The once blurry and mysterious vision of Magic Leap's future is slowly coming into focus in the present, despite the company's obsessive attempts to keep any and all information under wraps until the next reveal is absolutely necessary. A new tidbit of information hints at an addition to the company's unfolding story that almost no one had accounted for: retail stores.

Amazon makes it exceptionally easy to purchase anything you want in just a few minutes. From textbooks for school to live ladybugs, its more surprising when you can't have something delivered to your doorstep in a few day's time.

In my first tutorial on Linux basics, I discussed the importance of hackers using Linux and the structure of the directory system. We also looked briefly at the cd command. In this second Linux guide, I'll spend a bit more time with changing directories, listing directories, creating files and directories, and finally, getting help. Let's open up BackTrack and getting started learning more Linux for the aspiring hacker.

On Friday, the release date for her new album, Queen, Nicki Minaj is already grabbing headlines for the track "Barbie Dreams," where she disses Drake and a host of other rappers.

Welcome back, my hacker novitiates! There are many ways to hack databases, and most of these techniques require SQL injection (SQLi), which is a way of sending SQL commands back to the database from a web form or other input. In this tutorial, we will use SQL injection to get access to the underlying server. So instead of getting access to the database and its data, we will use the database as an intermediary to gain access to the underlying server.

Welcome back, my hacker novitiates! In previous guides, we have used one of the most powerful hacking platforms on the planet, Metasploit, to perform numerous hacks. They ranged from exploiting Windows XP and Windows 7/8 vulnerabilities, to installing a keylogger and turning on a webcam remotely. We have even been able to save the world from nuclear annihilation, see if our girlfriend is cheating, spy on suspicious neighbors, evade antivirus detection, and more.

Welcome back, my budding hackers! In previous tutorials, we've looked at some of the basic commands and concepts for using Linux. Along the way, I realized that I've failed to provide you with some basic background material on the stdin, stdout, and stderror.

Welcome back, my novice hackers! We've done a number of tutorials using one of my favorite hacking tools, Metasploit. In each of them, we've used the msfconsole, which can be reached through either the menu system or through simply typing "msfconsole" from the terminal.

From time to time, you may need to locate the version and build number for a particular app on your iPhone or iPad, but it's not at all obvious where you can find the information. Well, there's more than one place to look on iOS 18 and iPadOS 18, but none are perfect solutions. Knowing each method will ensure you can always find any app's real version number.

Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. It can include the carrier, the owner's name and address, and even connected online accounts.

On Yelp, you have the option to check in to a business you're visiting. For you, broadcasting who you're with and where you're at is fun for social purposes, but for business owners, you're basically giving them free publicity. Well, almost free publicity. Since there's incentive to get you to check in, some businesses reward customers with special deals, such as 20% off your first visit.

When using Linux, we often need to install new software, a script, or numerous large files. To make things easier on us, these files are usually compressed and combined together into a single file with a .tar extension, which makes them easier to download, since it's one smaller file.

Welcome back, my aspiring hackers! In recent tutorials, I have made reference to the name and location of the Linux devices in the file system, such as sda (first SATA or SCSI drive). Specifically, I have mentioned the way that Linux designates hard drives when making an image of a hard drive for forensic purposes.

Welcome back, my greenhorn hackers! Several of you have you have emailed me asking whether it's possible to install a keylogger on a victim’s computer using Metasploit. The answer is a resounding "YES"!

In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack.

It's exciting to get that reverse shell or execute a payload, but sometimes these things don't work as expected when there are certain defenses in play. One way to get around that issue is by obfuscating the payload, and encoding it using different techniques will usually bring varying degrees of success. Graffiti can make that happen.

The Google Phone app is one of the best dialers for Android today, especially with all of the unique and exciting features it brings to the table. Unfortunately, without owning a Pixel phone, you are unable to officially download the app, making a modified version your only option. However, this version of Google Phone is missing a few key features, such as spam protection and business search.

Welcome back, my fledgling hackers! If you're like most aspiring hackers, at one time or another you've probably spent too much time playing Call of Duty and not enough time preparing for your final exams.

Businesses leave paper trails for nearly every activity they do, making it easy for a hacker or researcher to dig up everything from business licenses to a CEO's signature if they know where to look. To do this, we'll dig into the databases of government organizations and private companies to learn everything we can about businesses and the people behind them.

Welcome back, my tenderfoot hackers! This is the third installment of my series on basic Linux skills that every hacker should know. Although some hacking tools are available for Windows and Mac, every real hacker uses Linux—for good reason.

Apple is notoriously cryptic when it comes to the reveals of its new products, and as usual, they've kept us guessing about the release of the iPhone 5 (or "New iPhone?"). It's expected to be officially revealed on September 12, and rumor has it that sales will begin on the 21st. Though the whole world seems to be anxiously awaiting the announcement, there has also been some controversy surrounding the iPhone 5's production. With the high number of suicides and poor working conditions at Foxc...

Software takes time to create, and time is money, so a lot of great apps aren't free. But to generate interest, some developers will make their paid apps free for a limited time. The potential for a long-term increase in daily active users more than offsets the short-term lost revenue. So for us end users, the trick is knowing when these sales are going on.

While the tech industry is hot in pursuit of mainstream smartglasses for consumers, another early maker of enterprise-focused AR hardware has apparently met its end.

Why would Magic Leap, a company preparing to launch its first augmented reality headset this year, need a developer for iPhone and iPad apps? It's not as crazy as it sounds.

If you haven't heard yet, Google is revamping the Play Store with version 8.0. While it so far doesn't seem to have any life changing features, there are ones that certainly will make your life easier, like their new updates feature.

With some of the groundwork out of the way in getting a Mac set up for hacking, it's time to start looking at toolboxes. Our first toolbox is Git, which will be used throughout future tutorials.

More often than not, when you find an app that offers a particular functionality, there are ten other apps on the Google Play Store that offer virtually the same features. But the reason we choose one app over the alternatives is mainly due to one thing—a preference for the user interface of the app we ultimately install.

Hello partners, first of all I would like to thank all those who have sent me positive feedback about my posts, to say that I'm always willing to learn and teach. I'm also open to answer the appropriate questions.

Welcome back, my fledgling hackers! Over the years, we have examined multiple ways to own, exploit, or compromise a system. On the other hand, we have not spent a lot of time on denial-of-service (DoS) attacks.

If you look at the label on your favorite processed snack, there's a good chance you have no idea what half the ingredients are. It's nothing new, but with natural and organic foods becoming huge trends, we're hyper-aware of all the "chemicals" we eat.

Android's newest Jelly Bean 4.2 update comes with Daydream, a feature that allows you to run screensaver-like apps while your Android device is docked or charging. While the feature comes with several stock 'daydreams' available, there's a hidden Easter egg one that you can unlock! The 'daydream', aptly titled BeanFlinger, is hidden inside of Android's 4.2 Jelly Bean. In order to unlock it, you'll have to go to the phone's Settings and click on About phone. From there, you should come across ...

"Jef with one F" from the Houston Press compiled a list of the 10 best steampunk songs, but it's really a collection of the best steampunk music videos. There are some amazing videos in the collection, such as this one, "Brass Goggles" by Steam-Powered Giraffe. It's not the best-looking, but it's a great performance.

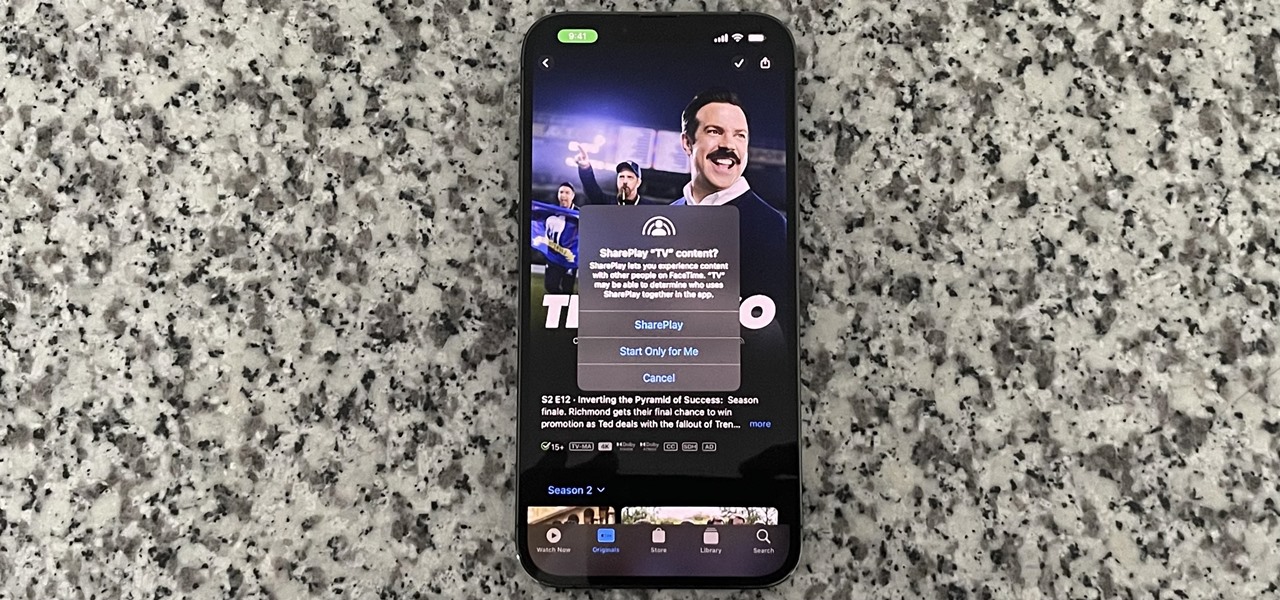
SharePlay is arguably one of the most significant features to hit FaceTime since group calls, and it's still hard to find apps that support shared experiences in FaceTime. Apple does list a few apps, but there is no official index of all the apps with SharePlay integration. That's where we come in.

Just like cash, bitcoin is used for everything from regular day-to-day business to criminal activities. However, unlike physical cash, the blockchain is permanent and immutable, which means anyone from a teen to the US government can follow every single transaction you make without you even knowing about it. However, there are ways to add layers of anonymity to your bitcoin transactions.

Apple released iOS 13.4.1 to the public on April 7 but also pushed out the update for the new second-generation iPhone SE model on April 23, one day before the device's official release. The update fixes a FaceTime bug and Bluetooth quick action failure that appeared in iOS 13.4.

Call Screen is one of best features on Pixel phones. With one button, you can screen calls using Google Assistant and avoid pesky spam callers. However, after the call, there is seemingly no way to access the transcripts for future review. Fortunately, there is a way, but it is tucked away.

Recently, buzz for the Google Pixel 4 has been rising thanks to a patent discovered by 91mobiles. This patent appears to show an almost bezel-less phone with a screen-to-body ratio we have only dreamt of, and no notch in sight. The problem is this isn't the Google Pixel 4. It's actually the Pixel 2 XL.

In an SEC filing published on Monday, Snap, the company behind Snapchat, disclosed that Imran Khan, its chief strategy officer and a member of the NR30, is leaving the company to "pursue other opportunities."

The gig economy is thriving, and if you aren't already making money with your phone, you could be missing out on easy residual income. Some people just want extra cash, and some even manage to completely ditch the 9–5, enabling them to work at their own pace and set their own hours.

A controversial video from Magic Leap's past has once again surfaced, but this time it comes with a lot more credibility and a good bit of excitement around the Magic Leap One headset.