
How To: Make a Blaze Trap in Minecraft
Welcome to Minecraft World! Check out our advanced tutorials and come play with us on our free server.


Welcome to Minecraft World! Check out our advanced tutorials and come play with us on our free server.

I have had a lot of people ask me, "How does my neighbor keep getting into my wireless?!". Chances are, these people are all using WEP, a deprecated wireless encryption protocol. Either that, or you are using one weak WPA passphrase.

So, you scratched up your $500 Adobe CD and now it's unreadable. You could go buy a new one, but you already purchased it! Searching The Pirate Bay and downloading some Adobe software can usually be easy enough, but what should you watch out for?

Cryptography is a quintessential part of computer security in the modern world. Whenever you buy something on eBay or log into Facebook, that data is encrypted before it's sent to the server in order to prevent third parties from eavesdropping and stealing your sensitive information.

Throughout this integral guide, I'm going to aid you along the path to bigger and better builds. Often times, people just jump in and build, but we mustn't hurry things if we want our builds to be all the more satisfying when they are finished. Building the actual builings should be the easy (and the most simple step in any great build), but we have to start with what's underneath your pixelated feet.

How did it happen? How did your ultra-secure WPA password on your wireless network get broken into? Well, you might have just found yourself at the mercy of a cracker.

With the purchase of my latest computer, installing Linux turned into a nightmare from Hell. The graphics drivers are probably the biggest issue that anyone with a newer computer will run into when installing Linux. AMD and NVIDIA are the dominant ones on the market, both of which have awful support.

THE ODYSSEY is an epic adventure, a world first, a race against time, an entire year of living dangerously.

Flash memory can be a tad unpredictable at times. I have had 4 flash drives die out on me over the last few years, and they usually die without warning. When a flash memory based device dies, the data is likely impossible to recover. Adversely on an HDD, or Hard Drive Disk, even if the disk dies out, someone will probably be able to fix it and get it back to working order—at least long enough for you to back up your data. Hard drives are a bit more forgiving. As you can guess, due to the unpr...

More password cracking action from Null Byte! Today we aren't going to be cracking passwords per se, rather, we are going to learn the basics of generating rainbow tables and how to use them. First, let's go over how passwords are stored and recovered.

Big name individual hackers and hacker groups everywhere in the news are getting caught and thrown in jail. Everytime I see something like this happen, I won't lie, I get a little sad. Then I wonder, how are these guys getting caught? If a group like LulzSec, with all the fame and "1337-ness" can get caught, I think my hacker comrades are doing something wrong.

Gamers who have their Xbox 360's firmware flashed may have recently noticed an inability to play backups, or even make backups of newer games that have come out, such as Gears of War 3 and Dead Island, to name a few.

Halloween is just a few days away, and since I've been churning out the creepy Bingo of the Days for everyone the past few weeks, it seems fitting to do a puzzle based on them.

Gamers who have their Xbox 360's firmware flashed may have recently noticed an inability to play backups, or even make backups of newer games that have come out: Gears of War 3 and Dead Island, to name a few.

Anyone who likes shooters is going to hate me for saying this: the best game of the 2000's for me was Psychonauts by Double Fine Studios. It came out in 2005 for the original Xbox, achieving critical acclaim, but never selling very well due to its sheer kookiness and poor marketing. Over the ensuing years it has become a cult classic, with downloadable re-releases on Xbox 360 (sadly no longer available). PC has allowed gamers who missed out on the original to bask in its ageless glory.

Games like Minecraft and Braid have proven that there is money to be made in the indie game marketplace, which means more and more designers are following suit, one being Zeboyd Games. The two-man indie design team released two excellent JRPG spoofs on the Xbox Live Indie Games (XBLIG) Marketplace in 2010: Breath of Death VII ($1) and Cthulhu Saves the World ($3). Both have been well-reviewed and spent time near the top of the XBLIG sales charts, but its success couldn't be rivaled by what wa...

See how to bake without butter, sugar, eggs, dairy milk and more. If you think it’s impossible to bake without butter without losing flavor and texture, then keep on reading. Even if you already substitute butter in your cakes and cookies, there may be some things in this article that you haven’t tried yet.

In the mid '90s, there was no such thing as a widely available indie video game. Brick-and-mortar stores were the only places for consumers to buy games, and magazines were the only outlets to hear about them. For video game creators, the need for a publisher to market and distribute was logistically essential to attract players.

It's currently 2011, but when you fire up your game console, put your hands on the controller and play the new Dead Space 2 video game, you're warped into the future— into the year 2511— just 3 years after the events that took place in the first Dead Space. And it's sure to be a beautiful, frightening, futuristic experience.

If you have any little ones in your life (or you're simply a grown-up kid yourself), Just Bento has has posted Maki's Top 10 Bento Rules for Back-to-School. Rules listed below, click through for full explanations.

"Simplicity is the ultimate sophistication." -Leonardo da VinciLearning a kata requires that you go through several stages. First you have to learn the basic pattern and the techniques. Then you have to perfect what you've learned. Then you have to deconstruct what you've learned and perfected in order to truly understand what the kata is teaching you vis a vis close quarter engagement.

This one smells like a fish story. It is not. Tuesday April 13, Dave and I got up to surf westward at 7 in the morning. First rate waves. Headache cold water....sun blocked by the cliffs. Fast, clean, beach break. 3-4 foot sets, mostly lefts. About 15 dolphins swam by. Blase blase. We always see dolphins. But then some bigass whale with barnacles breaches. We are speechless. It is about 20 feet from us. We follow it for about thirty seconds and pinch ourselves. Have-you-ever? No...

As 2009 comes to a close, the Telegraph presents a compilation of this past year's wackiest inventions. As always, here at WonderHowTo, we are inspired and impressed by ingenuity. The contraptions below range from utter silliness (engagement ring bra) to downright amazing (see-through concrete). Check it out.

For all of you PS3 owners who got addicted to the wonderful puzzle platformer LittleBigPlanet, your hopes and dreams have finally been realized— LittleBigPlanet 2 is now out! Originally set to be released in November of last year, Media Molecule's LBP2 was in stores last Tuesday, January 18th.

Have you ever wondered how to successfully create a panorama with your camera? What is a Panorama?

During pregnancy, women will end up carrying a good amount of extra weight. While a third of the weight gained will come from the baby, the other two thirds come from the changes that happen in your body while you're pregnant.
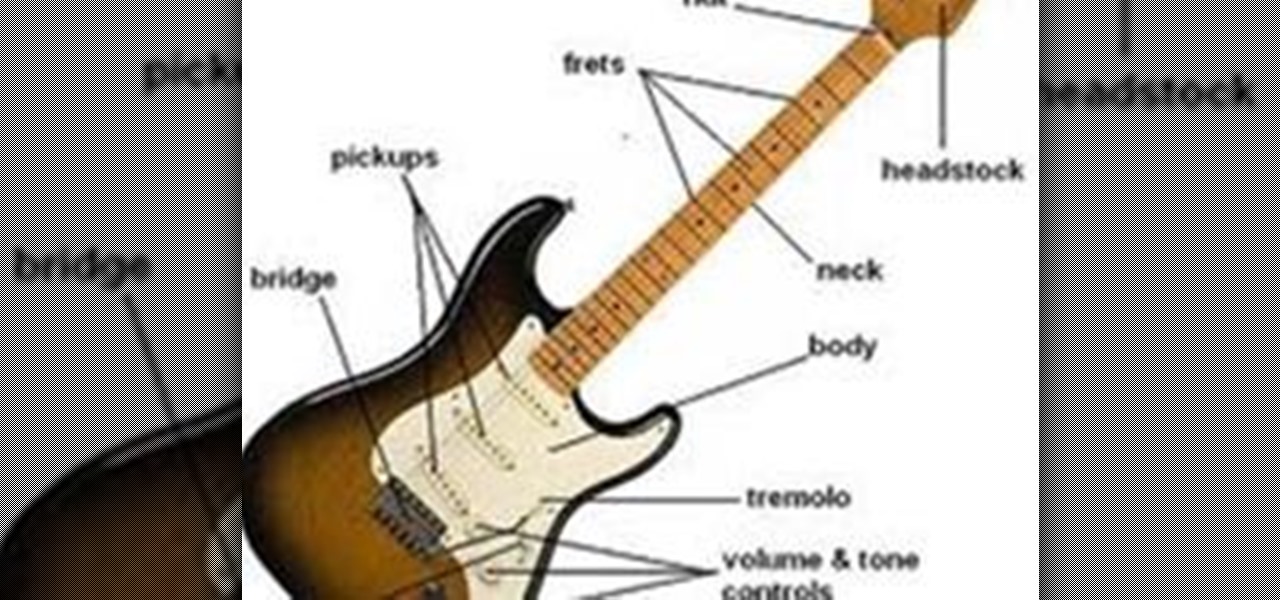
How to be a better guitarist

In a recent arbitrage tip, we showed you the secret to making money fast by buying and selling the same thing over and over again on eBay. But there's one thing you need to know about the buying part—get the lowest price possible! This article aims to show you some of the best methods to making sure you're paying the lowest prices on eBay, so you're the best arbitrageur out there, with your profits higher than ever!

There's three types of animal lovers in the world. The first are your basic pet owners. The ones with a

My girlfriend was going away for a few weeks, but where she was going, there was no easily accessible Internet. She works mostly on the web, so it was imperative that she have a decent Internet connection during her travels. So, tethering her phone was the only real possibility.
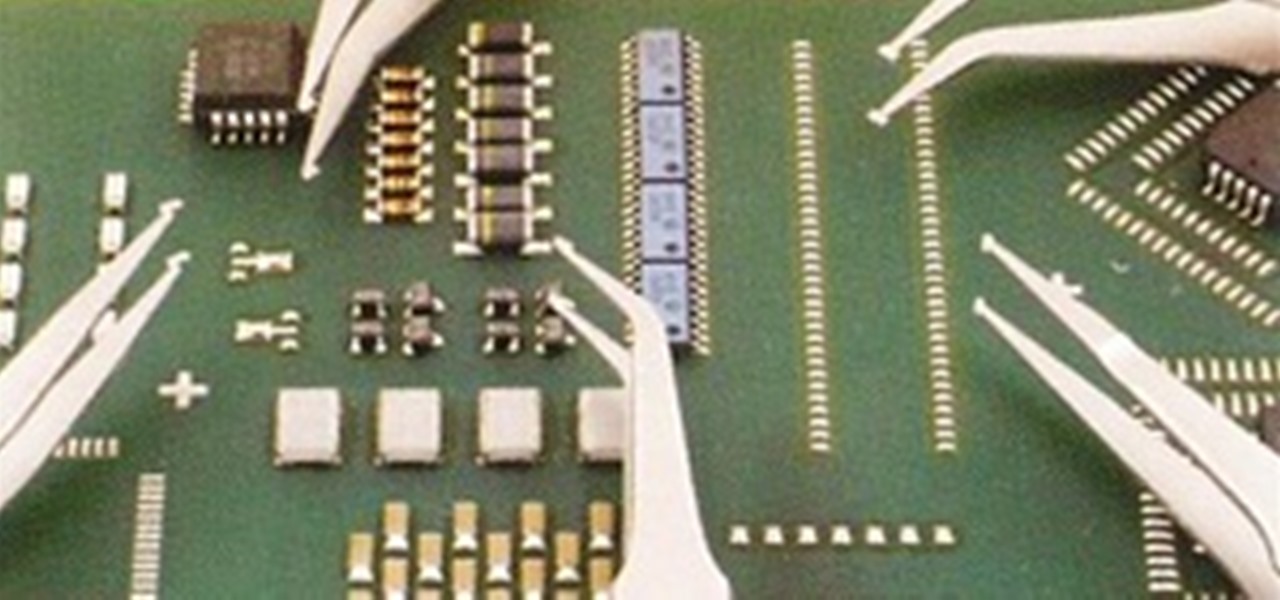
Whenever we make a homemade circuit, we use what are called through-hole components. Any components with long metal leads is a through-hole component. They are great for soldering to, but it's tough to fit enough through-hole resistors and capacitors into a smartphone. To get those last microns, we have surface-mount components for SMDs (surface-mount devices). These are all of those teeny, tiny things you see when you crack open your digital camera or laptop case.

With the mass arrests of 25 anons in Europe and South America, and the rumors of an FBI sweep on the east coast of America floating around, times look dicey for hackers. Over the past few days, a lot of questions have been posed to me about removing sensitive data from hard drives. Ideas seem to range from magnets to microwaves and a lot of things in-between. So, I'd like to explain a little bit about data forensics, how it works, and the steps you can take to be safe.

You've probably seen those deep-web images floating around on the Internet. Usually, it goes something like this: There is a towering iceberg and the deeper the underwater portion extends, the more “hidden” and “exotic” the content is described to be. Sometimes these images are accurate to a point, but most are just making things up.

In my second article of the laser weapon series (see the first part here on CO2 lasers), I'll be expanding on the potential of pulsed lasers.
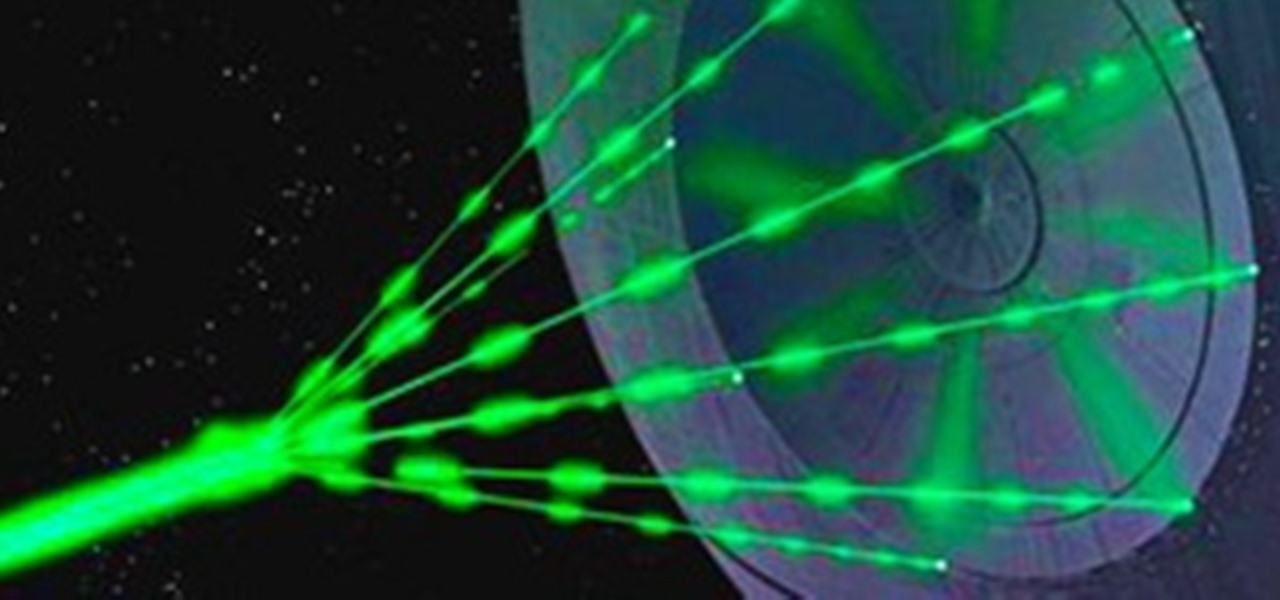
In this series on weaponized lasers, I'll be exploring the function, operation, strength and building instructions for three basic laser weapons; CO2, Diode, and Flashlamp. These laser types are just a few of many, selected because of their simplicity and basic construction (depending on your experience).
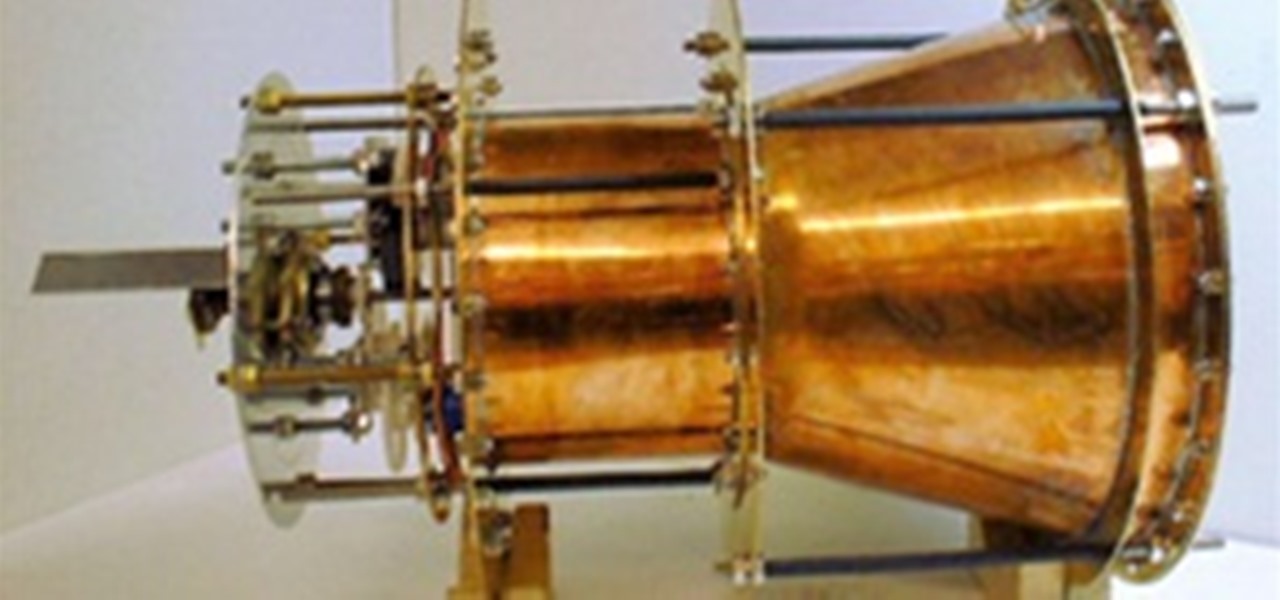
Welcome to Microwave Energy—the next part of my Making Electromagnetic Weapons series. For the Electromagnetic Pulse Generator, check out the last three articles (One, Two and Three).

Hello and welcome to another InfoSecurity World tutorial. The intent of this article is to teach one how to encrypt sensitive files. When set up correctly with a strong password, it would be almost impossible to hack. Even the FBI have had issues decrypting this software. I'm here to teach you how to create a general encrypted container—not the complex hidden TrueCrypt volume.

Last week I had a quick look at V.I.K.T.O.R, the anthropomorphized automated editing app that lives on your iPhone, and today it’s time to put it to work.
There's nothing better than playing a game of Scrabble, feeling the smooth wooden tiles in your hand and savoring the heavy fumes of cardboard, cheap wood and plastic as you rearrange the letters on your rack into the perfect word. You try to keep a straight face while you watch your opponent sweat, but you can't help but release that diabolical grin of self-admiration as you play the elusive triple-triple. The score's recorded and you feel sorry for your bitter rival, but then you remember y...

Since its release three years ago, Canon's EOS 5D Mark II has been the most sought out digital SLR for photographers everywhere. But it's also becoming a favorite amongst cinematographers, thanks to its compact size and high-def video recording mode, seeing action in everything from independent features to Hollywood blockbusters and even big network TV shows.