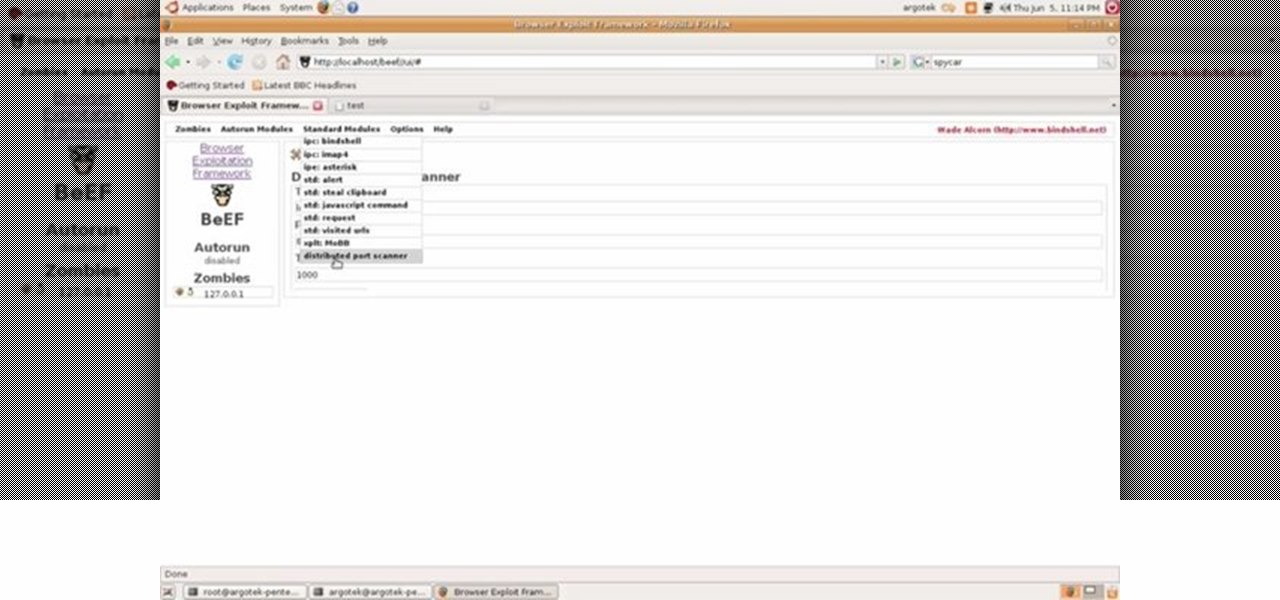
This video tutorial talks about browser exploitation. Particularly, it talks about tools, like BeEF, that can be used to hack known vulnerabilities within browsers and some cool frameworks that you can use to check the security of your own browser. To get started hacking your own browser, watch this how-to.

What better way to end a perfect day than by learning how to play one of your favorite songs? In this free video keyboard lesson, you'll learn how to play Lou Reed's "Perfect Day" on the piano. While this lesson is geared toward intermediate players, beginners are certain to take something away as well. Watch this tutorial to get started playing "Perfect Day" by Lou Reed!

Ever wanted to solo over the chord progression from Carlos Santana's "Samba Pa Ti" on your ukulele? Who hasn't, right? This ukulele lesson presents a quick overview of a highly adaptable G scale pattern that works over the progression in Carlos' Santana's "Samba Pa Ti." For more information, or to get started soloing over Santana's "Samba Pa Ti" on your own ukulele, take a look.

This video lesson covers a basic bossa nova rhythm pattern for the guitar player interested in learning Brazilian music.

New to the guitar? You needn't sound that way. This video tutorial demonstrates a simple twelve-bar blues progression focusing on the C7 chord shape. To get started playing this three-chord C7 progression on your own guitar, take a look!

In this short how-to video, self-described earth mother Mayo Underwood demonstrates how you can germinate seeds in damp paper towels prior to planting them in your personal garden. Watch this tutorial and start some seeds of your own today!

Learn how to do speed tube shoulder presses. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do alternate dumbbell swims and dumbbell cross punches. Presented by Real Jock Gay Fitness Health & Life.

Squats are probably the most useful exercise you can do at the gym—no other single exercise encourages more muscle growth. With a range of motion that incorporates many different muscle groups in the legs, core and upper body, squats strengthen not only those muscles, but also the tendons and ligaments that connect them. In addition to their strength-building benefits, squats also teach you core stabilization, which is important for almost any athletic endeavor. Learn how to do barbell squats...

Learn how to do single-leg flat bench standups and sculpt your body without weights! Presented by Real Jock Gay Fitness Health & Life.

Learn how to do dumbbell fly to presses. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do flat bench leg lifts. Presented by Real Jock Gay Fitness Health & Life. Benefits

Save tons of money by building your own LED pen that works with a multitouch smart board / whiteboard. You'll also need a WiiMote (Wii Remote) to use in conjunction with your homemade LED pens that you'll be making in this video. To get started with this awesome project, you'll need a 1.5 volt tolerant infrared LED, momentary push button switch, AA-battery case holder, one AA battery, containment unit (Sharpie marker or highlighter body), pliers, superglue, thin copper wire and a soldering iron.

Kevin Rose is joined by John Todd, a well known, leading Asterisk expert, to introduce you to the amazing VoIP (Voice over IP) world of Asterisk, the open source voip telephony toolkit. In this episode, Kevin and John take you through the installation and configuration of this powerful tool, and show how it can be used to give anyone complete control over their phone experiences, such as voice over wifi, eliminating phone costs, choosing from hundreds of VoIP providers, creating your own voic...

Check out this how-to video and learn how to build a SAFE hydrogen generator. Be sure that you test volts vs. amps for safety reasons! Follow along with this instructional video, and start making some sweet, sweet hydrogen.

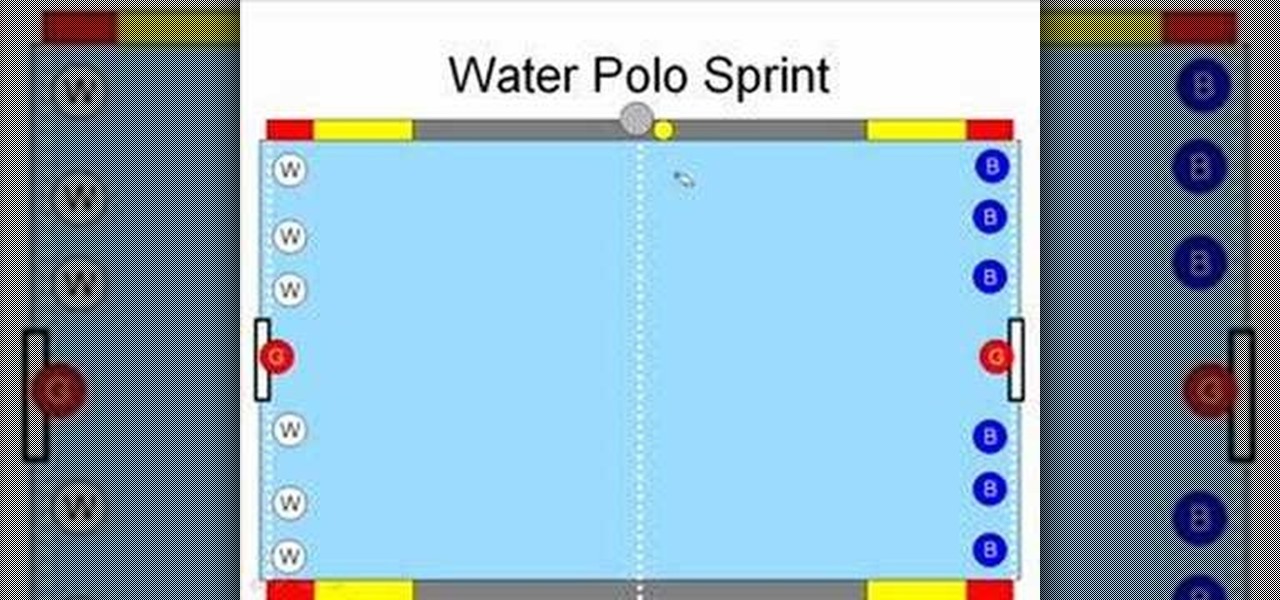
This is basic lesson and moving diagram showing the start of a water polo game, known as the sprint.

Superbike Magazine starts with the roll on power wheelie. They talk about weight balance, throttle control, slipping the clutch and coming down on a lunge when pulling wheelie stunts on a motorcycle.

The native timer feature on your iPhone works well enough that you probably haven't even thought about installing a third-party timer. With just a few taps, you can get a countdown for any amount of time up to 24 hours (or one second shy of 24 hours, to be precise). But as fast as it can be to set a timer from the Clock app, there are even faster ways to start the countdown.

Over half of all Americans have listened to at least one podcast, and that number is growing every year. With over one million podcasts and 30 million episodes in existence, there's no end to discovering new voices expounding on a range of topics.

As a meeting host on Zoom, you can't control what a participant does during your live video call, but you do have the power to turn off their camera so that other people aren't subjected to distractions. So if you catch someone in your call purposely making obscene gestures or accidentally exposing themselves while using the bathroom, you can block their camera, as long as you know how.

Chance are, you or someone you know is that person in the gym: flexing in front of a mirror, posing for the perfect photos to show off your workout results. But finding the right picture is hard. The thing is, it doesn't need to be.

If you record yourself for a vlog or story post using your selfie camera, it can be challenging to stay on message. You might worry too much about the way you look or sound to focus on what you want to say. Using a script can help, but looking away from the camera to read is unprofessional, even on social platforms like Instagram. What you need is a teleprompter, and there are apps for that.

For years, Skype has been synonymous with video calling and messaging. However, as the industry moved toward encryption and privacy, Skype usage was discouraged by experts due to its murky encryption. To combat this, Skype has introduced true end-to-end encryption.

Front and center for iOS 12 this year is Group FaceTime, which allows users to chat with up to 31 additional people at once. While that ambitious feature is sadly delayed, don't cast away FaceTime just yet — you can always pick up your iPhone and start a call with any single contact directly from the Messages app.

The app that started as simply a photo-sharing social media platform has expanded to encompass so much more than that. Between live videos, stories, chat, and animated stickers, Instagram is more than the sum of its pictures. Now, there's a new feature to add to that list for Android and iOS — video and audio calls.

So after being teased last Christmas with an email promising that the Meta 2 was shipping, nearly a year later, we finally have one of the units that we ordered. Without a moment's hesitation, I tore the package open, set the device up, and started working with it.

While the iMovie application for Mac has a few more bells and whistles, Apple's mobile version of its video-editing program is jam-packed full of features and more intuitive than its big brother. Still, before you dive right in to become a movie editor on your iPhone, it's good to know the basics first.

Thanks to live-streaming video and social media apps like Facebook, Instagram, and Snapchat, we're all on camera nowadays. Unfortunately, though, we don't have a script to work with when we're shooting selfie videos, so it's hard to come off as perfectly eloquent when you're just freestyling off the top of your head.

If you've ever been inspired to try out 3D modeling after enjoying computer-generated imagery in video games and movies, chances are you've checked out an paid applications like 3ds Max (previously called 3D Studio Max), or even free ones like Blender, then just went "No Way! It's way too complicated."

Many new developers are diving right into the Microsoft HoloLens, but augmented and mixed reality are fairly big subjects in terms of learning. There's a lot to cover and, unfortunately, very few places for someone brand new to Windows Holographic to begin lessons.

This guide is written for anyone who is practicing his penetration skills using the Metasploitable 2. The problem that we are facing here is that we have to penetrate to Metasploitable 2 and when this happens we understand that we are not logged in as root but as a user with less privileges!

Welcome back, my budding hackers! In this series, I have been trying to familiarize you with the many features of the world's best framework for exploitation, hacking, and pentesting, Metasploit. There are so many features, and techniques for using those features, that few pentesters/hackers are aware of all of them.

Right, So i've been asking alot of questions here on Null-Byte and everyone has been really helpful to me.

Welcome back, everyone. In the previous part of this rapid-fire miniseries, we built the victim portion of the shell. Today, we'll be building the attacker portion. This script will initialize interaction with the victim portion of the shell, send commands, and receive the output.

Cord cutters are changing everything about TV—the more of us that sever ties with cable, the more changes we start to see. In fact, viewing habits have already changed so drastically that waiting a week to see the next episode in a series is no longer acceptable, as binge watching has completely eclipsed this old-fashioned format.

I'm back. School's an ass. On my quest for knowledge, which started approximately 3 years ago, I can upon an interesting little artifact. It is called the Arduino.

When I started to go to this site I found it fascinating and found myself coming here all day I have used a lot of the info I have gotten from here in my professional career and on my own. I currently am the VP of RND for a small IT company. I have been pushing toward Penetration Testing as a service for our clients and future clients. For the past 10 years here it has been a very long uphill battle and have hit a lot of road blocks. So I decided to work on this on my own of course as soon as...

Recently, I've been experimenting with BeEF (Browser Exploitation Framework), and to say the least, I'm hooked. When using BeEF, you must "hook" the victims browser. This means that you must run the script provided by BeEF, which is titled "hook.js", in the victims browser. Once you've done that, you can run commands against the victims browser and cause all kinds of mayhem. Among these commands, there is an option to use the victims webcam. This is what we'll be doing here today, so, let's g...

Welcome back, my fledgling hackers! Let's continue to expand our knowledge of digital forensics, to provide you the skills necessary to be a digital forensic analyst or investigator, as well make you a better hacker overall. In your attempts to enter a system or network undetected, it is key to understand what a skilled forensic investigator can learn about you, the alleged hacker.

Welcome back, my rookie hackers! In my ongoing attempts to familiarize aspiring hackers with Linux (nearly all hacking is done with Linux, and here's why every hacker should know and use it), I want to address a rather obscure, but powerful process. There is one super process that is called inetd or xinetd or rlinetd. I know, I know... that's confusing, but bear with me.