
How To: Get a strong core with cable squats
Learn how to do cable squats. Presented by Real Jock Gay Fitness Health & Life. Benefits


Learn how to do cable squats. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do standing cable chest flys. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do wide push ups. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do plyometric clap push ups. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do close grip push ups. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do proper push ups. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do side pillar hip lifts. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do shoulder push up. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do superman holds with freestyle kicks. Presented by Real Jock Gay Fitness Health & Life.

Learn how to do one arm medicine ball push ups. Presented by Real Jock Gay Fitness Health & Life. Benefits

We've all been there. You wake up early, hungry for breakfast, but not just any breakfast will do. You want bacon and eggs. So, you blindly stumble into your kitchen, underwear-clad, and begin fumbling about with pots and pans. After a few minutes, you fill your pan with delicious and smokey rashers and turn the heat on. Everything seems okay... until the bacon actually starts to cook. With a splat, burning hot grease flies out of the pan and bombards your skin, causing intense pain and great...

There are loads of reasons for somebody to want to recover a Windows password, and there are lots of different ways of doing it. My favorite of all of these ways is to use a piece of software called Ophcrack because:

Building a DIY Alarm System: The Concept So, you want to protect your property, or maybe a room, car, or even your backyard. The concept of an alarm system is to notify the "alarm administrator" that there is an intruder entering the previously designated boundaries. The triggers for this boundary could be as simple as a pressure sensor, or as complicated as a laser network. They all do the same thing, but some work better than others.


Mobile privacy is one of the most pressing security issues in existence. Since we carry our phones with us everywhere we go, we need to ensure that we're safe from prying eyes.

One of the first steps when pentesting a website should be scanning for hidden directories. It is essential for finding valuable information or potential attack vectors that might otherwise be unseen on the public-facing site. There are many tools out there that will perform the brute-forcing process, but not all are created equally.

The USB Rubber Ducky and the Digispark board both suffer from the same issue when attacking macOS computers: a keyboard profiler pop-up which tries to identify any non-Apple USB keyboards. While it's an annoying setback, the solution is a simple modification that allows Mac computers to be targeted, which affects the ability to target Windows and Linux devices.

While SSH is a powerful tool for controlling a computer remotely, not all applications can be run over the command line. Some apps (like Firefox) and hacking tools (like Airgeddon) require opening multiple X windows to function, which can be accomplished by taking advantage of built-in graphical X forwarding for SSH.

The punch hole design of the Samsung Galaxy Note 10 has challenged users to find a clear way to deal with it. Although it's less intrusive than a notch, if left unaccounted for, it can be just as much of an eyesore. One of the more creative ways we've found is to use as a battery indicator.
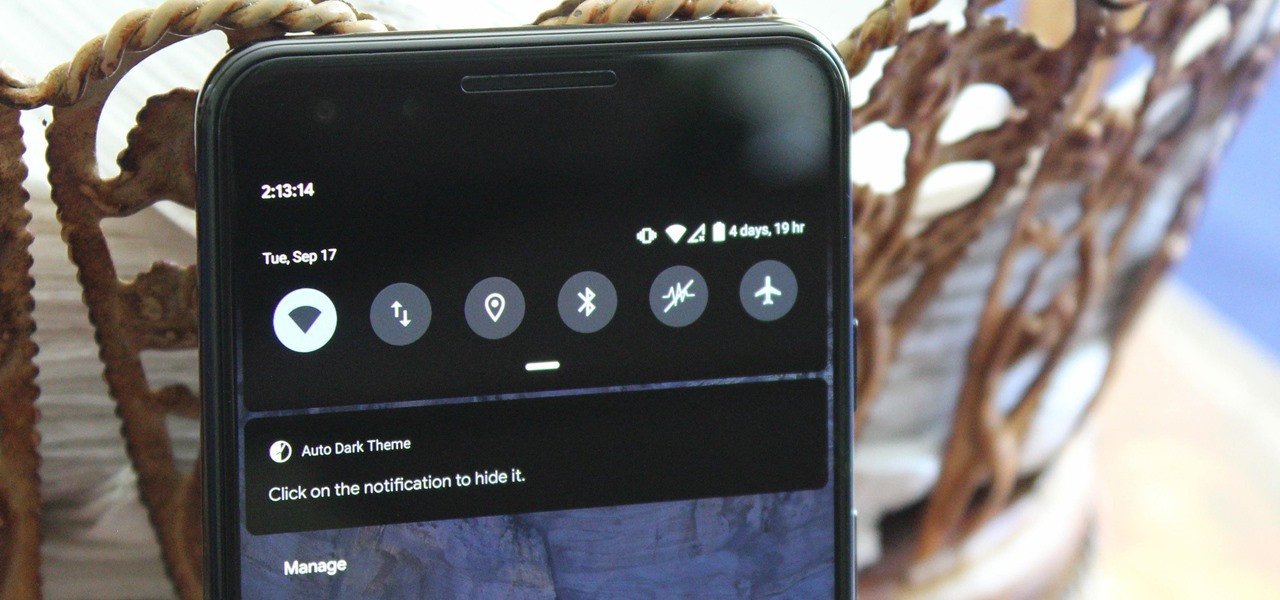
Android 10's new dark mode is a pleasure to behold for longtime users. Ever since OLED panels became widespread, we've been clamoring for the feature. But now that we have it, there's a new problem: it doesn't turn on automatically based on time of day. Thankfully, a simple app can turn dark mode into a true night mode.
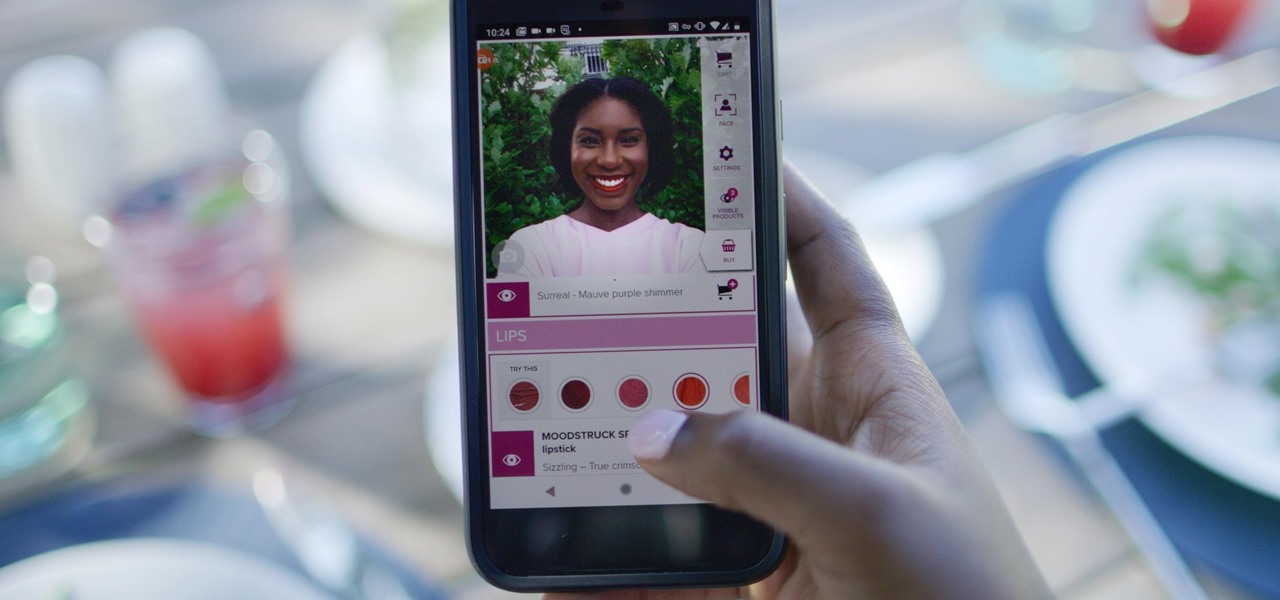
Now that some of the best-known beauty brands are leveraging augmented reality to market and sell products, the rest of the market is beginning to catch up — fast. The latest competitor to add AR to its arsenal is direct sales makeup company Younique.

One of the first steps in attacking a web application is enumerating hidden directories and files. Doing so can often yield valuable information that makes it easier to execute a precise attack, leaving less room for errors and wasted time. There are many tools available to do this, but not all of them are created equally. Gobuster, a directory scanner written in Go, is definitely worth exploring.

The longer it takes Apple, Snapchat, Facebook, and other tech giants to build their own version of augmented reality headsets and smartglasses, the longer runway of practical experience Microsoft gains with the HoloLens and its sequel. The latest example: AR cloning.

While a viable version of consumer-grade smartglasses has yet to find mainstream success, two more contenders emerged this week, as Vuzix confirmed that a leak of a fashion-forward design is legitmate and Vivo introduced tethered smartglasses designed to pair with its new 5G smartphone.

Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. It can include the carrier, the owner's name and address, and even connected online accounts.

As the opening act to the grand unveiling of the long-awaited HoloLens 2 at Mobile World Congress Barcelona on Sunday, Microsoft showed off the standalone Azure Kinect time of flight sensor, which also happens to supply the improved human and environmental understanding capabilities of the next-generation augmented reality headset.

Now that Lego Movie 2, a film about an imaginary world made of plastic bricks existing parallel to the real world, is in theaters, it's the perfect time to shop for Lego apparel at a store modeled after that world.

Depending on your region, you may not be offered the same call recording option other OnePlus users have. But, as with most things Android, where there's a developer with a will, there's a way regardless. And the method we are about to describe is one of the easiest, most stable, and undetectable ways to do it. Perhaps we should discuss why OnePlus has been holding out you when it comes to this feature, though.
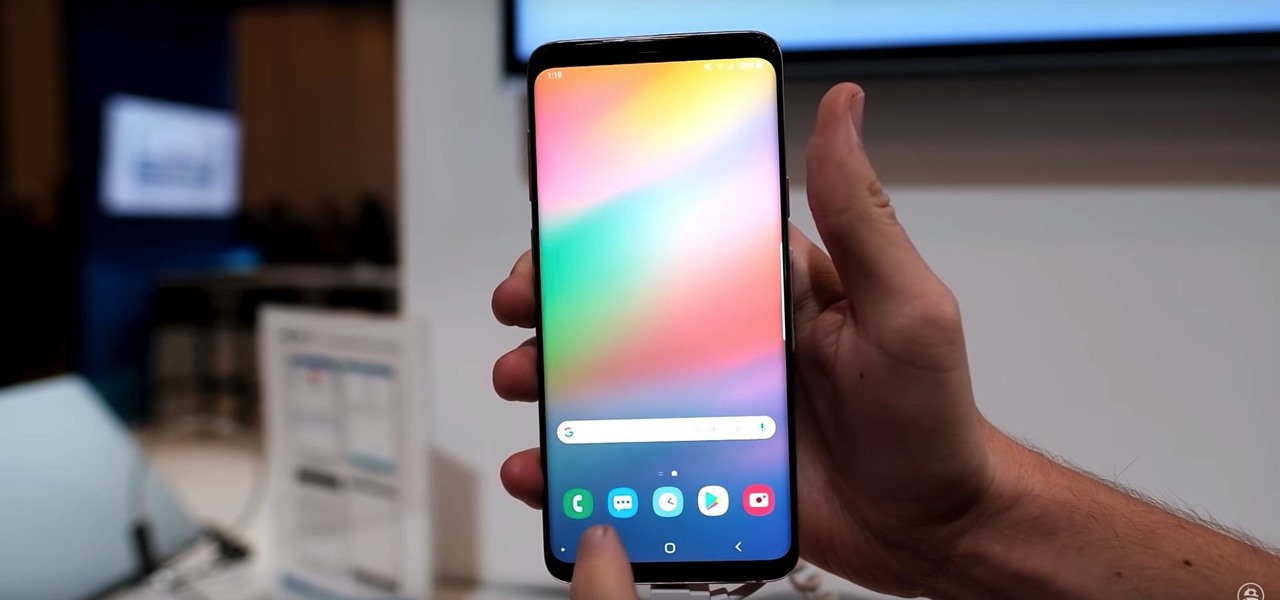
Who doesn't love a refresh? Samsung's upcoming One UI makes it easier to use your device with one hand and adds a fresh coat of paint to the formally "Samsung Experience" skin. While you're probably looking forward to installing One UI on your phone, not all Galaxies are equal — your device could be one of the first to receive the update, or it could never see One UI at all.
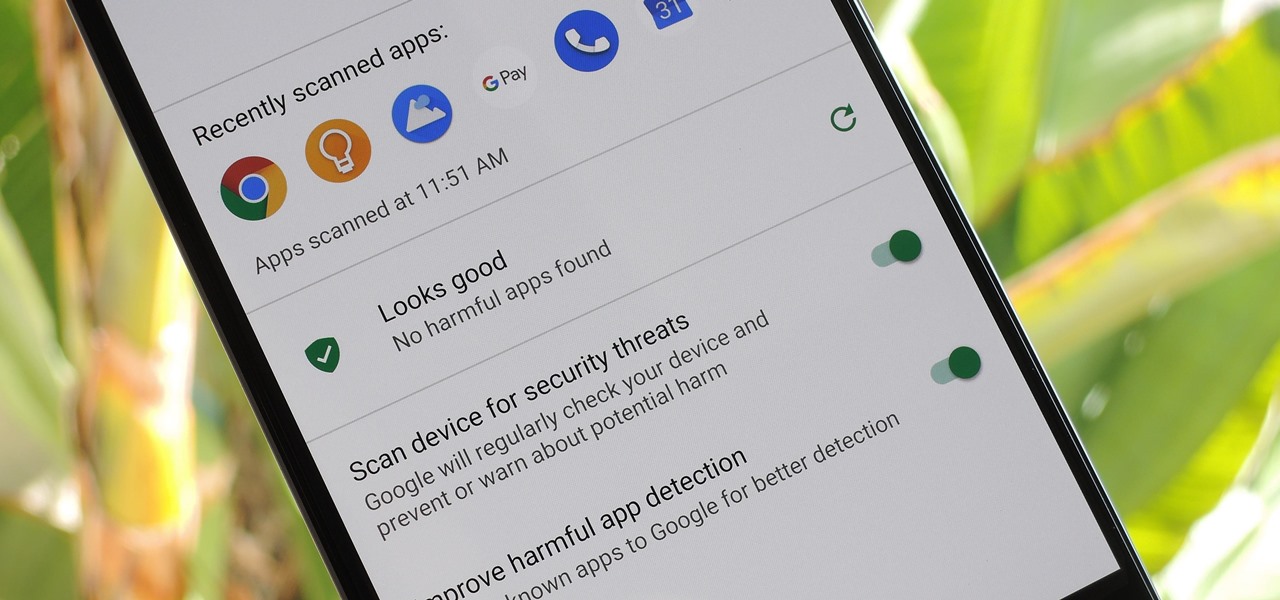
According to Google's new Android ecosystem transparency report, you're eleven times more likely to be infected by malware if you're running Android Lollipop (5.0) as opposed to Android Pie (9). The same report shows that if you sideload apps, you're almost seven times more likely to be infected than if you stick to Google Play as your app source. All of the data provided in the report is quite interesting, but there's a clear pattern among malware-infected users.

Automotive augmented reality company WayRay has set its destination for a $1 billion valuation with an estimated time of arrival of 2019, and it has just passed a major milestone towards that goal.

Gmail conversations, Facebook private messages, and personal photos can all be viewed by a hacker who has backdoor access to a target's Mac. By livestreaming the desktop or exfiltrating screenshots, this information can be used for blackmail and targeted social engineering attacks to further compromise the mark.
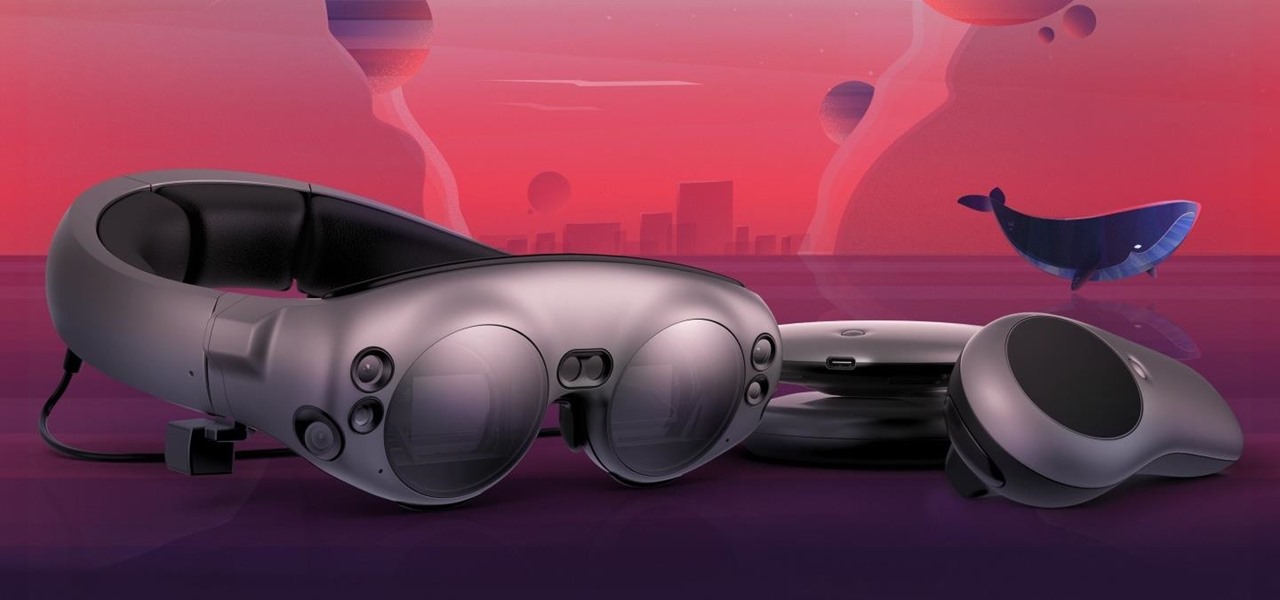
If you subscribe to notifications for Magic Leap CEO Rony Abovitz's Twitter feed, you'd think everyone in the world already has a Magic Leap One. Alas, that is not the case, but those not within the geographic areas of Magic Leap's LiftOff service now have a loophole through which they, too, can join the "Magicverse."

Just in time for Women's Equality Day on Aug. 26, Treasury Wine Estates is breaking out a line of wines with augmented reality experiences that pay tribute to historically famous women.

The latest version in Epson's Moverio line of smartglasses looks to offer a headworn window into the world that prioritizes versatility as well as mobility.

Note-taking apps are a dime a dozen on the Play Store. However, due to their inability to sync across devices, many can't compete with Google Keep. Mozilla decided to throw their hat in the ring with Notes by Firefox, and unlike others, their notes app syncs easily with one of the most popular browsers, plus it's encrypted.

With summer in full swing, these Snapchat lenses are as hot as ever. With people celebrating the 2018 World Cup in Russia, Snapchat contests that earn could earn you a free ride to Comic Con, and the everyday innovation that comes out of Lens Studio, there's something for everyone here this week.

Thanks to Apple's ARKit 2.0 augmented reality framework in iOS 12, we now have a "Measure" app built right into our iPhones that can measure real-world objects. No more physical tape measure or ruler. No more guessing. Just whip out your iPhone, open the app, put your camera, and get measurements. Before you do, however, there are a few things you'll want to know.

Electronics maker Epson is courting developers to its Moverio smartglasses with an updated software development kit (SDK) and integration with a web-based tool for publishing augmented reality experiences.

Backdooring a powered-off MacBook is easy when a few minutes of physical access is allowed. That attack works well if the hacker also shares a Wi-Fi network with the victim, but this time, I'll show how to remotely establish a connection to the backdoored MacBook as it moves between different Wi-Fi networks.