The Metaverse, or AR cloud, has been a sci-fi dream for decades, but only recently have companies begun to actually develop the technology to build it. With its latest funding round, Epic Games is suddenly a front-runner in this pursuit.
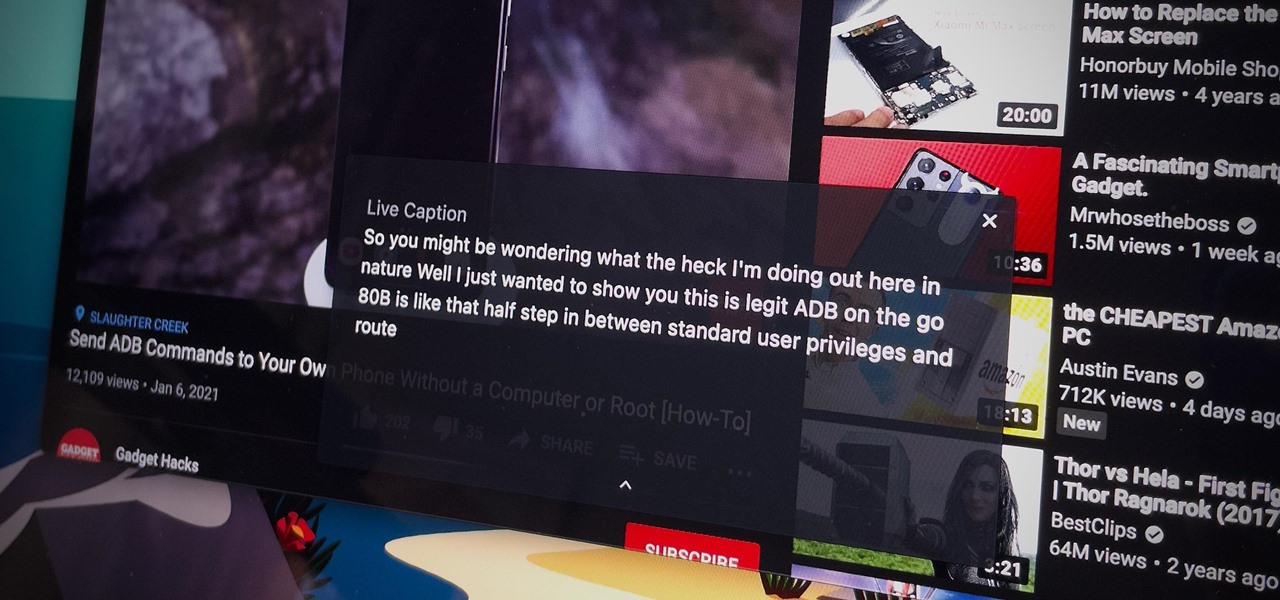
Captions are great for catching every word and important sound in a movie or TV show, but now there's a way in Google Chrome's desktop browser to enjoy captions for any audio file or source. You could ensure you never mishear a comment during an online meeting, and you could even follow along to a song's lyrics on platforms that don't already have in-sync lyrics, such as SoundCloud.

UPDATE: The OnePlus 8 Pro has been released! Check it out on the official OnePlus website or read through the rumored specs we've left below for posterity.

A good smartphone can be the perfect workout companion. You have music for motivation, videos for pushing through boring cardio sessions, GPS to keep you on course, and even an array of sensors for gathering data about your workout. But not all phones are created equal when it comes to helping you stay fit.
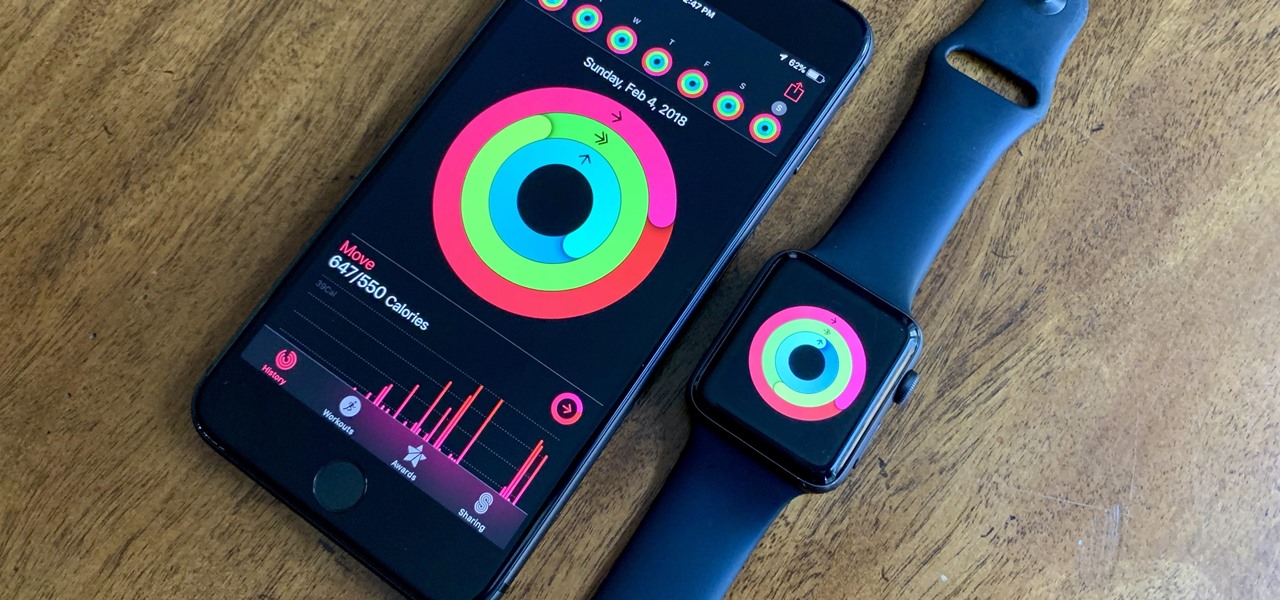
Apple Watch owners know the struggle — it's the end of the day, and those rings aren't met. Whether you forgot your watch before hitting the gym, let the battery run out, or just didn't move enough, you could feel the sting of fitness failure. But it doesn't have to be this way. You can actually close your Activity rings yourself; it just takes a little know-how.

Gotta catch 'em all, right? That's easier said than done, considering that Pokémon GO has region-specific characters that you may never get a chance to see. Sure, you can spoof your GPS location to make the augmented reality game think you're at a different spot on the map, but Niantic Labs seems to be catching on to this method, and some users have been soft-banned for a few hours after trying it.

Your iPhone's Photos app just got a major new feature that lets you edit multiple photos and videos simultaneously. That means you no longer have to try and remember all the adjustments made in one image or video to try and get the same look in another photo or video.

Router gateways are responsible for protecting every aspect of a network's configuration. With unfettered access to these privileged configurations, an attacker on a compromised Wi-Fi network can perform a wide variety of advanced attacks.

The tactic of brute-forcing a login, i.e., trying many passwords very quickly until the correct one is discovered, can be easy for services like SSH or Telnet. For something like a website login page, we must identify different elements of the page first. Thanks to a Python tool for brute-forcing websites called Hatch, this process has been simplified to the point that even a beginner can try it.

Its official: On May 8, T-Mobile finally released the Android Oreo update for the LG V30 and V30+. Now, every major US wireless carrier has pushed the update. For me, this update is a big deal. Not only does Android Oreo bring some new tools and features, but LG has also included a few additions as well.

Beginners learning brute-forcing attacks against WPA handshakes are often let down by the limitations of default wordlists like RockYou based on stolen passwords. The science of brute-forcing goes beyond using these default lists, allowing us to be more efficient by making customized wordlists. Using the Mentalist, we can generate millions of likely passwords based on details about the target.

The mysterious technology product teased via an eccentric TED Talk nearly five years ago has finally been revealed, and it's called the Magic Leap One: Creator Edition. After all of the non-disclosure agreements, furtive comments from CEOs and insiders given early access to the device, and a seemingly never-ending string of hints dropped by the company's CEO, Rony Abovitz, on Twitter, we finally have a real look at the product.

Word games can expand your vocabulary skills in all sorts of exciting and creative ways. Because of this, both the iOS App Store and the Google Play Store are awash with word games, making it hard to differentiate between good and bad titles. This is especially troublesome if you're looking to purchase a game, as everyone hates to waste hard-earned cash.

Kali Linux is the obvious first choice of an operating system for most new hackers, coming bundled with a curated collection of tools organized into easy-to-navigate menus and a live boot option that is very newbie-friendly. But Kali isn't the only distribution targeted at pentesters, and many exciting alternatives may better fit your use-case. We've already covered BlackArch Linux, now it's time to talk about Parrot Security OS.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

There's a tool on your iPhone that can help you with your overall emotional well-being, one that can help you be more aware of your emotions throughout the day and build resilience against the stressors in your life.

The tech world was taken by surprise this week with the unexpected unveiling of Snap's augmented reality Spectacles smartglasses.

Samsung's stock Galaxy Themes system leaves much to be desired with its restrictive and expensive theme packs. Back in the day, the gold standard for Android theming was CyanogenMod Theme Engine. And while it no longer exists, a successor has emerged to fill the void.

Using a strong password is critical to the security of your online accounts. However, according to Dashlane, US users hold an average of 130 different accounts. Memorizing strong passwords for that many accounts is impractical. Fortunately, password managers solve the problem.

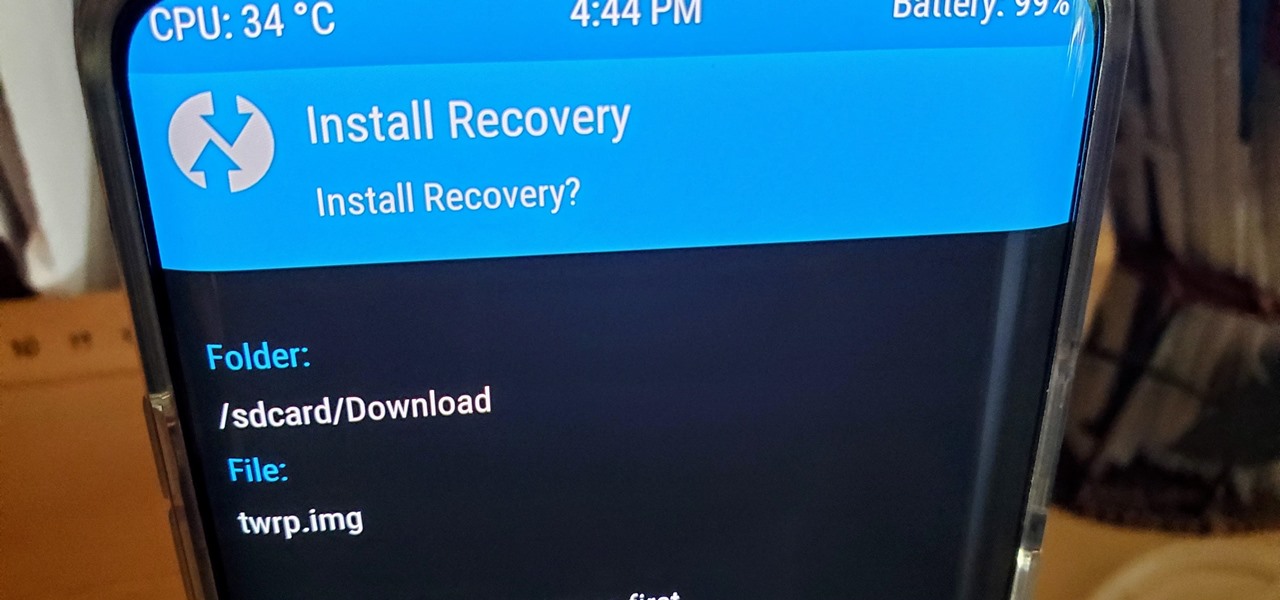
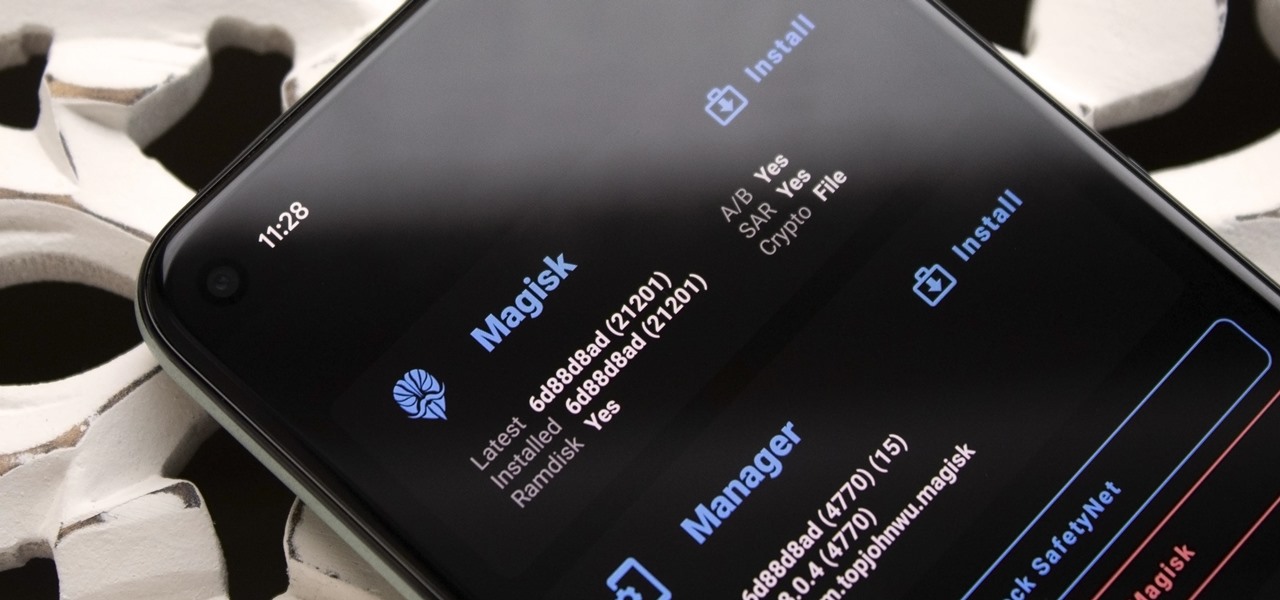
When it comes to modding your Android device, you'll want to be familiar with the TWRP name and what it stands for. It's a tool that you'll be using to make NANDroid backups or to install just about any mod file you can think of — the number of uses is quite awesome. You'll mostly be after Magisk for root access and potentially a custom kernel as well.

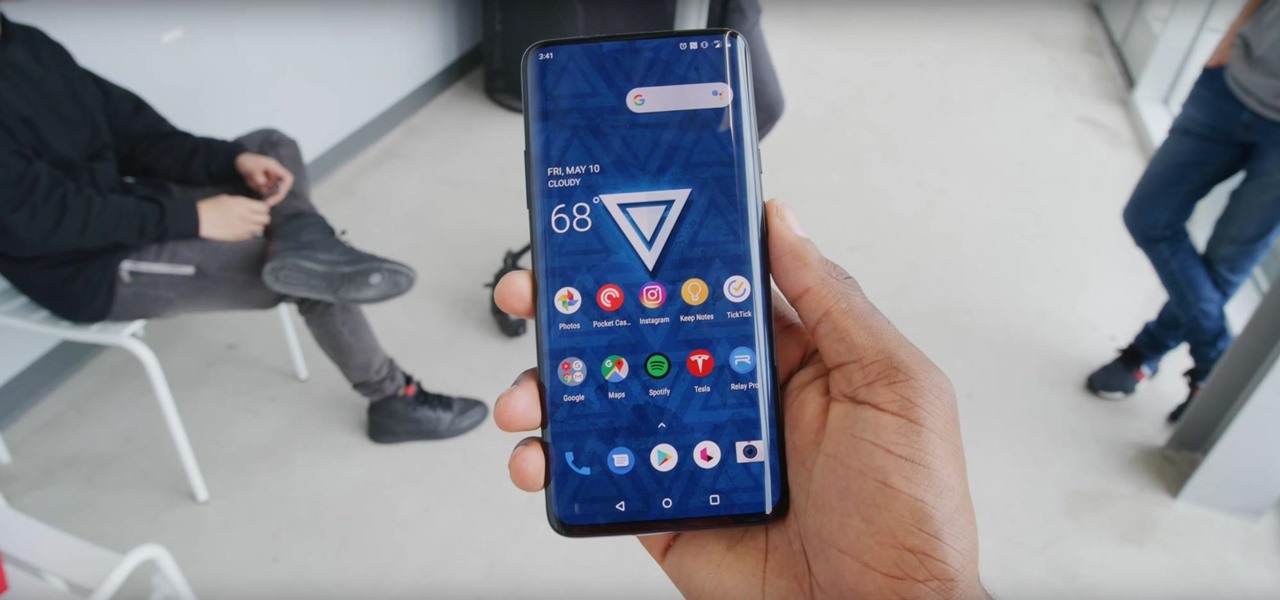
The OnePlus 7 Pro is definitely a beast on paper. With a specs page that ticks virtually every box and a price point that undercuts the competition by hundreds of dollars, it's hard to overlook this phone. But before you get too excited, know that OnePlus has repeatedly shown to be misleading with their official specs.

There have been concerns with how much personal information Google tracks and all the things they know about us. Of course, that's what makes Google services so useful, they can use that information to cater to each of us individually. So yes, it serves a purpose, but it's not great for personal data security.

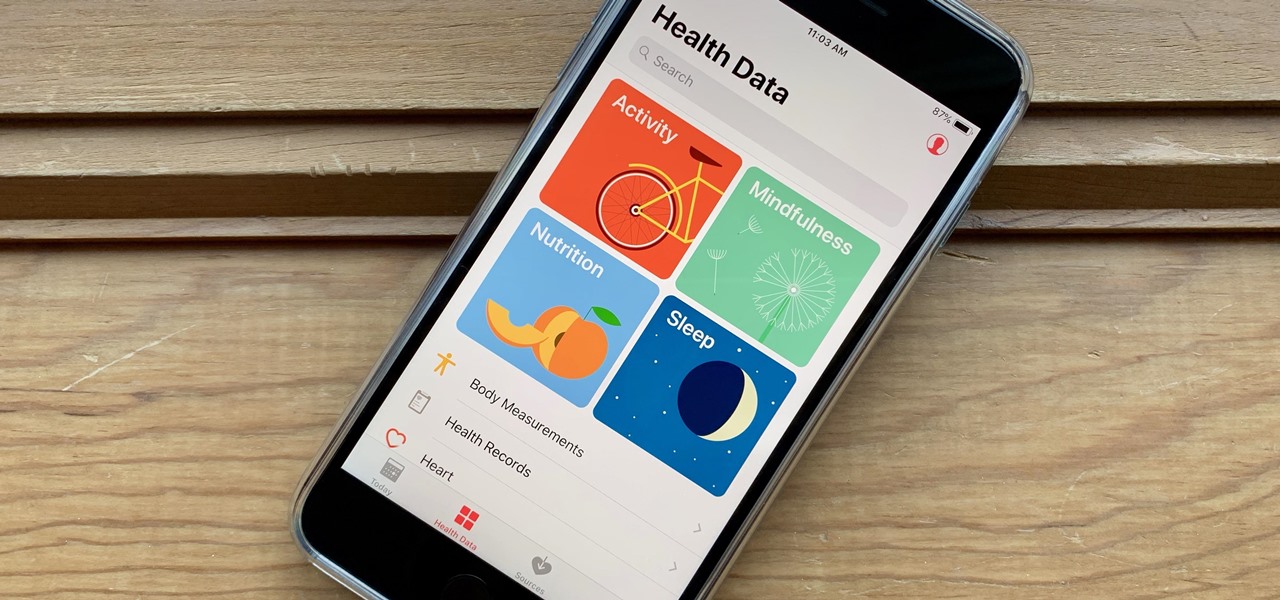
It's not easy staying fit and healthy these days with addicting phones, oversized portions, and long workdays, to name just a few things. To succeed, it takes work, commitment, and an understanding of your mind and body — and your iPhone can help you with some of that. While Apple pushed its Screen Time tool to help curb unhealthy smartphone habits, its "Health" app can help with everything else.

You can mod every aspect of your phone's software with root, but if you want to make changes at the hardware level, you'll need a custom kernel. If you've looked into custom kernels before, one name undoubtedly kept coming up: ElementalX. It's easily the best custom kernel out there, and the reason for that is its awesome developer, flar2, aka Aaron Segaert.

Smartphones and laptops are constantly sending Wi-Fi radio signals, and many of these signals can be used to track us. In this guide, we'll program a cheap IoT device in Arduino to create hundreds of fake networks with common names; This will cause nearby devices to reveal their real trackable MAC address, and it can even let an attacker take over the phone's data connection with no warning.

The calendar app is one of the unsung heroes found within your iPhone. It's the ultimate personal assistant that you've come to rely on to keep track of your schedule and ensure you never miss a class or meeting, all while reminding you of upcoming birthdays and deadlines to help maintain good relationships with loved ones and colleagues.

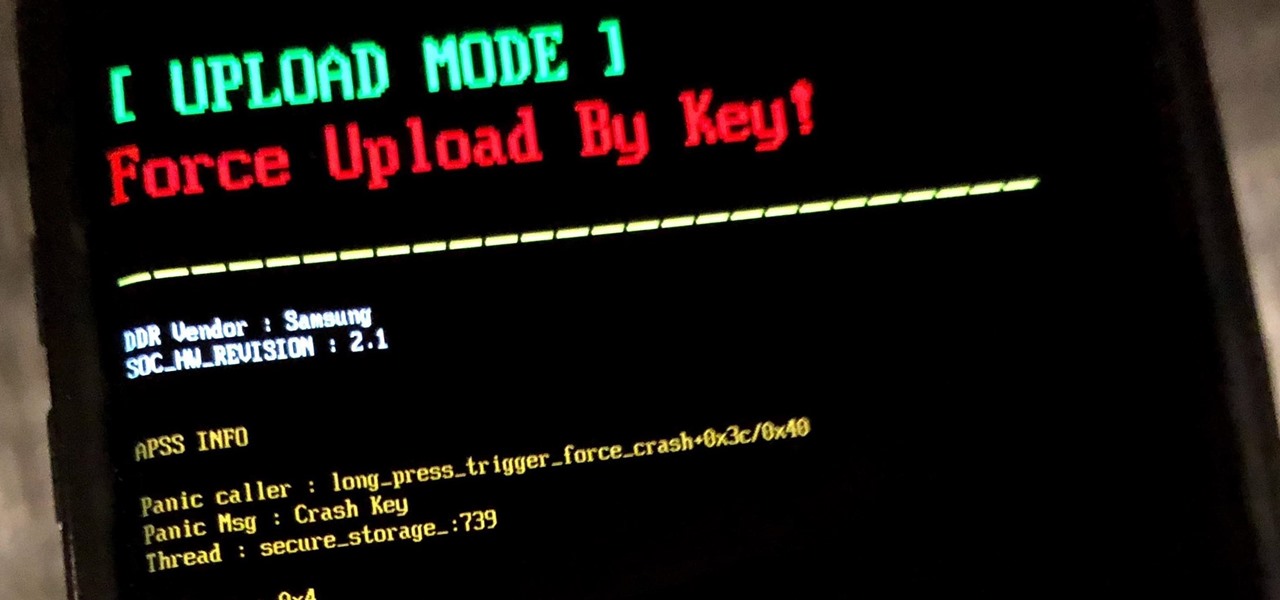
If you own a Samsung phone and enjoy rooting or modding your device, flashing official firmware can be very useful. Odin is Samsung's own internal program for loading such updates for testing purposes, and it's quite easy to use for your own custom modification needs.

So, your grandmother finally wants to ditch her flip phone for a shiny new smartphone? Congratulations. But helping her get used to her new device, even when it's an iPhone, is no small task. Grandma mastered checking her email in late-2012 and just recently learned there's a thing called "Facebook." But we love grandma, and thanks to this guide, we can definitely make this happen for her.

One of the best things about Android is the ability to customize your phone to your liking. From changing the layout of icons to finding the perfect wallpaper to reflect your current mood, there's a wide range of tools to make your phone yours.

It always looks different when it's not about you. The Internet is our world's Alterego. Those many bits don't really make sense unless we want them to be valuable, to mean something.

The emergence of Facebook's collaboration with Ray-Ban to launch Stories smartglasses has finally put an exclamation point on a new category of smartglasses: the pre-augmented reality wearable segment.

The race for the future of AR wearables gained steam this week with several pivotal developments. First, Apple, the subject of numerous reports and rumors regarding its purported AR headset, is reportedly eyeing an in-person unveiling of the device for later this year, rather than introduce it at its upcoming virtual Worldwide Developers Conference, which would usually be as good a time as any to make a big AR hardware announcement.

Snapchat may trail Facebook and Instagram in terms of daily active users, but a new partnership with Samsung may get those innovative AR Lenses onto the mobile devices of a lot more users.

Microcontrollers like ESP8266-based boards have built-in Wi-Fi, and that's really cool, but what's even cooler is that certain pro models of the D1 Mini also have a port where you can connect a directional antenna. This can give you exceptional range, but if you were to just plug one in after opening the package, it most likely wouldn't work.

Okay, so you rooted your Android phone .... now what? There are a few ducks you need to get into a row, like backing up your stock boot image, getting SafetyNet sorted, and improving security with biometrics. But there are also awesome root mods waiting for you — just don't get ahead of yourself.

If you have ever wanted to mod your Android device, your new best friend is easily going to be Team Win's TWRP custom recovery. This gives you access to file flashing on the fly, which can include such things as Magisk for root access, or even a custom ROM to replace the stock firmware that came with the device.

Once you've installed Ubuntu with security in mind and reduced the possibility of network attacks on your system, you can start thinking about security on an application level. If a malicious file is opened on your system, will an attacker be able to access every file on the computer? The chances are much slimmer if you put the proper defenses in place.

Windows 10 and macOS have poor reputations when it comes to customer privacy and user policies. Our hacking Windows 10 and hacking macOS articles might make it seem like a reasonably secure operating system doesn't exist. But I'm here to tell you that there is a viable alternative that could provide some sense of security and trust.

Even though most phones don't have Oreo yet, Google has released Android 9.0 Pie. It's available on Google's own Pixel devices, and updates should soon be available to partnered devices from Essential, Nokia, Oppo, Sony, Vivo, and Xiaomi. We're already digging into it to highlight all of the features and changes.

Android comprises an entire ecosystem of apps, games, functions, and features, so it would only make sense that it has its own lexicon. Words, phrases, and acronyms that didn't exist ten years ago are now used in an off-the-cuff style by developers and support technicians across the web.