against it.

It's been a long journey for Netflix users. At first, it was a rough ride as Netflix struggled to find its place in the homes and hearts of movie watchers everywhere. Once monthly subscriptions bumped off the pay-per-rental charges, Netflix soared to great heights, known for their flat-fee unlimited rentals without due dates, late fees, or shipping and handling fees. And it was smooth sailing when streaming services were incorporated into monthly plans, with customers being able to rent DVDs ...

Bourbon is the ultimate American spirit, considering the barrel-aged distilled spirit was originally produced in an area known as Bourbon County, Kentucky. To meet the legal definition of bourbon, it must be produced in the United States, must be created with at least 51% corn, and aged in new oak barrels. There are two types of bourbon whiskeys—straight and blended. Straight bourbon means that the bourbon has been aged for a minimum of 2 years, and has no other coloring or flavoring added. B...

More than a year ago, Twitter rolled out the first phase of its Promoted Tweets ad service, which consisted of selected tweets from advertising partners like Best Buy and Sony Pictures receiving "promoted" exposure in the search results pages on Twitter and in the trends lists. These ads were clearly labeled as such, so it was never any real bother to Twitter users.

Advancements in technology usually lead to the miniaturization of old technologies, and video games are no exception. Since at least 1990, game hardware manufacturers and enterprising DIY electronics enthusiasts have poured their efforts into making full-size video game consoles smaller, even handheld. And for good reason—who would have ever played a black and white Game Boy if they could have had an actual NES in their pocket?

Do you remember when video games came on tiny chips in plastic cartridges? When the CD and 3D graphics just meant ugly games with long load times? Before epic cinematics, spoken dialog, or cordless controllers? Do you still have all of your old games and lament that the consoles, cords, and controllers required to play them have either been stolen by exes or broken while moving apartments?

These are the KGB Agent Guidelines as taken from 542542.com/guidelines. kgb Guidelines

Last week Amazon set their sights on the mobile app market, launching their Appstore for Android. This week they're attacking Android devices once again, but that's not all—they're getting into the online storage biz.
On Thursday, March 9, there was a news story on the evening news about Khan Academy (NBC News). The story began when Sal Khan started tutoring his cousin in 2004. Since he was in Boston and she was in a different city, he decided to make and post videos on YouTube so anyone could watch the videos. Later he added videos for her brothers and for people that contacted him with requests for other videos. During this time Sal had a job that he later replaced with another job. Today Sal has 2010 vi...

These impressions are coming from a person completely new to the Final Fantasy Online world. Never played FF 11 or the FF 14 Beta. This game is not friendly to new people. The account creation is a Kafka like experience in things that don't make sense. For the game itself, the beginning tutorial is awful and does not really teach you the basics of combat. Here is a small breakdown of my opinions, with the good points first so that they don't get overshadowed by the negatives.

West LA Seido Karate-do embeds its personal protection program into its on-going classes. Private instruction in this aspect of Seido can also be arranged with Kyoshi on an individual basis.