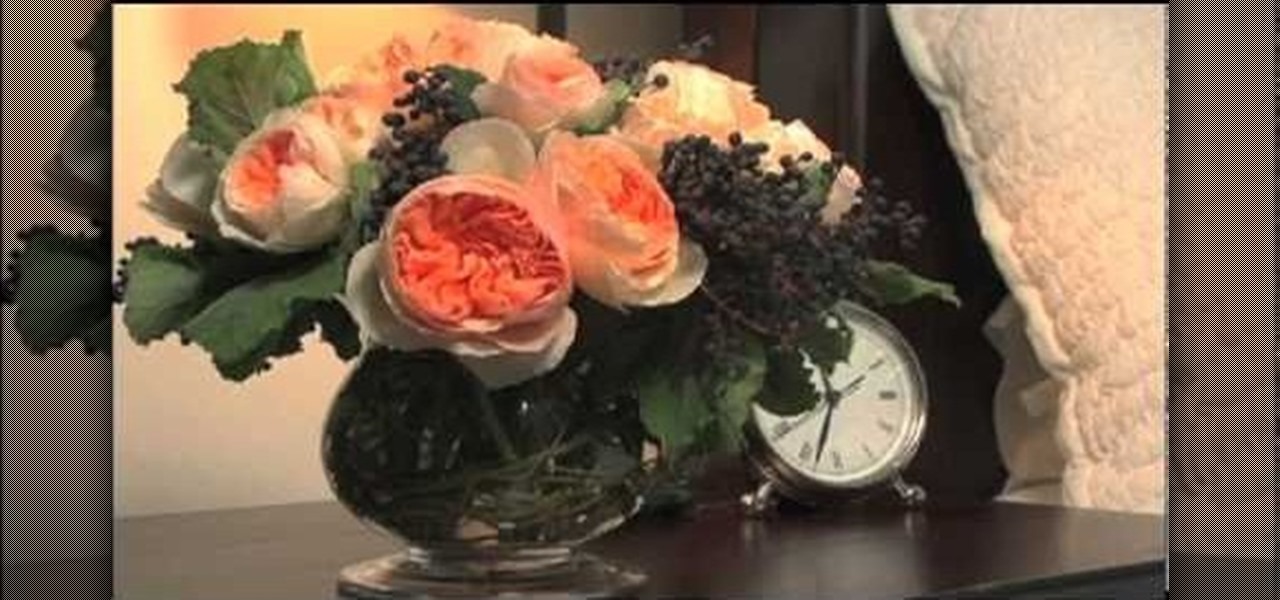In its goal to push the visual quality of real-time rendering to a new level, Unity is starting the new year off right by releasing a sneak peek at its upcoming interactive rendering improvements via a short, three-minute first-person interactive demo called "Book of the Dead."

Camera angles can be expressed in both physical and psychological terms. The first episode presents the physical angles: low-angle, high-angle, and dutch angle.
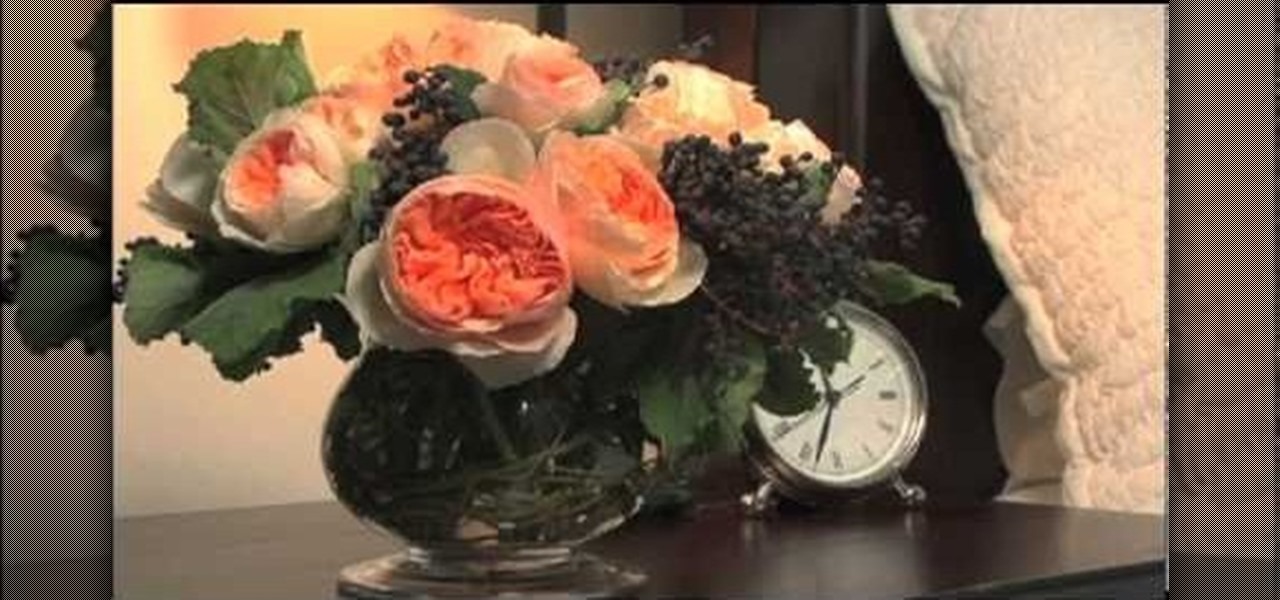
We know we're dead in the middle of winter and you probably have few thoughts about fields of wildflowers and the birds and bees (the literal ones). But what better way to take yourself out of your winter slumber than by thinking about how you'll adorn your house for spring?

Okay, so just to be clear, this is not a crochet tutorial for crocheting a stitch that resembles your new Blackberry Pearl (though, admittedly, that would be pretty damn awesome).

Show your father how much you love him this Father's Day by crafting a literal representation of your feelings. This cute and easy to make origami heart comes adorned on top with a handsome white tie, sending your father messages of thanks and kindness.

When we say gangsta chicks, we don't mean two streetsmart whores with baggy pants and chola eyebrows. Rather, this drawing tutorial presents a literal - and very humurous - interpretation of "gangsta chicks."

Tie loose ends together - in the literal and original sense sense of the phrase - by sewing together the ends and/or hems of your knitting projects like a pro. Whether you're fusing together two pieces of wool-knitted cloth to form the back of a beautiful winter sweater or just want to join patchwork knits into a rasta-cool beanie, knowing how to stick pieces together is integral for a tidy project.

Lady Gaga is the queen of shock, and what better way to jolt the public than with a literal lightning bolt? Lady Gaga seldom repeats a look, but she's stood by her favorites, including a Minnie Mouse inspired hair bow and the black and pink lightning bolt look presented in this video.

Any artist who excels enough in his profession will create some sort of signature on his painting to notify other it's his work. Some painters, like Jan van Eyck, are cryptic with their inscriptions, putting it in almost impossible to see areas in the painting, while others, like Chinese painters, put their literal stamp on paintings with a carved seal stamp.

This tube top is the literal way to transform your winter wardrobe into your spring/summer wardrobe. Using a bland turtleneck which you are sure to have in stock from all those Christmas presents from older relatives, you can create a breezy tube top that's perfect for going to the beach.

Okay, so just to be clear, this is not a crochet tutorial for crocheting a stitch that resembles your new Blackberry Pearl (though, admittedly, that would be pretty damn awesome).

A good video can turn a mediocre song into a smash hit, while a bad video. Well, that's just embarrassing. While MTV doesn't really play music anymore, the internet is flooded with good old fashioned music videos. This how-to video will offer some tips for making yours stand out of the crowd. You don't need to be too literal, but try picking a style. Watch this video tutorial and learn how to make a music video.

We know there are probably like 100,000 "Avatar" makeup tutorials on YouTube, but how often are you really going to wear a striped blue face out of the house unless it's Halloween? Skip the literal interpretation and don an "Avatar" look you can actually wear on the everyday by checking out this makeup tutorial.

How your fingernails and toenails look is very telling of how well you take care of yourself. Most girls remember their face, but when it comes to lower body parts it's easy to neglect taking care of them too.

Pompadours sound kind of, well, pompous, and look rather prosh. With a literal "I'm above you" upward beehive bump that towers over your own head and others, a pompadour is a hairstyle with 'tude, and while before people that it was too ostentatious to wear, starlets like Jennifer Lopez and Rachel McAdams have worn the style on the red carpet to much acclaim (and copycats).

For many, taking a bite out of a red velvet cupcake is a delicious treat, and even a present of sorts, especially if you generally deny yourself of such sweets during the rest of the week. So why not make your next batch of cupcakes look like literal gifts by adding a bow on top?

Are you a fan of Depeche Mode? This tutorial is designed to help you play "Enjoy the Silence" by Depeche Mode on the piano or keyboard. This song isn't taught in a literal or mechanical fashion but rather is taught to grasp the song's structural parameters & essence. This video will help you understand the body of "Enjoy the Silence" by Depeche Mode and enables you to make it your own. This how to video is for intermediate to advanced piano students. With this lesson you will be able to play ...

Are you a fan of Tori Amos? This tutorial is designed to help you play "Siren" from Great Expectations soundtrack by Tori Amos on the piano or keyboard. This song isn't taught in a literal or mechanical fashion but rather is taught to grasp the song's structural parameters & essence. This video will help you understand the body of "Siren" by Tori Amos and enables you to make it your own. This how to video is for intermediate to advanced piano students. With this lesson you will be able to pla...

This tutorial is designed to help you play "Landslide" by Stevie Nicks of Fleetwood Mac on the piano or keyboard. This song isn't taught in a literal or mechanical fashion but rather is taught to grasp the song's structural parameters & essence. This video will help you understand the body of "Landslide" by Stevie Nicks of Fleetwood Mac and enables you to make it your own. This how to video is for intermediate to advanced piano students. With this lesson you will be able to play Stevie Nicks'...

Some girls are designated as so hot they could "kill with a kiss," but with no woman is this designation so literal as Poison Ivy, whose plant toxin-filled lips kill any man she sets her puckers on.

Valentine's Day is almost here, and if you're like me, you're scurrying to do something special for your mate. The standard chocolates and flowers just isn't cutting it anymore, and you can only make so many homemade cards before it becomes banal and meaningless. So, what can you do that shows you put some work into it, while not breaking the bank?

You love to drink, but could do without the (literal!) headache. Imagine a world in which hangover prevention is actually possible! In this video, we'll teach you how to prevent a hangover, so you'll never waste another day post-drinking.

This tutorial is designed to help you play famous riffs by Bjork on the piano or keyboard. These songs aren't taught in a literal or mechanical fashion but rather is taught to grasp the song's structural parameters & essence. This video include riffs from Human Behaviour, Joga, Bachelorette, The Modern Things, Army of Me, It's Oh So Quiet, & Isobel. This how to video is for beginner to intermediate piano students. With this lesson you will be able to play famous riffs by Bjork on piano.

In this simple tutorial you will be shown step-by-step how to write local shellcode for use on 64-Bit Linux systems. Shellcode is simple code, usually written in assembly that is used as payload in exploits such as buffer overflow attacks. Payloads are the arrow head of an exploit: though the rest of the arrow is important for the delivery of the attack, the arrow head deals the killing blow. In reality, payloads are slightly less exciting yet far more interesting and intelligent than medieva...

Peeling apples is pure grunt work, especially if you have a recipe that calls for a lot of 'em, like apple pie. You can make this task go by much more quickly if you use something from your tool box—your literal tool box, that is.

The lovely Kato of Steampunk Couture has gone hardcore. For those who prefer to exercise their imaginations a bit more, Voila! Veronique Chevalier in Gearhearts Steampunk Glamour Revue- click here should do... A recent kerfuffle unfolded on facebook's Steampunk Revolution group when a discussion was started by Steampunk R &D''s very own Austin Serkin on the subject of Kato's new foray into steampunk porn, which was, ahem, examined in detail. (Well, figuratively, not literally, since her websi...

Modern warfare takes on a more literal translation with the advent of new augmented reality displays revealed recently by the US Army to improve soldiers' situational awareness on the battlefield.

It's been an exciting week for Tesla. First, Elon Musk offered a preview of the nearly complete Model 3, then China tech giant Tencent invested $1.78 billion in the company. Now, Tesla has officially updated its Autopilot software today for Tesla owners with Autopilot 2.0 hardware.

In many programs on Linux, you'll come across programs which allow you to specify additional arguments instead of just simply running the program by itself. If you've used the Kali distribution, I'm more than certain you'll have come across these with the command line tools, else if you have been following these tutorials, we have already come across three tools which also use the same technique, i.e. gcc, gdb and wc. How do we do this with C? Let's find out.

What's up guys! It's time to discuss strings in more detail. Review

Even the most unadventurous eaters can usually be coaxed to take a bite of an exotic fruit (except, perhaps, the notoriously stinky durian). After all, fruit is sweet, juicy, and filled with natural sugars.

Navigating through the darkness—literal darkness, not the existential variety—is always a difficult task on its own, and my Android doesn't necessarily make it any easier. Many manufacturers offer quick access to a flashlight or torch feature, but my Galaxy S4 doesn't have an easily accessible toggle or button available to turn it on.

With the announcement of Google Glass Enterprise Edition last week, a literal behemoth entered the arena of companies serving augmented reality solutions to business customers. While Google Glass, with the backing of Alphabet, has the potential to be a disruptor, the field already has a number of players who have been in the game.

A crick is a sudden, spasmodic pain and stiffness in the neck caused by tight muscles that can absolutely ruin your entire day. It can last for more than one day and can be triggered by the smallest movement of the neck, such as a simple pandiculation, aka a yawn-stretch. Although you can't always prevent them, there are many natural ways to lessen a painful stiff feeling in the neck.

It can be pretty tough to fall asleep when your brain is thinking nonstop or anxiety has gotten the best of you, and it seems to only get harder when you're lying in bed listening to yourself breathe. Yet paying attention to that breathing may be exactly what you need in order to find a calm, easy entry into a good night's rest.

Welcome back, my tenderfoot hackers! Hacker newbies have an inordinate fixation on password cracking. They believe that cracking the password is the only way to gain access to the target account and its privileges. If what we really want is access to a system or other resources, sometimes we can get it without a password. Good examples of this are replay attacks and MitM attacks. Neither requires us to have passwords to have access to the user's resources.

We've told you how a rice cooker can work as a DIY sous vide machine and make amazing risotto the lazy way, but did you know that it can also make pancakes, bread, mashed potatoes, and poached fruit?

There's no denying that adding more programming languages to your arsenal is crucial to boosting your career, but learning a new language in the literal sense is just as enriching and mentally stimulating. Not only will you be smarter — those who know more than one language are known to have better reasoning, problem-solving skills, and creativity — but it'll also open you up to more job opportunities.

We love standing around a barbecue with an icy cold beverage in hand, enjoying the delicious smell of smoky food and chit-chatting with pals. Grilling season — it's our favorite time of the year.

Greetings all. Before I get into the tutorial, I would like to mention that I am fairly new to Null Byte (been lurking for some time though), and what really appeals to me about this place is its tight, family-like community where everyone is always willing to help each other and the constant search for knowledge that inhabits this subdomain is a driving motivator for me to join in. I'm glad I arrived at the right time. Anyway, wipes tears (not really)...