In this tutorial, we learn how to rig a counter weight trap. This is great as a fishing trap but can be rigged to be used as a tree trap. First, you will need to take a rock and wrap around it to create a counter weight. After this, bring the rope high over a branch, then down onto a lower branch. From here, wrap the rope around the trap and leave the rest of the string hanging. Now, the rock should be hanging high in the air and there should be a stick tied to the bottom of the rope to keep ...

A new study published by American University demonstrates how Pokémon GO and other augmented reality games can help city governments bring communities closer together.

Despite the fact that over 600,000 Snap Lens filters have been created since Lens Studio debuted in 2017, and Facebook is reporting that more than a billion users have interacted with its Spark AR filters across Facebook properties, social augmented reality filters get a bad rap in the AR industry.

Augmented reality is often likened to granting superpowers to mere mortals, but what about mutant powers?

If you're a part of Generation X or a Millennial, there's a good chance that the first mobile game you played was Snake on an old school Nokia phone. Now, you can relive that nostalgia of monochrome and push buttons in augmented reality with the Facebook Camera.

The company behind Japan's beloved Gozilla, Japan's Toho Studios, has for years tried to give fans the sense of what a giant, nuclear-powered lizard invading Tokyo might feel like. Until now, those attempts have been limited to the movie theater, but now, with the help of the Microsoft HoloLens, Godzilla is finally getting its chance to invade the actual city, with terrified fans looking on from a safe distance.

Honeywell recently completed successful testing of virtual window technology that enabled drivers to maneuver an otherwise windowless combat vehicle on rough terrain at speeds exceeding 35 miles per hour.

After the mobile augmented reality platforms of ARKit and ARCore moved Google's previously groundbreaking Project Tango (the AR platform that gave us the first smartphones with depth sensors) into obsolescence in 2018, we've seen a bit of a resurgence of what was then a niche component for flagship devices.

Sure, it's the giving season, but sometimes you've just got to treat yourself to some cosmetics. If you're shopping at Walmart, L'Oreal just made that a shade easier when shopping for Garnier hair color products with an assist from Google Lens and the Modiface AR platform.

Months ago, we showed you some of the powers of Spatial, the HoloLens app that allows groups of workers to collaborate in augmented reality using 3D avatars.

The Super Bowl of bicycle racing, the Tour de France, added augmented reality to its TV broadcast this year.

The crime procedural show is the perhaps the most direct path to the average TV viewer's heart. Could the same hold true for augmented reality games?

Just weeks after officially launching its mobile augmented reality toolkit, Google can now claim one of its first Android and ARCore app exclusives with the Curate app from Sotheby's International Realty.

Just as the Transformers animated TV series of the '80s were basically half-hour commercials for toys, a new Transformers AR app for iOS similarly functions as a promotion for the latest installment in the film franchise.

The world is a massive place, especially when you consider the field of view of your smartglasses or mobile device. To fulfill the potential promise of augmented reality, we must find a way to fill that view with useful and contextual information. Of course, the job of creating contextual, valuable information, to fill the massive space that is the planet earth, is a daunting task to take on. Machine learning seems to be one solution many are moving toward.

With mobile developers near and far primed to implement augmented reality into their iOS apps with Apple's ARKit, uSens offers them a new tool for markerless location tracking.

From Farmville to selling a company to Google, Amitt Mahajan has been through the startup ringer. Now, as managing partner with Presence Capital, he's funding the future of augmented and mixed reality.

Over the past decade, Marvel Studios has been a dominant force at the box office, raking in more than $21 billion dollars. Averaged out over that span of time, the yearly earnings of those movies outweigh the gross domestic product of some countries.

Wearables startup North has made a smart move to get its Focals smartglasses into the hands of more consumers.

After adding dual cameras to its camera glasses, Snap is finally taking full advantage of the depth-sensing abilities of newer iPhones as well, extending the use of its new 3D Camera Mode.

Back to the Future Part II missed wildly on many technological advances for the year 2015, such as flying cars and rehydration ovens. However, it connected on several predictions, such as video calling and biometric security, and it was in the ballpark (pun intended) on others, such as the Chicago Cubs winning the World Series.

Smartglasses startup Nreal enjoyed some highs and endured some lows this week, as the company landed a product placement with Kevin Bacon but then faced production issues related to the coronavirus outbreak.

Magic Leap's legal battle against Nreal has taken an intriguing turn this week, as Magic Leap set a date to discuss the matter with Nreal. But a new partnership struck by Nreal adds another wrinkle to the duel between the two AR wearable makers.

If we were to assign a theme for the 2019 edition of the Next Reality 30 (NR30), it might be something along the lines of, "What have you done for me lately?"

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.

Every step in the evolution of computing brings an in-kind leap forward in user input technology. The personal computer had the mouse, touchscreens made smartphones mainstream consumer devices, and AR headsets like the HoloLens and the Magic Leap One have leveraged gesture recognition.

You may have noticed improved photo quality in the Android Snapchat app in recent months. Believe it or not, this is because Snapchat only just recently started using a decade-old camera API that predates every Android phone in existence.

At first glance, it may not sound like there's much value in doing a crossword puzzle in augmented reality, but The New York Times has managed to revamp the pastime as an immersive game.

Sending Christmas cards via snail mail is so passé. Why spend the time and money for a bougie photoshoot, saccharine card design, and postage when you can use augmented reality to instantly dress up photos and videos to send to friends and family instead?

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

After first being announced at Mobile World Congress 2018, the ASUS ZenFone 5Z will finally be coming to the US. Deemed an iPhone X clone by some, there is more than meets the eye when it comes to this flasghip. While it is similar to the iPhone X, in some ways, it improves on the design.

With the announcement of ARKit 2.0 at WWDC 2018, Apple is bringing some powerful new capabilities to mobile augmented reality apps this fall.

Gaining access to a system is always exciting, but where do you go from there? Root or bust. Sure, a compromised host is a great way to run a botnet, or do some other boring, nefarious thing—but as hackers, we want root. We also want to take the easiest path possible, search out low-hanging fruit, and exploit them. SUID programs are the lowest of the low-hanging fruit.

Angry Birds, one of the first franchises to find success in mobile gaming, continues to shoot its shot at new life in augmented reality gaming.

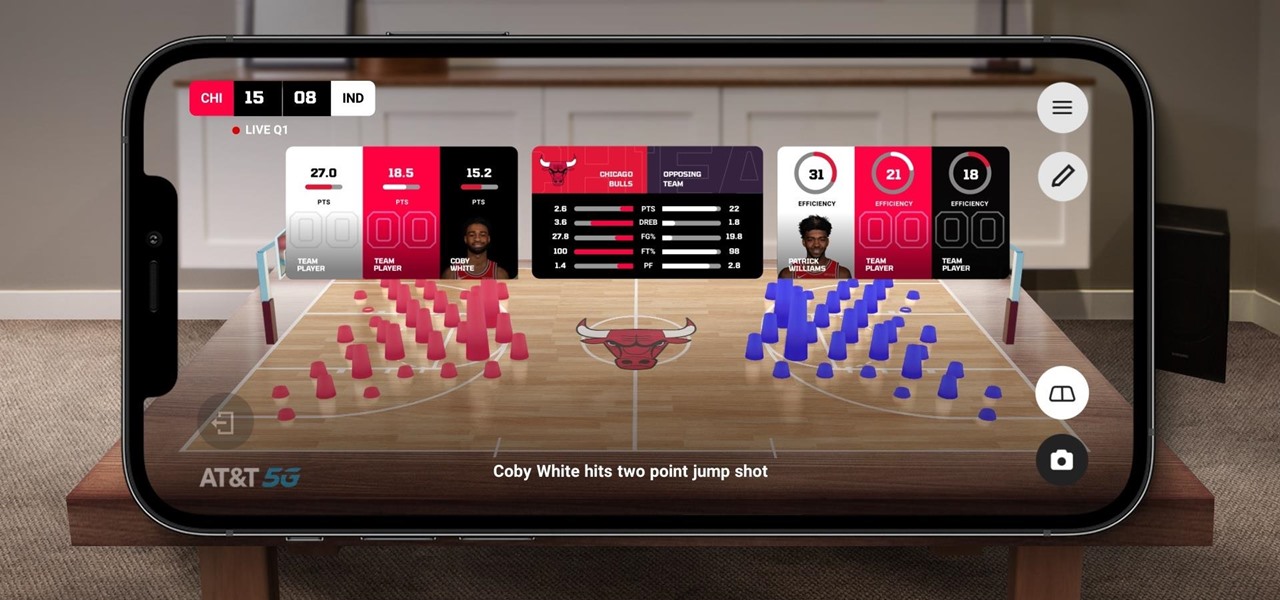
The Chicago Bulls may not be very relevant in the current NBA standings, but they do lead the league in one other area.

The COVID-19 pandemic forced many businesses into remote work models, whether they were ready or not, making Zoom a household (or home office) name for its video conferencing service.

The past year has revealed a gaping hole of opportunity in the world of business called virtual meetings. Some existing players like Zoom hopped on that opportunity, while others like Skype seemed stuck on the sidelines, and Google Meet just managed to catch up in time to snag some of the shift in remote work.

Walsh, a new community under construction on 7,200 acres of former ranch land near Fort Worth, Texas, will one day contain 15,000 homes.

During a penetration test, one of the most important aspects of engaging a target is information gathering. The more information you have coming into an attack, the more likely the attack is to succeed. In this article, I'll be looking at SpiderFoot, a modular cross-platform OSINT (open-source intelligence) gathering tool.

We're still basking in the afterglow of the HUGE Snap Partner Summit last week, where Snap made Snapchat a much stronger augmented reality platform while also unveiling the AR smartglasses version of Spectacles. This week, we got a peek at how Spectacles AR started and got our hands on Lenses from Lego and Disney featured during the keynote.