Please read the following in Rod Serling's voice. Picture, if you will, a mother. She comes home after a long day at the office, relieved that she took some chicken breasts out to thaw and will be able to make a quick and easy dinner for her family. She opens her refrigerator to get the chicken, but to her horror she does not see it… she forgot to take the chicken out of the freezer after all. What will she make for dinner now? How will she feed her family? She has entered…the Panic Zone.

Welcome back, my greenhorn hackers! Throughout this series on Metasploit, and in most of my hacking tutorials here on Null Byte that use Metasploit (there are many; type "metasploit" into the search bar and you will find dozens), I have focused primarily on just two types of modules: exploits and payloads. Remember, Metasploit has six types of modules:

As the days get shorter and the weather cools down, I prepare to "hibernate." I add piles of blankets to my bed, wrap myself in layers of flannel, and—most importantly—eat as if I'm storing energy for winter.

Dumplings have been around for centuries in various forms; spätzle, as well as chicken and dumplings, are dough-y dumplings with no filling, whereas Russian pierogis and Chinese jiaozi are dumplings that contain meat, vegetables, or both.

Welcome back, my tenderfoot hackers! Recently, Microsoft released a new patch (September 8, 2015) to close another vulnerability in their Windows Vista, 7, 8, and 8.1 operating systems. The vulnerability in question (MS15-100) enabled an attacker to gain remote access to any of these systems using a well-crafted Media Center link (MCL) file.

In my opinion, there is no candy greater or more timeless than Sour Patch Kids. They're the ultimate treat: sweet and refreshing, yet sour and tangy. These contrasting flavors are what make Sour Patch Kids perfect for the people of all ages—especially your kids. So let's make dishes that incorporate this awesome candy into your cooking rotation!

Sushi rolls, known as makizushi in Japanese, are only limited by your imagination—and your ability to roll them neatly, of course. While it may seem like a lot of effort, rolling sushi is a snap if you have the right tools.

Welcome back, rookie hackers! We recently began an exploration of ways to hack using the Bluetooth protocol. As you know, Bluetooth is a protocol that connects near field devices such as headsets, speakers, and keyboards. Its minimum range is a 10-meter radius (~33 feet) and maximum is at 100 meters (~328 feet).

Whether it's the start, middle, or end of summer, it's prime-time grilling season. If you find yourself without a grill, however, it may seem as if half your summer plans of swimming by the pool while stuffing hot dogs in your face could be ruined.

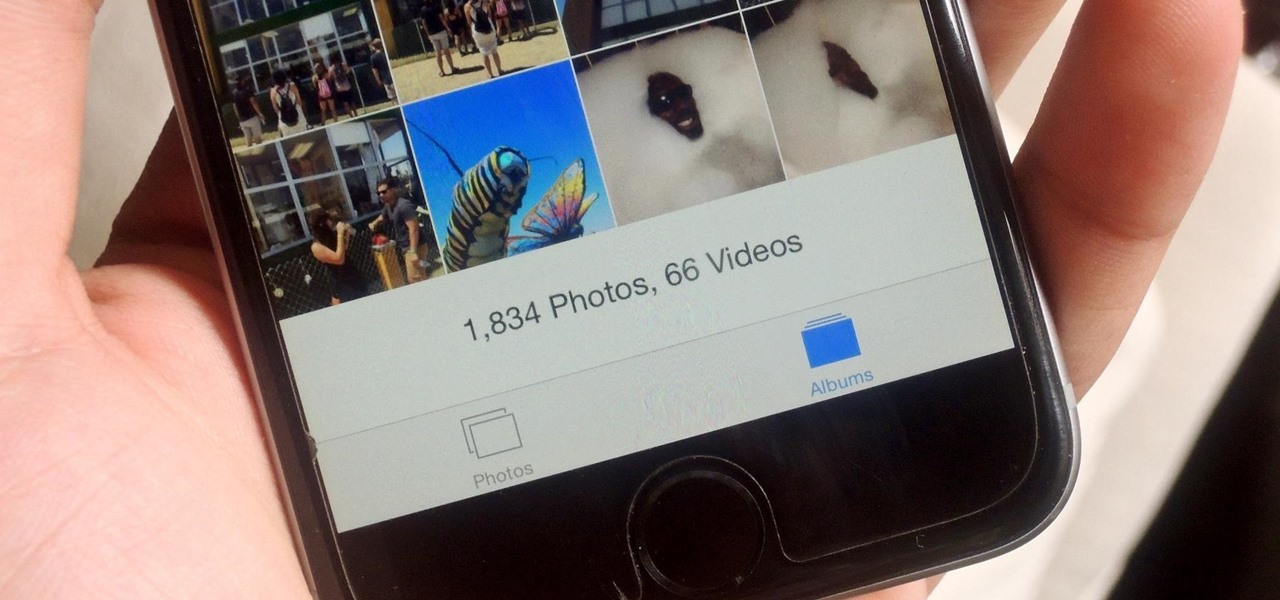
If you have a ton of photos and videos on your iPhone, backing up to iCloud is probably a no-go since it only provides 5 GB of free storage. Yes, you can buy more storage, but who wants to do that? And what happens if you run out of storage, stop backing up, and your phone gets lost, stolen, or damaged.

Hi all, Pro Hackers/Crackers, Let's see how we can use batch for our own Protection instead of exploiting someone with it.

One of the latest home-improvement gadgets out there today, smart lighting, has become more popular as prices come down. That being said, its still quite a penny to shell out. In this article, I'll go through a few of the top products out there today, including the Philips Hue, Belkin WeMo, and Lifx.

When you're trapped at your desk before a jumble of data just waiting to be categorized, or zoning out during an important meeting, your mind wanders and, chances are, you feel a little guilty because of it. Yet you shouldn't try to reign in that distracted thinking. Instead, let your brain get distracted, and you'll unconsciously strengthen your memory.

Welcome back, my nascent hackers! We have spent a lot of time in previous tutorials focused on hacking the ubiquitous Windows systems, but the vast majority of "heavy iron" around the world are Linux or Unix systems. Linux and Unix dominate the world of Internet web servers with over 60% of the market. In addition, Linux and Unix servers are the operating system of choice for major international corporations (including almost all the major banks) throughout the world.

Emojis have transformed the way we laugh and cry, tell stories, give responses, and express excitement to get a drink after work — without any actual text required. Heck, in an incredibly meta move, the Oxford Dictionary even named the "Face with Tears of Joy" emoji as their word of the year at one point. So how could you not want to be an emoji character for Halloween? Emojis are everywhere. The ubiquitous symbols are already on smartphones, tablets, and social networks, so why not help them...

Welcome to the first chapter of Excel is Simple, a place where we will burst all myths around excel and try to make it simpler and fun to use.

Many Android games use large, storage-heavy OBB files to store supplemental data. Generally, games with high-end graphics download these extra files when you install them from the Google Play Store.

Most Android devices allow you to simply replace a ZIP file in your /system/media folder if you want to change your boot animation. Unfortunately, though, this isn't the case for the Galaxy S5, as it's been buried deep in Samsung's TouchWiz skin.

Third-party keyboards have been available for iPhone ever since iOS 8, but which ones are worth checking out? There have been many options over the years, and if you want keyboard features like swipe-typing and themes, you're going to have to put Apple's stock QuickType keyboard on the backburner and try out these top hits.

Welcome back, my rookie hackers! I recently began a series on using Metasploit, and my goal with it is to teach you the very basics the incredibly powerful hacking tool has to offer while progressively moving on to the more advanced features.

For some, there's nothing more thrilling than carrying an armful of bags while wandering the mall; for others, there's nothing more annoying. No matter what category of shopper you fit into, the truth is that you aren't always in control of what you buy.

Journals are a great source of hilarity and embarrassment, detailing everything from your elementary school crushes to those super awkward middle school dances. While rereading your old hand-scrawled entries might make you cringe, that old journaling habit could benefit you as an adult.

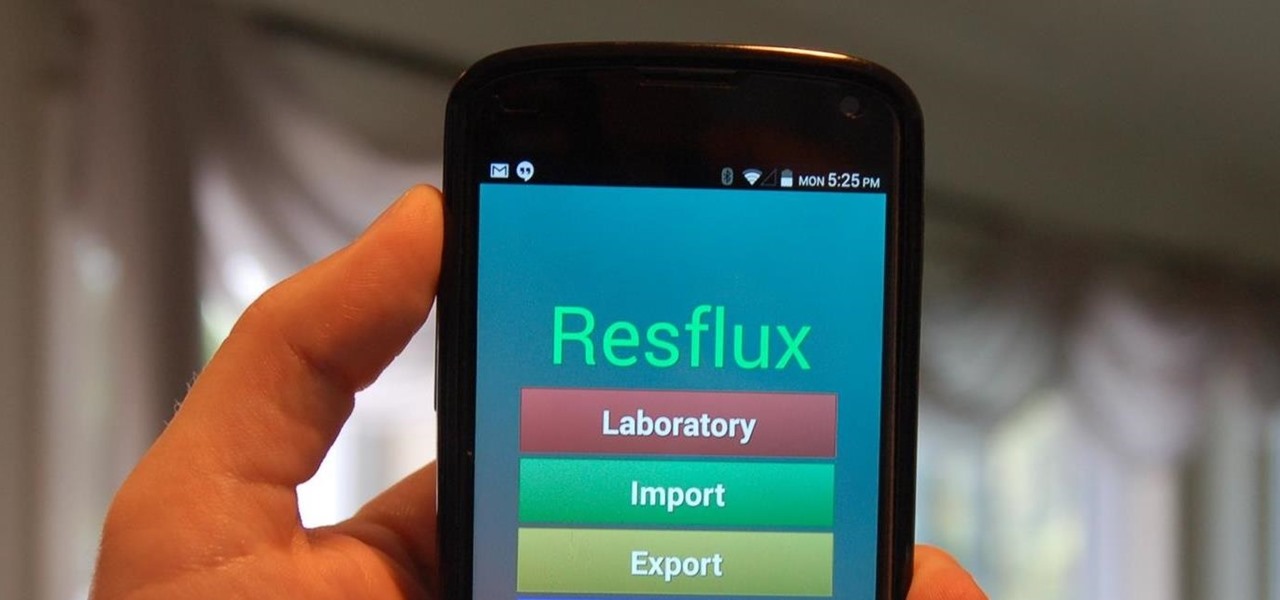
Resflux is an Xposed mod developed by Julian Paolo Dayag, aka WisdomSky, that provides users with a straightforward and functional way to customize and theme almost every aspect of the packages (apps and system components) installed on their Android device.

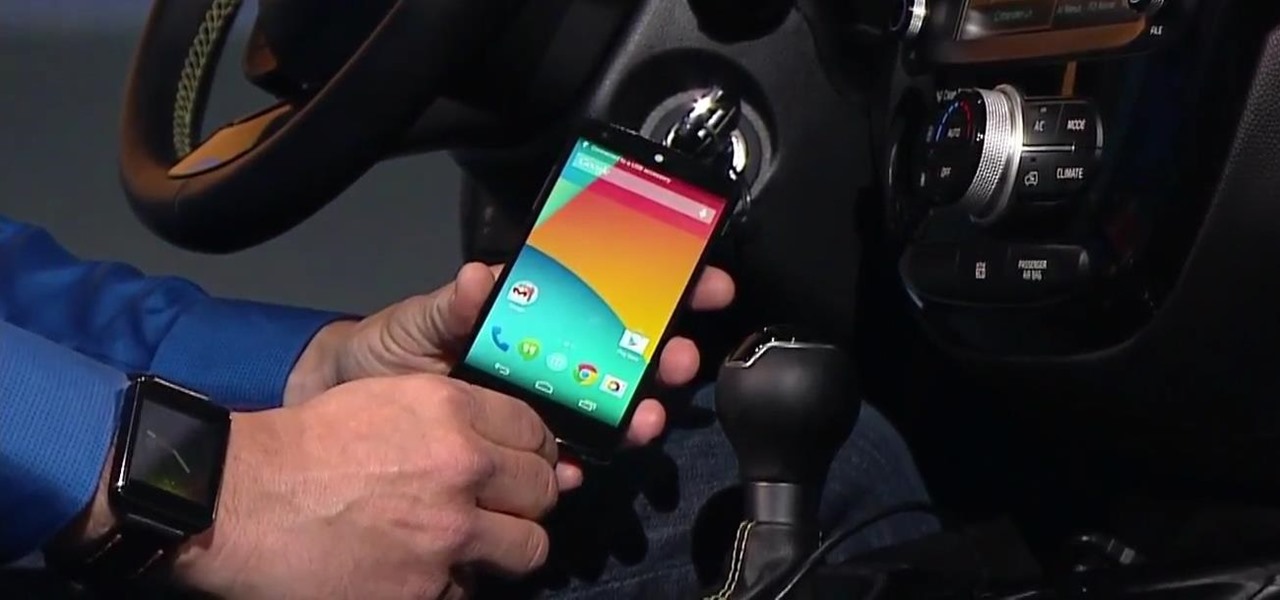
This year's I/O was all about bringing Android into the future and onto new devices. On top of announcing the upcoming "L" release of its mobile OS, Google showcased Android Wear, Android Auto, and Android TV.

The newer Graph Search in Facebook can help you find friends in specific cities, photos of a particular subject, restaurants that your friends liked, and a whole lot more. One thing it can't help you with just yet is searching public posts on Facebook, which you could do in the previous search version. Actually, some users do have the option to search public posts with Graph Search, but it's very limited and doesn't include me. If you're like me and don't have access yet, there is a workaroun...

It's one hell of a device, but the Samsung Galaxy S5 is still susceptible to the many hazards that other smartphones are prone to: theft, cracked screens, poor battery life, and particularly, overheating.

If you drop your smartphone in water, take it apart as much as you can and place it in rice. It's been the most recommended method of cell phone rescue since the days of clamshells. In fact, it's usually the only thing recommended when searching for "how to save your wet phone." Turns out, we've been wrong all along.

HTC's recent release of a new flagship phone brought tons of fanfare along with it. Dubbed The All New HTC One, the M8 edition of the popular One series phone also marked an update to the HTC Sense UI. Manufacturer skins like Sense can be a bit of a polarizing subject, especially amongst Nexus owners who are used to experiencing Android's interface exactly as Google envisioned it.

Welcome back, my greenhorn hackers! After the disaster that was Windows Vista and the limited and reluctant adoption of Windows 8 and 8.1, Windows 7 has become the de facto standard operating system on the desktop/client.

The @DesignGears guys have been busy today, leaking an unofficial KitKat build (Android version 4.4.2) for the AT&T Samsung Galaxy Note 3. The latest is a peek into what the international variants are beginning to see, although this build is far from official. Still, if you want to give it a shot, I'll show you how to install it, but make sure to check out the details below the how-to to see what you can expect, good or bad.

The mother of all games is almost here. Super Bowl XLVIII pits the Seattle Seahawks (or Seachickens, if you're from the Bay Area) against the Denver Broncos and regent exemplar of neck surgeries, Peyton Manning.

There are much better things that can go in your iPhone's status bar besides an always-on indicator displaying what carrier you're shelling out money to every month. While it would be nice to get rid of the carrier name altogether at the top of the screen, an even better option is switching it out with something else to better personalize your iPhone.

Welcome back, my rookie hackers! A short while back, I began a new series on database hacking, and now it's time to continue and extend your education in that field. As you know, the database contains all of the most valuable info for the hacker, including personally identifiable information, credit card numbers, intellectual property, etc. So, it's the ultimate goal of cybercrime and the APT hacker.

WhatsApp is one of the most well-known and most utilized cross-platform chat applications available today. It's free for one year, and only $0.99 a year after, which is chump change when you realize there are no hidden costs like international charges. Basically, it creates an easy to use forum for you and your friends to chat, regardless if they're an Android or iPhone user.

Welcome back, my fledgling hackers! Awhile back, I demonstrated one of my favorite little tools, netcat, which enables us to create a connection between any two machines and transfer files or spawn a command shell for "owning" the system. Despite the beauty and elegance of this little tool, it has one major drawback—the transfers between the computers can be detected by security devices such as firewalls and an intrusion detection system (IDS).

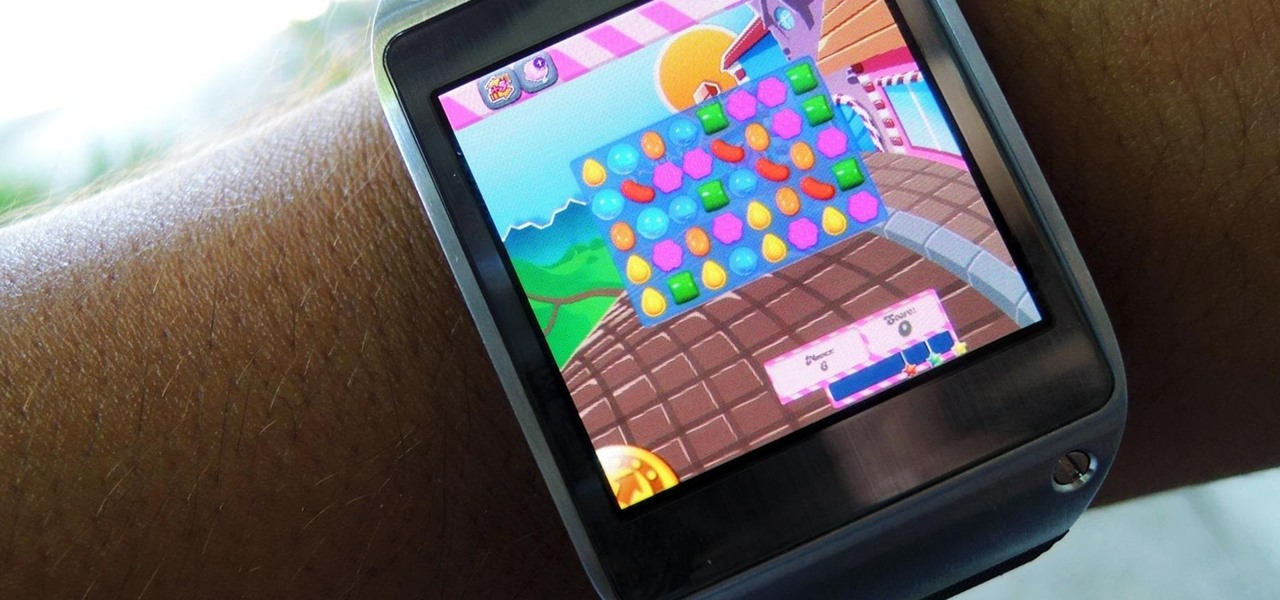
When it comes to the user interface, you're pretty much limited to the stock one that comes on your Samsung Galaxy Gear smartwatch—a carousel of large black and white icons representing the features and applications on the watch.

With the Samsung Galaxy Gear smartwatch only several weeks old, the extent as to what you can do with it is limited since there are only about 70 apps in the Gear Store right now, and a lot of those need the full app installed on your Samsung Galaxy Note 3 in order to function properly.

Whenever the word "popup" pops up, I immediately cringe because all I can think about are those obnoxious ads that ruin my everyday browsing experience. But, not all popups are evil.

Russians are well known for their knack at documenting exciting and horribly beautiful events on the go, from insane car accidents to attempted insurance fraud and even a superbolide meteor streaking across the sky.

For the most part, transferring files from your computer to your Nexus 7 (and vice versa) is a simple process. Just hook up your tablet to your computer with the USB cable and transfer. However, most of the time you'll need additional software on your computer to do this, and then, of course, you need the USB cable.