In our society, multitasking is an obsession. Whether it's driving while using your phone (DON'T DO IT) or drinking a cup of coffee while typing up some work, we multitask at every turn of the day. People that work all day in front of a computer are especially prone to multitasking, and that's why XDA-Developers member Floyd1973 has developed a way to control any Android phone while connected via USB to a Windows or Linux PC. Android Remote Phone Tools
Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private chat without clicking the link. Canary tokens come in several useful types and can be used even through URL shorteners.

It's always a good idea to know how an attack works at the very basic level. Manual techniques for exploitation often find holes that even the most sophisticated tool cannot. Sometimes, though, using one of these tools can make things so much easier, especially if one has a solid foundation of how it works. One such tool can help us perform a cross-site request forgery with minimal difficulty.

Web 2.0 technology has provided a convenient way to post videos online, keep up with old friends on social media, and even bank from the comfort of your web browser. But when applications are poorly designed or incorrectly configured, certain flaws can be exploited. One such flaw, known as CSRF, allows an attacker to use a legitimate user's session to execute unauthorized requests to the server.

It won't come as a surprise to hear that your cell phone, tablet, and laptop are loaded with bacteria and other organic material. While most of these bacteria are harmless, there are good reasons to reduce the capability of your mobile devices to infect you—or other people.

My husband's and my daily schedules are constantly changing. Frankly, it's complete chaos sometimes, so I can't plan to have elaborate dinners on the table at six o'clock every day. And by the time we actually get to eating in the evening, we've become so hungry that our moods have taken a nosedive.

1A Auto shows you how to repair, install , fix, change or replace your front struts with their loaded struts. This video is applicable the 01, 02, 03, 04, 05 Honda Civic

Apple hates game emulators. Go ahead, look around in the iOS App Store, you won't find any. But who needs 'em anyway?

Removing and replacing the brushes in your DeWalt power drill doesn't have to be a costly repair. You can do it yourself, and it doesn't require a lot of time or effort. Simply unscrew and take the casing off your corded DeWalt power drill to expose the brushes. The model in the video has spring-loaded brush holders. It's as simple as taking the old ones out, and dropping the new brushes in. Learn from a pro to efficiently and correctly restore the brushes in your corded drill.

Websupergoo demonstrates how to edit PDF files with the Infix PDF editor. Infix can replace an existing image with another image loaded from a file. To accomplish this, use the object select tool and choose the image for the replacement. The clipping mask is denoted by a pink border and will be retained and applied to the image that you would like to replace. Select the replacement by choosing the replace object option. Next, choose the replacement image from your computer files. After you re...

If you want to beat the worlds hardest game in a few seconds this is for you. The first step is to load the worlds hardest game. After the game is loaded right click on the pane and scroll down to the settings tab. Select the settings tab. After the setting tab is selected click the picture of the microphone located in the window pane. After this right click on the arrow using your mouse. To make this work loop and play must be ticked. After the game scrolls through all of the levels click th...

This video is a report by Terry from Good housing keeping. She reports that women of any age should be thinking of bone health and one of the best ways to strengthen your bones experts say is to follow low fat Mediterranean diet.

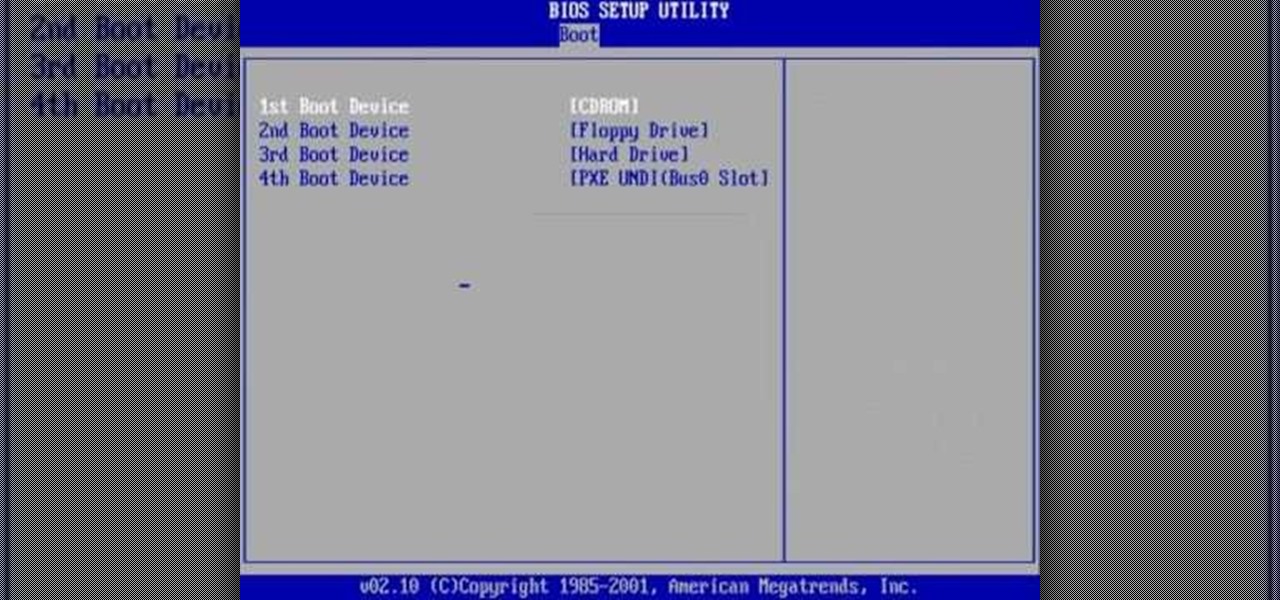
The video shows users how to change the boot sequence in a computer with an older AMI (American Megatrends, Inc.) BIOS to boot from the CD/DVD drive. This is required, for instance, if you need to reinstall an operating system, or fix a corrupted windows installation by running Windows Setup from the installation CD. Users should first enter the BIOS setup by pressing the delete key when prompted shortly after powering the computer on. Once the Bios Setup screen has loaded, users may navigate...

The internet is saturated with low-quality pictures, making it difficult to find a high-resolution image for specific albums, TV shows, movies, podcasts, music videos, apps, and books. Apple uses high-quality images, but it seems impossible to download cover art, posters, thumbnails, icons, and other images from within its apps on your iPhone. Now, with the help of a shortcut, it's as simple as can be.

Google's "Go" line of apps are lightweight counterparts designed to be limited speedy alternatives to their full-featured sibling apps. There is a Go version of Photos, Search, Maps, and more — but are they the right apps for you?

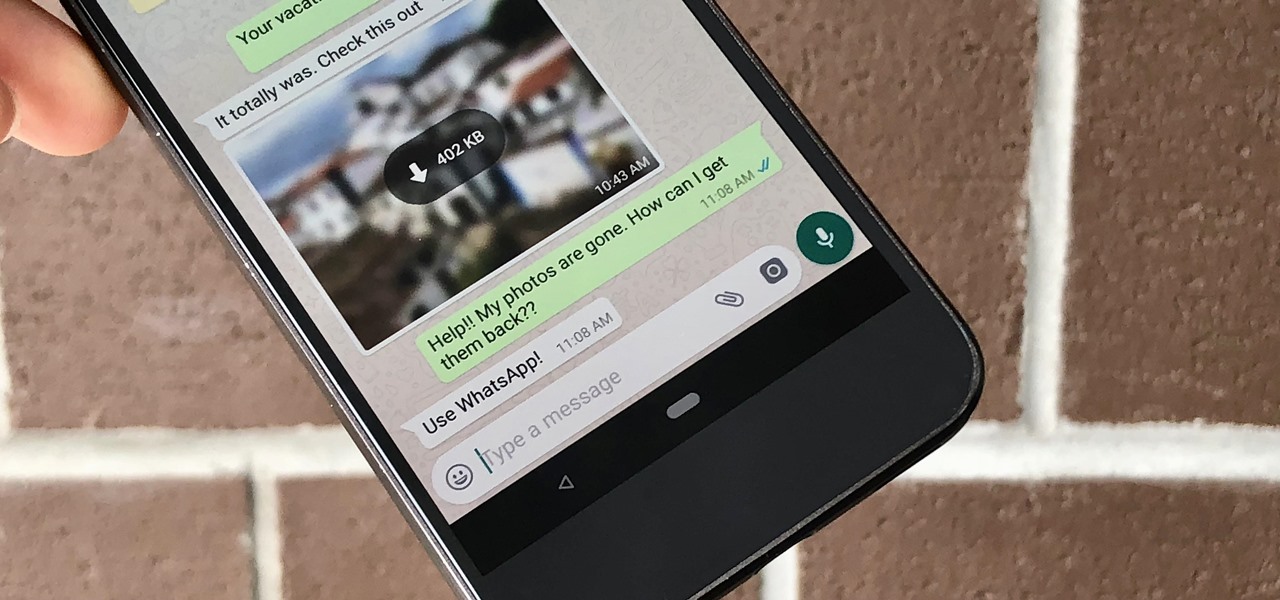
Thanks to cloud storage's increasing accessibility, permanently losing photos is becoming less and less common. Still, if you accidentally delete a picture from your smartphone without first making a backup of some sort, that data is pretty much toast — unless we're talking about photos from WhatsApp.

Soon all Android users will be able to use Samsung's cool Soundcamp app to write and record music. The announcement was made at the Samsung Developer Conference 2016, stating that the app, which was released last year for Samsung devices only, will become available to all phones and tablets running Android 5.0 or higher very soon.

Welcome back, my novice hackers! As most of you know by now, a notorious commercial, legal hacking group named "Hacking Team" was recently hacked. As part of the hack, thousands of emails and other material on their servers was divulged. Among the material released were three zero-day exploits. In this tutorial, we will walk through the steps to load one of them, which has become known as the CVE-2015-5119 exploit.

Some of my favorite games include Super Mario World, Super Mario Kart, Super Punch Out, and Super Metroid. If you still haven't caught on, I'm a big Super Nintendo fan. Growing up in the '90s meant spending Saturday mornings engulfed in front on my TV with the good old SNES running hard.

In this how to video, you will learn how to use the Nerf Gun Long Shot. First, you will need to know about the magazine. These can hold 8 shots and are spring loaded. Do not load 8 shots, as it will jam. Instead, load 6 shots to prevent this. The shots can be used in other guns, but the Long Shot magazine can only use this shots. The holes in the shots make a whistling sound. If you get shot, you will feel it regardless of distance. The gun has a trigger, a mount, a quick grab design, a hidde...

This is part 1 of 2 on how to complete the Takedown mission and get the Tag Em And Bag Em achievement. The Tag Em And Bag Em achievement is earned by completing the Takedown mission, so check out this video if you want to see how to complete this level.

Hacking RC is easy with Piaps Restaurant City Hack! Restaurant City is a Facebook game that allows you to create your own restaurant. Watch this video tutorial to learn how to cheat Restaurant City with Piaip's Hack (11/08/09). See how to download, install and run Piap's Restaurant City Hack v.1.13 or 1.12.

The tools required for this project are: an electric hand drill, a drill bit of the appropriate size and goggles to protect the eyes from falling debris. You will also need a ceiling hook kit, available in most major home stores. In the kit, there is a hook; a spring-loaded anchor; a threaded shank or screw, which is threaded on both ends; and another threaded shank or screw, which is threaded on one side and has screw thread on the other side for wood installation. To install in a sheetrock ...

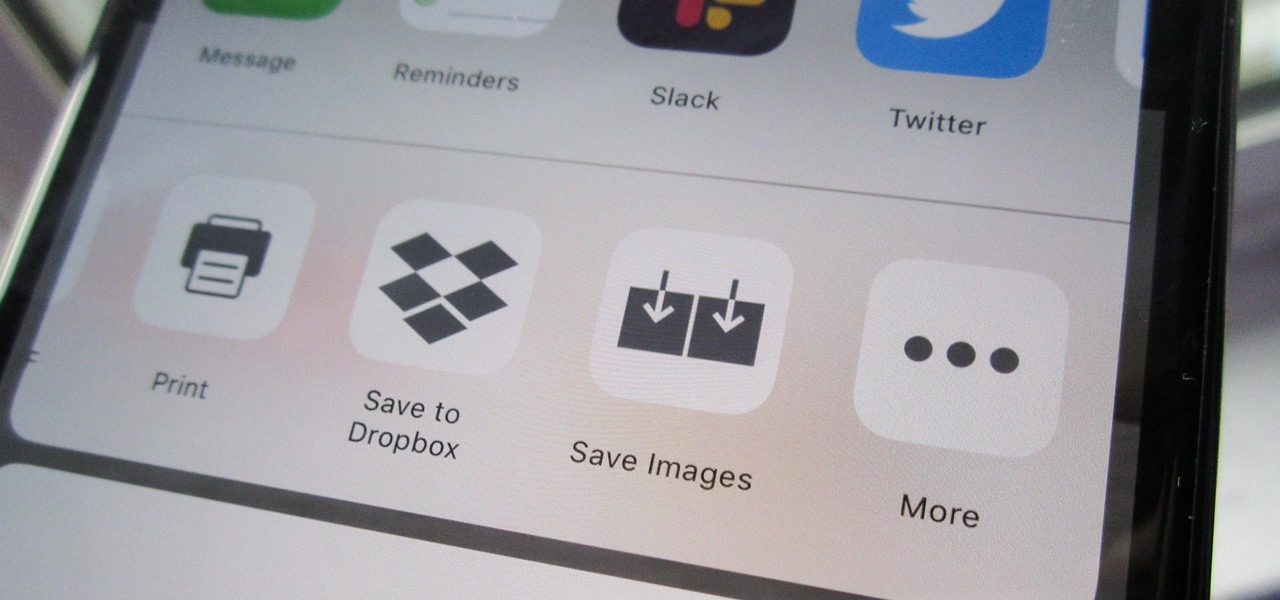
Some websites block image downloads on their webpages so you can't save them for reuse. That means long-pressing or force-pressing on protected images in Safari on your iPhone will not do anything or will omit the "Save Image" option. Taking a screenshot is the obvious solution to bypass restrictions, but you won't get the best quality. Thankfully, there's another way.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

Hackers often rely on lazy system admins and unpatched vulnerabilities to get access to a host. Keeping intruders off of our machines requires us to update daily, only run the services we need, and read the code, among other things, but we can still make mistakes. Luckily for us, we can limit the damage caused by those mistakes by running SELinux.

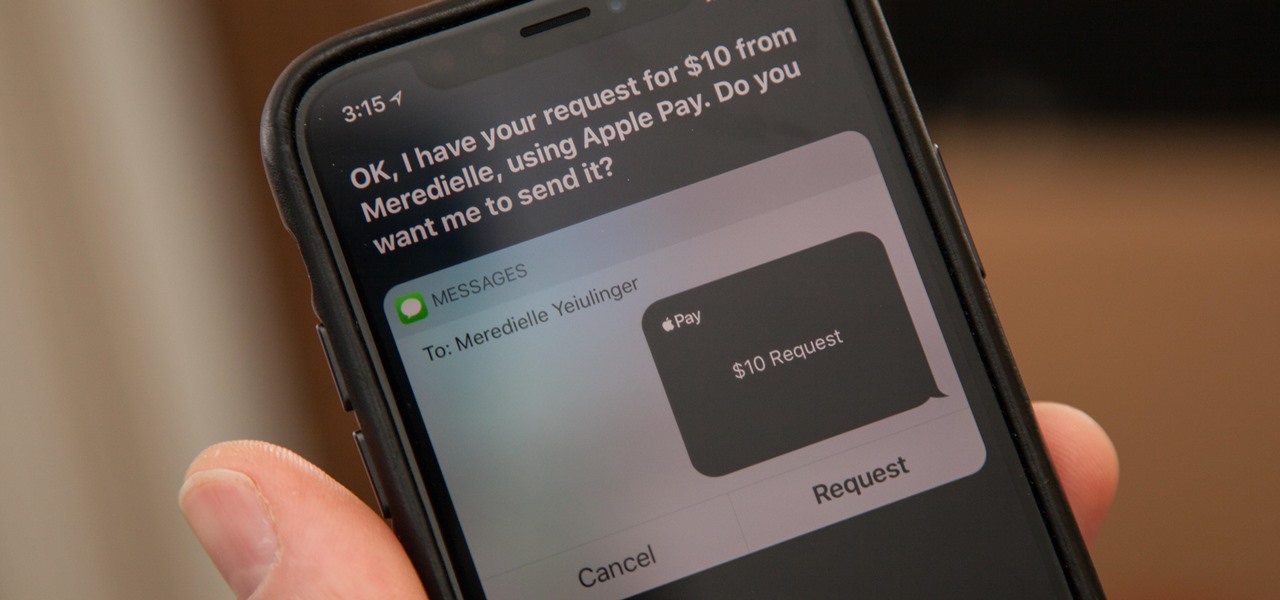
You might be proficient at sending your family and friends money using Apple Pay Cash on your iPhone, but what about when you need some digital currency in your wallet to buy in-app purchases or to get back the money you spent on someone's lunch? Requesting some Apple Pay Cash can be done a few different ways, none of which are hard.

Now that Apple Pay Cash has rolled out to compatible devices in the US, you're likely to give Apple's new person-to-person payment system a try since it's right there in the iMessage app drawer in Messages. However, just like with Venmo, Square Cash, and other mobile payment processors, there are some hidden fees, limits, and other fine print you need to be aware of.

In many places, May has given way to a surplus of strawberries cluttering the produce aisle. These sweet berries are great in a wide variety of delicious baked goods, from pies to cakes and everything in between.

If you've been around computers long enough, you've probably heard the phrase "have you tried turning it off and on again?" This trick usually works because it forces your computer to empty out the contents of its RAM and disk caches when you restart.

Welcome back, my tenderfoot hackers! One of the issues we often encounter with Metasploit is how to add new modules. Although Rapid7 (Metasploit's owner and developer) periodically updates Metasploit with new exploits, payloads, and other modules, at times, new modules appear that are not added to the Metasploit repository.

After all the leaks and peeks of the HTC One M8, it has finally been officially introduced to the public, available for purchase at most U.S. carriers. HTC also unveiled Sense 6 during the launch event, the newest iteration of its operating system, and thanks to their new Advantage Program, the update shouldn't be too far behind for the older One (M7).

Welcome back, my greenhorn hackers! After the disaster that was Windows Vista and the limited and reluctant adoption of Windows 8 and 8.1, Windows 7 has become the de facto standard operating system on the desktop/client.

The following video is the result of months of viewer requests to create a single-shot airsoft rifle. The design I decided to film the video around ended up being quite durable, and very capable of being loaded with single pellets, or multiple pellets to operate as a shotgun.

With the recent announcement of our server shutting down, it's time to get in and save the things you've made. However, this will work on any CraftBukkit server as well, and gives no extra strain to the server as the work is all done on your local computer.

Sometimes it's hard to find the time to watch your diet. When you're in a rush, you'll eat whatever you can. Many people grab snacks without considering food quality. But there are healthy vending options.

The Department of Biological Sciences at the University of Alberta brings you this video tutorial specifically relevant to your student laboratory courses, specifically microbiology. If you're a student at any school of biology, this information will be helpful for learning how to use Sephadex gel filtration for chromatography in the lab.

Karen Gillan must have had an absolute blast chewing the scenery as Nebula in Guardians of the Galaxy Vol. 2, seeing as how Nebula is a ball of pure, seething fury pretty much 24/7. Combine that larger-than-life personality with her iconic blue and silver cyborg look, and you have a guaranteed hit for cosplay or Halloween.

In the case of rotting food, microbes are not our friends. Now, scientists have developed a new food wrap coated with tiny clay tubes packed with an antibacterial essential oil that can extend the shelf life of perishable food, so we can waste less and eat more.

This is my first contribution in an ongoing series on detailing the best free, open source hacking and penetration tools available. My goal is to show you some of the quality tools that IT security experts are using every day in their jobs as network security and pen-testing professionals. There are hundreds of tools out there, but I will focus and those that meet four key criteria: