Welcome back, my aspiring hackers! Those of you who use Windows in a LAN environment understand that Windows machines can share directories, files, printers, etc. using "shares." This protocol dates back to the 1980s when the then dominant computer firm, IBM, developed a way for computers to communicate over the LAN by just using computer names rather than MAC or IP addresses.

Eating healthy poses a challenge nowadays with so many options that taste great but aren't really good for you. Nutritionists have made it their life's work to understand what actually does a body good. Here's how you can follow their example.

Welcome back, my novice hackers! Reconnaissance is one of the most important preparatory steps to hacking. As I have emphasized many times before here on Null Byte, you must know the operating system, the ports, the services, the applications, and sometimes even the language of the target to be effective. If you haven't taken the time to gather this info, then you are likely wasting your time.

Without a comprehensive root method for all Android phones and tablets, a device-specific approach is needed. And since we always cover new rooting methods for all the popular phones here at Gadget Hacks, we've built this always-updated guide to rooting many mainstream Android devices.

If you're anything like me, every time you travel you end up in a desperate panic for a decent W-Fi connection. Whether you want to post your photos, research the best beaches, or kill time during an overnight layover, a hotel's Wi-Fi quality is of paramount significance in making a reservation.

Welcome back, my hacker apprentices! Last week, I started off my password cracking series with an introduction on the principles and technologies involved in the art of cracking passwords. In past guides, I showed some specific tools and techniques for cracking Windows, online, Wi-Fi, Linux, and even SNMP passwords. This series is intended to help you hone your skills in each of these areas and expand into some, as yet, untouched areas.

When OS X Yosemite was first announced, there were a number of features that struck my attention, but one in particular that stood out above them all was the ability to make and receive texts and phone calls from your Mac, which Apple calls Continuity.

Welcome back, my tenderfoot hackers! We have looked at a number of ways that we sniff traffic on the network with such tools as Wireshark, tcpdump, dnsiff, and others, but each of these tools is only capable of pulling packets off the wire.

We've all been there. Stranded in a large lot or parking garage, braving the rows upon rows of identical cars in an endless concrete landscape because, for the very life of us, we can't remember where we stashed the very ride that brought us there.

Nintendo fans rejoice! Not only can you play classic NES games on your iPad or iPhone without jailbreaking, you can play Game Boy Advance and Game Boy Color games. And that's not it. Now, thanks to @angelXwind, we can add Nintendo DS to our list of non-jailbreak emulators for iOS 7.

Welcome back, my novice hackers! We've done a number of tutorials using one of my favorite hacking tools, Metasploit. In each of them, we've used the msfconsole, which can be reached through either the menu system or through simply typing "msfconsole" from the terminal.

The flexibility within Android is pretty amazing. Unlike iOS, you can make a lot of modifications with nothing more than a download from Google Play, but to really step up your softModder game, you'll need to go a little further.

If you're marginally inclined towards computers, you've probably been approached at some point by a family member who wants you to "fix" their system during a visit home. With the holidays coming up, these opportunities (or ambushes) are even more likely.

You probably already know what you want to do when you grab your phone. More than likely, you're either going to make a call, send a text, or open an app. So why can't you just do that right from your Samsung Galaxy S3's lock screen?

It may not be as large as the Samsung Galaxy Note 2, but the Galaxy S3's screen size is still big enough to make iPhone owners cry themselves to sleep. The 4.8-inch AMOLED display with 720 x 1280 pixels makes the GS3 a great mobile companion—and an even better portable gaming device.

You'd think the ability to block calls from certain numbers would be built in to most phones by now, but that's certainly not the case with the iPhone.

I love surprises. Surprise parties, surprise visits, surprise Patrick... But there are times when a surprise is the last thing you want, like reaching into your pocket to find that your Samsung Galaxy S3 is not where it should be.

Welcome back, my rookie hackers! Several of you have written me asking about where they can find the latest hacks, exploits, and vulnerabilities. In response, I offer you this first in a series of tutorials on finding hacks, exploits, and vulnerabilities. First up: Microsoft Security Bulletins.

Welcome back, my neophyte hackers! Several of you have written me asking how to crack passwords. The answer, in part, depends upon whether you have physical access to the computer, what operating system you are running, and how strong the passwords are.

Smartphones are great. They help you keep in touch with your loved ones and stay up to date on what's going on in the world. The problem is that like everything else that's useful, they cost money to use, and between calling, texting, and data plans, it can get really expensive.

Every Windows system includes command prompt; and while a lot of people on Null Byte and WonderHowTo in general know how to use it, some people don't know anything about it, even how to access it.

Yes, boys. It’s true. It’s here. IT’S FOR REAL!! I am here to provide a list of things that boys should do (meaning they don’t do these things very often, probably why us girls think it’s adorable when they do) when they are pursuing one of us lovely ladies. There is a lot more to making her fall for you than you think, and yes, it’s the little things. The opened doors, the little touches, the tiny encouragements. Those are the things that matter. So here we go...

Caller ID is great to have, but there are certain situations where you don't want the person you're calling to have your number. People who sometimes use their personal phones for work may not want clients knowing where to reach them outside of work, and anytime you're dealing with Craigslist, it's better to be safe than sorry.

When a phone has only one main button, it can be pretty frustrating when that one button doesn't really work anymore. If you have an iPhone 4 or 4S, you know exactly what I'm talking about. Yep, the Home button, which is prone to unresponsiveness and lag. Most users blame the Home button issues on either dirt, moisture, or misalignment. No matter what the reason, having a busted Home button sucks, especially for those of you no longer under warranty. But that's okay, because there are a few t...

Steampunk music is an oft-debated genre, full of bands playing all sorts of different sounds. While this can make it difficult to generalize about the genre as a whole, it means that the average person is bound to like at least some Steampunk bands. That's why it's a great idea to support some independent Steampunk bands this holiday season by buying their music for yourself, or sharing it with someone else.

Serve your friends and family turkey this year in a nontraditional way by baking and decorating these turkey cupcakes. Turning ordinary and very blah chocolate cupcakes into feathered birds requires only some chocolate icing, candy corn, and sprinkles.

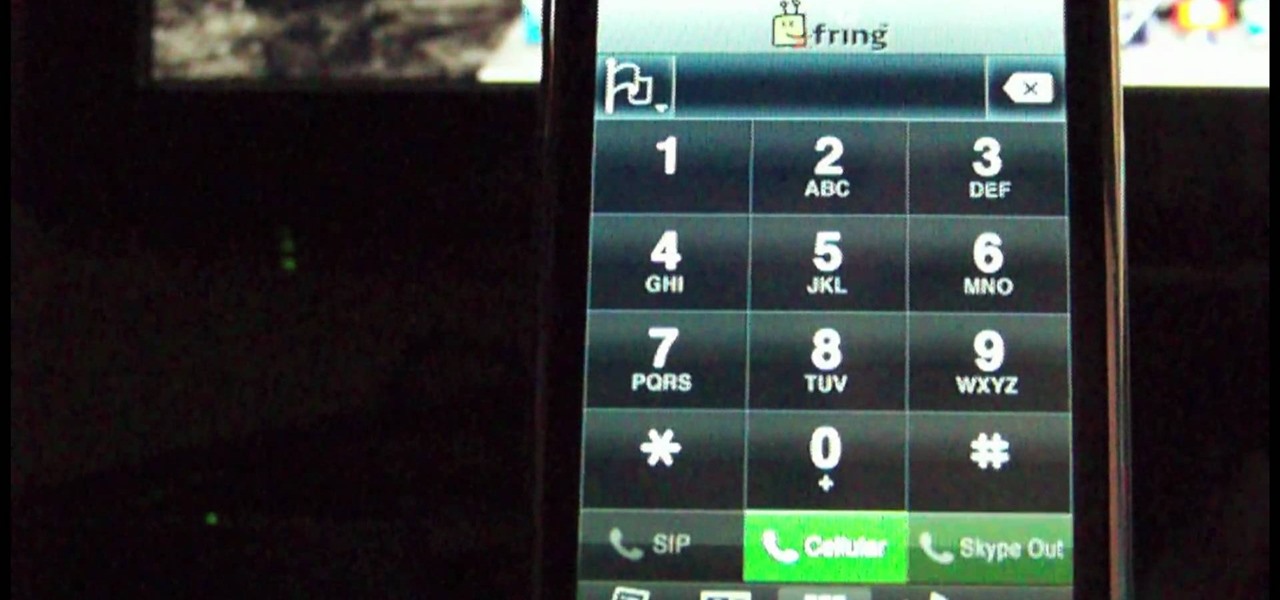
There are two ways to use iPod to make international calls that you should think about, when you are using your iPod Touch. One method is a free method. The other method is an inexpensive one. You will need to down load the "fring" app. If you haven't already done so, you will need to download the SIP service.

Thanks to "Mean Girls," we now know that Halloween is the only time you can dress like a slut and get away with it. Which means that if your concept of a witch costume still includes a crooked nose, warts, and a green face, then you're living way in the past, honey. Blast forward to the future—and the sexier side of things—by dressing up as a sexy witch this Halloween.

In order to block websites on your computer, you will need the address for the website that you want to block. Gather that information first. Then, click on Start. Then, go to Run. Next, type in the following: c://windows/system32/drivers/etc. Click OK.

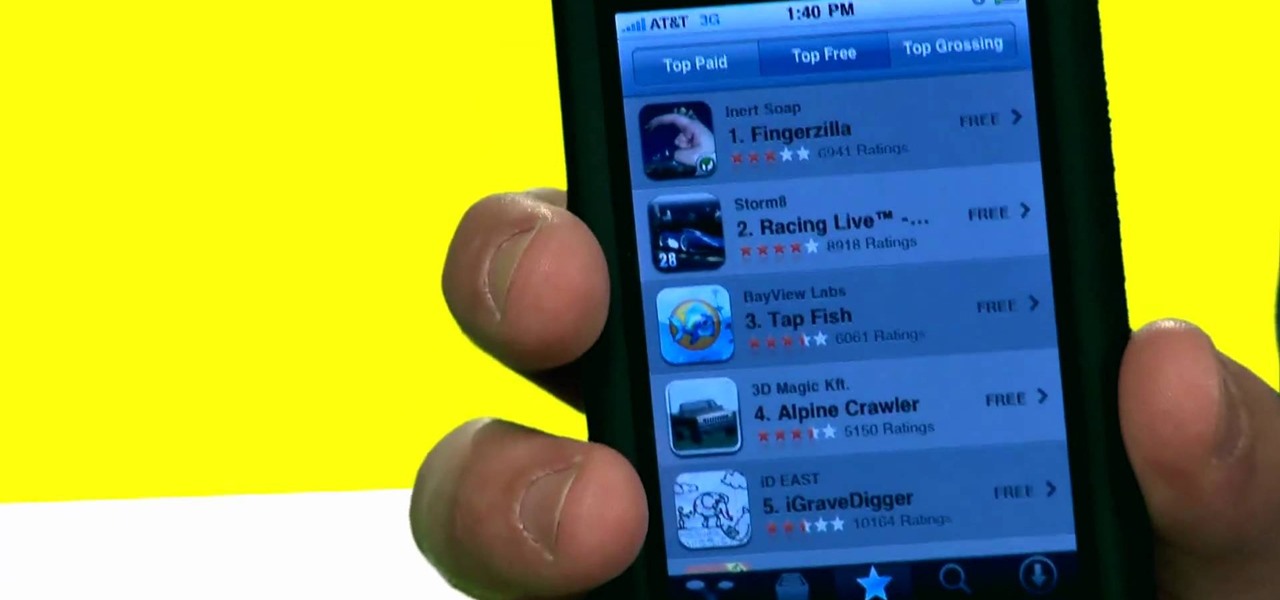
There's a ton of great applications you can buy and download for your iPhone, even your iPod Touch, and they're all at the tip of your finger (literally), right there in the Apple App Store. So how do you actually get one of those apps on your iPhone? Best Buy has answers. The Best Buy Mobile team explains how simple it is to download apps from the App Store on the Apple iPhone.

If you have ever found yourself working on a car project at your home and ran out of fuses, this tutorial is for you. Instead of going out and paying around $30 to $40, make your very own. It's wasy and saves you time and money.

This video tutorial from izbyfl shows how install Google Chrome and enable its plugins in Ubuntu. First download application from here: http://www.google.com/chrome/intl/en/eula_dev.html?dl=unstable_i386_deb.

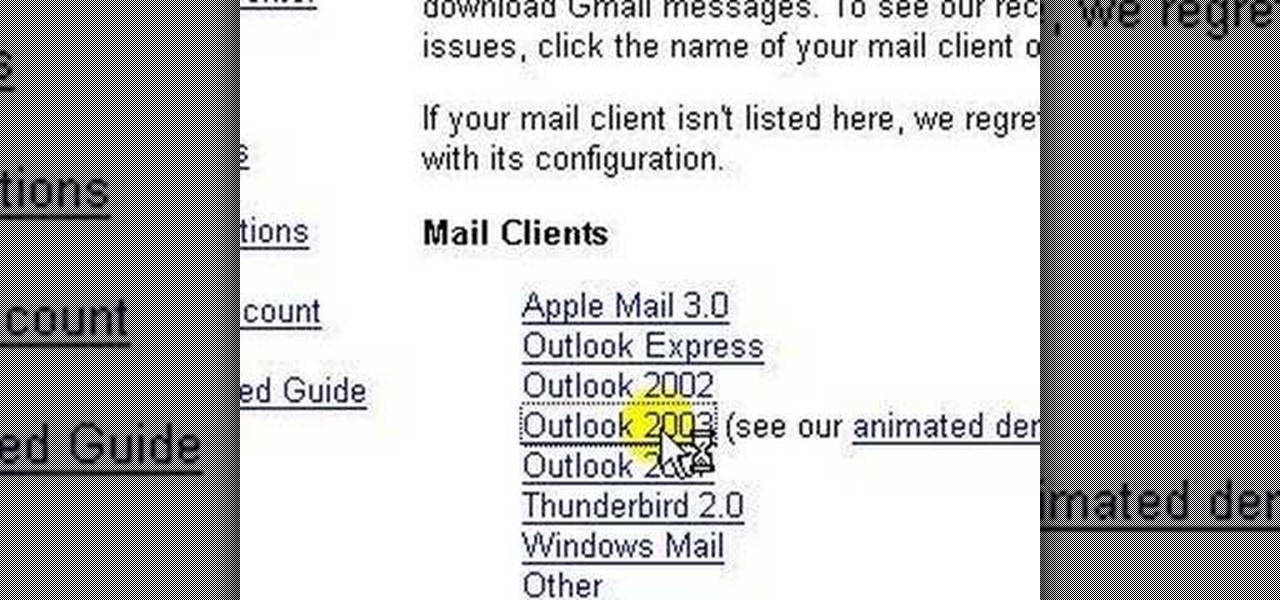
lakercoolman shows us how to set up our gmail account with this quick tutorial. Basically outlook express is a program that helps us to organize our email with added features such as contacts, to do lists and calender entries. Its an offline email client that allows us to work offline and also lets us set up exchange servers aswell. Ohter email servers such as hotmail and yahoo charge for thios service but the advantage of gmail is that IMAP or POP access is free. in ofer to set up, navigate ...

This video tutorial from adamstechvids shows how to resize photos in Windows using Picasa application.

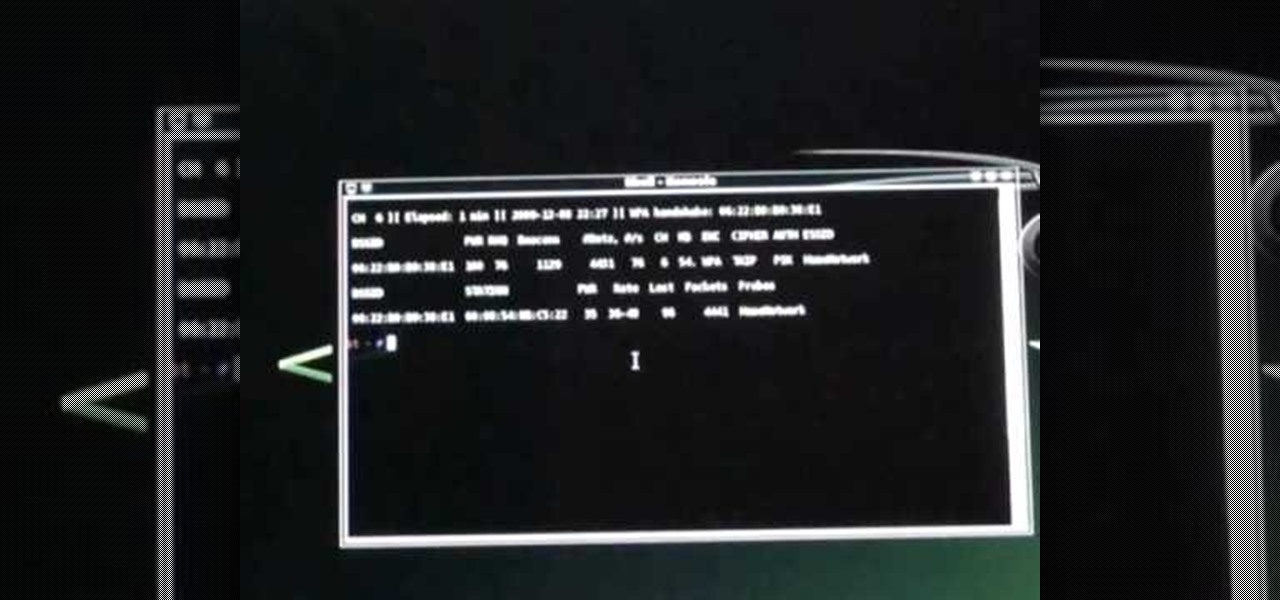
In this video we learn how to crack WPA using Back Track. The first step is the boot into Back Track using a VMware Virtual Machine Image. Next you need to open a shell console. In the console you will type "airmon-ng" and press enter. This does a check to find the wireless guard interface name. Next, type "airodump-ng wlan0" and press enter. This will tell it what wireless card to use and scan for wireless networks. You are looking for the one that comes up WPA. Copy the MAC address then typ...

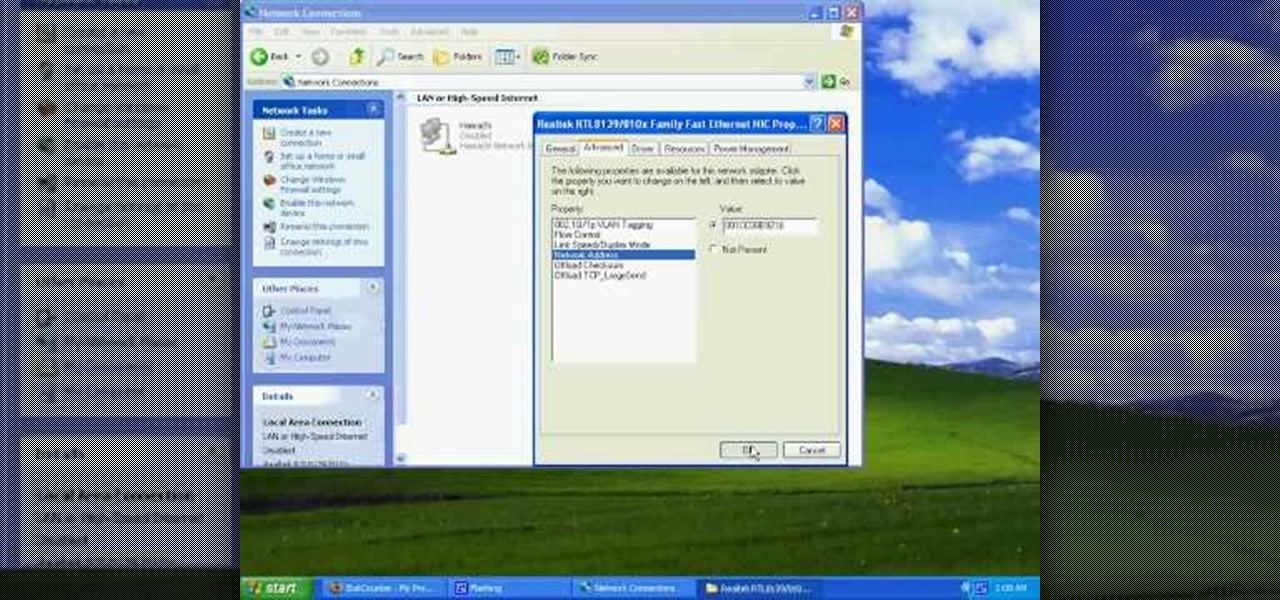
This video tutorial from tarunkumarsinghal shows how to change Mac address on Windows XP. Click Start menu and then Control Panel. Make sure control panel window is in classic view mode. If not, change it to classic from the left pane.

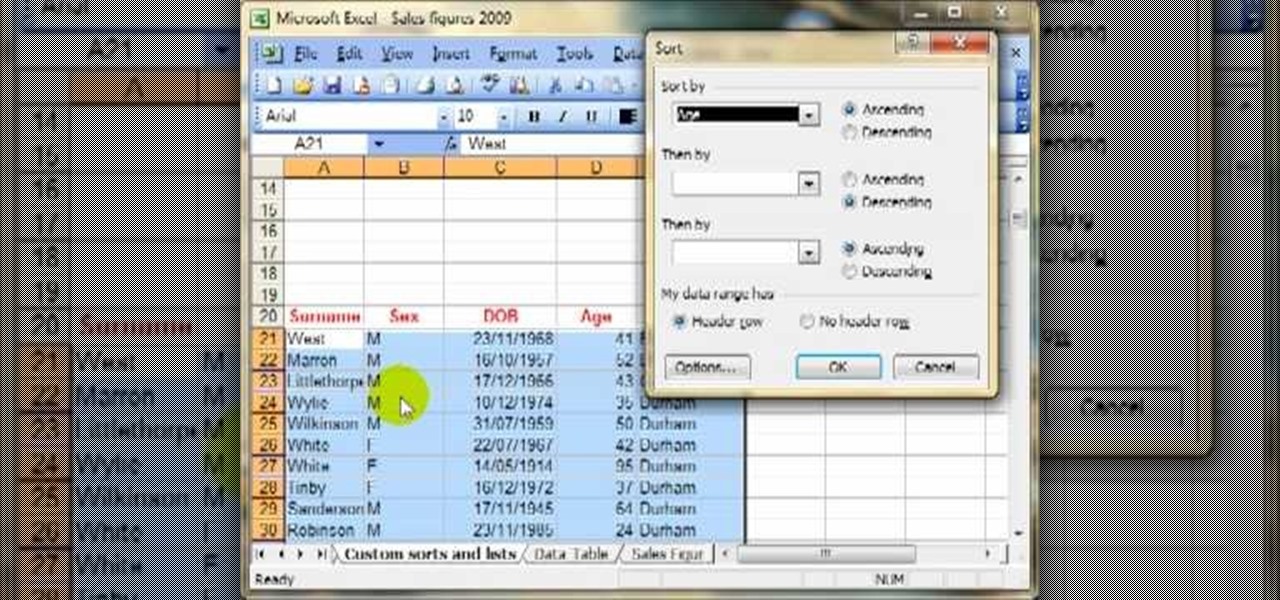
Today we are going to learn how to sort data in a Microsoft Excel 2003 spread sheet. We will go over single column and multiple column sorting. In a single column sort you may high light the data or just click on any cell in the column. Once the data is selected look for the sort icons just under the menu bars. There is a sort ascending and sort descending icon. Click on the icon and Excel will sort the list. When sorting multiple columns the data must be in columns next to each other. If the...

A lot of people fear bats; in fact, bats rank third on America's most feared list behind spiders and snakes. Most people get nervous around bats because they are hard to see at night and can fly around undetected; not to mention that Dracula myth that hasn't done bats any favors.

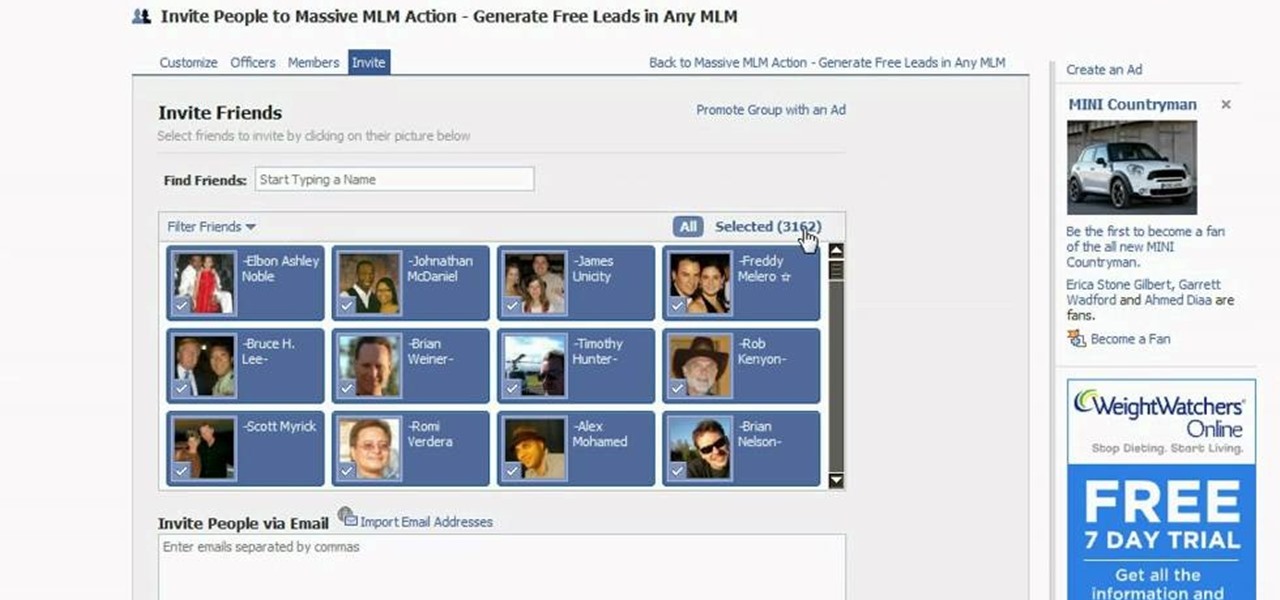
Do you have tons of friends on Facebook? Would you like to invite everyone you know to an event you are hosting or to try a product you are marketing? Normally to do this, you would need to select friends one at a time, reach Facebook's max invitee limit and then go in and do it again, and keep doing so until you get through your whole list. But what if you have hundreds of friends? This could take forever! Check out this tutorial and learn how to bypass Facebook's regulations and invite mass...