Heartbleed, move over. There's a new bug in town, and this time it's also affecting Mac and Linux computers. It's called Shellshock (its original official title is CVE-2014-6271), and it's currently got a 10 out of 10 severity rating over at the National Cyber Awareness System. While some updates have been issued to fix this bug, they were incomplete, and your system is probably still vulnerable, as it has been for the last probably 20 years.

Canvas fingerprinting is the web's trickiest privacy threat, but it's not impossible to stop. With all the media attention it's gotten lately, it's time we lay out exactly how to detect and prevent this invasive tracking technique.

Brining is magic. All you have to do is make a mild saline solution, toss in your protein of choice, let it soak, and cook. You end up with incredibly tender, flavorful meat or tofu for very little effort. So why aren't more of us doing it?

Not that long ago I wrote an article discussing what it would be like, realistically, if you were to accidentally travel back in time to the Victorian era. At the end of that article, I mentioned that the best thing you could bring with you on a time-traveling adventure is a Kindle, or similar e-reader, stuffed full of the knowledge of the 21st century. Why a Kindle? Well, I own a Kindle, and I love it. However, there's far more to it than that.
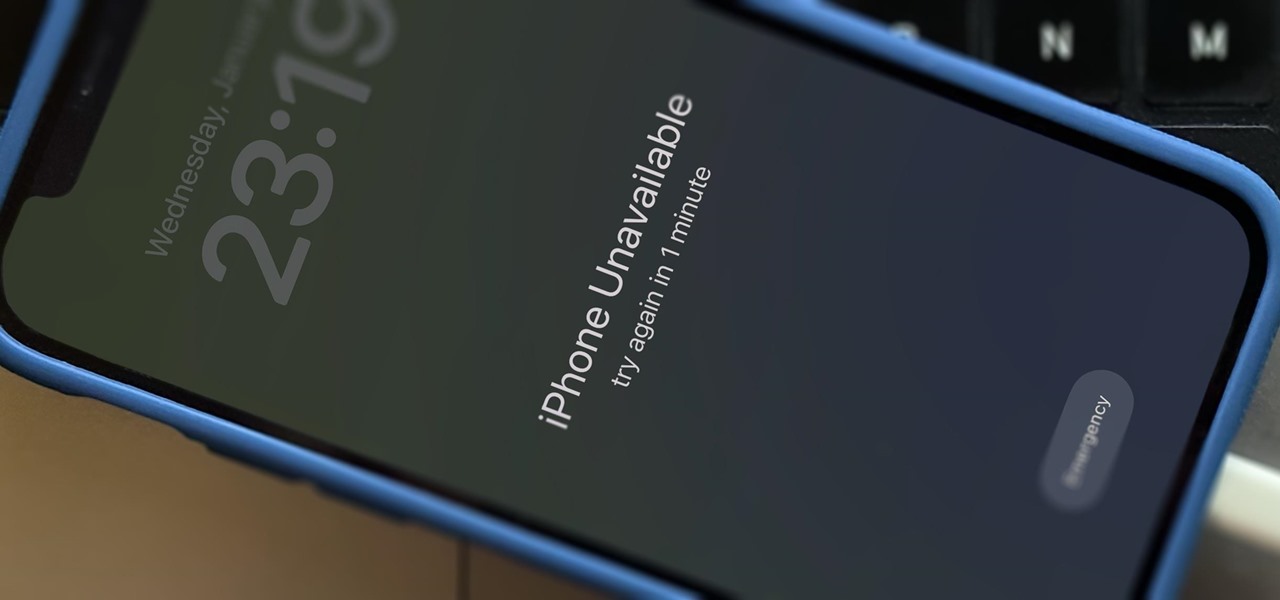
There's only one thing keeping hackers, thieves, law enforcement agencies, and maybe even the people you thought you could trust from breaking into your iPhone should they ever get possession of the device. Their odds of bypassing that thing are pretty good, but there's an easy way to make it an almost impossible feat.

Phones these days are expensive. The iPhone 11 Pro is presumed to start at $999, following the iPhone XS and iPhone X's leads. One way to bring down that cost is to trade in your old iPhone, but there isn't one clear-cut way to do that. You could trade your iPhone into a participating website or put yourself out there and sell the iPhone on your own. It's all about what's best for you.

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.

Russian cyber disinformation campaigns have many missions, but one of particular interest is using technology to monitor, influence, and disrupt online communications surrounding culturally sensitive topics or protests. The ability to watch these events, and even filter positive or negative tweets to amplify, gives rise to the ability to execute a number of disinformation campaigns.

Google Calendar is a cornerstone of the Google Suite, perhaps second only to Gmail itself. Whereas email is constantly plagued by phishing attacks, as of yet, the calendar is a relatively untapped social engineering attack vector. But it's relatively easy for an attacker to inject a meeting or event into a target's Google Calendar and use it to exploit them.

Beginners learning brute-forcing attacks against WPA handshakes are often let down by the limitations of default wordlists like RockYou based on stolen passwords. The science of brute-forcing goes beyond using these default lists, allowing us to be more efficient by making customized wordlists. Using the Mentalist, we can generate millions of likely passwords based on details about the target.

PowerShell Empire is a post-exploitation framework for computers and servers running Microsoft Windows, Windows Server operating systems, or both. In these tutorials, we will be exploring everything from how to install Powershell Empire to how to snoop around a target's computer without the antivirus software knowing about it. If we are lucky, we might even be able to obtain domain administrator credentials and own the whole network.

Thrift stores! As a Steampunk, they can be your best friend, but it's easy to make a tragic mistake. This hands-on guide will help you navigate the murky waters of successful thrifting in order to find the hidden gems that will make your Steampunk outfit complete!

When you think about it, isn't life just one big open-world RPG just begging to be conquered? We all have a set number of specific tasks or chores we must complete every single day like clockwork. Sometimes, these items on our to-do list can become tedious and cause us to lose motivation. What if you could take those tasks and turn them into something awesome instead? Now you can.

On the surface, AppleCare+ seems like an expensive and gimmicky option to tack onto your already pricey iPhone 11, 11 Pro, or 11 Pro Max. Upon further inspection, however, you'll see that its seemingly expensive price tag is chump change compared to the fees you'll have to pay if you end up having to repair your premium device outside its one-year warranty.

Update: The new Galaxy phones are now official! Check out all the details on the Galaxy S10 and S10+ or the Galaxy S10e.

Clumsiness is the great equalizer when it comes to smartphones — it makes no distinction between the most expensive flagship handset and cheaper mid-range models. A hard drop onto pavement will usually result in a shattered screen, regardless of how pricey your device is. And with a smartphone breaking every two seconds, we're truly our own handset's ultimate nemesis.

On July 20, 1969, humans set foot on the moon for the first time. But some say our microbes beat us there. With the Space Age came new questions about microscopic invaders from outer space and concern about where we are leaving our microbial footprints. The questions are even more relevant today.

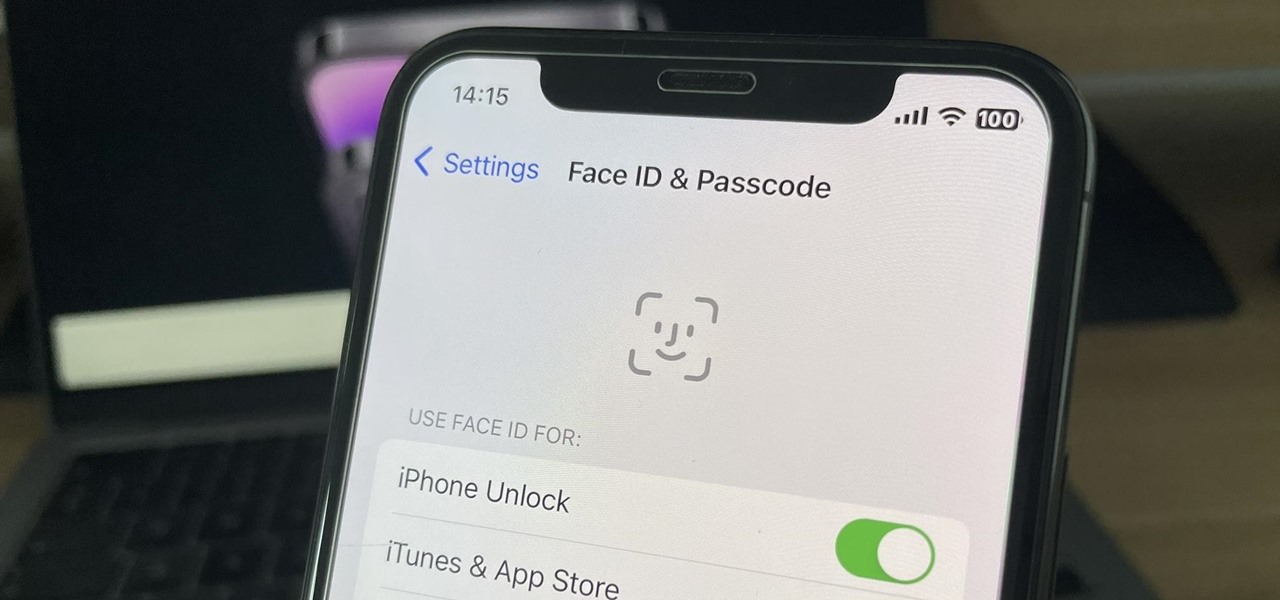
The iPhone 13 and iPhone 14 series models have a new feature on iOS 16 that lets you use Face ID when your iPhone is in landscape orientation. This is most helpful when trying to make purchases in apps and games where you use your iPhone rotated on its side. If you're having issues using Face ID in landscape mode, there may be some easy solutions to getting it working.

Apple's Always-On display feature for the iPhone 14 Pro and 14 Pro Max can show important information on the screen even when the device is sleeping. While the dimmed Lock Screen may seem like a WYSIWYG component, there are actually a few ways you can customize it to fit your needs better.

One of the most promising avenues of attack in a web application is the file upload. With results ranging from XSS to full-blown code execution, file uploads are an attractive target for hackers. There are usually restrictions in place that can make it challenging to execute an attack, but there are various techniques a hacker could use to beat file upload restrictions to get a shell.

You can feel it in your bones. You may die if you don't get this phone. There's just one problem — the price. Suddenly, you come across what seems like manna from heaven. That very device, at a deeply discounted rate, can be yours.

Last year, your iPhone's Weather app received some great features, but things are even better now with the latest iOS 17 version.

Hackers often find fascinating files in the most ordinary of places, one of those being FTP servers. Sometimes, luck will prevail, and anonymous logins will be enabled, meaning anyone can just log in. But more often than not, a valid username and password will be required. But there are several methods to brute-force FTP credentials and gain server access.

The new iOS 14 for iPhone arrived Wednesday, Sept. 15, 2020, alongside iPadOS 14, and there are a lot of features to uncover. Improved widgets. Better home screen customization. Exciting Messages improvements. New abilities in Camera and Photos. There's so much here that it'll take months for you to learn everything by heart.

In this lesson we will learn how to solve probability problems involving a spinner. A probability measures the likelihood of a certain event. It always ranges between 0 and 1. The following formula can be used to find the probability of a particular event:

In this math lesson we will learn how to solve simple probability problems with a number cube. The probability of an event measures the likelihood that the event will occur.

New Year's Eve. It will be one hell of a chaotic night. Trust me. The overcrowded streets. Long lines for the urinal. Maxing out your credit card on that shot of Cuervo. You'll be lucky to make it out alive.

If you're a skiier, you already know the dangers of avalanches during your playtime. Watch this video to learn how to ski safely and properly. With these tips, you can minimize the likelihood of avalanches and danger. Watch this how-to video, and you'll be able to ski safely in deep powder without fear. Ski safely in deep powder to avoid avalanches.

This video demonstrates how to do a Russian join. Great for yarns that won't felt, or won't look good felted. This join reduces the likelihood of ends popping out of the work, especially if you break the yarn instead of cut it, and don't split the plies. Can also be done more simply as a single color join by just threading old strand into the new strand. Do a Russian join.

Following the first part in this series on advanced cracking techniques, we are going to go over how we can intelligently crack passwords using the old-fashioned bruteforce method. These unique cracking techniques aren't widely used, because most crackers are Script Kiddies who have no idea what the concepts are behind cracking passwords, thus, word won't get around too quickly.

Well, Ol' Man Winter is upon us yet again, blasting us with his icy breath. When I was a kid, I loved wintertime because it meant the prospect of sledding, snowball fights & missed school days in which to enjoy both. Now that I'm 45, however, my attitude toward the season has taken a complete 180-degree turn: I find myself dreading it because of the likelihood of being snowed-in for days on end, and the certainty of being forced to endure the frigid temperatures.

Summertime is officially here, which means that the likelihood of someone leaving a glass of cold water on your wooden furniture without a coaster and leaving behind an annoying water ring mark on the surface has increased tenfold. What can you do to get rid of that annoying mark?

Have you already abandoned your New Year's resolutions? Maybe you need a refresher on how to stick to your goals and avoid succumbing to your worst temptations and unproductive habits. No matter where you are in life right now, all of us can benefit from increasing our sense of willpower.

Earlier today, @DesignGears leaked an unofficial KitKat build for the Galaxy Note 3, and now they've dropped one for our Galaxy S4s, too. How to Install the 4.4.2 Build

Lying is awesome. From a very young age, children learn that flat out denying the truth gets you out of trouble and helps keep you calm in the face of horror. But what happens when you just have to know if someone, say, used your toothbrush? You could ask them to take an expensive and arduous polygraph test.

Jet engines combine oxygen from the surrounding air with on-board fuel to burn at very high temperatures and create thrust in the direction of the flame. Rockets, which we will learn about in a later post, are similar but carry oxygen internally and can therefore function in space!

Different genres of social media have changed the world, but they are not omnipotent. In most cases this is a good thing, but not in the case of Operation Rainfall. It has been a purely well meaning social media movement that should have led to a great boon for the North American gamer public, but instead has served as a reminder of how stone aged Nintendo of America's (NOA) corporate thinking remains.

In the first part we differentiated the two types of control, mental and physical. In part 2 we will dig deeper into Physical crowd control and analyze examples that are present today.

This is Part II in the Lockdown: The InfoSecurity Guide To Securing Your Computer series. Before beginning, check out Part I. This article will cover using alternate software to increase your security and will provide you with some information about websites and programs that test a computer's security. It will also guide you to software you can install or follow so you know what programs need to be updated on the computer. Lastly, I will talk about some features that should be disabled when ...

BioShock is one of the best games of all time. It combines FPS gameplay with RPG storytelling and supports multiple systems better than any other game, that much is for sure. And the setting of its amazing story is a place called Rapture, a high-tech libertarian colony at the bottom of the Atlantic built by Andrew Ryan, a greying industrialist clearly inspired by John Galt and his creator Ayn Rand, the mother of Objectivism and modern American libertarianism in general. Ryan is a Soviet exile...