Facebook essentially strong-armed us all into installing their standalone Messenger app for mobile devices, but the recent initiative that allows third-party development on the platform definitely makes it worth your time.

Welcome back, my greenhorn hackers, and happy New Year! Now that your heads have recovered from your New Year's Eve regaling, I'd like to grab your attention for just a moment to preview 2015 here at Null Byte. I hope you will add your comments as to what you would like to see, and I'll try to honor as many requests as I can.

We always want to find more ways to help brilliantly lazy cooks make great-tasting food and save money and time in the process. Luckily, our Facebook fans are invaluable sources of information when it comes to getting cool tips, behind-the-scenes info, and more.

Welcome back, my fledgling hackers! Sometimes, for a variety of reasons, we can only get a command shell on our target system. For instance, with Metasploit, it's not always possible to get the all powerful Meterpreter on our target system. In other cases, we may be able to connect to a command shell via Netcat or Cryptcat.

Before Apple jumped into the phablet game with their iPhone 6 Plus, there was the Samsung Galaxy Note series. Initially knocked for their size, the Notes slowly but surely gained popularity, thanks to powerful hardware, incredible displays, extensive features, great battery life, and a surprisingly-useful stylus.

If you struggle with deciding which wine you should buy for an intimate dinner, or the type of beer with the highest alcohol content that doesn't taste like tree bark, then check out some of these great alcohol-friendly apps to make better booze decisions.

Tuesday has long been considered the best day to save money on a plane ticket. Airlines typically announce new deals on Monday, so by Tuesday, all other airlines have matched their competitor's lowest fares. It's a tip that I learned at a young age from my father and was solidified by countless others who swore by it. Well, it turns out that we were all wrong.

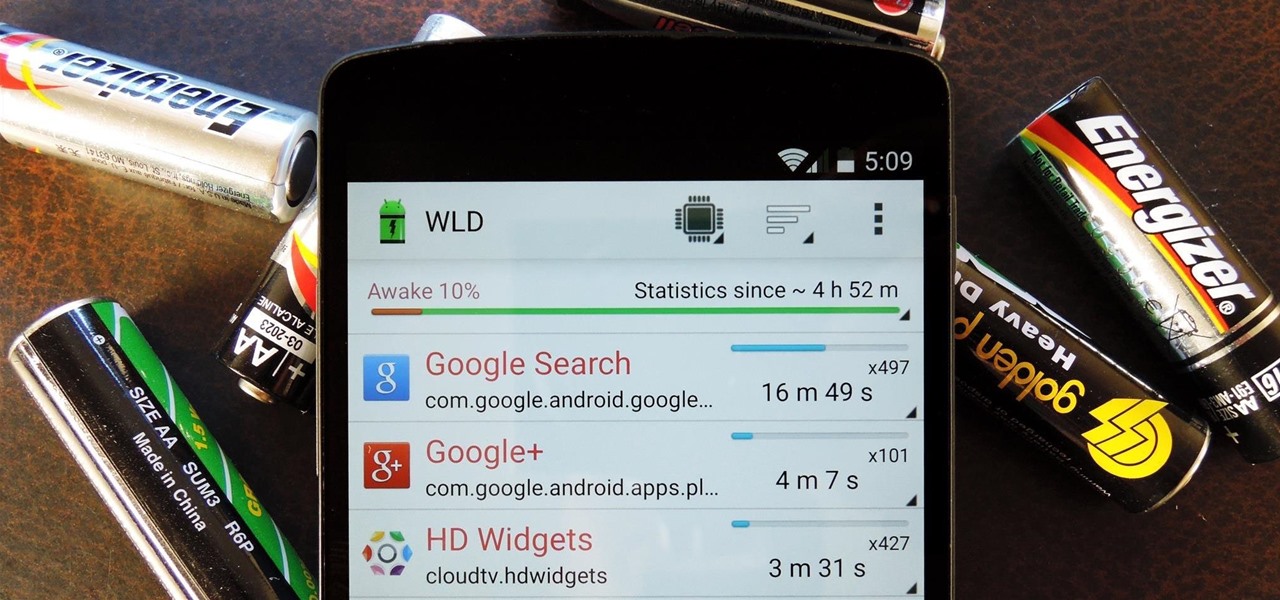
When you're actively using your phone, a certain amount of battery drain is to be expected. But, if your device is just sitting in your pocket draining its battery, that's when you need to take action.

Welcome back, my greenhorn hackers! In previous Wi-Fi hacking tutorials, I have shown you ways to create an Evil Twin, to DoS a wireless AP, and to crack WEP and WPA2 passwords, but in this tutorial, I will show you something a little bit different.

Mirror, mirror on the wall, who is the fairest of them all? Besides being one of the most notorious misquotes of all time (the line is "Magic Mirror on the wall, who is the fairest of them all"), it's a question that men and women probably have asked themselves more than once.

Apple is set to unveil the iPhone 6 on September 9th, and shortly thereafter carriers like AT&T and Verizon Wireless will begin selling them online and in stores. So, if it's time in your contract for a device upgrade, it's time to start thinking about trading your current iPhone in for up to $400 in value.

Better sleep, smartphone news, and changes to your favorite forms of entertainment. There's been a lot going on over the last couple of weeks in the world of tech, and we thought we'd show you all of the need-to-know products, updates, and ideas that we think are most important.

Loaded with a gorgeous display and a powerful processor, the Kindle Fire HDX is an impressive all-around tablet, especially when it's used for what Amazon Kindles were built for—reading electronic versions of novels, textbooks, and other printed works.

Welcome back, my aspiring hackers! Many of you have installed Kali Linux as a virtual machine (VM) using VMware or VirtualBox, while others have installed Kali (or BackTrack) in a dual-boot system. The drawback to installing these hacking systems as a VM is that it then requires an external wireless adapter (your wireless adapter is piped through the VM as a wired device, eth0), but it makes for a great place to test your hacks while honing your skills.

With just a swipe and tap of a finger, we can access enormous libraries of information on our smartphones like never before. Whether we want more info about gluten sensitivity or just want to brush up on 18th century philosophers, there's an article somewhere in the vast ocean of the internet that can lend us a hand.

Android uses a set of permissions that apps can request to perform certain actions, and you're notified of these permissions each time you install an app. The problem here is the fact that you aren't given any built-in way to deny apps these permissions (although Danny just showed a workaround for this).

It's the biggest day of the year for all things Google. Their developer conference, dubbed Google I/O, gives us a peak at what the guys at Mountain View have been working on over the course of the past year, and this year, Android was center stage.

When OS X Yosemite was first announced, there were a number of features that struck my attention, but one in particular that stood out above them all was the ability to make and receive texts and phone calls from your Mac, which Apple calls Continuity.

With its growing popularity, it's clear that the Chromecast isn't going away anytime soon, with options for casting games, cloud files, music, and much more. But not all content providers are in a hurry to add support for the device, and SoundCloud is one of them. While My Cloud Player is by no means an official SoundCloud app, it comes pretty darn close.

One feature of Samsung devices that's less useful than I had expected is S Voice, the voice assistant that ships with all new Galaxy devices. The voice is annoying, the features are lacking, and it's an all around subpar product. With Google Now, Siri, and now Microsoft's Cortana, Samsung needs to really step up their game—even on the new Galaxy S5.

Pretty soon, every restaurant and store you walk into will know exactly what you're doing. Retail analytics companies like Euclid, ShopperTrak, RetailNext, and Prism Skylabs have penetrated hundreds of food shops and retail stores across the country, installing sensors that track and log customers' moves while they dine and shop.

Welcome back, my novice hackers! We've done a number of tutorials using one of my favorite hacking tools, Metasploit. In each of them, we've used the msfconsole, which can be reached through either the menu system or through simply typing "msfconsole" from the terminal.

The @DesignGears guys have been busy today, leaking an unofficial KitKat build (Android version 4.4.2) for the AT&T Samsung Galaxy Note 3. The latest is a peek into what the international variants are beginning to see, although this build is far from official. Still, if you want to give it a shot, I'll show you how to install it, but make sure to check out the details below the how-to to see what you can expect, good or bad.

Welcome back, my aspiring hackers! One of those areas of Linux that Windows users invariably struggle with is the concept of "mounting" devices and drives. In the Windows world, drives and devices are automatically "mounted" without any user effort or knowledge. Well, maybe a bit of knowledge. Most Windows users know to unmount their flash drive before removing it, but they usually think of it as "ejecting" it.

Welcome back, my hacker apprentices! I recently began a new series on digital forensics to show aspiring hackers what the forensic investigator can do and see while investigating a cyber attack. This is the second installment in that series and will focus upon network forensics. In other words, what can a network forensic investigator learn about the attacker during an investigation and how.

Smartphone users these days can get bombarded with texts and emails every hour. Online retailers sending you coupons to get you to buy stuff. Girlfriends asking where you are. Service providers reminding you to pay your bills on time.

Automation applications bring the future a little closer. If you've seen Minority Report or other futuristic sci-fi movies, the intrigue of having your electronics work independently is something we can all appreciate.

Ever since the FBI took down the Silk Road and Dread Pirate Roberts last month, many questions have been raised about whether Tor still provides anonymity or not, and if it's now broken. I'll try to address that question here today succinctly from multiple angles, keeping it as simple and plain-language as possible. The Closing of Silk Road

Welcome back, my budding hackers! One of the most time-consuming, but necessary, activities in hacking is reconnaissance. Before we can hack a system, we need to know what operating system it's running, what ports are open, what services are running, and hopefully, what applications are installed and running.

While Siri has never been my favorite, after using her in the new iOS 7, I have definitely become a fan. If you want to know why, check out the newest cool features that Siri has to offer!

If you're a Twitter user, it's a safe bet to assume that you've used a hashtag. On all social networking sites that have the capability, such as Instagram, Facebook, and Google+, the pound (#) symbol is used to mark and designate specific keywords or topics in order to make it effortless for users to connect with one another.

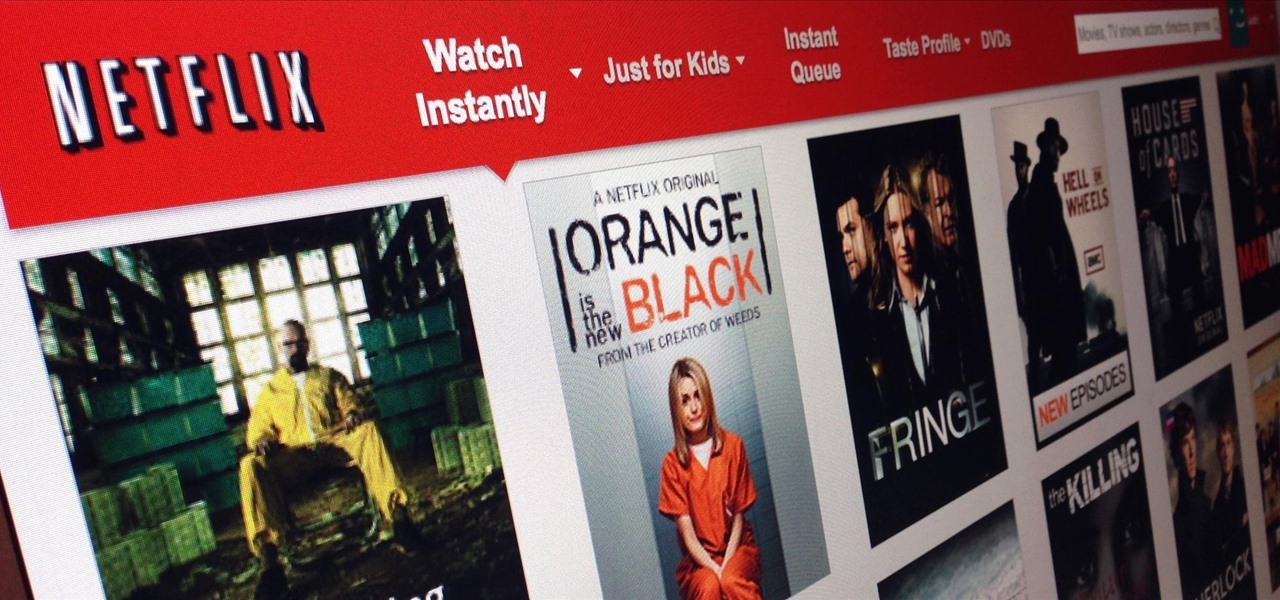
Considering that the average movie ticket these days is $8.38, it's not much of a surprise that Netflix is kicking ass. The same amount will get you a full month of unlimited streaming, and you don't even have to leave your couch. While no one's arguing that it isn't a great deal, the biggest issue most users have with the service is the limited amount of available content. Anything?

Welcome back, my nascent hackers! Earlier, I wrote a guide on finding operating system and application vulnerabilities in Microsoft's own security bulletins/vulnerability database. In this tutorial, I will demonstrate another invaluable resource for finding vulnerabilities and exploits by using the SecurityFocus database.

Welcome back, my hacker apprentices! In recent weeks, the revelation that the NSA has been spying on all of us has many people up in arms. I guess I take it all in stride as I just assume that the NSA is spying on all of us—all of the time. Don't get me wrong, I don't condone it, but I know the NSA.

While the PlayStation 3 is an awesome gaming console and the iPhone is an awesome smartphone, Apple and Sony have made two devices (that could be perfect for each other) nearly incompatible. Truth be told, this is more Apple's fault than Sony's, but we'll get into that later.

Welcome back, my rookie hackers! Several of you have written me asking about where they can find the latest hacks, exploits, and vulnerabilities. In response, I offer you this first in a series of tutorials on finding hacks, exploits, and vulnerabilities. First up: Microsoft Security Bulletins.

Welcome back, my fledgling hackers! In one of my recent articles, I showed you how to install BackTrack as a dual boot system on a Windows computer. In this tutorial, I will walk you through BackTrack, giving you a tour of the most salient features for the hacker-to-be.

An average of 140,000 hard drives crash in the United States each week, according to online backup service Mozy. Additionally, 70 percent of Americans have lost a laptop, smartphone, or tablet, and the average person now loses 1.24 devices each year—less than half of which are ever recovered.

There are two options when it comes to a dent in your car — live with it, cringing each time it enters your view, or get rid of it. While the latter is obviously the best option, most of us will probably just live with dents and dings since spare money is better spent on the actual functionality of the vehicle. However, there is a way to knock out automobile dents yourself with relatively little cash in the bank.