Hackers and makers are often grouped under the same label. While hackers draw on computer science skills to write programs and find bugs, makers use electrical engineering to create hardware prototypes from microprocessor boards like the Arduino. We'll exercise both sets of skills to program a $6 NodeMCU to display the status of a Wi-Fi link via an LED, allowing us to monitor for jamming attacks.

Think back to when you last wanted to transfer some music or videos to your friend's smartphone and how difficult and slow it was. As powerful as our phones are, the default file sharing options are limited. There are, fortunately, some better options which make moving files easy, secure, and painless.

The calendar app is one of the unsung heroes found within your iPhone. It's the ultimate personal assistant that you've come to rely on to keep track of your schedule and ensure you never miss a class or meeting, all while reminding you of upcoming birthdays and deadlines to help maintain good relationships with loved ones and colleagues.

If you need to hack an Android device, try a remote administration tool. Known more familiarly as a RAT, there are open-source RATs that are barebones and exorbitantly priced RATs that are more polished. There are also low-cost and polished RATs that aren't intended to be RATs at all, such as Cerberus, an anti-theft solution available right on Google Play.

Russian cyber disinformation campaigns have many missions, but one of particular interest is using technology to monitor, influence, and disrupt online communications surrounding culturally sensitive topics or protests. The ability to watch these events, and even filter positive or negative tweets to amplify, gives rise to the ability to execute a number of disinformation campaigns.

There's always an iPhone in our list of top phones for privacy and security, due in large part to advanced security measures like Face ID, consistent iOS updates, and easy ways to prevent unwanted access and excessive data sharing. However, some of those options actually do the opposite and hinder security. It all depends on how you use your iPhone, but you should at least know everything available.

Kali Linux is established as the go-to operating system for penetration testing, but in its default configuration, it's less than ideal for regular desktop use. While in many scenarios, a live boot or virtual environment can resolve these issues, in some situations, a full installation is better. A few simple changes can be made to a Kali Linux desktop to make it safer to use in this environment.

A burner number isn't just for criminals and cheating spouses. In this digital world, with many of our interactions being conducted online, a throwaway phone number acts as a buffer — it lets you enjoy the web without having to give out your personal information, such as real name or phone number.

The iOS App Store is a big place, offering over two million applications in total. However, there are actually some apps you can and should install on your iPhone that the iOS App Store doesn't include. And no, these apps do not require any difficult jailbreaking or complicated sideloading techniques — they are really simple to install.

The most significant customization aspect of the iPhone is most definitely the home screen. Before iOS 14, Apple only threw in a feature here and there to appease those who like a more personal touch on the most visible part of the operating system. Now, there are great customizability options to give you a real personalized touch, and that includes app icons.

Beginners learning brute-forcing attacks against WPA handshakes are often let down by the limitations of default wordlists like RockYou based on stolen passwords. The science of brute-forcing goes beyond using these default lists, allowing us to be more efficient by making customized wordlists. Using the Mentalist, we can generate millions of likely passwords based on details about the target.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

In just a few months, Binance has experienced explosive growth, overtaking its rivals to rank among the top three cryptocurrency exchanges in the world by trading volume. Without a doubt, Binance is now among the best sites for trading alt-coins like Ripple (XRP), Stellar (XLM), and NEM (XEM) to name a few.

There's no doubt Kali has established itself as the most popular penetration distribution available. However, just because it's the fan favorite of beginners and security researchers doesn't make it right for everyone. Manjaro Linux is a beginner-friendly Arch-based distribution which can be easily weaponized with the Black Arch expansion, creating a friendlier first-time Arch experience.

Coinbase is the primary go-to for many users when it comes to investing in Bitcoin (BTC), Ethereum (ETH), Litecoin (LTC), Ripple (XRP), and more, due to its user-friendly interface. But before you join them, know that the ease of use comes with a price. Coinbase charges fees for each transaction, and your bank might even add charges on top of that. Plus, there is some fine print to be aware of.

The headphone jack is becoming outdated technology in smartphones — that's what many manufacturers would have you believe. For the convenience of the audiophiles out there, we recently published our list of all phones that have removed the 3.5 mm jack. But what did each company gain inside their flagship phones by removing this supposedly antiquated port?

Every time you make a call or send a text, you're giving the recipient your phone number. This can be quite the security vulnerability, opening yourself up to scammers, spammers, and the feds. In this how-to, we'll look at what a burner phone is, why you might want one, and how to get started using a free second phone number on your regular smartphone.

Aircraft equipped with ADS-B are constantly shouting their location into the radio void, along with other useful unauthenticated and unencrypted data. In this guide, we will make an ADS-B receiver using a Raspberry Pi with a software-defined radio (SDR) dongle, which we can use to track aircraft anywhere in real time.

So you finally decided to make the switch from iOS to Android, huh? Well first off: welcome to the world of tomorrow. And secondly: good call, mate.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Apple just announced the iPhone 6, and no matter whether you've been with Android for a few months or few years, there's a good chance you're enticed by the idea of switching over to the other side.

My first encounter with a phablet was late last year with the AT&T version of the Samsung Galaxy Note 2, having never touched or even seen its highly-acclaimed and pioneering predecessor. Initially, I was a bit overwhelmed by the enormous screen and taken aback by the dated stylus, which brought up ugly memories of my dad using his ten pound PalmPilot.

If you've recently built a Wi-Fi spy camera out of an ESP32-CAM, you can use it for a variety of things. A baby monitor at night, a security camera for catching package thieves, a hidden video streamer to catch someone going somewhere they shouldn't be — you could use it for pretty much anything. Best of all, this inexpensive camera module can perform facial detection and facial recognition!

Your voice is the key to unlocking many features on your iPhone. For example, you can ask Siri to send a text message to a friend, add items to a list, run a custom shortcut, or turn on your lights, but Apple does not allow you to unlock your iPhone with a Siri voice command. Instead, you can turn to a lesser-known feature to unlock your iPhone without Face ID, Touch ID, or typing your passcode.

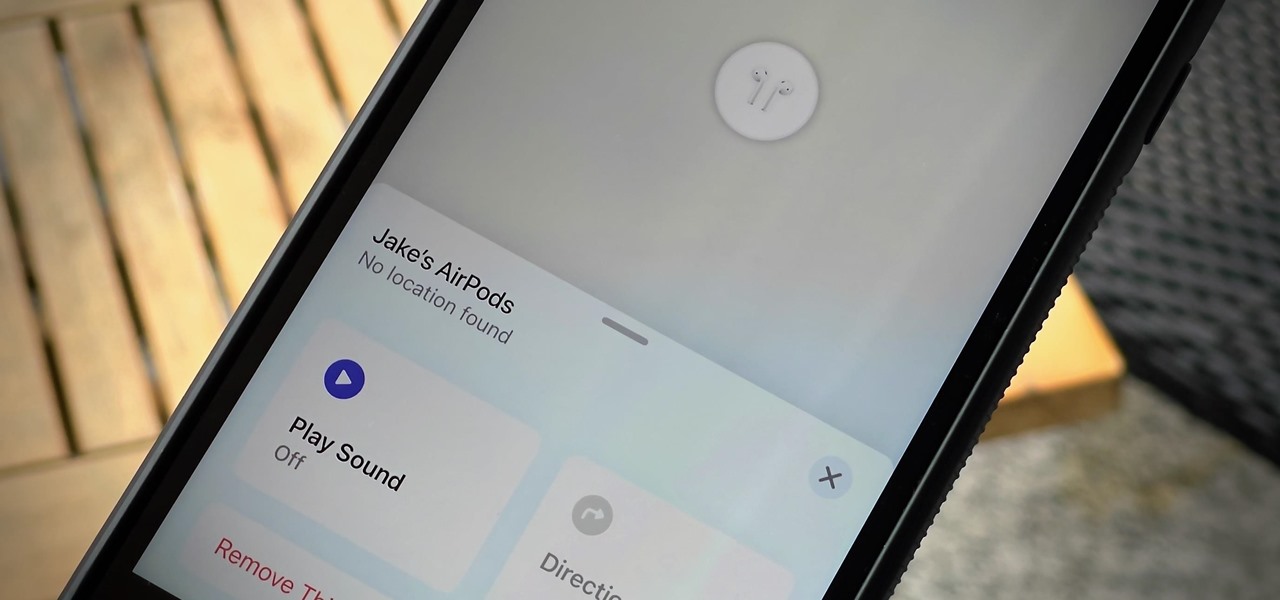
If you lose your AirPods, AirPods Pro, or AirPods Max, you can turn to Find My to locate them. But sometimes, things don't go according to plan, and many things can go wrong. For example:

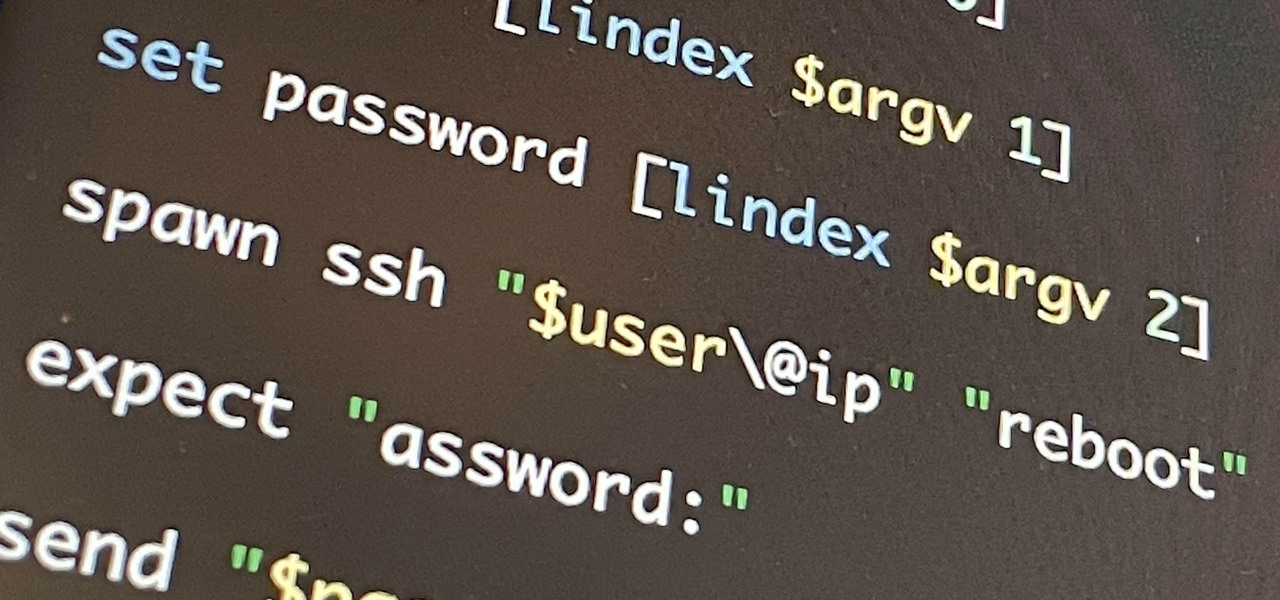
If you're getting into automation, Bash scripting is usually the way to go. However, there are a couple of limitations, and one of them is logging into another device like a Raspberry Pi and running a script automatically. To help in those situations, we're going to automate delivering an SSH payload with an "expect" script.

We often discuss the augmented reality efforts coming from the biggest players in Silicon Valley like Google, Facebook, Apple, and others, but one name that keeps coming up when you really begin to dig into the AR space is Vuzix. Since the late '90s, the company has quietly but deliberately worked to build itself into a viable competitor in the enterprise space via its wearable display technology.

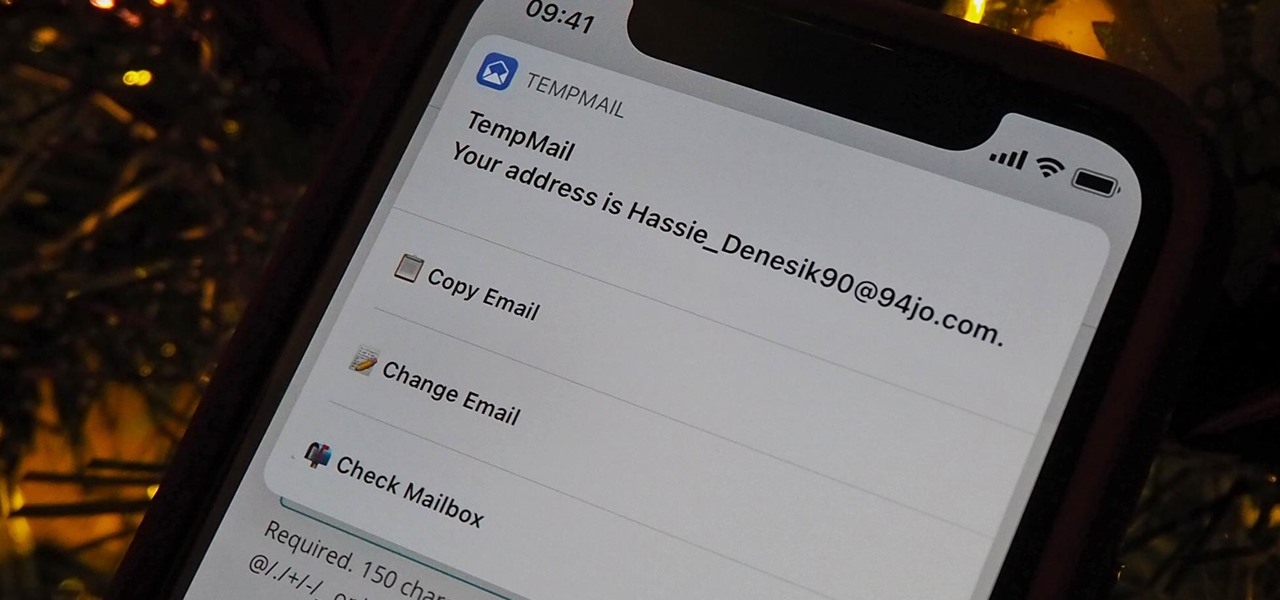
A temporary email can go a long way. Using your actual email to sign up for a mailing list to receive 10% off a purchase doesn't make sense if you don't use the website much. It means you'll have to deal with spam emails from then on, which is why an anonymous email is perfect not to have to deal with all that trouble. And that's where the TempMail shortcut for your iPhone comes in handy.

There's a lot of talk these days about how the iPhone 12, 12 mini, 12 Pro, and 12 Pro Max can shoot Hollywood-quality video with HDR and Dolby Vision. The video processing is really cool when it works, but as of right now, you might find its limitations outweigh its use to you. If that's the case, there's a way to turn it off.

The moment arrives when you finally pop a shell on the web server you've been working on, only you find yourself in a strange environment with limited functionality. Restricted shells are often used as an additional line of defense and can be frustrating for an attacker to stumble upon. But with enough patience and persistence, it is possible to escape these restricted environments.

If there's an iOS app you want to hide from your iPhone's home screen, there are a few built-in ways to do so in iOS 14, but there is a clever workaround you can use in older iOS versions. Plus, it also works in iOS 14 as a way to disguise app icons instead of just hiding them, so no app is what it seems.

One of the most exciting things as an ethical hacker, in my opinion, is catching a reverse shell. But often, these shells are limited, lacking the full power and functionality of a proper terminal. Certain things don't work in these environments, and they can be troublesome to work with. Luckily, with a few commands, we can upgrade to a fully interactive shell with all the bells and whistles.

Unlike the realm of virtual reality, augmented reality is less about losing yourself in some fantasy environment, and more about getting things done in the real world. So while we've seen some great games that capture the imagination on devices like the Magic Leap One and the HoloLens, when it comes to real-world usage, the biggest developments coming for AR apps that are the more practical ones.

For many, phones are starting to replace televisions as the primary device for watching videos. Thanks to their portability and easy to use apps, it's often simpler to watch Netflix, Hulu, YouTube, or Prime Instant Video on the smaller screen. But not every phone is suited to fit this need, so we did some testing to find the best of the best when it comes to streaming videos.

If you have ever wanted to mod your Android device, your new best friend is easily going to be Team Win's TWRP custom recovery. This gives you access to file flashing on the fly, which can include such things as Magisk for root access, or even a custom ROM to replace the stock firmware that came with the device.

You probably know of Apple's Text Replacement feature for iOS, iPadOS, and macOS, but you're probably not using it as much as you should. With it, you can create your own keyboard triggers for almost anything you can think of, whether it's an email address or an entire email. There are endless reasons to create custom text replacements — and we'll show you why.

There's a hidden feature on iOS that will turn your iPhone or Apple Watch into a remote control for your nearby iPad or other Apple devices — and it's nowhere near as complicated as Switch Control.

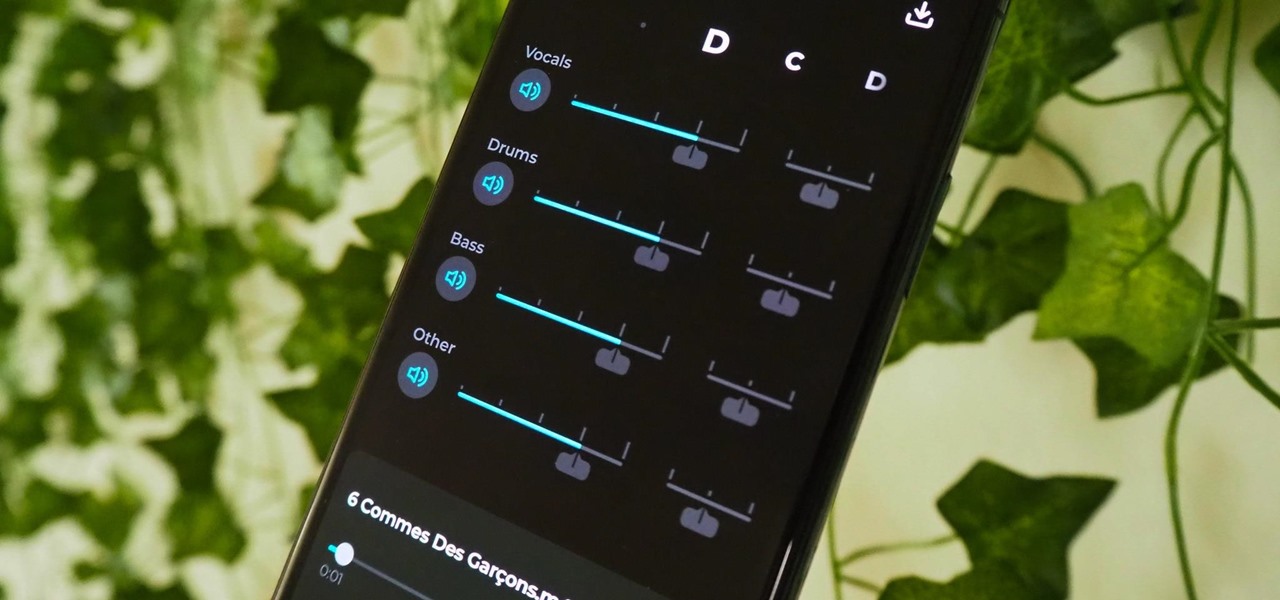
Finding an instrumental or karaoke version of a song can be pretty easy unless you're dealing with a song that isn't popular. That leaves you with just the full version of the song, complete with vocals. So how do you convert it into an instrumental or karaoke track?

Adobe Audition, Audacity, and other audio editing software have tools to isolate vocals and instruments in regular songs so that you can get an instrumental track for karaoke, vocals for an a capella version, or solo drums, bass, keys, etc. that you can use to learn the song yourself. The software is mostly for desktop computers, and it doesn't always do a good job, but that's where Moises comes in.

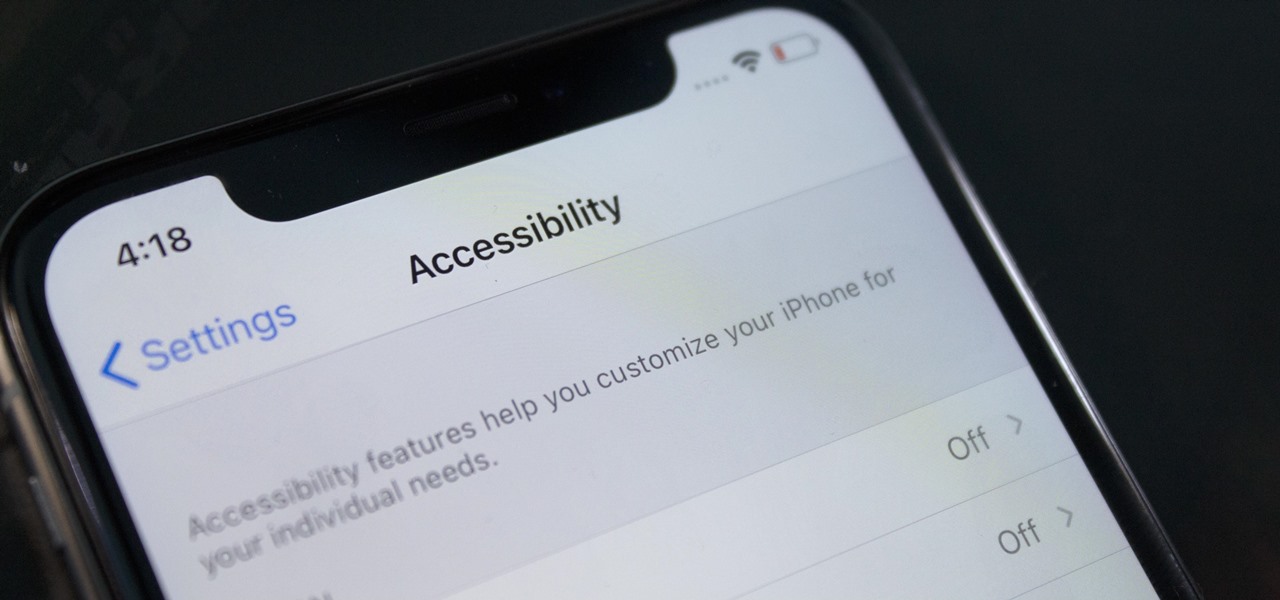
According to the CDC, one in four U.S. adults has a disability, where limitations can involve vision, cognitive function, hearing, motor skills, and more. That's why the iPhone has accessibility features; so that everyone can use an iPhone, not just those without any impairments. Apple's iOS 14 has only made the iPhone even more accessible, and the new tools benefit everyone, not just those that need them.