Of the hundreds of uses for our devices, the one that I cherish most is the ability to kill time just about whenever and wherever I need to. Whether it's reading news, checking social media, or watching videos, we have a ton of ways to pass the time in that two-hour DMV line or dentist's waiting room.
We've all been there. Your phone's either dead or barely hanging on with a few minutes of life left, and you only have a small window of time to charge it before you need to head out. Sure, you can charge it for the few minutes you have, but what's the point if your device is going to die again in several minutes?

You know that sinking feeling you get when know you've just done the unthinkable? It's the worst. Sending that ridiculous text message to the wrong number or posting a shameful tweet during a weekend bender.
I used to have nightmares when I watched Terminator 2. I mean, I didn't step on a playground for a least two months after I saw that movie. There was something terrifying about computers having so much intelligence.

Craigslist is probably the greatest site ever created, and I'm just talking about it's classified section, both awesome and amazingly creepy. Seriously, spend 20 minutes scrolling through the personals and you'll never want to take your eyes off the screen. But I digress—Craigslist is also one of the most convenient places to buy and sell pretty much anything you can think of. I've used it to buy my bed, my old bike (which was stolen!), and my couch. And while Craigslist is great in many ways...
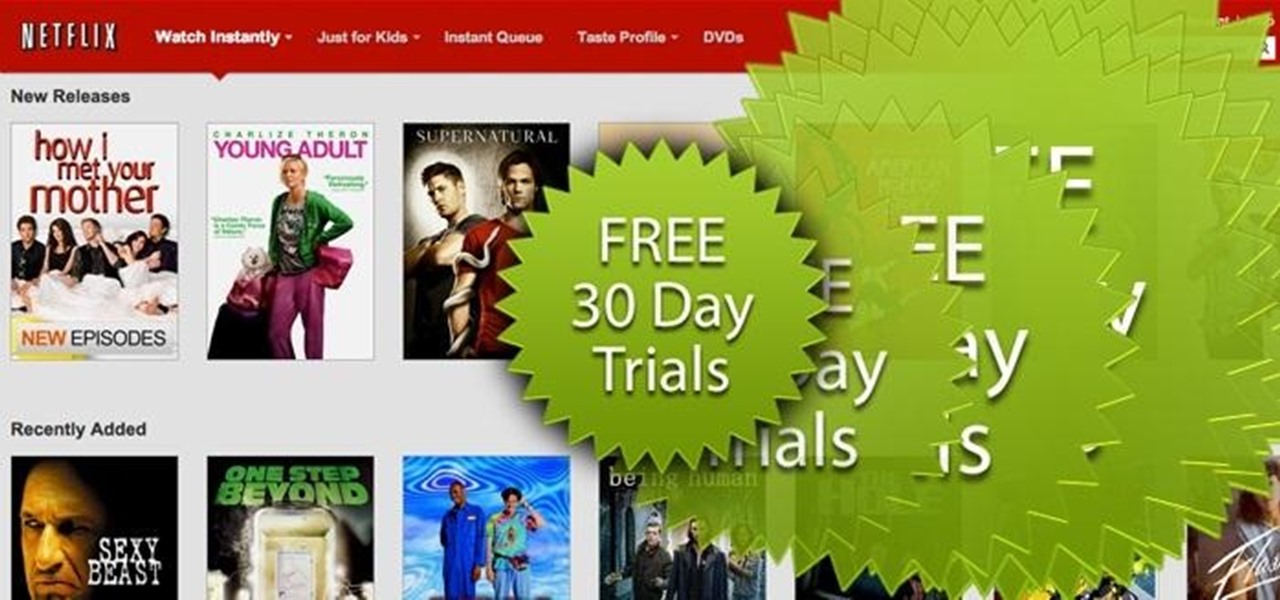
Free trials are a great way to test out products before a purchase, or simply for the exploitation of free stuff for that limited amount of time. Some trials last a few days and some last even a month or two, but no matter what—these trials will always expire. But like most things in life, there is a way to get around such limitations.

Most of us have some sort of malware scanner or antivirus program on our computers, but what about our smartphones? A lot of people don't realize that computers aren't the only devices that are susceptible to malicious software and apps—they can follow you on your smartphone or tablet, too.

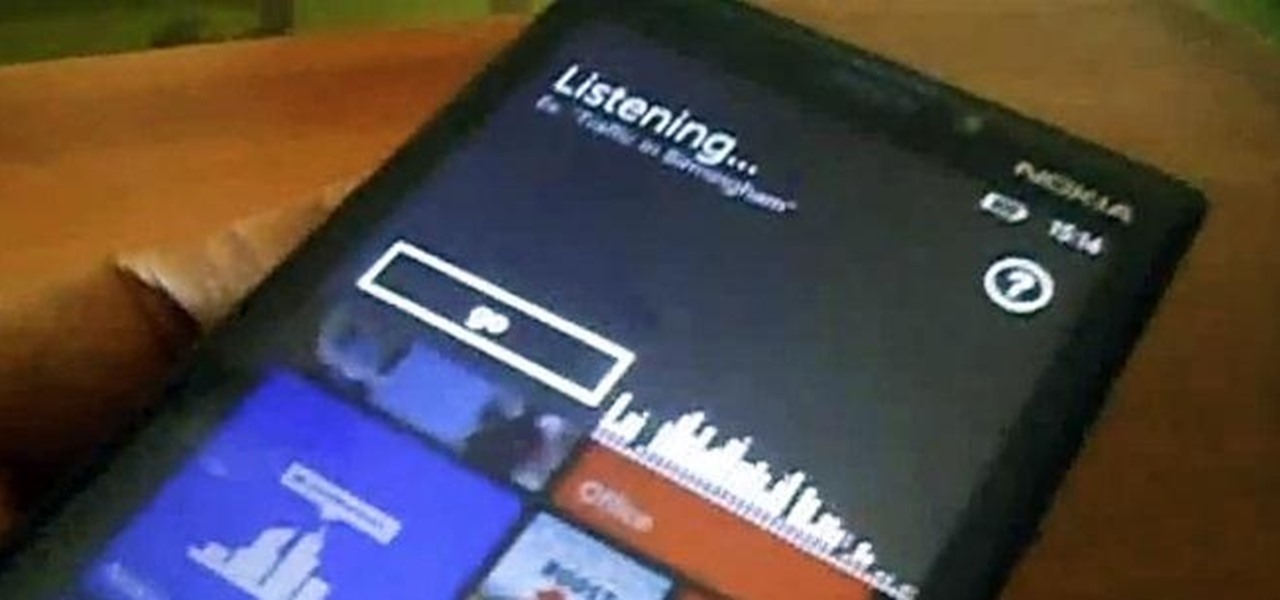
Like most new things, the Start Screen in Windows 8 has its adorers and detractors, but either way you slice it—it's here to stay. I'm still getting used to the Start Screen, so I'm not sure if it's a love or hate feeling yet, but I do know one thing—I want my own background!

There's really nothing safe about transmitting sensitive information electronically, but even if it gets there safely without being seen by prying eyes, there's no guarantee what happens to it once it reaches its destination. And let's face it, there are some things that you just don't want floating out there forever. So what can you do? Whether you want to send an email, a text, or a link, there are ways to send messages that self-destruct so that once they're read, they immediately vanish. ...

All of my hacks up to this point have been operating system hacks. In other words, we have exploited a vulnerability usually in an operating system service (SMB, RPC, etc.) that all allow us to install a command shell or other code in the target system.

In my first few articles, we focused on operating system hacks. These hacks have been primarily on older operating systems such as Windows XP, Windows Vista, and Windows Server 2003.

People are always looking for ways to save money, and for the most part, saving money and cheating the system are synonymous when it comes to things like free internet access. Practically every new gadget is capable of connecting to the web, which means more and more people are looking for ways around those hefty internet bills.

Getting a new phone is like getting a pair of new socks—you can't wait to try them on and when you do, they feel totally awesome. Maybe that's just me, but for many customers that have already received their highly anticipated iPhone 5 in the mail, awesome is definitely not the word they are using.

What's the first thing you would do once you realized you were lost in, say, a desert? If you're like me, you would immediately pull out your cell phone and start dialing every number. But what if you have no service? What if your battery is dead?

Learn tips for using the Celtx free screenwriting software, including project library, production schedule, editors, and online services in this free screenwriting video series.

Recording phone calls has always been tricky due to legal, ethical, and technical considerations. With iOS 18.1, Apple brings your iPhone a native call recording feature that simplifies this process while addressing privacy concerns.

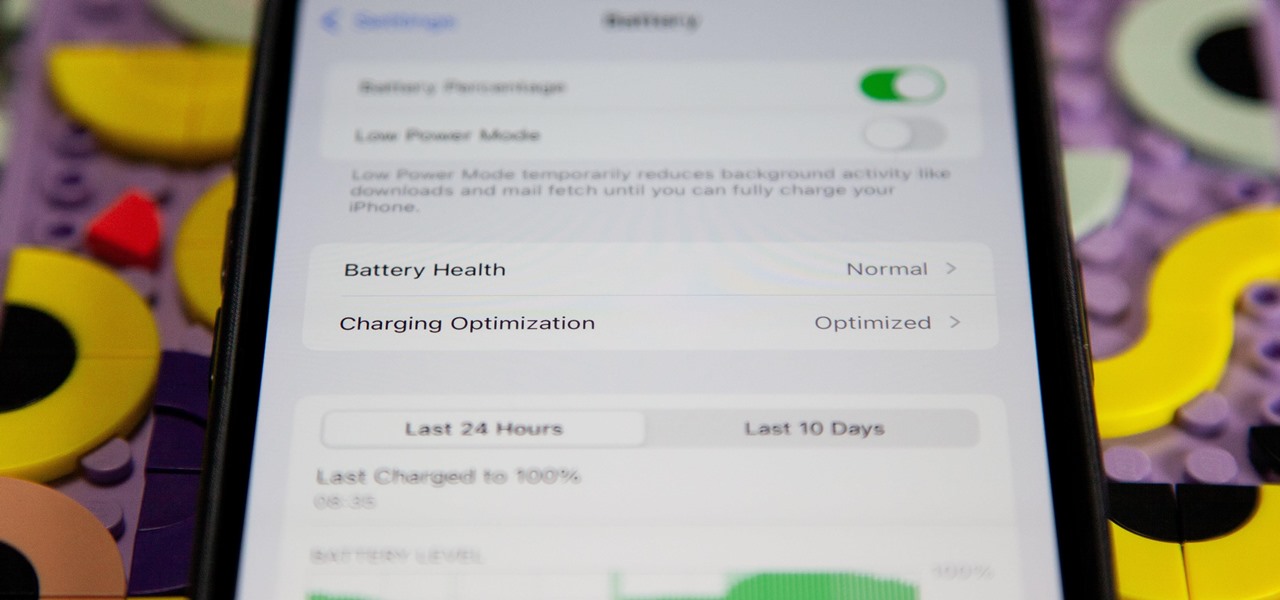
If you're ever curious about your iPhone's battery health, there are easy-to-access stats that let you know the last charge amount, which apps are eating away at most of your power, and even your battery's remaining capacity. Now, a new update makes it easier to know how well your battery is doing.

You see the status bar nearly everywhere on your iPhone, and it almost always looks the same. But you can use a few tricks to spice things up a bit — without jailbreaking your iPhone.

YouTube Music just refreshed the user interface for playlists, seemingly taking away the ability to shuffle the songs in your playlists. While the update has been rolling out for months, you might just be getting the updated look on your smartphone, and there's no giant "Shuffle" button like there was before. But that doesn't mean there's no more shuffling.

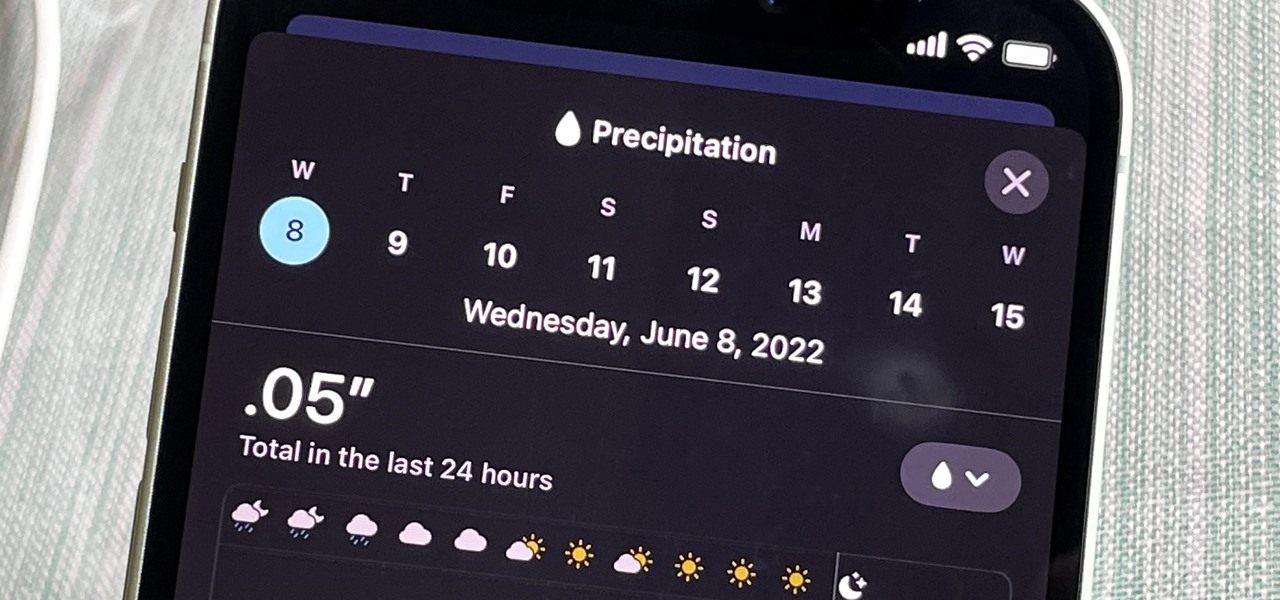
Your iPhone's Weather app received its biggest update yet. Apple finally incorporated its Dark Sky purchase into Apple Weather, so you'll see more information for each location's forecast. Plus, there are a few surprises to be excited about, such as the ability to add more trackable cities.

There has been drag-and-drop functionality for iPhone since at least iOS 11, but iOS 15 adds a new ability that makes essential emails even easier to find when you need them.

It's already been a banner year for mergers and acquisitions in the augmented reality industry, with WaveOptics and Ubiquity6 among the notable companies acquired. Two of the more active M&A players, Snap and Epic Games, continued their respective buying sprees this week with major deals supporting their AR strategies.

Google and Snap held their annual conferences this week, and both companies managed to upstage their new AR software features with fantastic new AR hardware.

The march of Amazon to insert itself into nearly every retail arena continues with the e-commerce giant's latest move to launch its own brick-and-mortar beauty salons.

This week, Google showed off some wild new and innovative AR experiences that showcase the WebXR protocol for browser-based AR content, while 8th Wall applied its own web-based AR platform in service of Captain Morgan.

Apple seeded software testers iOS 14.5 public beta 6 today, Wednesday, March 31. The update includes a new battery calibration for iPhone 11, 11 Pro, and 11 Pro Max, as well as two new Siri voices.

Apple just seeded developers the sixth iOS 14.5 beta today, Wednesday, Mar. 31. The update includes a calibration for battery health measurements for the iPhone 11 line, as well as two new Siri voices.

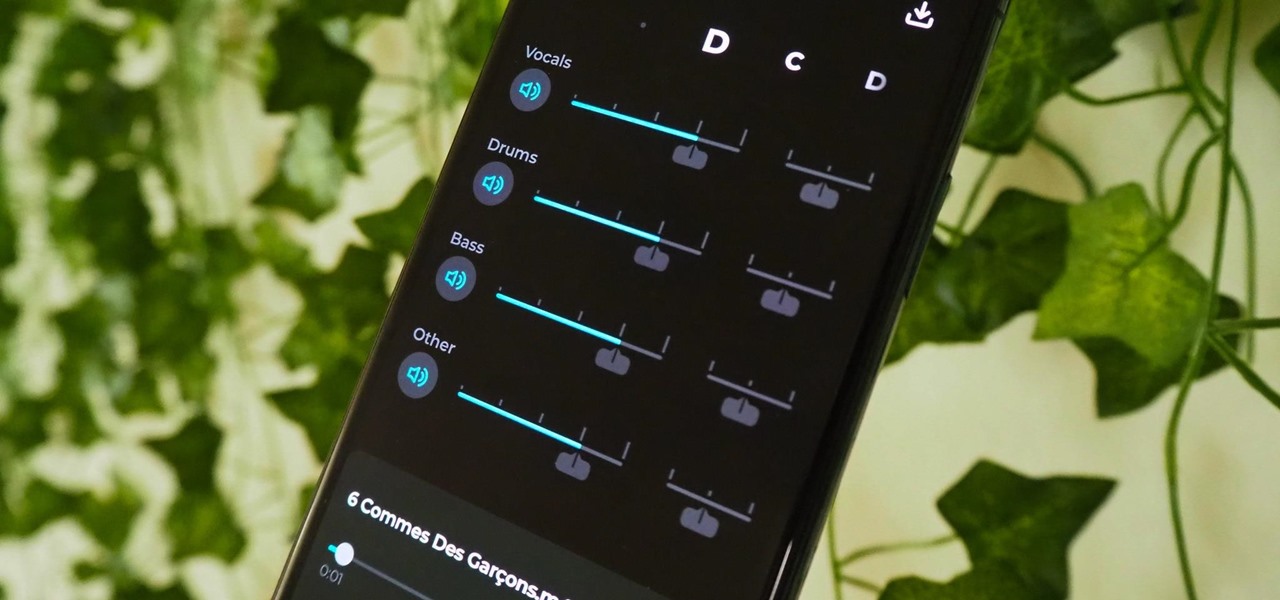
Adobe Audition, Audacity, and other audio editing software have tools to isolate vocals and instruments in regular songs so that you can get an instrumental track for karaoke, vocals for an a capella version, or solo drums, bass, keys, etc. that you can use to learn the song yourself. The software is mostly for desktop computers, and it doesn't always do a good job, but that's where Moises comes in.

If it has an internet connection, it's got a huge attack surface for hackers. But what makes your phone even more dangerous is its portability and the collection of sensors it houses that can be just as good at tracking you as the camera and mic.

As protests surge in the wake of George Floyd's murder by a Minneapolis police officer, powerful photographs and videos from the demonstrations have gripped the world, putting our nation's very real and very justifiable widespread civil unrest out into the digital world. Unfortunately, these pictures could put you or others in danger if precautions aren't taken before uploading them online.

Thanks to numerous smartwatch deals this holiday season, many people are receiving their first one. But what exactly can they do? In regards to fitness, quite a lot. With a growing list of sensors and software updates, these small devices can be the very thing you need to ultimately reach your fitness goals.

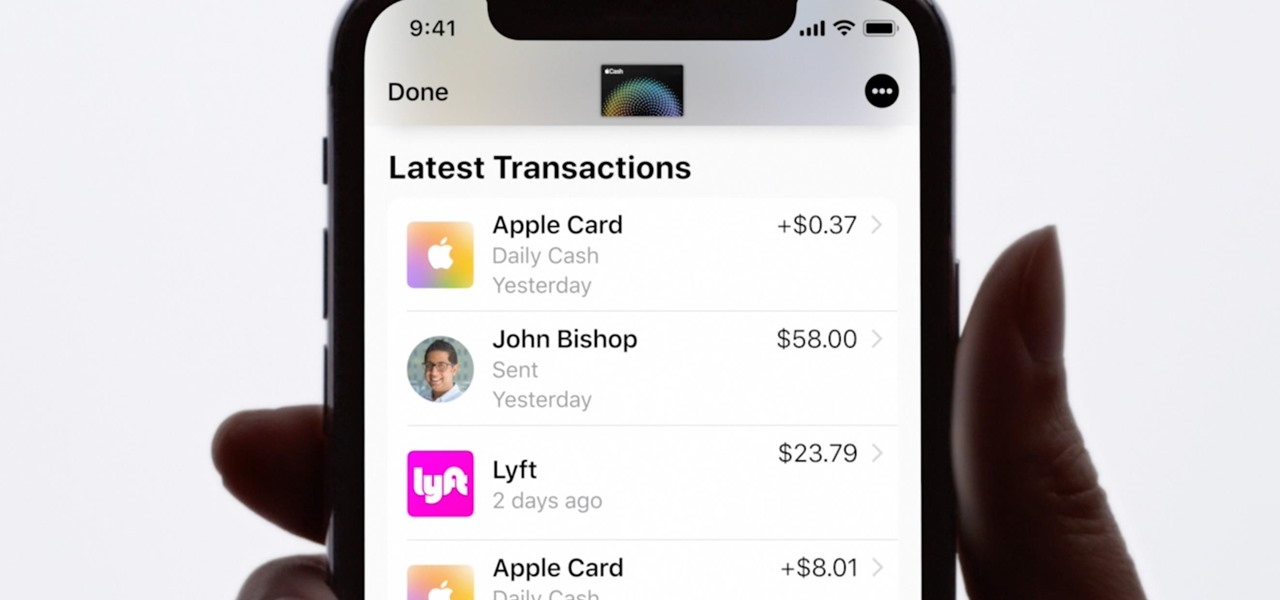
Apple Card is the iPhone OEM's big leap into the credit card market. Its low barrier to entry and ease of use make it an appealing option, especially for those who often pay for goods with Apple Pay. To get the best rewards possible, make sure you use the Apple Card at stores where you can get 3% cash back.

If you've ever needed to prove you have remote access to a device, or simply want a way to convince someone their computer is haunted, SSH can be used to make a device begin to show signs of being possessed.

Comparing the present-day states of the consumer and enterprise sectors of augmented reality is like evaluating the merits of sports car versus work trucks. Like consumer AR, sports cars are sexy and exciting, but perhaps a bit impractical at times. On the other hand, enterprise AR is utilitarian, but it gets the job done and, in the long run, pays for itself.

Traveling abroad can be a hassle. Between the flight, hotels, food, and the languages barriers, it can be a lot to manage. There's one tool you have that can help with all of this — your smartphone. Fortunately, nowadays, you don't have to change your carrier to continue using your phone.

Since iCloud's introduction in 2011, you get only 5 GB of complimentary cloud storage with your Apple account. With iPhone backups, app data, iCloud Drive files, and even emails (if you have a Mac, Me, or iCloud email address), you'll quickly run out of space to back up photos and videos. Fortunately, Google offers 15 GB of free storage, making it easy to upload your Camera Roll for safekeeping.

The gym can be pretty distracting. With the slamming of weights and pieces of equipment, loud music blasting through the speakers, and plain old grunting, it can be challenging to focus on your workout. However, with your just your phone, you can not only eliminate these distractions but make the most of your time there.

The Pixel 3 runs stock Android, so you might think that since you've used an Android device before, you should know your way around the new phone by default. But Google has actually added several great Pixel-exclusive software features to its flagships, and not all of them are easily discoverable.

The most common Wi-Fi jamming attacks leverage deauthentication and disassociation packets to attack networks. This allows a low-cost ESP8266-based device programmed in Arduino to detect and classify Wi-Fi denial-of-service attacks by lighting a different color LED for each type of packet. The pattern of these colors can also allow us to fingerprint the tool being used to attack the network.

It only takes a few commands to manipulate a MacBook's secure HTTPS traffic and pluck login passwords out of the encrypted data. Let's take Facebook and Gmail hacking to the next level by intercepting Safari and Google Chrome web traffic in real time.