As headlines focus on melting glaciers and rising water levels caused by global warming, climate change is quietly taking its toll on the nearly invisible occupants of this planet, the microbes.

The bacteria Klebsiella pneumoniae is a bad actor known for being antibiotic-resistant and causing a variety of serious infections in hospitals, including pneumonia, surgical site wounds, and meningitis. K. pneumoniae is something you do not want to encounter if you have a compromised immune system.

If you ever imagined turning the surface of your desk into one large augmented computer, well the future might not be far off, my friends. Lampix, the company that transforms any surface into a smart surface, is currently working on a portable and quite fashionable lamp to project an augmented computer onto any surface that you can interact with using your hands.

LOOOK, a Seattle-based mixed reality and development studio, can now peer into the future with their new geotechnical engineering visualization application for Microsoft HoloLens.

Alright, NB community! Here we go... Bubble Sort. What Is Bubble Sort?

Welcome back! In our last training session we covered classes and how OOP can make programming/scripting easier. Today we'll be taking a breather and covering something fairly simple, bitwise operators.

Hey there, reader! In this tutorial we are going to explain how values are stored in variables as either signed or unsigned. Try to not get lost!

Hello there, reader! If you've clicked on this How-to then it means you are interested in learning some C programming or just generally curious about what this page has to offer. And so I welcome you warmly to the first of many C tutorials!

Welcome back, my nascent hackers! We have spent a lot of time in previous tutorials focused on hacking the ubiquitous Windows systems, but the vast majority of "heavy iron" around the world are Linux or Unix systems. Linux and Unix dominate the world of Internet web servers with over 60% of the market. In addition, Linux and Unix servers are the operating system of choice for major international corporations (including almost all the major banks) throughout the world.

Welcome back, my novice hackers! It has become clear from some of your questions that quite a few of you are unfamiliar with the hexadecimal system, or simply, hex. The hexadecimal system is used throughout computing and if you have never studied this Base16 numering system, it may appear relatively opaque.

Welcome back, my hacker trainees! A number of you have written me regarding which operating system is best for hacking. I'll start by saying that nearly every professional and expert hacker uses Linux or Unix. Although some hacks can be done with Windows and Mac OS, nearly all of the hacking tools are developed specifically for Linux. There are some exceptions, though, including software like Cain and Abel, Havij, Zenmap, and Metasploit that are developed or ported for Windows.

It is often said that the best hackers remain unknown, and the greatest attacks are left undiscovered, but it's hard for an up-and-coming penetration tester or white hat to learn anything unless one of those factors is actually known or discovered. But the end goal here in our SQL injection lessons is to make that statement as true as possible for us when performing our hacks.

The key to becoming a competent white hat is knowing how the technology that you are trying to exploit actually works. SQL injection is one of the most common methods of attack used today and also one of the easiest to learn. In order to understand how this attack works, you need to have a solid grasp of ... you've guessed it ... SQL.

In Guardians of the Galaxy Vol. 2, Mantis resides in the shadow of an Ego who considers himself the actual heart of the universe. But when it comes Halloween costumes? Mantis will be the center of attention every time. The internet sure has noticed Mantis, and it's abuzz with debate over who she is. Is she just another iteration of the submissive Asian woman stereotype? Or is her character an empowering representation of empathy and the autism spectrum?

If you need a tiny, flexible attack platform for raining down human-interface-device (HID) attacks on unattended computers, the USB Rubber Ducky is the most popular tool for the job. By loading the Ducky with custom firmware, you can design new attacks to be effective against even air-gapped computers without internet access. Today, you'll learn to write a payload to make "involuntary backups" through copying a targeted folder to the Ducky's USB mass storage.

Killing more than 29,000 people each year, infection with Clostridium difficile (C. diff or CDI) is the most common healthcare-associated infection in the US. In a disturbing development, new research reveals recurring cases of the infection are soaring.

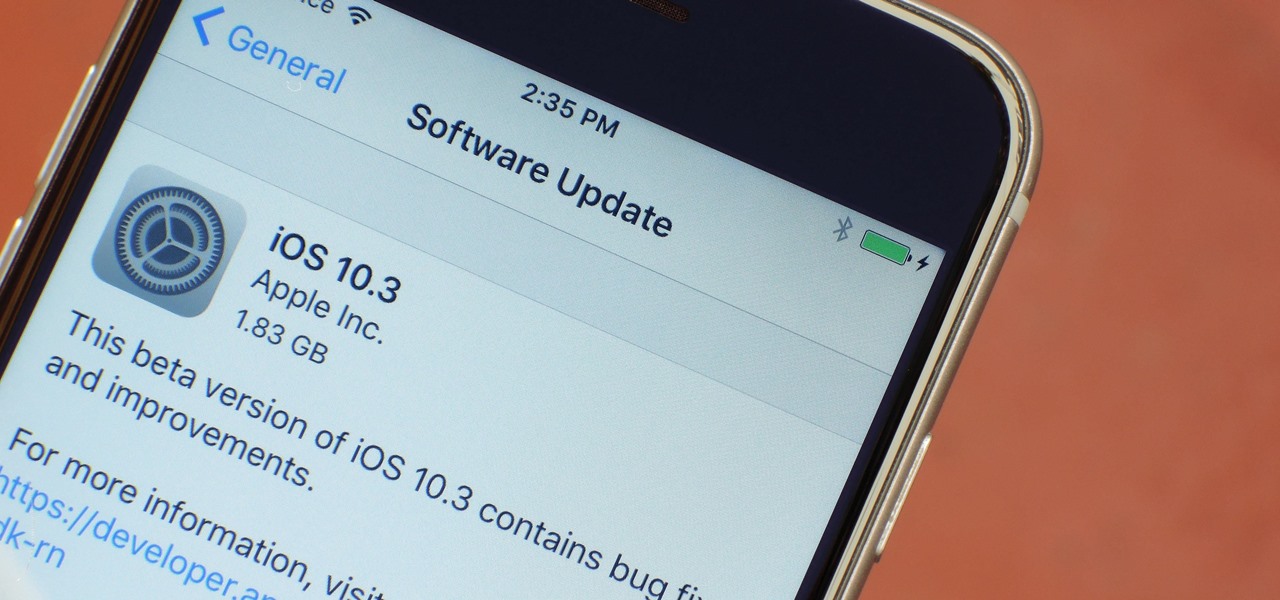
Apple just pushed out the iOS 10.3 update to everyone on March 27, so if you haven't installed it yet, make sure to do so by going to Settings -> General -> Software Update. Trust us, you'll want to.

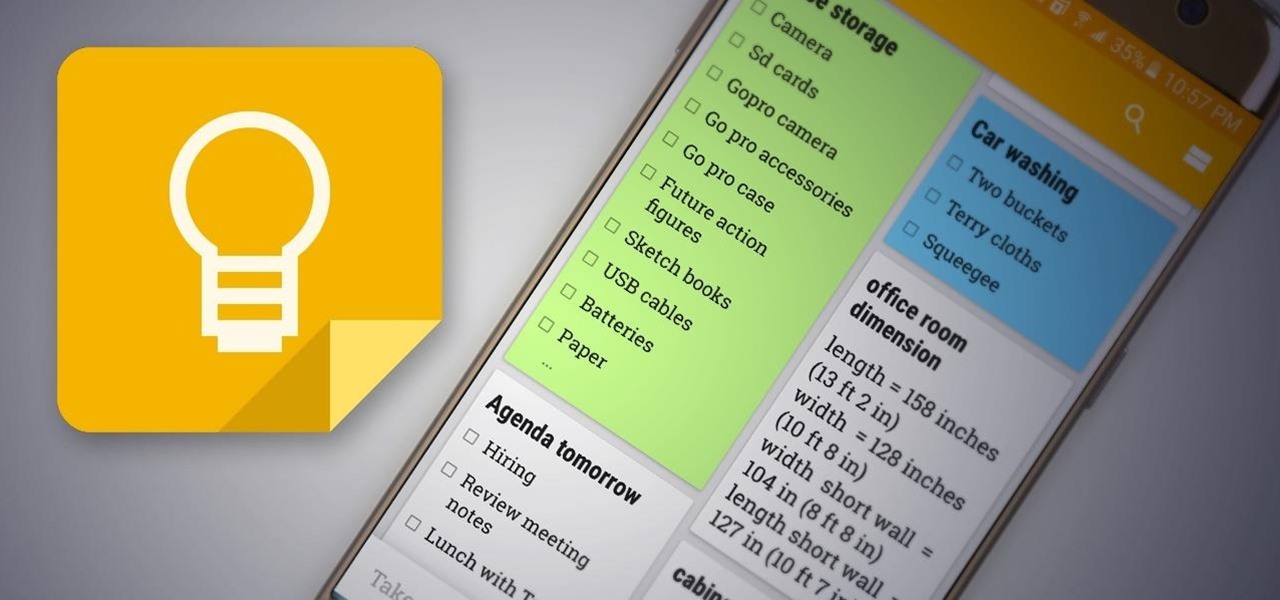
When it comes to note-taking, Google Keep is one of the most diverse and functional applications on the Android platform. Sure, there are a plethora of other note-taking apps to choose from, such as ever popular OneNote and Evernote, but Google Keep differentiates itself from the crowd with its user-friendly interface and Google Now integration.

Hello everyone! How's subnetting going? Did you practice a lot? I hope you did, but even if you didn't we will go through some more examples so you can be feeling confident after reading this article. It's all about that bad boy binary!

Welcome back, my novice hackers! One of the most common questions that Null Byte readers ask is: "How can I evade detection by antivirus software on the target?" I have already talked about how AV software works, but to obtain a deeper understanding, what better way is there than opening up and dissecting some AV software?

Why can't I see who is stalking my Facebook profile?

A travelator, also known as a moving walkway or moving sidewalk, seems like a tricky thing to build in Minecraft, especially when it's zigzagging, but there are really simple autowalks out there (like this one).

The practice of using sound to trigger augmented reality interactions hasn't been widely used, but a new experience is so impressive that it could kick off more use of the dynamic.

Digital artist Beeple's $69 million NFT art auction at Christie's has a second act called Wenew, and includes attempting to open the digital art floodgates to mainstream collectors and artists alike by using physical goods.

For awhile now, Google has offered the ability to translate text through smartphone cameras via Google Translate and Google Lens, with Apple bringing similar technology to iPhones via Live Text.

Nintendo may be developing cases that'll turn your iPhone into a gaming device like the Game Boy, but until something materializes there, you're stuck with cheap knockoffs on Amazon or a real Game Boy or Game Boy Color. But there's something else you can do to play eight-bit Nintendo games on your iPhone right now.

In just a few weeks, on May 29, the annual AWE (Augmented World Expo) conference will take place once again in Silicon Valley (Santa Clara, California, to be exact).

The rise and fall of Meta, the Silicon Valley-based augmented reality startup that looked to challenge the likes of Microsoft's HoloLens, and others, took just six years.

Google's next-gen cellular carrier, Google Fi, which replaces Project Fi, is making waves across the mobile industry. With super-cheap plans starting at only $20 and the ability to connect to millions of Wi-Fi hotspots across the globe, it's tempting many users to make the switch from AT&T, Sprint, T-Mobile, and Verizon Wireless.

As you're surely aware, your phone can be used against you. Thanks to our cameras and microphones, a clever hacker can obtain access to your device and invade your privacy. But spying isn't limited to just these two sensors — gyroscopes, proximity sensors, QR codes, and even ads can be used to paint a very clear picture about who you are and what you're currently doing.

An incorrectly scaled object in your HoloLens app can make or break your project, so it's important to get scaling in Unity down, such as working with uniform and non-uniform factors, before moving onto to other aspects of your app.

Configuring onion services for the first time can be tricky. A surprising number of system administrators make seemingly trivial mistakes that ultimately lead to catastrophic cases of de-anonymizing supposedly anonymous sites on the dark web. OnionScan is a tool designed to identify common misconfigurations in onion services and aid us in understanding how to fix them.

You know Moana's a rock-solid pick for Halloween this year. The question is, how far will you go to become Moana? Are you going to just slap on a cream skirt and a red bandeau? Or do you want to go all out and end up with the finished product like YouTuber Gladzy Kei did?

Tossing an old Android smartphone with a decent battery into your hacking kit can let you quickly map hundreds of vulnerable networks in your area just by walking or driving by them. The practice of wardriving uses a Wi-Fi network card and GPS receiver to stealthily discover and record the location and settings of any nearby routers, and your phone allows you to easily discover those with security issues.

Tony Parisi, the global head of VR/AR at Unity Technologies, has been passionately working with virtual and immersive spaces for a long time. And while the internet world we live in now is very different than when Parisi was co-authoring VRML (Virtual Reality Modeling Language) — an early attempt at creating 3D environments that would work in a web browser — some of the questions that were assumed answered are being asked again.

Many people find Steampunk problematic for a whole host of reasons, not least of which is the glorification of an era of Western history that featured institutionalized slavery, racism, sexism, elitism, and many more -isms.

The cinematic photos feature in Google Photos can create impressive three-dimensional views of normally flat images, turning ordinary pictures into life-like representations of the moment captured. Google Photos would automatically pick images from your library to apply the effect to. Now, you can choose images on demand from your library — it's just not super obvious that you can.

"Unfortunately, no one can be told what the matrix is, you have to see it for yourself." That's the line just before Morpheus gives Thomas Anderson (aka Neo) the red pill, finally opening his eyes to the tapestry of code that has veiled his eyes for his entire life.

For most mainstream users, LiDAR sensors for precision depth sensing remain the exclusive domain of Apple iPhones and iPads, but Google is helping Android device makers close the depth gap on the software side via its ARCore toolkit.

Thanks to numerous smartwatch deals this holiday season, many people are receiving their first one. But what exactly can they do? In regards to fitness, quite a lot. With a growing list of sensors and software updates, these small devices can be the very thing you need to ultimately reach your fitness goals.