With its recent acquisition of 3D gaming engine PlayCanvas, Snapchat parent Snap, Inc. appears to be preparing a challenge to the existing players in the world of game development, particularly in terms of augmented and virtual reality gaming.

Patent holder Genedics, LLC has filed a legal complaint alleging that hand-tracking startup Leap Motion is infringing on its intellectual property.

Unity 5.6 was just released on March 31, and it will be the last entry in the Unity 5 cycle. With all of the new features, it looks like Unity 5 is going out with a bang.

Apple's just released a new beta of iOS 7.1 for developers, Beta 5, which fixes some small bugs and adds some minor feature enhancements. With previous reports stating that the final version of 7.1 was slated for a public release in March, these early leaks are indications that the final will be released in the following weeks, shortly after the Golden Master version hits developers.

For being an inexpensive tablet, the Nexus 7 packs a 1,280 x 800 pixel resolution into a relatively small display, offering a very sharp-looking 216 pixels per inch. What does that mean? It's one of the best e-readers on the market.

Most carmakers now agree with Waymo that piloting driverless cars is best left to the machine — with no meddling from the human.

Check out this supernatural tutorial video that offers 7 tips on getting started in becoming a paranormal investigator. Just follow these simple steps:

The Audi A8 may be short on the wow factor as the industry's first Level 3 car, but Audi has revealed some interesting details about one stand-out feature underneath the hood: the car's ability to self-pilot itself at stop signs and lights.

All eyes will be on Tesla CEO and founder Elon Musk tonight to see if he is reveals details about the status of Tesla's challenged Autopilot at tonight's official Model 3 launch party.

The Cloud Security Alliance (CSA), a leading IT trade association, has published its first report on risks and recommendations for connected-vehicle security, ahead of when driverless cars are about to see volume production in the near future.

WhatsApp sneakily made some security changes to iCloud backups without your knowledge, ladies and gents. Not that strengthening security is a bad thing, but still!

Is your blog booming or just plain boring? IMaybe it's not boring, but you probably aren't getting much traffic, at least, not the amount you want. If you want to learn how to increase your traffic to your blog or website, this video has information pertaining to quick traffic.

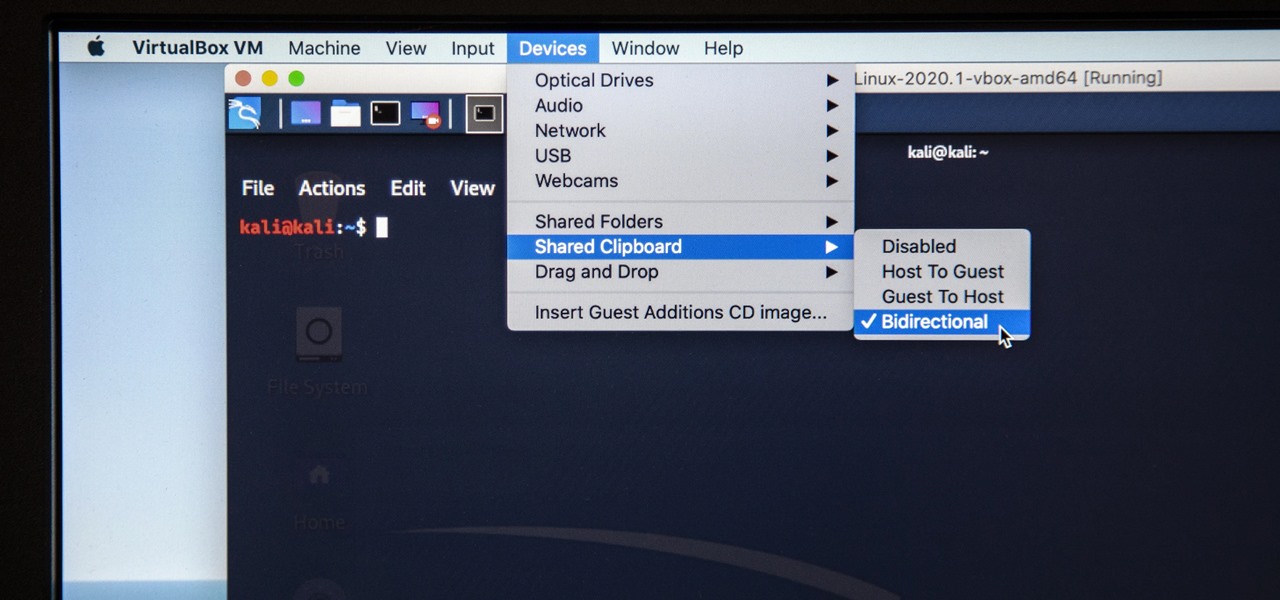
Last week, I updated VirtualBox on my computer since I had skipped a few versions, then I could no longer copy text or paste text from my Kali virtual machine to my host OS and vice versa. Installing the Guest Additions didn't seem to do anything, and the bidirectional shared clipboard was enabled, but there was one thing that did work for me that may help you out too if you experience the issue.

Samsung, like other OEMs, partners with third-party companies to include their apps on Galaxy devices. For example, Microsoft pays Samsung millions to pre-install certain Office apps. But one of these partners might not be on the up and up.

The latest official update for iPhone, iOS 13.2, introduced 22 new features and changes to the iOS 13 era, building off the improvements brought by iOS 13.1 and iOS 13 proper before it. It's time to take our first peek into what's next for iPhone and iOS, as Apple releases iOS 13.3 developer beta 1 today, Tuesday, Nov. 5.

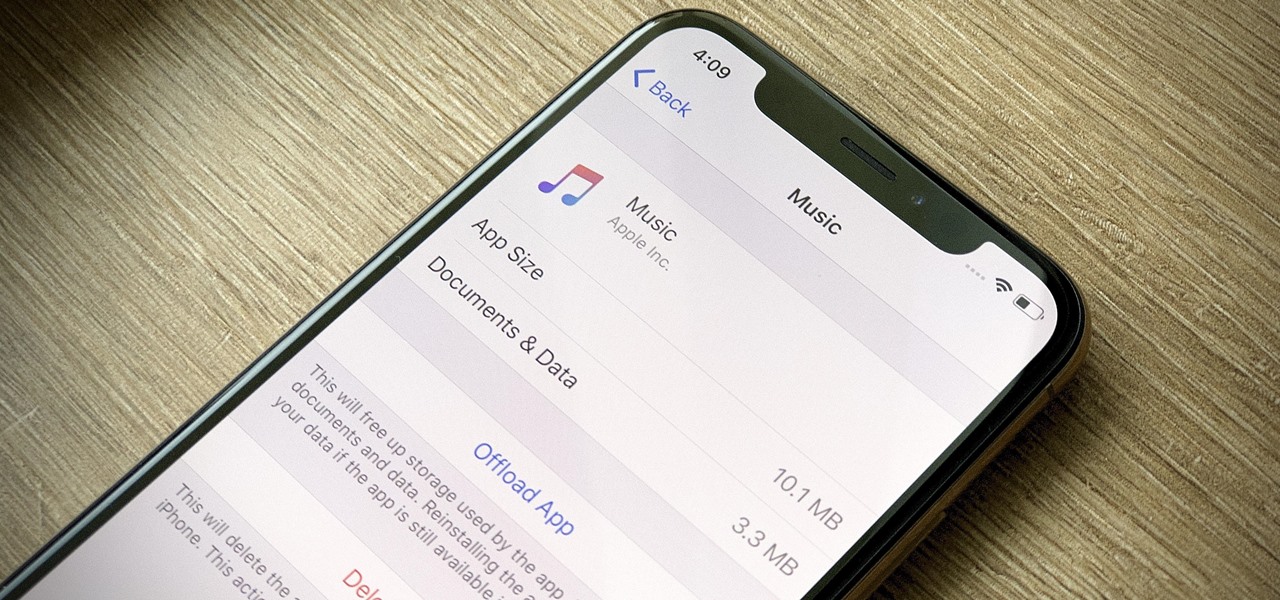
While smartphones are increasing their built-in storage every year, they're also giving you more features that consume all that extra space quickly, like when you shoot 4K videos. So while you may have a load of gigabytes for all your music, it may get eaten up quickly by apps, photos, and videos. Luckily, Apple Music has an auto-delete feature, so you don't have to manage anything manually.

With the change to a glass back, many of us are concerned about the durability of OnePlus 6. While glass does offer some benefits such as lighter weight, without proper reinforcement, it can easily shatter in one drop. Now we have our our first look at its durability thanks to JerryRigEverything.

By default, the Galaxy S9 and S9+ only have 15 media volume steps — in other words, there are only 15 increments between silent and full volume. That's usually fine if you're using your phone's speakers, but if you're wearing headphones, more fine-tuned controls would be helpful.

A massive leak appeared the web today, and it's got some huge security implications for every iPhone on the market. On the plus side, it also has some potential for enabling deep-level modifications and jailbreak tweaks.

Apple just pushed out iOS 11.2.5 beta 7 today for iPad, iPhone, and iPod touch to both developers and public beta testers. On Wednesday, Jan. 17, beta 6 was released, and there were two betas the previous week. With Apple promising a patch for "ChaiOS" next week for everyone, it's like iOS 11.2.5 will be that update.

Snapchat announced today that you can now design geofilters in-app, making it easier than ever to customize your snaps. This new feature incorporates a mobile creative studio, so you no longer have to use your computer to create your custom masterpiece.

This week's Brief Reality is led by a pair of stories with an eye to the future of the augmented reality industry, first in terms of standards for the industry, then with regards to its future applications in the automotive realm. Finally, one company looks to boost its future sales with an executive hire.

Google's Pixel and Pixel XL flagship phones are a rousing success, with consumers praising the fluid user experience and overall performance as two of the devices' biggest strengths. But even though Google may have knocked it out of the park with a set of Apple-like smartphones that "just work," there's still room for improvement in a few areas.

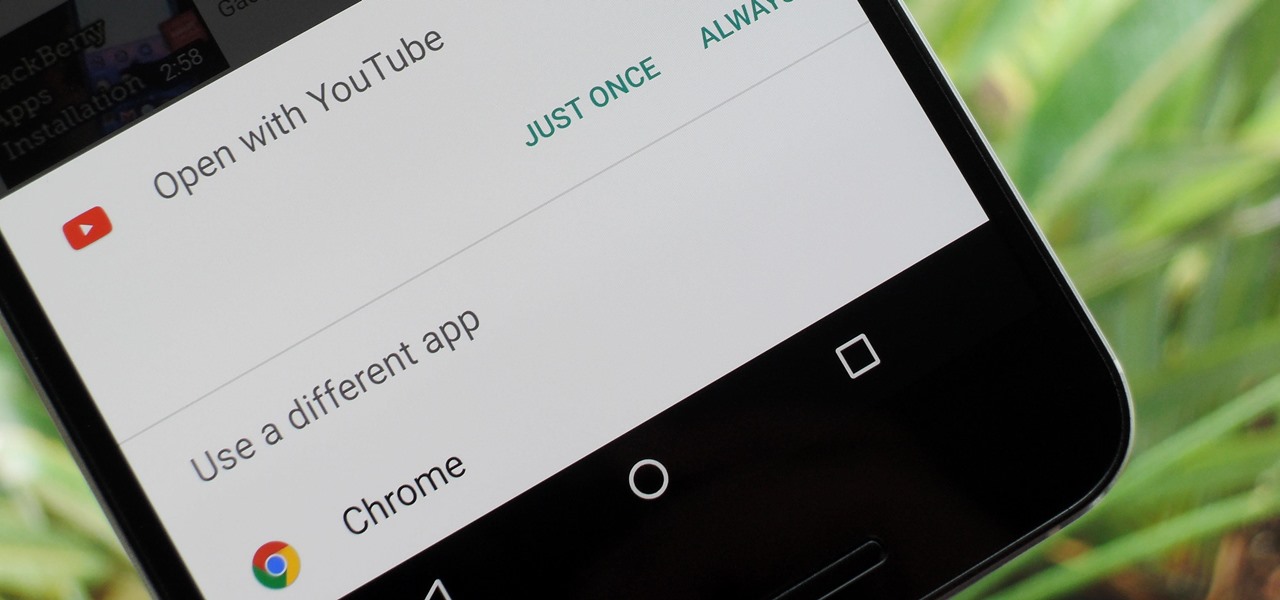
One of Android's biggest strengths relative to iOS is the fact that you can use any app to open compatible links, not just the stock ones that come preloaded on your device. When you tap a link that two or more of your apps are capable of opening, you'll see a message asking which app to launch it with—and from there, the choices are "Just Once" or "Always."

A judge just handed down a ruling that will make the U.S. government's quest to unlock the work iPhone of one of the San Bernardino shooters much more difficult.

A little-known company in India is making waves after announcing that it will sell an Android 5.1 Lollipop smartphone for less than $4 (or, more precisely, 251 rupees). The Freedom 251, from Ringing Bells, sounds almost too good to be true. Is that because it is?

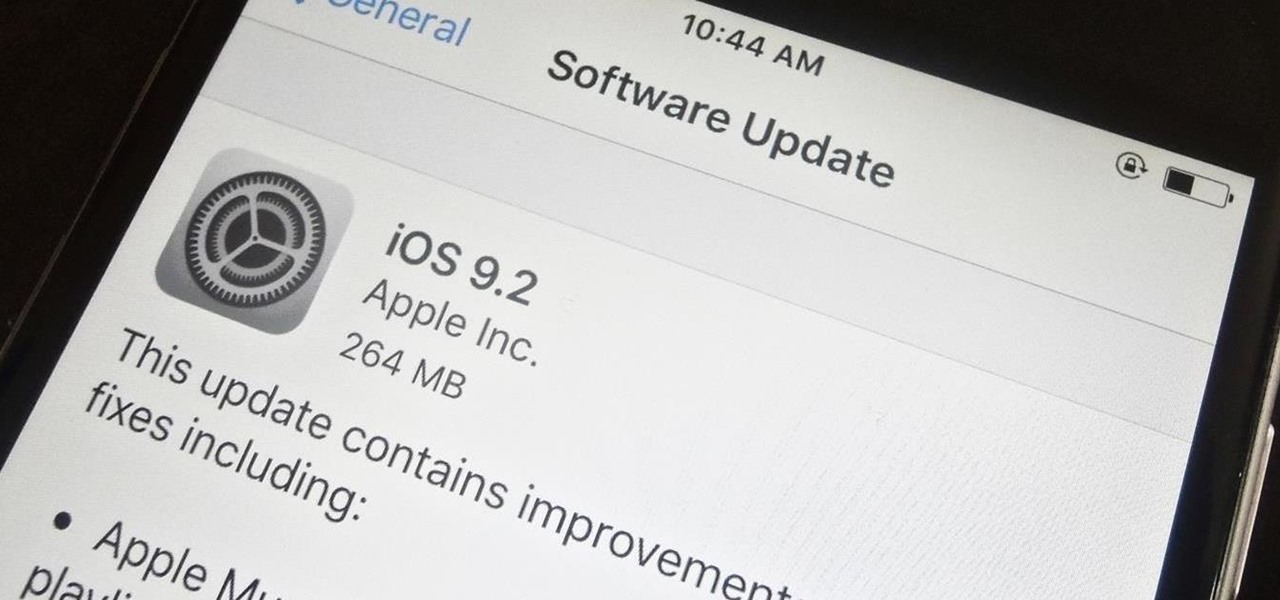
We're near the end of a productive year for Apple, one that introduced a new Apple TV, the iPad Mini 4 (in conjunction with the Apple Pen), the iPad Pro, and the iPhone 6S and 6S Plus, as well as iOS 9. Now, the second major update to iOS 9—version 9.2—has just been released to the public.

Samy Kamkar, the security researcher known for the MySpace Worm and his combination lock cracking skills (using an online calculator), is back—and this time, he's after your credit cards!

As mobile devices become more and more popular, service providers have unfortunately resorted to capping data. What this means is that, depending on the plan you have with your ISP, you could have limits placed on how much data you can use for a set period of time. Once you've hit the limit, your ISP could drastically slow down or throttle your internet speed or charge you outrageous overage fees.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

The next-generation Audi A8 to launch in July is expected to be the world's first Level 3-capable production car to go on sale in retail channels.

With thousands of people across the country protesting, you might be thinking about joining the march. But as is too often the case, law enforcement has been called to oversee the protests, and interactions aren't always peaceful or lawful.

The art of privilege escalation is a skill that any competent hacker should possess. It's an entire field unto itself, and while it's good to know how to perform the techniques involved manually, it's often more efficient to have a script automate the process. LinEnum is one such script that can be incredibly useful for privilege escalation on Linux systems.

It is said that the best way to avoid detection when hacking is to leave no trace, and often that means not touching the filesystem at all. But realistically, in most cases, it's impossible not to interact with the filesystem in one way or another. The next best thing to do to throw off any investigators is to change the file attributes to hide activity. We can do this with Metasploit's Timestomp.

Filmic Pro has a superb suite of professional settings — bit rate, frame rate, and mic choice, to name a few — which can enable you to capture the best footage possible. But different shots require different setups, and it can be frustrating to change settings on the fly. Filmic Pro lets you skip that whole process by saving your favorite settings as presets for quick and easy access.

The recent announcement of a $480 million US Army contract awarded to Microsoft over Magic Leap for supplying 100,000 augmented reality headsets shows just a how lucrative the enterprise (and government) sector can be for AR.

Hundreds of Windows 10, macOS, and Linux vulnerabilities are disclosed every single week, many of which elude mainstream attention. Most users aren't even aware that newly found exploits and vulnerabilities exist, nor that CVEs can be located by anyone in just a few clicks from a selection of websites online.

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.

With the rise of website encryption (TLS), sniffing passwords from network activity has become difficult. However, it's still possible to quietly exfiltrate a target's network traffic in real time to extract passwords and sensitive information. Pertaining to macOS, there are two methods for retrieving traffic from a backdoored Mac.

IFTTT (short for If This, Then That) is an amazing piece of software that automagically links actions on your phone with online services and real-world objects. For example, an applet could read: "if you come home, then turn on Wi-Fi." IFTTT goes further than just using simple smartphone functions, though — thanks to applets, it's fully configurable with a ton of smartphone apps.