The Nexus Player is one of the most robust set-top streaming devices on the market. This is mainly due to the fact that the base software it runs is a direct fork of Android, which is a very powerful operating system itself.

With over a billion monthly active users, it seems that Facebook is nowhere close to being dethroned as the most popular social media service in the world (sorry, Ello). While their stats may be impressive, it doesn't mean that Facebook is as good as it can be.

Many modern Android devices use a display technology called AMOLED. These screens differ from traditional LCD displays in that each pixel emits its own light, so a backlight is not required. Even better, when rendering a black element on the screen, AMOLED displays simply don't light up the associated pixels, meaning virtually no power is used. Since black pixels use little to no power on an AMOLED screen, more black pixels means lower battery consumption.

In the aftermath of the unindicted police killings of Michael Brown and Eric Garner, we've been told that the system worked as intended. When our legal system's outcome is at conflict with what a majority of Americans believe is just, it's clear that some changes are needed. But what specifically needs to change? And what can an average citizen with a moral and just cause do to prevent these kinds of tragedies from repeating themselves again and again?

When it comes to getting your computer and smartphone to work well together, there's no service more robust and capable than AirDroid. For years, it's been the go-to tool for users looking to transfer files between their devices or access contact lists and call logs from their computer.

Welcome back, my aspiring hackers! Those of you who use Windows in a LAN environment understand that Windows machines can share directories, files, printers, etc. using "shares." This protocol dates back to the 1980s when the then dominant computer firm, IBM, developed a way for computers to communicate over the LAN by just using computer names rather than MAC or IP addresses.

Audiobooks are great because they require little-to-no effort on your behalf. When driving in traffic, why not listen to George R.R. Martin's lengthy A Feast for Crows instead of repetitive, commercial-laden radio? Maybe it harks back to prepubescent bedtime readings, but having things read to me is a very satisfying experience.

Welcome back, my hacker novitiates! A short while ago, I introduced you to regular expressions. Regular expressions are a language that is particularly useful for finding complex text patterns in streams of data.

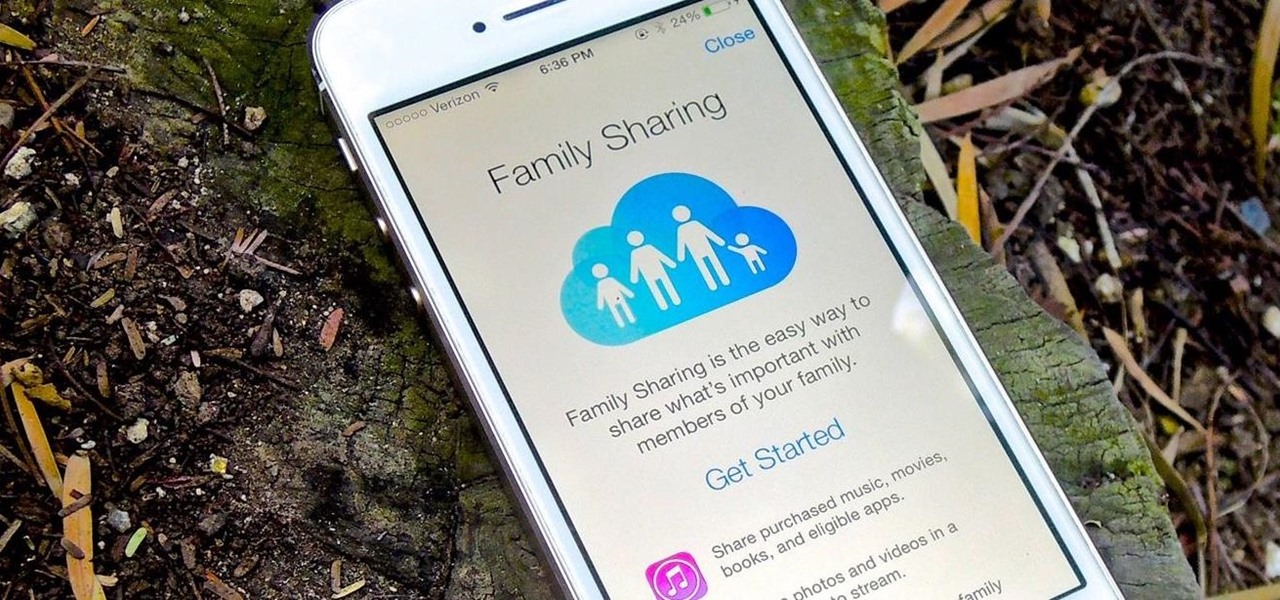
There are a ton of great new features in iOS 8, and one of the most interesting (and perplexing) ones is called "Family Sharing."

The Xposed Framework offers many great customization options for your Galaxy S5. S Health, with its ability to read your heart rate through a built-in monitor, is one of the main selling points of the GS5. Trouble is, the two don't seem to play nice together.

When the Nexus 5 debuted, one of its coolest features was the fact that you could say "OK Google" any time you were on the home screen to launch a Google Voice Search. This feature was ultimately made available for other devices by way of the Google Now Launcher.

If you've ever seen one of those Samsung commercials from about a year back, you know that the Galaxy S series of phones come with a feature that allows you to do certain things by making gestures in front of your screen. They call this feature Air Gesture, and it enables you to perform certain functions without even touching your phone.

Whether it's spotty data coverage, bad customer service, or a high monthly bill, at some point many of us consider changing carriers. The problem is, we often don't want or need to change our devices. Since it's now legal to unlock devices to bring to new carriers, getting devices switched over is doable, but it's pain going into carrier stores and dealing with their constant upselling.

With apps and games getting bigger and more memory-hungry every year, storage space is at a premium. High-definition videos and photos of innumerable pixels certainly don't help the matter, either.

Welcome back, my greenhorn hackers! Sometimes, we don't have a specific target in mind, but rather we are simply looking for vulnerable and easy-to-hack targets anywhere on the planet. Wouldn't be great if we had a search engine like Google that could help us find these targets? Well, we do, and it's called Shodan!

Welcome back, my aspiring hackers! Those of you who've been reading my tutorials for some time now know that I am adamant regarding the necessity of learning and using Linux to hack. There is no substitute, period.

Welcome back, my novice hackers! I have tried to emphasize throughout this "Hack Like a Pro" series that good reconnaissance is critical to effective hacking. As you have seen in many of these hacks, the techniques that we use are VERY specific to the:

Here's a routine that I'm sure all of us smartphone users go through at least several times a day. You notice your Samsung Galaxy S4's notification LED blinking, grab your phone to see what it is, and enter your PIN. Only instead of anything important, you find that it's just some online store enticing you with sales promotions, or some other email that you could have easily done without.

Welcome back, my rookie hackers! The more we know about a system or network, the better our chances of owning it and not leaving a trace for investigators to follow. One of the often overlooked sources for information is the Simple Network Management Protocol (SNMP). Many rookie hackers are not even aware of it, but it can prove to be a treasure trove of information, if you understand how it works and how to hack it.

Whenever the word "popup" pops up, I immediately cringe because all I can think about are those obnoxious ads that ruin my everyday browsing experience. But, not all popups are evil.

Welcome back, my nascent Hackers! In my last blog, we looked at a passive way to gather information necessary for a hack. The advantage of using passive recon is that it's totally undetectable, meaning that the target never knows you're scouting them and you leave no tracks. The disadvantage, of course, is that it's limited to only some websites and not entirely reliable.

Welcome back, my novice hackers! Most of my tutorials up until this point have addressed how to exploit a target assuming that we already know some basic information about their system. These include their IP address, operating system, open ports, services running, and so on.

Not having internet sucks! We do a ton online these days, from working, shopping, studying, and collaborating, to watching fail videos and endlessly clicking through memes.

Google Reader is soon to be no more. Yesterday, the company announced that the service will be shutting down as of July 1, 2013, as part of Google's second "Spring Cleaning."

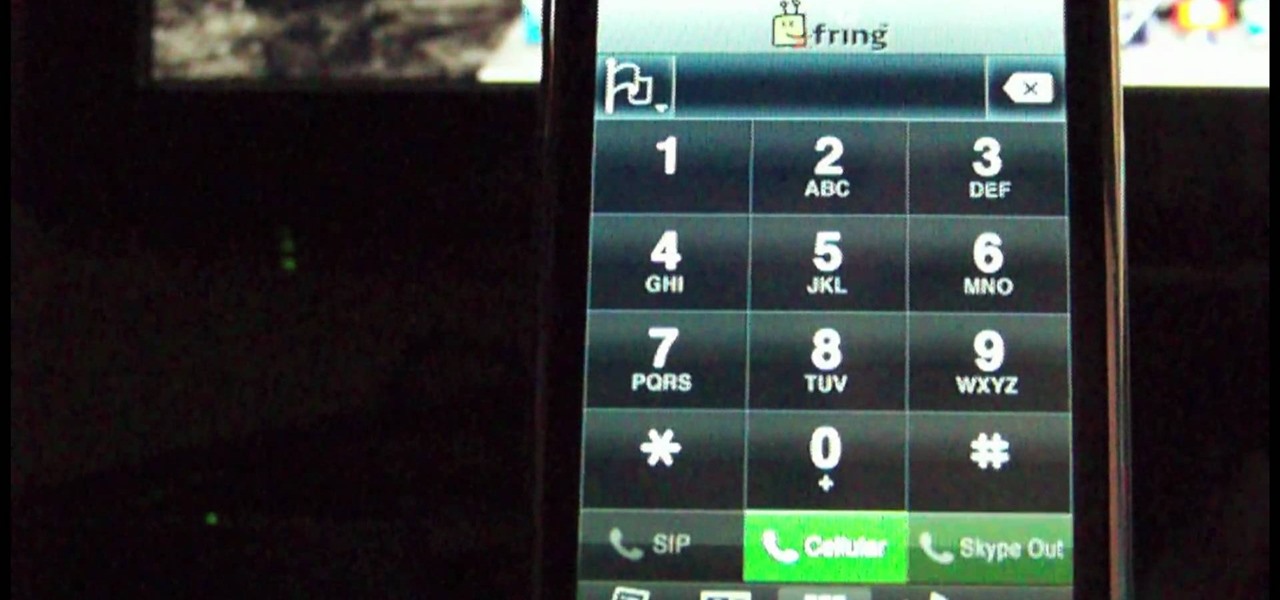
There are two ways to use iPod to make international calls that you should think about, when you are using your iPod Touch. One method is a free method. The other method is an inexpensive one. You will need to down load the "fring" app. If you haven't already done so, you will need to download the SIP service.

In order to unlink your Google account and your YouTube account, you will need to go to Google. Click on My Product. Then, click on Edit. Next, click on "Close the account and delete and all services linked to the account". Check the box that says YouTube. Scroll down to the password box. Enter your YouTube password. Next check both boxes. Then, click Delete Google Account.

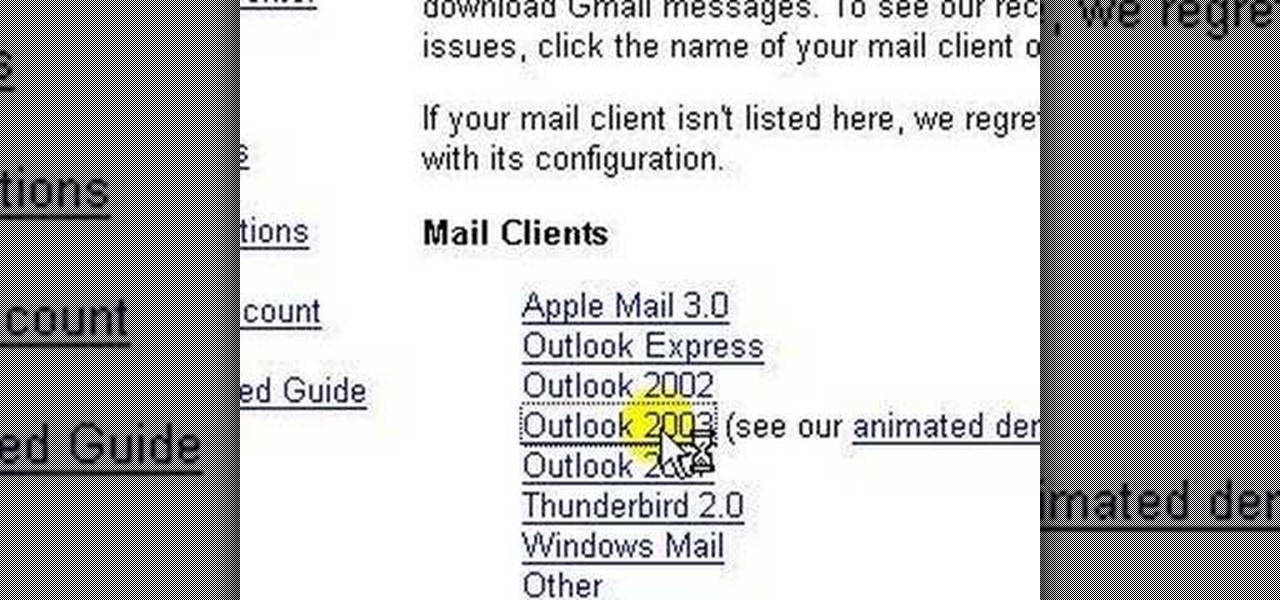
lakercoolman shows us how to set up our gmail account with this quick tutorial. Basically outlook express is a program that helps us to organize our email with added features such as contacts, to do lists and calender entries. Its an offline email client that allows us to work offline and also lets us set up exchange servers aswell. Ohter email servers such as hotmail and yahoo charge for thios service but the advantage of gmail is that IMAP or POP access is free. in ofer to set up, navigate ...

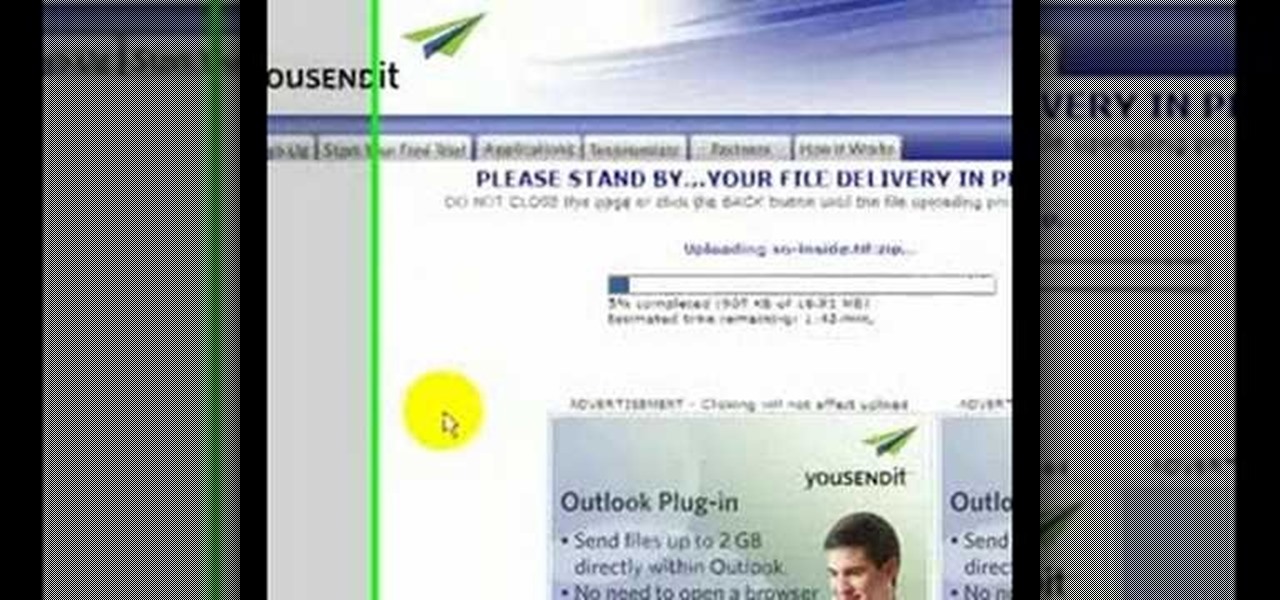
This video shows you how to use the online file delivery service YouSenditIt.com to send a file to someone. There are two ways to do this. One is to register for an account and send a file, and the other is to do it directly from the interface that you'll find on the website. You don't have to register, but generally if your file is going to be larger than 20 MB the person on the receiving end will need to register. But in this video we're shown how to send a file from the interface you're pr...

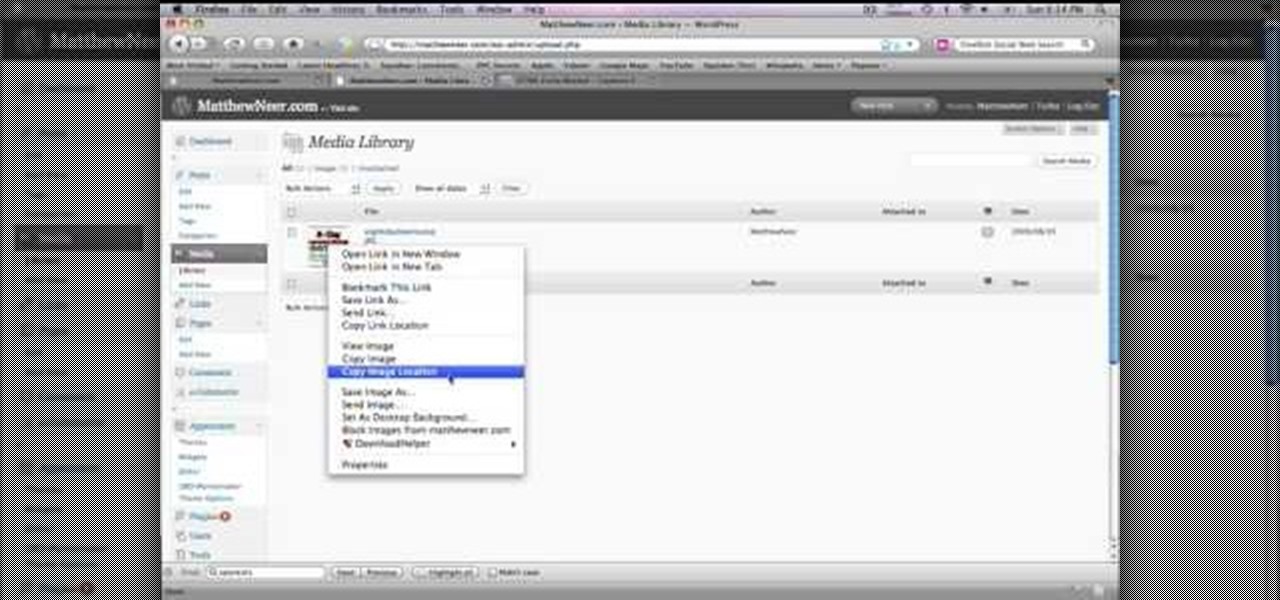
In order to create a custom caption box in WordPress you'll need to go to your dashboard. Here click on appearances, then on editor. Now over on the right select the sidebar option. Here you'll see some code, what you need to do is find the word that you want to replace on the main page, you can use ctrl+F to find the word. When you've found it within the code just replace it with whatever you want and then press the 'apply' button. You'll see that the main page will now be displaying the wor...

Learn how to connect to the internet using your PS3 using an Ethernet cable. What you will need: 1. An internet modem or hub. 2. The details required to connect to the internet (password etc.). 3. A PS3 and an actual internet connection e. g. BT or AOL. Once you have those just follow these steps: 1. Take your Ethernet cable and plug it into the back of the PS3 into the socket labeled Ethernet. 2. Plug the other end into your internet modem. 3. Turn on your ps3 and go to "network settings" un...

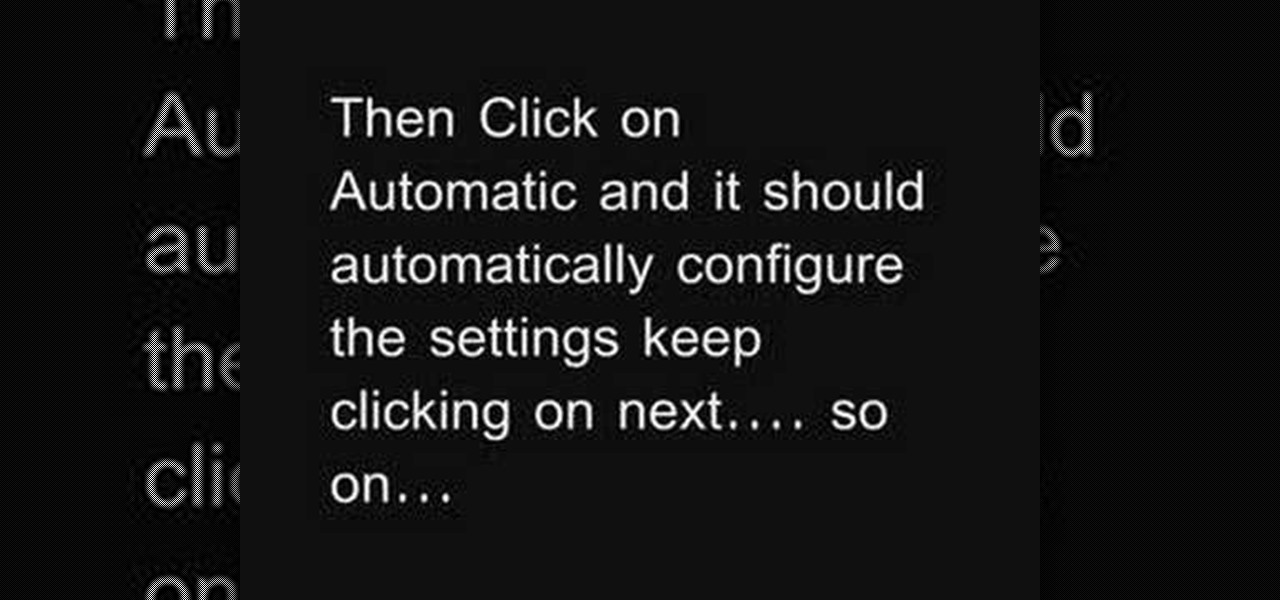
Unlock a jailbroken iPhone 3GS to use it with T-mobile. DISCLAIMER: This only works with an iPhone 3GS, not any other iPhone, and only on firmware 3. 0 or lower. 1. Turn off 3G under "settings" and then "general". 2. Go to Cydia. 3. click "manage" and then "sources". 4. Press "edit" and then click "add". 5. Type in: http: //repo666. ultrasn0w.com. 6. Add source. 7. Wait for it to update the sources. 8. Click "repo666" and then "Ultrasn0w". 9. Click "install" and wait for it to install . 10. H...

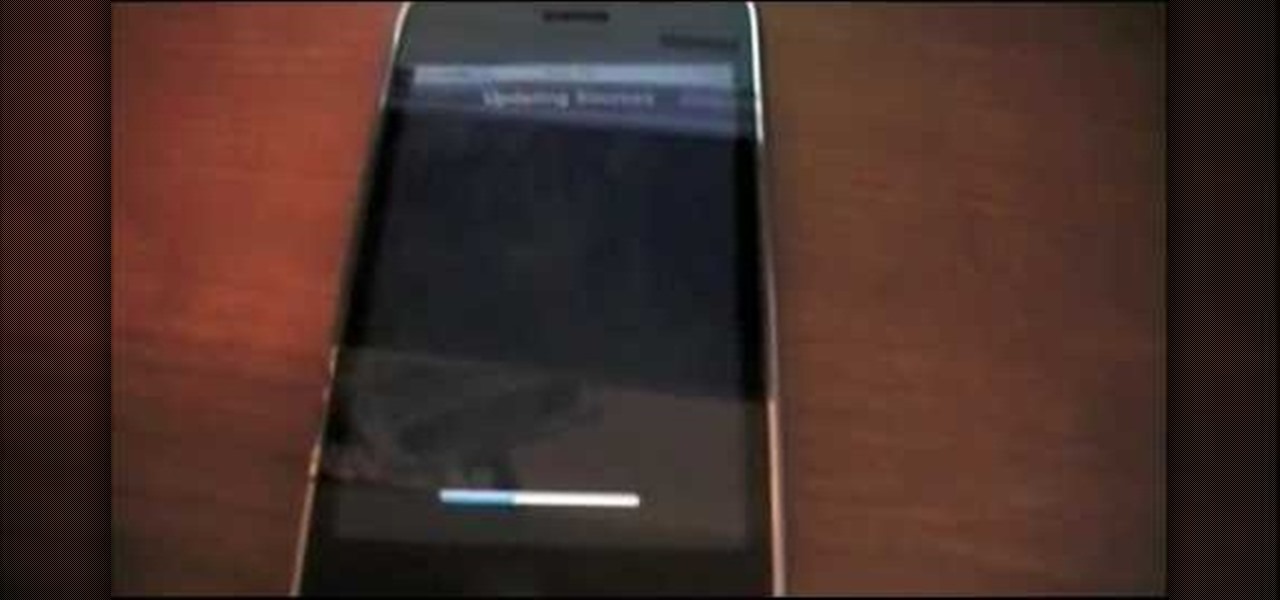
Blackra1n is one of the easiest jailbreak programs made. This jailbreak works for iPod Touch 1G, 2G, and the iPhone 1G and 3G. For an iPhone 3GS or an iPod 3G, this will be a tethered jailbreak, meaning that if you want to reboot your device, you will have to reconnect it to your computer and re-jailbreak. For iPhones, it will also update your base band, meaning that if you were using a service provider that wasn't AT&T, it will reset it to use AT&T again. This jailbreak is very easy. Go to b...

Watch this video to learn how to unlock your Samsung phone. Power up the phone. It shows the boot logo. Take the battery out and insert T-Mobile SIM card. Turn phone on. Shows welcome. Confirm T-Mobile by dialing 611. To unlock phone: Take out the battery and SIM card. Put in an AT&T SIM card. Put the battery back into the phone. Turn on the phone. It says," wrong card". Dial *2767*3855#. The phone will reboot after 15 seconds. Screen says, "Welcome to T-Mobile". To keep service dial *7465625...

If you ever wondered how you could make your internet web browsing faster, then this video will give you a crucial tip. The loading speed of web pages and web sites is greatly influenced by the type of web browser you are using. The narrator in this video suggests that you search for other types of web browsers besides Internet Explorer or AOL. The main web browser that is advocated by narrator in this video is Firefox. He explains how Firefox is able to load pages faster than Internet Explor...

Did you know you can use your iPhone as a portable modem for your other devices? The first thing you need to do is set up Internet tethering on your phone. This is not difficult and requires only a jailbroken iPhone and a computer to do. Some hackers charge over $20 to tether your phone, and with this video, in a few simple steps you can accomplish it for free.

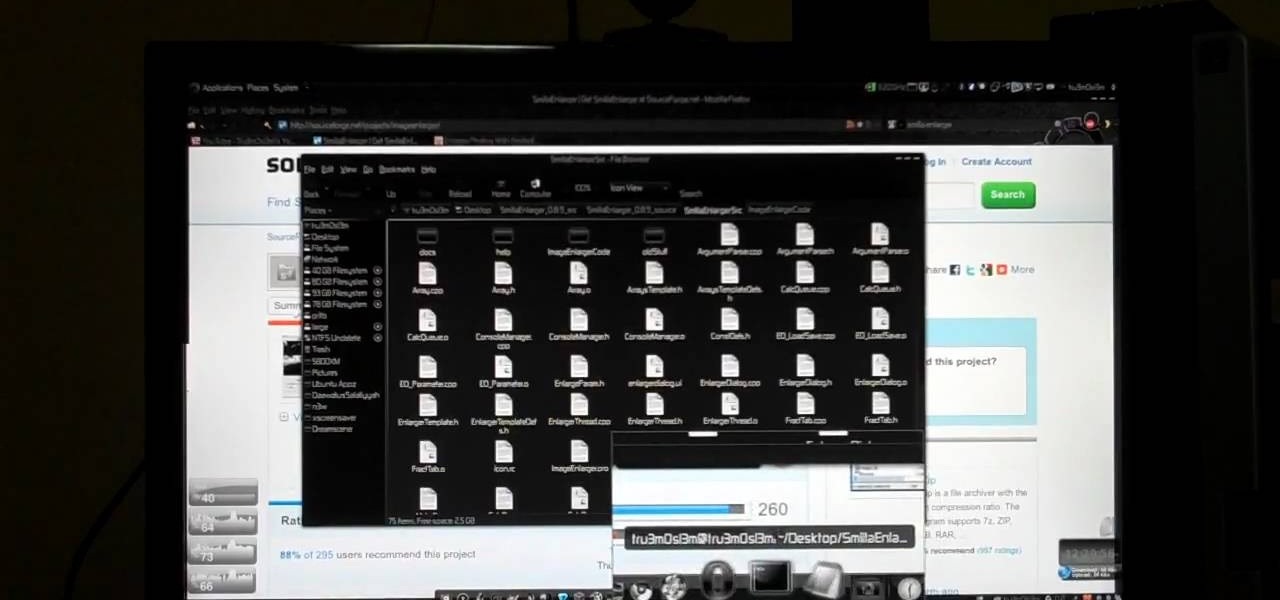
Ever hear of SmillaEnlarger? It's a small graphical tool (based on QT) to resize, especially magnify bitmaps in high quality. Check out this video tutorial on how to back up and restore data easily on Ubuntu Linux.

The CEC, Canada Experience Class, is a new program to help a person who has held residency in Canada gain permanent residency status. The program realizes that, by going to school or living in Canada while working, many people have the skills necessary to make the transition to live in Canada permanently. To qualify for CEC, you must be a temporary worker living in Canada for at least two years with two years of skilled working experience. A second way you can qualify is by being a foreign gr...

The citizenship card is a document that naturalized Canadian citizens use to prove that they are Canadian citizens. This card is needed to get certain documents such as a Canadian passport. It never expires but it can be updated to include a new picture or name change. Citizens born in Canada do not use the card, they use their birth certificate to prove citizenship. Naturalized citizens can apply for this card and so can people with parents of Canadian descent. People who have previously had...

Hosting your first holiday dinner? These tips & tricks will help you pull together a fabulous party without losing your holiday spirit or mind!

Looking to create a savings account? Once you see how much you can save when you spend only on needs rather than wants, you may never go back to frivolous shopping. In this video, ways to stop spending so much money are gone over.