For right-handers, work from right to left or top to bottom. For left-handers, work from left to right, or top to bottom. Bring the needle to the front of the fabric at A, and pull the thread through. Now, for the rest of your stitches, you can work them more quickly if you "run" them on the top of the fabric, without taking your hand to the back. Go down at B, and, using your fingers on your non-dominant hand (the one that's not holding the needle!) behind the fabric, encourage the needle to...

This video shows you how to assemble and install a Thule ladder rack (part # TH375) pick up truck rack system, part of the professional series line. The second video goes over adding the Thule ladder tilt rack and the third part shows you quickly how to use it.

How to cook Puerco Pibil by Robert Rodriguez. This is an excellent spicy breakfast. This is the slow roasted pork as seen is his film Once Upon a Time in Mexico. 5T whole annato seeds 2t whole cumin seeds

If you have a beautiful Annual flower bed or a formal bed with lawn on one side you'll want a clean edge between the two. It not only looks nice but keeps weeds from encroaching into the bed helping reduce maintenance. There are several ways to create a nice edge to your beds. You can use a shovel, digging a line bit by bit but that gets hard on the back. Available materials for edging include, plastic edging and metal strips and wooden edging pieces. The wooden edges can be linked together b...

One of the few raspberry pests is the raspberry cane borer. It is an easy pest to control organically because all you do is clip it out, no spraying and no one gets harmed. It's simple to find, look at your cane, you'll see where it is dead, then go down about 6 inches and you'll see 2 little girdle lines. The adult has girdled the cane and laid an egg in between. If you don't clip this out that egg will hatch, the worm will go down that cane and kill the whole cane. So as soon as you see the...

In this tutorial, we learn how to draw people using boxes. Start off by drawing a box for the head, then a box for the body that is bigger then the top box. Keep drawing boxes and rectangles to make the entire body, tracing over it with lines, then filling the body in with muscles and bones. After this, make the face and add on hair to the body. Use shading to make the figure look more realistic. The boxes should give you an outline of where each body part will go, and give you a guide on how...

In order to build a trip wire, you will need the following: a knife, fishing line, a rope/string, sticks, and a large stone.

This video demonstrates how to create an ocean inspired makeup look. Apply primer to the eyes, first, as a base. Darken the base with a dark neutral powder. Brush it on with a eye shadow brush. Add a little green eye shadow to the inner 1/3 of the upper lid. Use a violet blue eye shadow to fill in the rest of the lid. Add a lighter blue to the middle 2/3 of the eyelid. Add your neutral brow bone color to fill in the upper 1/3 of the eye. Brush a little blue eyeliner underneath the eye.

Everyone wants to have a pretty young thing on their arm, but not everyone can get it. To secure perfect trophy wife of your dreams, you need to meet a few criteria. Check out this tutorial and learn the do's and don'ts of dating younger ladies.

Don't sit back and take verbal abuse! This tutorial will teach you how to dish it back out and craft the perfect insult.

Plagiarism is a serious offense, even if you are copying from the web. With this tutorial, learn how to cite websites properly using MLA format and avoid any trouble.

You don't have to eat out just to get to enjoy this impressive layered treat. You can add a decadent finish to your next dinner by showing your family your culinary skills and unveiling a homemade tiramisu for dessert.

Entertain your friends by turning your traditional personal headphones into a mini loud speaker with just an old mint tin and a playing card. This might not be the most advanced or prettiest way of listening to music but sure is a fun way to kill some time.

1. Peel the mango from top to bottom. Using the Y-shaped peeler, work your way around the mango, removing the skin. If the fruit is not quite ripe, keep peeling it away until the pulp is bright yellow. As you expose more pulp, use a paper towel to hold the peeled mango so it doesn't slip out of your hand. Peel away the tips. 2. Determine the tallest line of the mango. Place the mango on the cutting board and find the side that seems the tallest. the pit will be sitting along that line. 3. Sli...

Watch this video to learn how to get Rihanna's bronze look by the Makeup Geek. Use your ring finger to apply a coppery color (example: Illamasqua Liquid Metal in "Enrapture") and spread it all over your lids and up towards your eyebrows.

This video is a free drawing lesson on how to draw landscape scenery. • Draw a baseline or a horizontal line in the middle of the paper.

This is a cute look. Miley Cyrus is very popular and everyone loves her. This is a great look for going out and partying! Who wouldn't want to look like a famous person? Follow these steps and enjoy the look.

Lauren gives easy step by step instructions for makeup users of any experience level to create the beautiful look inspired by Paramore in their "Ignorance" music video.

With these instructions, getting a plum wine makeup look is quick and easy. 1. Begin with a clean face and apply a mixture of moisturizer and foundation all over your face for a smooth base.

The Department of Biological Sciences at the University of Alberta brings you this video tutorial specifically relevant to your student laboratory courses, specifically microbiology. If you're a student at any school of biology, this information will be helpful for learning how to mix gradients with a gradient mixer in the lab.

Hello, my name is Nicole Valentine and on behalf of Expert Village, I'm here to talk to you about how to coordinate birthday games for a birthday party. Now we're going to discuss another birthday game and this one also happens to be an oldie but goodie. And this game is called connect the dot. This is a perfect game if you want the kids in your birthday party to kind of calm down. Let's say after they've eaten, or even the birthday cake. But you want to draw about 4 lines of dots containing ...

This film is about gold. Gold diving. Use of the hookah rig to find gold. Gold flakes, nuggets, and platinum nuggets are shown. Gold and platinum are 15-19 times heavier than other streambed materials and concentrate in low pressure areas and cracks that run across rivers and streams. You look for a crack on the bank, and follow it out until you meet the "gold line" and there you suck it out with your dredge. Gold will be on the outside edge of a river gravel bar, at the head of the bar (larg...

When you need to type in all caps on a computer, you just press the "caps lock" key. But no such key seems to exist on iOS. The "shift" key appears to work at first but will deactivate once you type one capital letter. Holding down the shift key while you type gets the job done, but it's a pain. While it might not be obvious, enabling caps lock is actually really simple.

The term "hacker" often has negative associations attached to it, yet the world is in dire need of professionals with hacking skills. White hat hackers are ethical computer hackers that use their hacking skills to pinpoint network vulnerabilities and patch them up before they can be exploited by the bad guys.

It's exciting to get that reverse shell or execute a payload, but sometimes these things don't work as expected when there are certain defenses in play. One way to get around that issue is by obfuscating the payload, and encoding it using different techniques will usually bring varying degrees of success. Graffiti can make that happen.

Your S20 has a shortcut for Samsung Pay along the bottom of the home screen. But it tends to get in the way sometimes, especially if you're using the new Android 10 gestures in One UI 2. Besides, if you don't use the feature, you probably don't want that little white line at the bottom of your screen anyway.

Google just released the first version of the next major Android update. Early Android 11 builds will only available as developer previews, so you can't just sign up for the beta program and install the update as an OTA for the first couple months. That said, it's still pretty easy to get.

It's that time again. Snow days, Thanksgiving dinner, holiday presents ... and great Black Friday deals. Starting the Friday after Thanksgiving (or sometimes a few days before), millions of items will go on sale, including your next Android phone.

The mobile augmented reality war for dominance between Apple and its Asia-based rivals is in full effect.

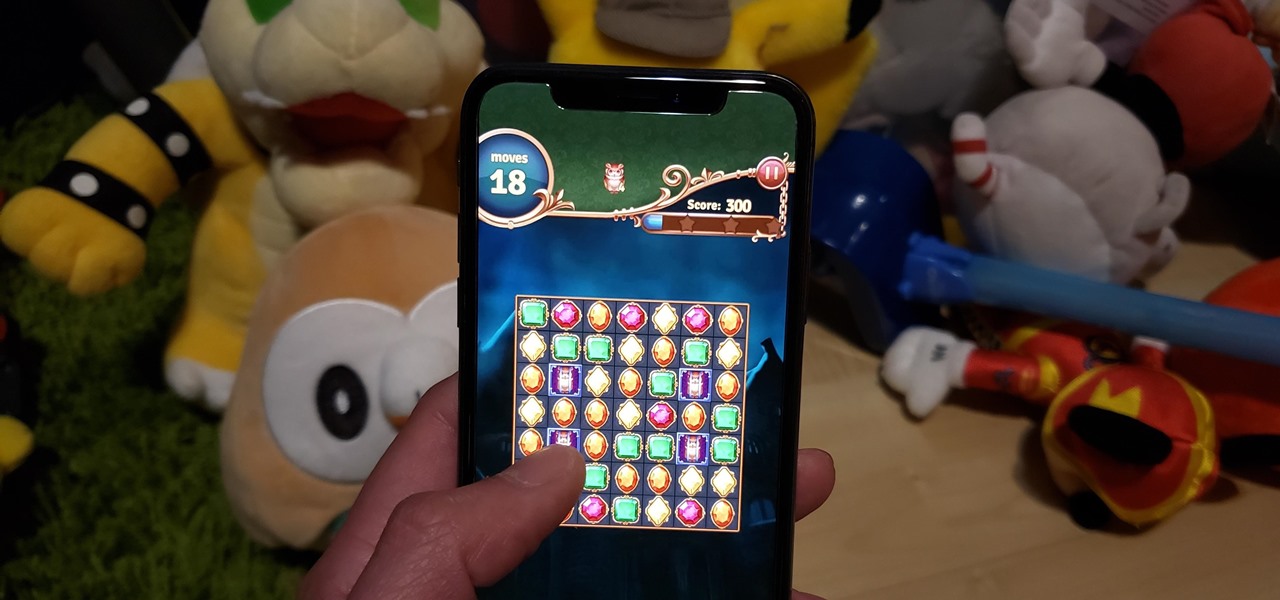
Though not as flashy as other mobile gaming genres like first-person shooters, puzzle games continue to glue players to their phones. Puzzlers are perfect companions while out and about or on a commute, and they're also a great way to stimulate your brain and hand-eye coordination in a fun, relaxing way.

With the number of web applications out there today, it comes as no surprise that there are just as many vulnerabilities waiting for hackers to discover. Finding those vulnerabilities can be a difficult task, but there are plenty of tools available to make the process easier. While it won't help find any zero-days, web scanners such as Uniscan will detect common vulnerabilities.

Apple released iOS 12.1.3 public beta 2 for iPhones on Wednesday, Dec. 19. Yes, that's confusing, since there was no first beta for iOS 12.1.3, but it indicates that it's the actual successor to iOS 12.1.2 public beta 1. Apple dropped iOS 12.1.2 unexpectedly to fix major issues but did not include everything in the beta, so we're picking up right where we left off.

It's that time of year again. No, not Thanksgiving. Black Friday. There are a lot deals available this holiday weekend, many of which include flagship Android devices. Whether you are thinking of buying a phone for yourself or looking for a gift for someone else, you can find a little savings to shop smart during the holidays.

In a previous tutorial, we were able to measure horizontal surfaces such as the ground, tables, etc., all using ARKit. With ARKit 1.5, we're now able to measure vertical surfaces like walls!

Have you noticed the many utility ARKit apps on the App Store that allow you to measure the sizes of horizontal planes in the world? Guess what? After this tutorial, you'll be able to do this yourself!

While our time with the Protostar VM from Exploit Exercises was lovely, we must move on to bigger things and harder challenges. Exploit Exercises' Fusion VM offers some more challenging binary exploitation levels for us to tackle. The biggest change is that these levels are all network services, which means we'll write our first remote exploits.

The idea of a dock on any smartphone, be it iPhone or Android, is a fantastic invention. It allows you to stay grounded with a core group of apps that you frequently use. However, sometimes that dock can feel like an obstruction in the face of style — but there's a trick to hiding that translucency behind those core apps at the bottom of your iPhone without jailbreaking.

As we aim for a wireless world, technology's reliance on cloud computing services is becoming more apparent every day. As 5G begins rolling out later this year and network communications become even faster and more reliable, so grows our dependency on the services offered in the cloud.

During our last adventure into the realm of format string exploitation, we learned how we can manipulate format specifiers to rewrite a program's memory with an arbitrary value. While that's all well and good, arbitrary values are boring. We want to gain full control over the values we write, and today we are going to learn how to do just that.

The one thing that separates a script kiddy from a legitimate hacker or security professional is the ability to program. Script kiddies use other people's tools, while hackers and security pros write their own tools. To that end, we're going to see how a stack overflow vulnerability allows us to flood a variable with enough input to overwrite the instruction pointer with our own commands.