
News: Sneaky! WhatsApp Adds Encryption to iCloud Backups on the Sly
WhatsApp sneakily made some security changes to iCloud backups without your knowledge, ladies and gents. Not that strengthening security is a bad thing, but still!


WhatsApp sneakily made some security changes to iCloud backups without your knowledge, ladies and gents. Not that strengthening security is a bad thing, but still!

Rumors that Apple is honing its automated car technology have skyrocketed. Thanks, now, in no small part to some enterprising members of the media who leaked the names of Apple's self-driving car team to the public.

If you're a parent of a toddler (or have a friend that acts like a toddler), you occasionally need to take a break just to preserve your mental health. The perfect way to buy yourself some "me time" in this scenario would be to pull up an episode of Dora the Explorer on Netflix or YouTube, then hand your phone or tablet over to your child (or child-like friend) and try your best to relax while they're occupied.

Welcome back, my aspiring hackers! One of those areas of Linux that Windows users invariably struggle with is the concept of "mounting" devices and drives. In the Windows world, drives and devices are automatically "mounted" without any user effort or knowledge. Well, maybe a bit of knowledge. Most Windows users know to unmount their flash drive before removing it, but they usually think of it as "ejecting" it.

Your best chance of getting to a destination on time during rush hour is to drive through relatively empty HOV lanes. Thankfully, if you're using Waze to navigate through traffic, you can easily locate HOV or HOT routes to optimize travel times by adding your toll passes in the app's settings.

Cruise Automation, General Motors' (GM) driverless car arm, has hired two hackers who were once seen by many as a safety threat to help find vulnerabilities in its self-drive car network.

Baseball fans can now leave their wallets behind at specific stadiums throughout the country. A new upgrade by Appetize to the foodservice and retail technology used at ballparks means you can now use Apple Pay to make purchases at 5 Major League Baseball stadiums.

Furniture shopping is about to get a whole lot easier thanks to Apple's AR Kit and Ikea. In an exclusive with Bloomberg Businessweek, Tim Cook, Apple CEO said:
Unlike the Moto X with its Active Display or the Nexus 6 and its Ambient Display, some devices (especially those now running Lollipop) do not include a function that permits the display to turn on upon getting new notifications while the device remains locked or the display inactive.

Many people are bored of the typical square-ish icons arranged in a uniform grid on their Android homescreen. I dislike looking at grids of buttons and sometimes I would like to have some really HUGE buttons for the applications that matter the most at any given time.

All you science and astronomy nuts out there, pay attention, this detailed video tutorial series will tell you everything you need to know about using the Meade EQ Series Telescope to ogle the universe.

Once in a great while something comes along on the internet that’s so unbelievably simple and yet works so well. Twitter is one of them. On the video conferencing side, now we have MeBeam. MeBeam, which requires no software or drivers to be installed, is a web application that will permit you and up to 15 of your closest friends to hold a video/audio conference (provided you and said friends all have webcams or, at the very least, microphones). For further details consult this simple how-to!

A powered-off MacBook can be compromised in less than three minutes. With just a few commands, it's possible for a hacker to extract a target's password hash and crack it without their knowledge.

Sometimes, you encounter words in a non-native tongue while using your Android device. The Google Translate app has an awesome feature where it will translate any text you highlight. An overlay will appear, and on this overlay, there will be the translation of the foreign word. This can help you if you need a translation quick fix or if you are learning a new language.

Depending on your region, you may not be offered the same call recording option other OnePlus users have. But, as with most things Android, where there's a developer with a will, there's a way regardless. And the method we are about to describe is one of the easiest, most stable, and undetectable ways to do it. Perhaps we should discuss why OnePlus has been holding out you when it comes to this feature, though.

Some phones have a feature that turns your screen white for a second when you're taking a selfie in dim lighting. This does a great job of illuminating your face in a pinch, but there are two problems with it: First, not all phones have the feature, and second, it doesn't work in third-party camera apps like Snapchat and Instagram.

The highly anticipated iPhone X is finally up for preorder, and it's been almost as exciting as we expected. With the dual cameras, bezel-less display, and high-tech facial recognition, there's almost nothing on the iPhone X that won't be liked. But around the same time as the iPhone X's announcement, another phone was revealed, and almost everyone seems to have forgotten about it. We didn't.

Now that the cutting-edge iPhone X is up for preorder, everyone is excited to see how the new device will compare to offerings from Apple's competitors. Namely the Galaxy Note 8, which is a beast of a phone in its own right.

The next-generation Audi A8 to launch in July is expected to be the world's first Level 3-capable production car to go on sale in retail channels.

Uber's year is going from bad to worse, and they may be subject to a potential criminal probe in the ongoing Waymo legal battle.

Recent launches of YouTube TV and YouTube Go created a bit of excitement on the web. Though the latter allows downloading, it doesn't allow background playback, as that would require a YouTube Red subscription for $10 a month. However, there's still a way to get both of these features without paying a dime.

Chinese search engine giant, Baidu, has just announced its own autonomous car platform which is intended to speed up the development of driverless vehicles.

Uber's driverless cabs began picking people up in Arizona in February, after its attempt at a pilot test in San Francisco. Now, one of these cars has been in an accident, and that's just the tip of the iceberg.
Some manufacturers, like Samsung and LG, have had split-screen multitasking on their custom versions of Android for years. But starting with Android Nougat, Google added this functionality to AOSP, which means that all phones and tablets running Android 7.0 or higher will now have a new multi-window mode.

A judge just handed down a ruling that will make the U.S. government's quest to unlock the work iPhone of one of the San Bernardino shooters much more difficult.

Welcome back, my tenderfoot hackers! Hacker newbies have an inordinate fixation on password cracking. They believe that cracking the password is the only way to gain access to the target account and its privileges. If what we really want is access to a system or other resources, sometimes we can get it without a password. Good examples of this are replay attacks and MitM attacks. Neither requires us to have passwords to have access to the user's resources.

Editor's Note: The claims by Vani Hari which were originally detailed in the article below about azodicarbonamide were unscientific in nature. This article has been updated to reflect that and provide more scientific context on the issue.

The U.S. Postal Service has been in trouble for quite some time. With more and more people choosing to go digital to take care of bills, legal documents, and pretty much all other forms of correspondence, they haven't exactly kept up with the times. I mean, let's be honest—when was the last time you sent snail mail?

Walking the streets at night can be uncomfortably dangerous. In 2010, there were 32,885 motor vehicle deaths in the United States. Of those, roughly 13%, or 4,280, were pedestrians. Two-thirds of those pedestrian deaths occurred at nighttime. Along with darkness, drivers also have to deal with rain and other harsh weather conditions. Combined, all of these factors can be very dangerous for anyone taking a walk at night. As it happens, pedestrian deaths are on the rise since 2009.

Cruise Automation, the driverless car startup General Motors (GM) bought for $1 billion in 2016, is readying a formidable fleet of robo-taxis for rollout in cities throughout the US. But when it comes to details about how the company plans to realize these lofty goals, it's been fairly tight-lipped.

You may have recently seen a plethora of Instagram users, including celebrities and politicians, sharing a screenshot declaring that the platform will implement a new "rule" where it would own and could use your photos and videos however it wishes. The screenshots are part of an internet hoax, one that's been around in one way or another since 2012, but what can Instagram actually do with your media?
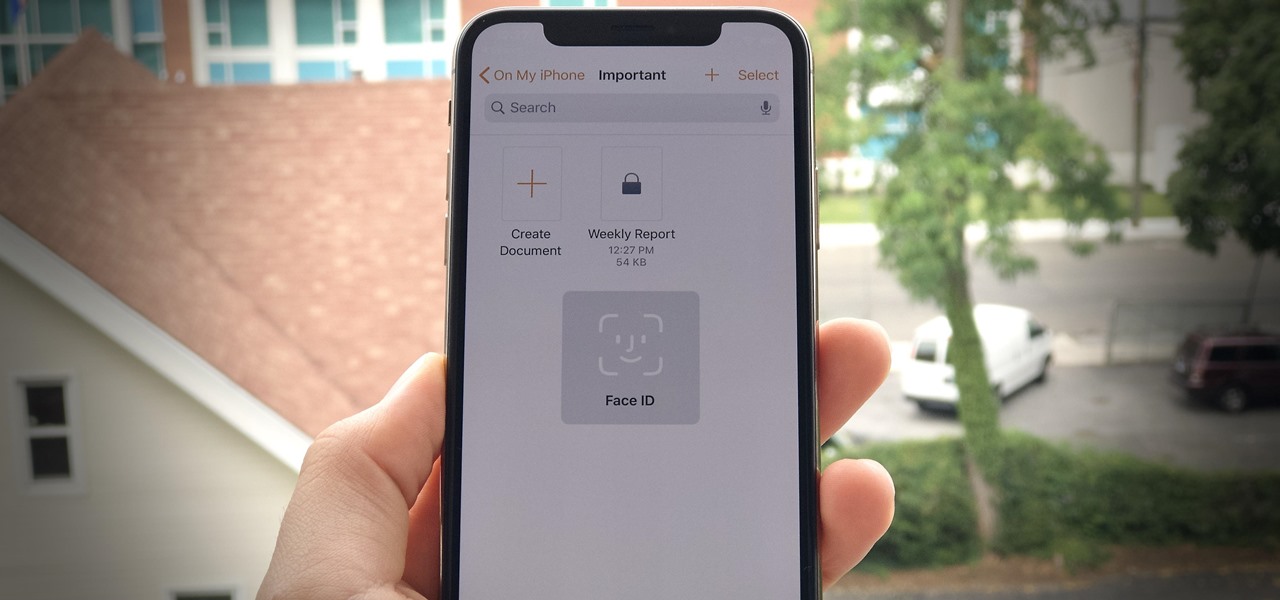
Your writing is just that — yours — so the work you do in Apple Pages should remain private until you choose to share it. Apple seems to share this sentiment. As another symbol of its dedication to user privacy and security, the company includes a feature in its word-processing app for iOS that allows you to lock documents behind a password, as well as with Face ID or Touch ID.

Giphy has had a few apps for iOS over the years. Giphy Keys was a keyboard built specifically for GIFs. Giphy Cam lets you create your GIFs complete with stickers. Giphy World is for adding augmented reality stickers to the real world. But now, Giphy has combined elements of all of these into its main app, so you can create, find, and share GIFs and stickers right from your keyboard.
Many apps claim to record phone calls on Android, but very few actually deliver. There's just too many different devices floating around out there for one app to be able to support them all — or so it would seem.

There's more to recording calls than just protecting yourself against liability or an angry ex — oftentimes, this feature is the perfect tool to save momentous calls like breaking news of your recent engagement to loved ones. And with the prevalence of video calls, you can even capture memorable video chats such as your mom's first glimpse of your newborn on your mobile, courtesy of Skype.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

As a longtime Android user, one of the changes I was most excited about with Android Pie was the fact that the volume rocker finally controls media volume by default. However, the new way isn't ideal for everyone, but thankfully, there's an app that can change it back.

With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

A team of academics from three different universities and two private companies have just discovered a new vulnerability that affects almost every Android device since 2012. The vulnerability is known as RAMpage, and it could be used to gain complete control over the device.

Another piece of Magic Leap's mysterious story has been uncovered thanks to a new patent application revealed on Thursday, March 15.