
News: Lenovo Expands Mirage AR Headset Beyond Star Wars with Marvel's Dimension of Heroes
Move over, Star Wars. You're not the only Disney property that can play in the Lenovo Mirage AR headset anymore.


Move over, Star Wars. You're not the only Disney property that can play in the Lenovo Mirage AR headset anymore.
Whether it's for health reasons or just to look better, many of us want to get in shape. It's a long process that starts with nutrition, and dieting is never easy. Fortunately, there are some great food-tracking apps that will make it a lot easier to become a healthier version of yourself.

For many, phones are starting to replace televisions as the primary device for watching videos. Thanks to their portability and easy to use apps, it's often simpler to watch Netflix, Hulu, YouTube, or Prime Instant Video on the smaller screen. But not every phone is suited to fit this need, so we did some testing to find the best of the best when it comes to streaming videos.

If you use Apple's email services and the "From:" field in your iPhone's Mail app is cluttered with @Mac.com, @Me.com, and @iCloud.com variations of the same address — along with third-party accounts — there's an easy way to declutter things and hide the addresses you don't use anymore.

Facebook added a new feature that lets you post 3D versions of your portrait mode photos for all your family and friends to see on their smartphones, computers, and virtual reality goggles. These new 3D photos add a whole new dimension to your images with movement and more depth.
Smartphones and laptops are constantly sending Wi-Fi radio signals, and many of these signals can be used to track us. In this guide, we'll program a cheap IoT device in Arduino to create hundreds of fake networks with common names; This will cause nearby devices to reveal their real trackable MAC address, and it can even let an attacker take over the phone's data connection with no warning.

The Play Store hasn't been the most secure place for apps lately. A quick Google search for "Play Store malware" will give you a taste of some of the malicious apps that snuck their way onto Android's official app store. Google is aware of the problem and they're tying to fix it, but their new Play Protect program doesn't have a great track record, so you might want to look elsewhere.

Clumsiness is the great equalizer when it comes to smartphones — it makes no distinction between the most expensive flagship handset and cheaper mid-range models. A hard drop onto pavement will usually result in a shattered screen, regardless of how pricey your device is. And with a smartphone breaking every two seconds, we're truly our own handset's ultimate nemesis.

Apple first added a "Drag and Drop" feature to iPads in iOS 11, but your iPhone can do a little of the magic, too. It's just not so obvious. While you can't drag and drop items from one app to another like you can on an iPad using Split View and Slide Over, you can move things around in certain stock applications. And it works the same whether you're using iOS 11, 12, or 13.

On your iPhone, your phone number and Apple ID email address are the default ways in which somebody can contact you on FaceTime. While you can't remove your phone number as an option, you can withdraw your Apple ID email account. More importantly, you can add any other email addresses you'd like to the list, so you never have to worry about a friend, family member, or coworker not being able to audio or video chat with you.
This week's Market Reality covers a variety of business news from acquisitions and partnerships to competitive and technology assessments to quarterly financial results.

We're almost there to completing the setup of your Mac for hacking! Now that we have Git and Homebrew under our belts, it's time to take on something fairly easy, but very important for our hacking needs.

The biggest corporation we know today is called Google, I bet you've heard of it yeah? How Google Tracks You:

When you think of all the fun and games smartphones have to offer, it's easy to forget that they also make a great tool for getting things done. With utilities like document scanners, calendars, to-do lists, office apps, and password managers, that little computer you carry around in your pocket has the potential to increase your productivity levels in all aspects of life.

If you purchased something from iTunes, the iOS App Store, iBooks Store, Apple TV App Store, or the Mac App Store and it doesn't work, didn't download, is buggy, or wasn't what you thought it was, you can get a full refund from Apple—you just have to know how to ask.

Welcome back! In the last round of python training, we talked about tuples and dictionaries. We'll be diverging again and talking about logical operators as well as membership operators. These are used very similiar to booleans, so if you haven't read that, I suggest you do so first.

This Video will show you how I make Cucumber and Tomato Salad.

This is second post in my series of posts for finding hacked accounts online. Please do read the part 1 of the post at http://null-byte.wonderhowto.com/how-to/find-hacked-accounts-online-part-1-0164611/
Notes on iOS has never been a particularly great app due to a lack of overall features compared to other note-taking apps like Evernote or Microsoft OneNote.

Both the Galaxy S6 and S6 Edge have had root methods available to them before the phones were even released, but the problem with these existing root methods is that they would trip the KNOX counter on your device.


The Watch Later feature lets you conveniently save videos to watch at a later time, using a playlist. Hover your cursor over the thumbnail of a video, like the one below, and click the clock icon to automatically add the video to your Watch Later list.

If you accidentally deleted a few contacts in Gmail, don't worry. You could still restore or find those email ids. This video will show you how to recover those contacts and bring back to your contact list. The process of recovering those contacts is quite easy. So please watch the video and follow all the steps carefully.

Welcome back, my novice hackers! Before we try to attack a website, it's worthwhile understanding the structure, directories, and files that the website uses. In this way, we can begin to map an attack strategy that will be most effective.
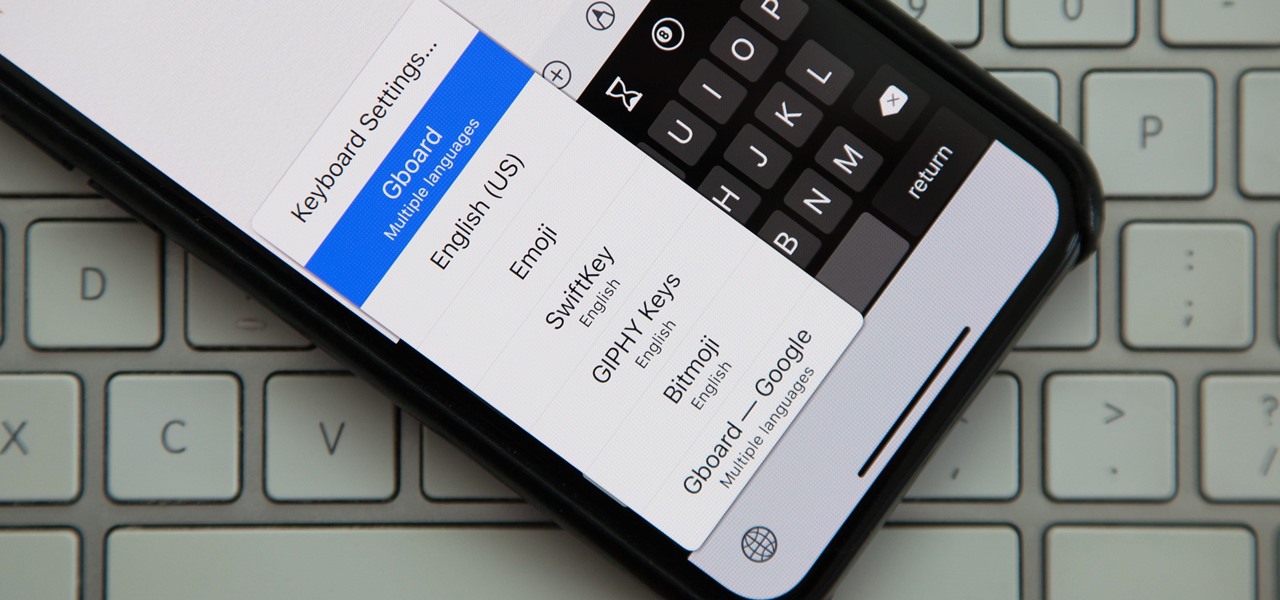
Back in iOS 8, Apple introduced the option to use third-party keyboards on iPhone, and since then, there have been a ton of third-party keyboards available such as Gboard, AudioShot, SwiftKey, Slated, and many more. However, adding and even using these keyboards can be kind of tricky.

Depending on who you ask, internet connectivity should be a basic human right. With Google recently embarking on a project to provide internet capabilities to remote corners of the world using balloons and satellites while Facebook attempts to do the same with unmanned drones, the concept of free web access is steadily gaining steam.

Welcome back, my hacker novitiates! In previous guides, we have used one of the most powerful hacking platforms on the planet, Metasploit, to perform numerous hacks. They ranged from exploiting Windows XP and Windows 7/8 vulnerabilities, to installing a keylogger and turning on a webcam remotely. We have even been able to save the world from nuclear annihilation, see if our girlfriend is cheating, spy on suspicious neighbors, evade antivirus detection, and more.

This video is going to teach you how to Create a DETACHABLE DIY Pvc Shoulder Rig Video: .

Video: . Learn How to Make My Creamy Cherry Pie Delight.

Welcome back, my budding hackers! In previous tutorials, we've looked at some of the basic commands and concepts for using Linux. Along the way, I realized that I've failed to provide you with some basic background material on the stdin, stdout, and stderror.

Yup, so I turned them vegan. The full recipe can be found here, or you can watch the video that I made on YouTube. Take a look at the ingredients below the video.

So moist, so clean and vegan. These vegan peanut butter cookies are soft and chewy. You can find the full recipe on my blog or just watch the video!

Overview of pre-built navigation menus in Xara Web Designer designs gallery. The navigation menus in Xara Web Designers designs gallery allows you to choose from a list of navigation designs without having to design it by hand. If you need assistance using Xara Web Designer let us know and we will do our best to create web design tutorials to help you.

Here's a list of the lifehacks shown in this video: Banana Foil

Unwanted advertising is everywhere. Annoying pop-up ads, overly loud late night commercials, spam...it never ends. And before spam, there was junk mail. Junk mail is even worse because unlike TV commercials and internet ads, it's physical. You can't just delete or ignore it—and it's an awful waste of paper. So what can you do about it?

For those of you still using a BlackBerry smartphone, this article will show you the tips and tricks to installing emulators and playing some classic Game Boy Advanced games on your device. You can find a few tutorials and videos out there on getting Game Boy Color or NES games on an Android device, but the most elusive mobile emulator is for Game Boy Advanced (GBA) on a BlackBerry.

In this Microsoft Word tutorial the instructor shows how to add a drawing or a free form shape to a document. Using the canvas in the Microsoft Word 2007 can be very helpful in adding graphical content to your document. Adding shapes and special effects like shadows, 3D will give a rich look to the document. To do this open a document in Word 2007. In the tool bar go to the Insert tab and in that select the Shape button. Now you are presented with plenty of predefined auto shapes. First at th...
Own a BlackBerry Curve 8330? Need a custom ringtone? Best Buy has answers. The Best Buy Mobile team explains how to set custom ringtones for contacts in your address book on the BlackBerry Curve 8330. There are many different ringtones to choose from and you may set a different one for each one of your contacts.

Windows 7 is the hot, new operating system replacing the past XP and Vista systems. Windows 7 is the most simplified, user-friendly version that Microsoft has developed - ever. Get acquainted with your new version of Windows straight from Microsoft.
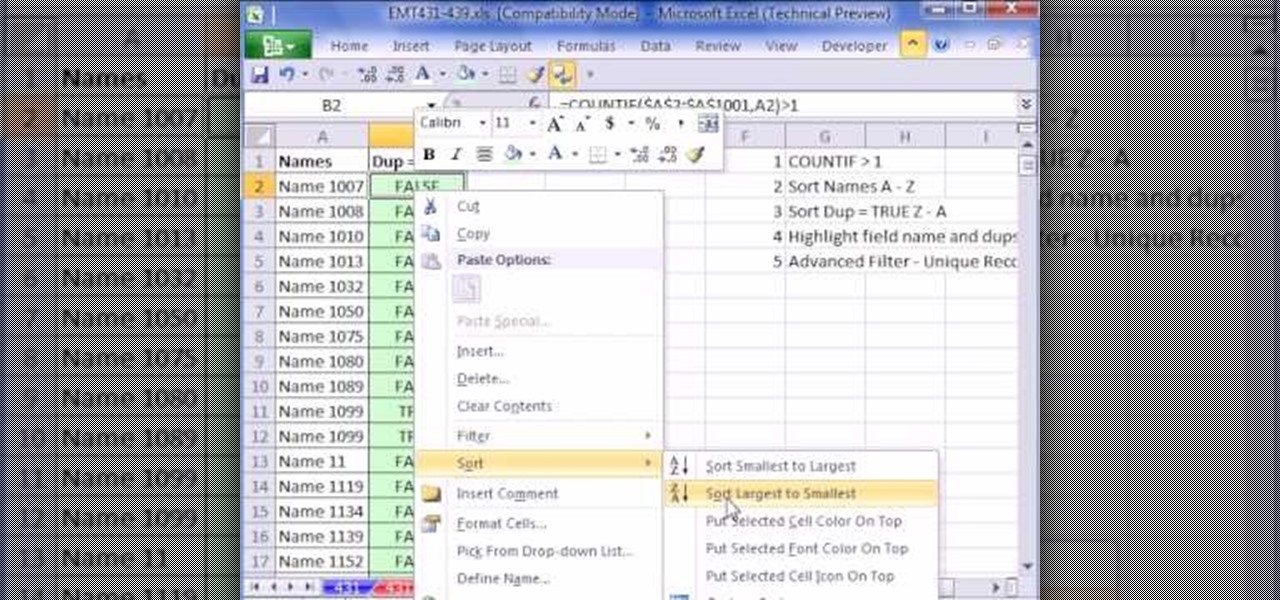
This video is about finding duplicate entries in excel sheet. The example excel sheet contains different names. There are around 1000 different names in the sample excel sheet. CountIf(range,criteria) formula has been used to do the comparison and return of results in True or False mode. Type =CountIf( now move your left arrow key, this will generate the formula like =CountIf(A2. Now press Ctrl+Shift+Down arrow, this will select all the available values in the column. Now press F4 to lock it ...