Who would have thought that dryer sheets can be a quick remedy for super-staticky flyaway hair? But it's true. It's all about the positive charges in the sheets and their ability to neutralize electron buildup. And that's not the only surprising quick fix for hair problems that you can easily find in your home.

A man-in-the-middle attack, or MitM attack, is when a hacker gets on a network and forces all nearby devices to connect to their machine directly. This lets them spy on traffic and even modify certain things. Bettercap is one tool that can be used for these types of MitM attacks, but Xerosploit can automate high-level functions that would normally take more configuration work in Bettercap.
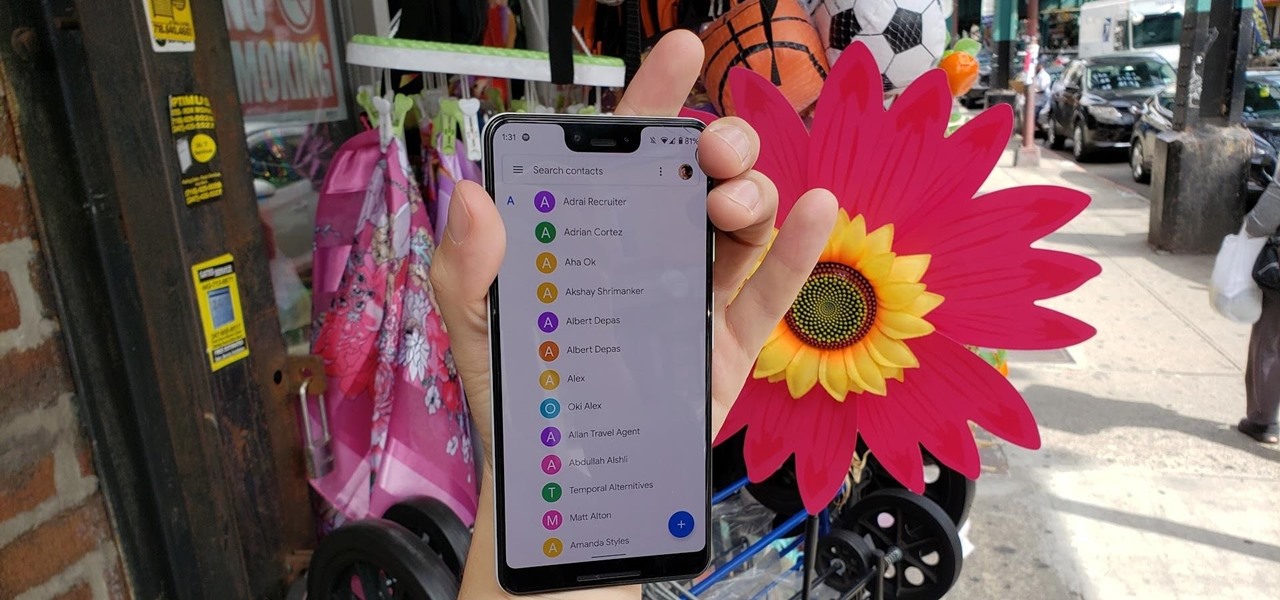
Your phone is loaded with contacts you've collected over the years. They're an asset, and you should use your library of connections outside the confines of your mobile device. Luckily, your Pixel uses a standardized medium to store contacts that can be used by the likes of LinkedIn, Outlook, Hubspot, iCloud, and more.

While Snapchat augmented reality often embraces pop stars like Drake and Ariana Grande, a couple of bands from the louder side of the music industry have found a home with Facebook.
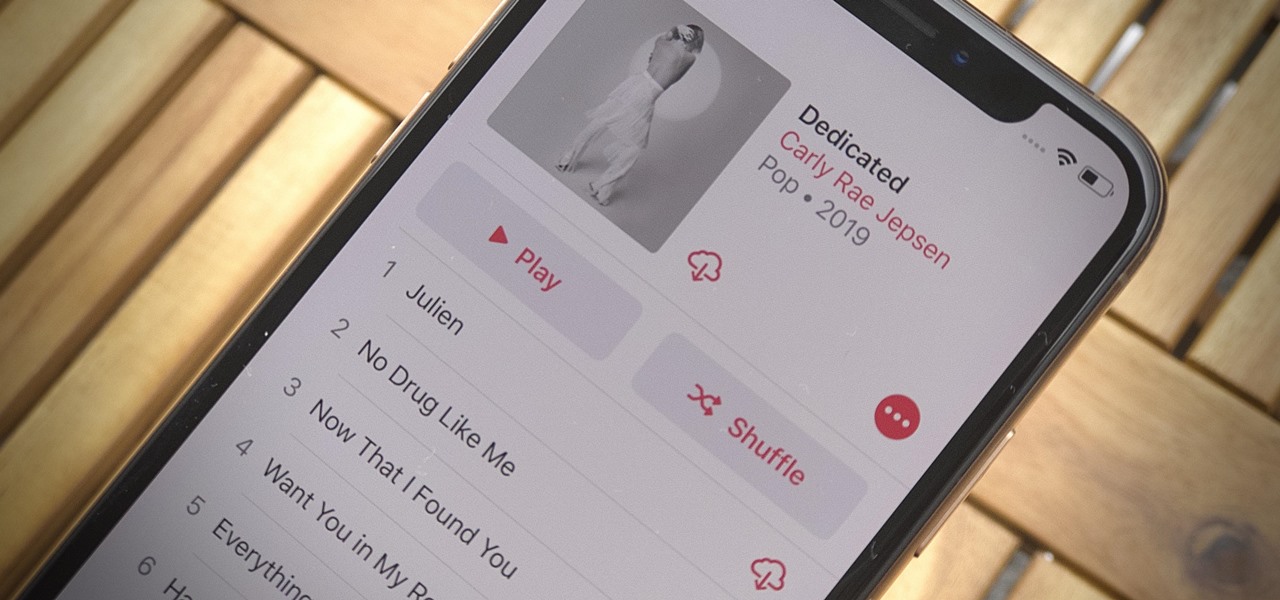
Newer smartphones usually come with a decent amount of storage, even at the lowest tier, but that doesn't stop items from filling up all that space. Watching movies offline, shooting 4K videos, and other processes can fill up your phone fast, and so can albums and songs in Apple Music.

Ransomware is software that encrypts a victim's entire hard drive, blocking access to their files unless they pay a ransom to the attacker to get the decryption key. In this tutorial, you'll learn how easy it is to use the USB Rubber Ducky, which is disguised as an ordinary flash drive, to deploy ransomware on a victim's computer within seconds. With an attack that only takes a moment, you'll need to know how to defend yourself.

Now that we've got all of our software installed, we're going to proceed with the next step in our HoloLens Dev 101 series—starting a fresh project and building it into a Holographic application. Then we will output the application to the HoloLens Emulator so we can see it in action.

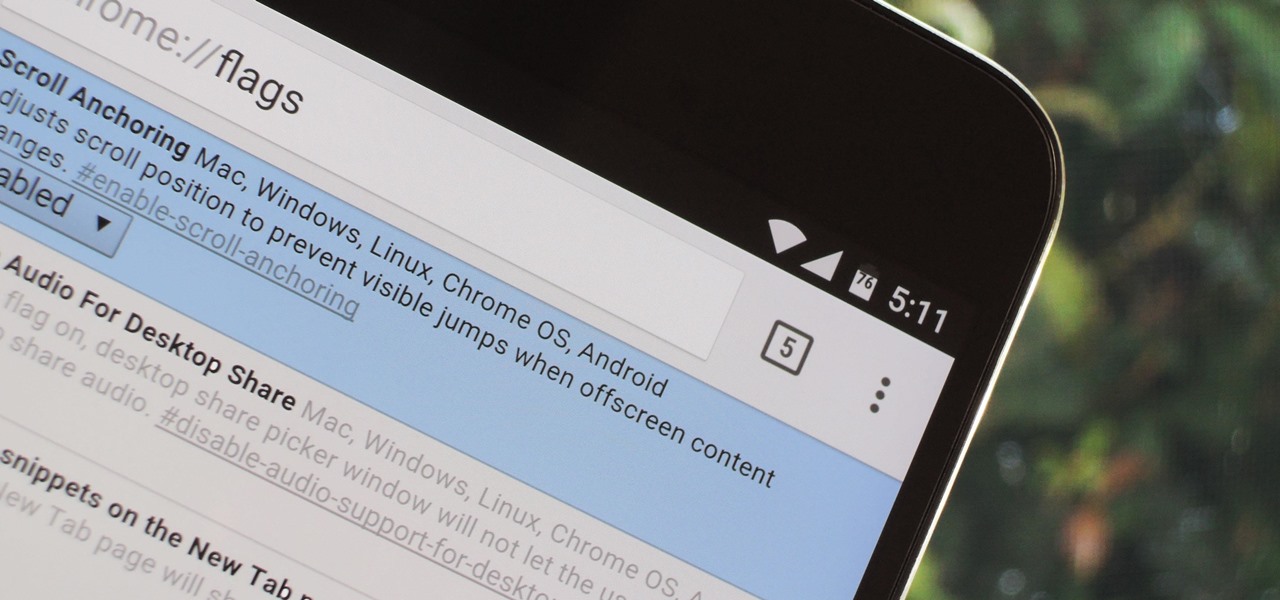
Google's Chrome browser comes pre-loaded on the vast majority of today's Android devices, and it's one of the fastest, most stable, and useful browsers out there. But it does have one major annoyance—while a page is loading, you'll see a link, then reach to tap it, but an element further up the page will load, and the link will jump out from underneath your fingertip.

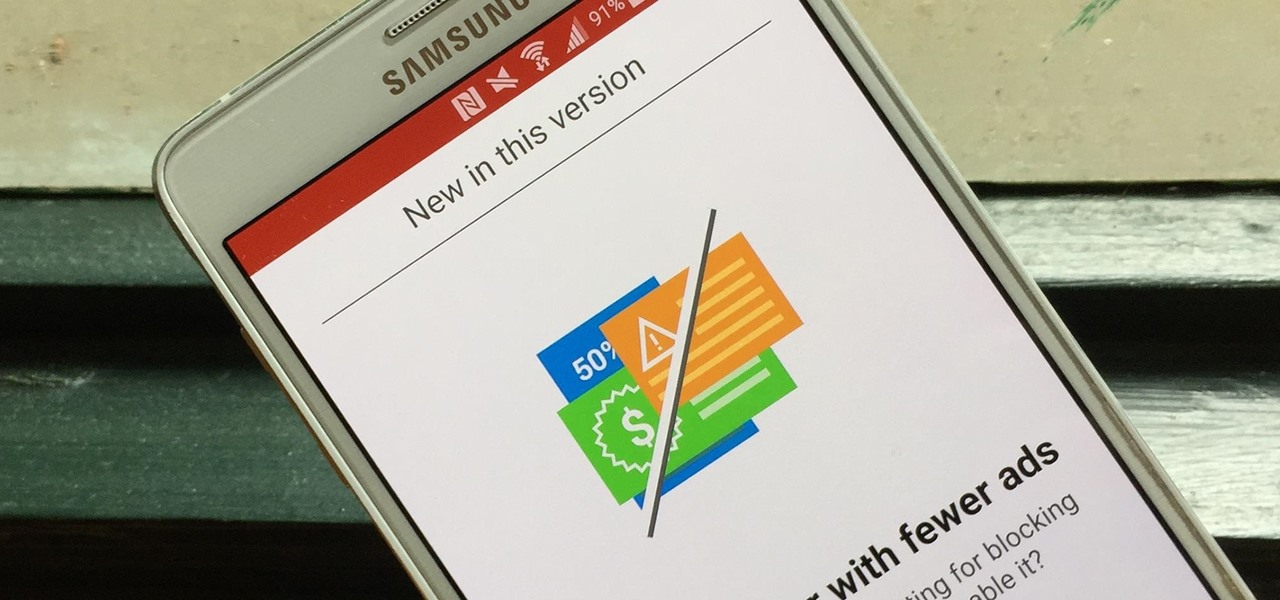
Opera's web browser for Android, Opera Mini, now comes with integrated ad-blocking technology for a less cluttered browsing experience. More importantly, it decreases the amount of data being loaded, which Opera claims increases webpage loading times by 40 percent. This is in addition to the 90 percent data reduction from Opera Mini's compression technology.

Welcome to a tutorial on crypting technology. In this article, we will be discussing types of crypters, how they work and why they work. After defining these, we will then make our own basic crypter using the function I gave to you as a task to complete by yourself in the previous tutorial.

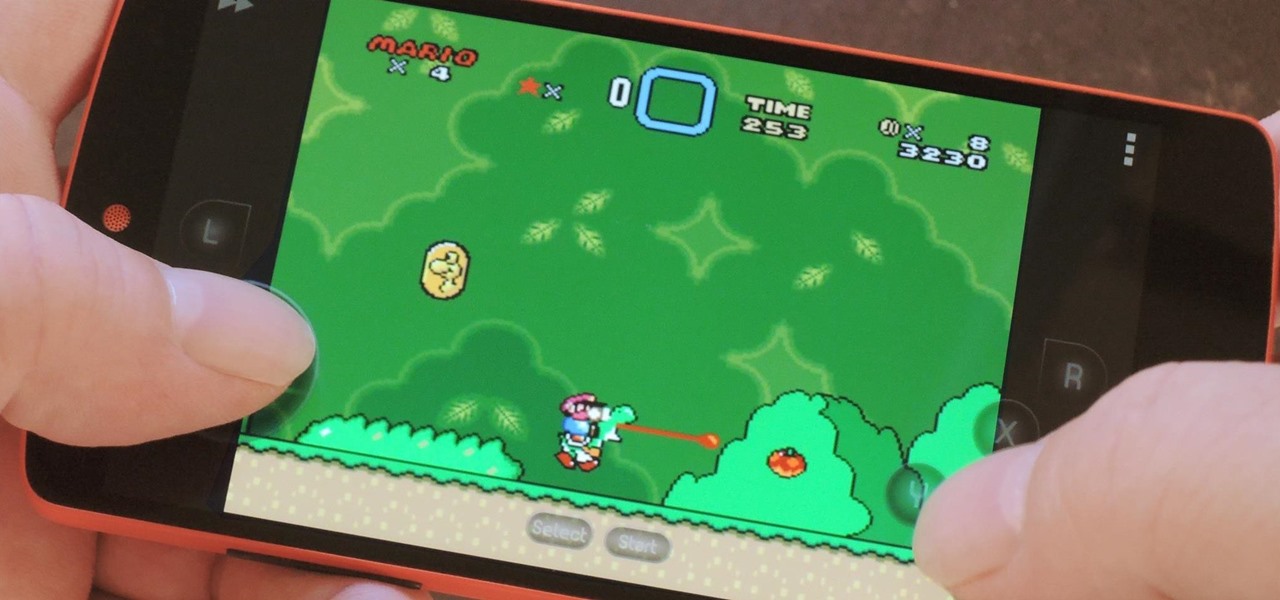
Smartphone games are getting pretty good these days, but they still can't beat the retro appeal of a good emulator. I mean, who wouldn't want to have their all-time favorite console and arcade games tucked neatly in their front pocket? Classics ranging from Super Mario Bros. to Pokémon can all be played at a silky-smooth frame rate on today's devices if you can just find a good emulator to run them on.

This is a short explanation and tutorial on how to grab saved passwords from Google Chrome, ideally from a meterpreter session. The idea behind this is to understand how saved passwords work and how to keep them safe. Let's have some fun :D Understanding Google Chrome Saved Passwords

Welcome back, my aspiring hackers! In many of my earlier tutorials, I mentioned the complementary nature of hacking and forensics. Both disciplines, hacking and forensics, benefit from a knowledge of the other. In many cases, both disciplines will use the same tool. In this tutorial, we will use another tool that can be used in either discipline—Sysinternals—a suite of tools developed by Mark Russinovich.

As with any software, Android apps can occasionally suffer from bugs. But finding the root cause of such issues can often be difficult, and reporting bugs is a cumbersome experience.

In case you haven't heard, chia seeds are off of the novelty plant grower and in your supermarket. Why? Because they're a nutrient-dense food loaded with calcium and fiber (18% and 42% respectively of your RDA per one ounce of seeds). There are even some preliminary studies that show chia might be useful in combating diabetes.

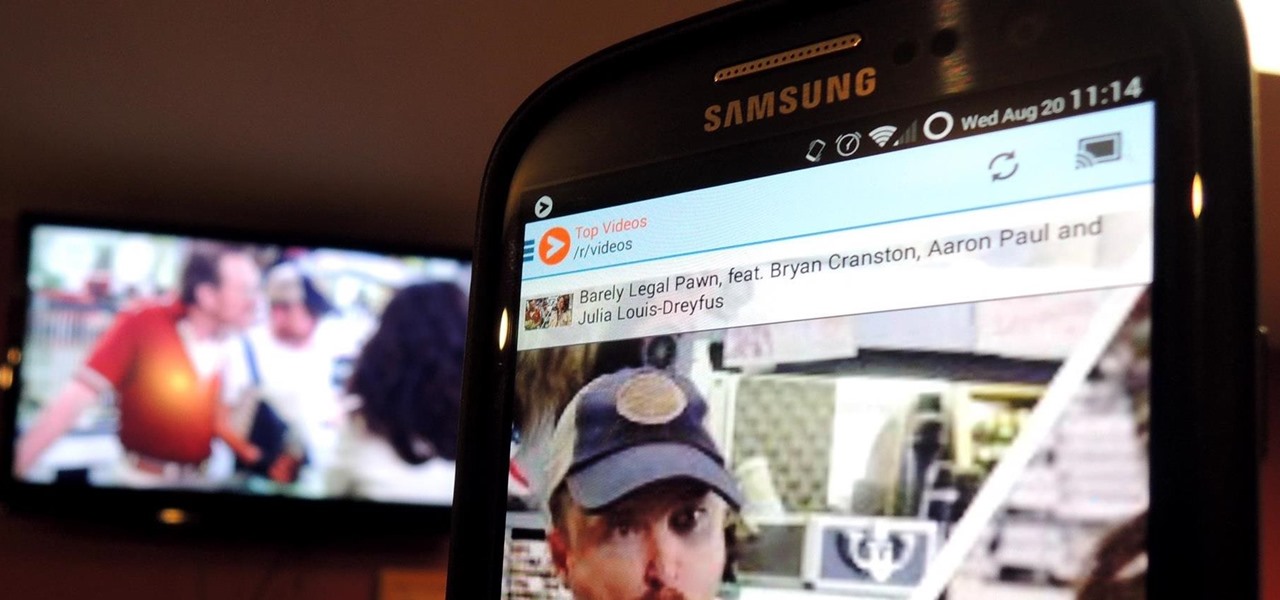
I spend an ungodly amount of time on Reddit, and while I do enjoy scrolling through memes and scandalous confessions, I must admit that I spend the majority of my time watching an endless stream of YouTube videos.

John Frusciante, of Red Hot Chili Peppers fame, has just launched a new album, literally. His latest work, Enclosure, was loaded up on Sat-JF14 satellite inside the payload bay of the Interorbital Neptune Rocket on March 29th and launched into orbit.

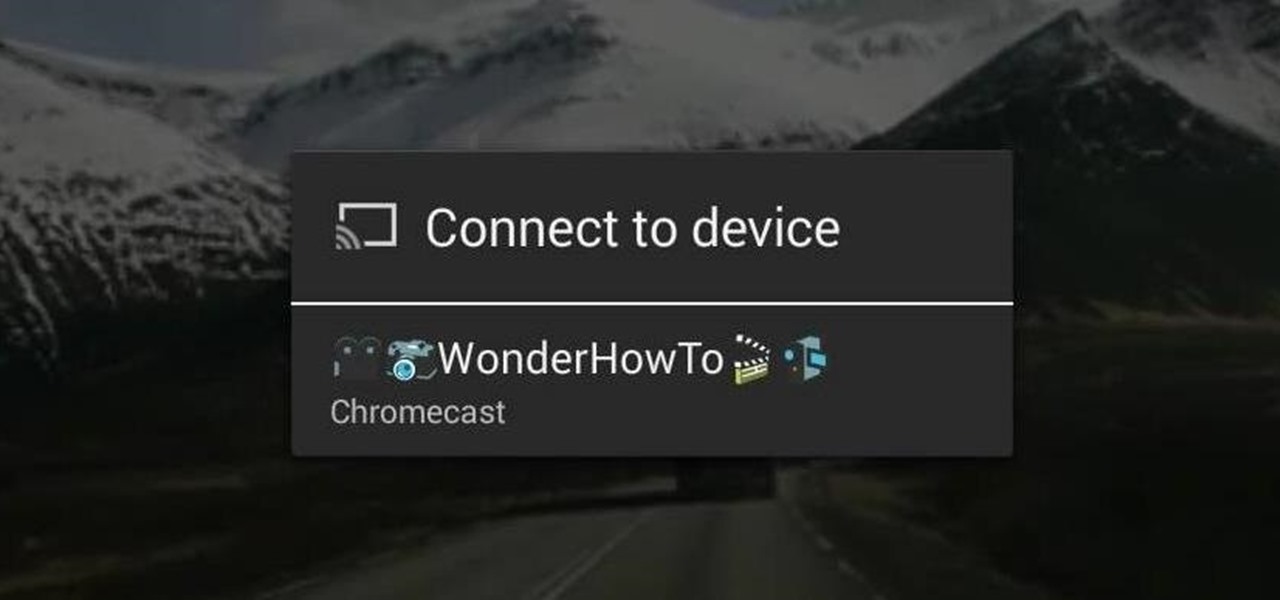
With the development kit fully open, the functionality of our Chromecasts seem to expand with each passing day. From a portable gaming system to your own personalized news station, our little gadgets have a lot going for them.

Most people don't ask for gift cards, but they're always a popular gift choice for notoriously hard-to-shop-for people—or the time-constrained gift-giver. While most gift cards are attached to certain stores, many folks will get a prepaid Visa or MasterCard card that allows them to make purchases wherever those companies are accepted.

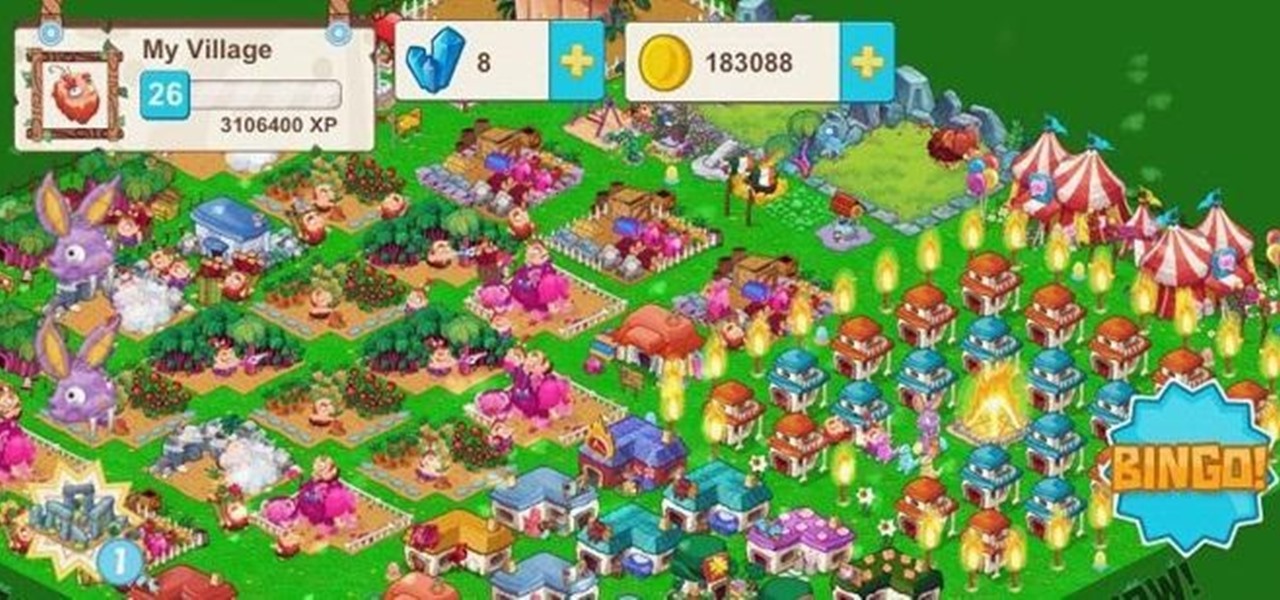
So, you've finally managed to get addicted to one of those free farming games, like Farm Story or Tiny Village. You play the game nonstop now, and the only thing stopping you is that dreaded on-screen notice to come back in 23 hours to finish farming or building. Come back in 23 hours… WHAT?!? Most of these free games will start charging you at this point. Time becomes a luxury. Well, not anymore, thanks to XDA Developer StupidIdea, who made a time-tricking app called GMD Speed Time (that's t...

Keys are on the way out. They're clunky, take up precious space, and slow you down when you have tons of identical-looking gold ones on your keyring. Everything we can open with keys can now also be opened with wireless technology in just a click—so why use keys anymore? Sure, you can pay hundreds of dollars for an automated lock system on your house—but why do that when you can build it yourself!

Whether you've got an itch for a mini-flamethrower, a shower of burning sparks, or a exploding ball of flames, these little fireworks-producing lighters may be the answer to your pyrotechnic cravings!

Gerridae—you've probably seen these weird bugs gliding across the surface of the water when you're out swimming or fishing. These insects are commonly referred to as water striders, or more cleverly, Jesus bugs, for their ability to "walk on water". It's a pretty cool trick, but what could it do for science, right? Turns out, quite a bit. Photo by felixtsao

Want an electric car without the price tag? You could always build your own, or maybe just hack your old gas guzzler into an eco-friendly electric machine... This weekend at Defcon, security consultant David Brown showed off his "Voltswagon" project, a 1974 Beetle named Shocky that he converted to electric for only $6,000. He removed the old combustion engine, radiator, and a few other unneeded parts to make it lighter. Then he loaded it with batteries front and back, ten Interstate DC-29, 12...

If you want to get started sniffing Wi-Fi networks, you usually need to start with a wireless network adapter. But thanks to a Wi-Fi sniffing library written in Arduino and the ultra-cheap ESP8266 chip, you might not need one. For less than $10 in electronics, you can build a tiny Arduino Wi-Fi sniffer that saves Wireshark-compatible PCAP files and fits anywhere.

While hackers adore the command line, working with the GUI (graphical user interface) of an operating system has some advantages. This is especially true when it comes to post-exploitation. When we can control the mouse and keyboard of a remote computer, we can truly say we have complete control over the device. Today, I'm going to introduce to you the PyAutoGUI module, which does just that, and just how much fun you can have with it!

PowerShell Empire is a post-exploitation framework for computers and servers running Microsoft Windows, Windows Server operating systems, or both. In these tutorials, we will be exploring everything from how to install Powershell Empire to how to snoop around a target's computer without the antivirus software knowing about it. If we are lucky, we might even be able to obtain domain administrator credentials and own the whole network.

Whether you're in an airport, restaurant or waiting room, the insidious grip of televisions on human life is omnipresent. Sometimes it's nice to talk to other human beings while looking at them directly—actually hearing what they have to say.

If you don't work in construction or are a woodworking master, you probably aren't entirely sure what all those marks are on a tape measure. Sure, you likely know the basics, like there are 12 inches to a foot, but what are all those little tick marks for? Don't let all those little lines dissuade you from using a tape measure. Follow these guidelines to help you read all those little ruler marks.

We've shared a capture-the-flag game for grabbing handshakes and cracking passwords for Wi-Fi, and there are some upcoming CTF games we plan on sharing for other Wi-Fi hacks and even a dead-drop game. While security-minded activities and war games are excellent ways to improve your hacking skills, coding a real video game is also an excellent exercise for improving your programming abilities.

Google has started to release a Go line of Android apps. These apps offer a minimalistic version of their major app counterpart. So far, we have Go versions of Maps, Photos, Gmail, and more. Who are these apps for and why would you want to use them? Here's a quick overview of Google Photos and Gallery Go.

Following on the heels of the announcement that ThirdEye's Gen X2 MR glasses began shipping in September, ThirdEye has revealed it has developed an app that helps soldiers aim their weapons during battle situations.

Businesses that have adopted enterprise-grade wearables for their workforces now have a new option among the multitude of AR productivity apps that can help their team members communicate in AR.

If you don't want the large and permission-hungry Facebook app on your phone, the perfect solution is to create an app icon for the Facebook mobile site on your home screen. The website version of Facebook doesn't run background tasks, has no distracting notifications by default, you won't be giving Facebook as much data, and your phone's battery life will be improved.

A lot of people still trust their web browsers to remember every online account password for them. If you're one of those users, you need to adopt a more secure way of managing passwords, because browser-stored passwords are hacker gold mines. With a USB Rubber Ducky and physical access to your computer, they can have a screenshot of all your credentials in their inbox in less than 60 seconds.

Over the last few years, the virtual reality space has earned a welcome reputation for fostering better representational balance with regard to gender compared to the general tech industry, with women like Nonny de la Peña and many others leading the charge.

With developers chomping at the bit to play with ARKit 2.0, Unity has updated its ARKit plugin to enable access to the new augmented reality superpowers of the toolkit.

The one thing that separates a script kiddy from a legitimate hacker or security professional is the ability to program. Script kiddies use other people's tools, while hackers and security pros write their own tools. To that end, we're going to see how a stack overflow vulnerability allows us to flood a variable with enough input to overwrite the instruction pointer with our own commands.

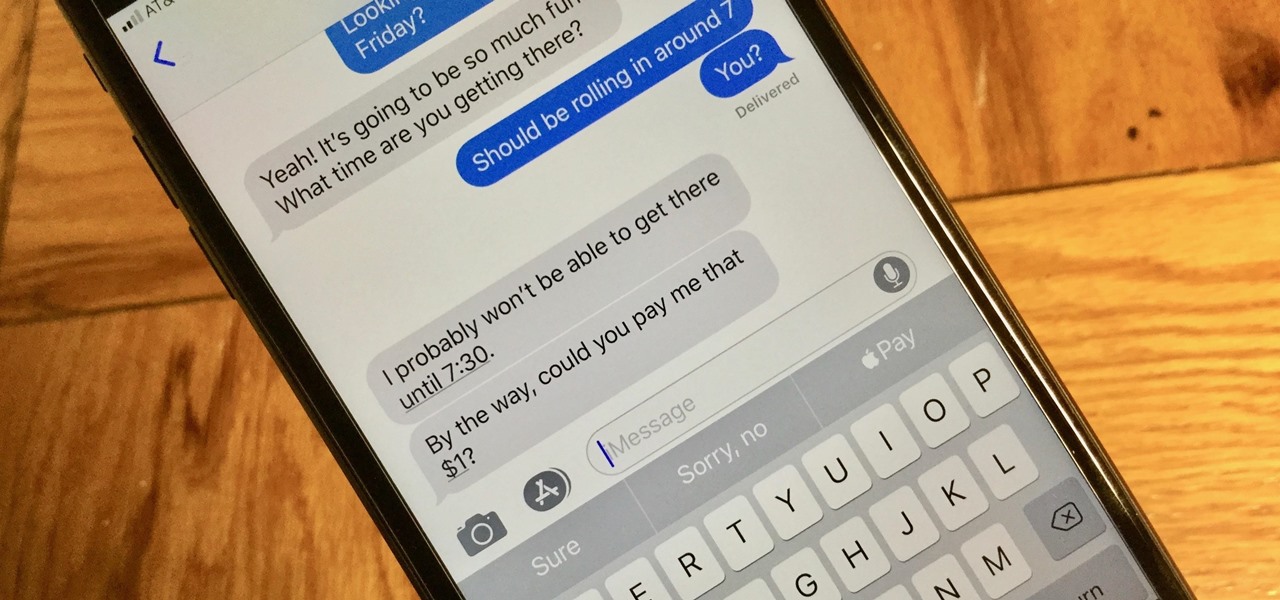
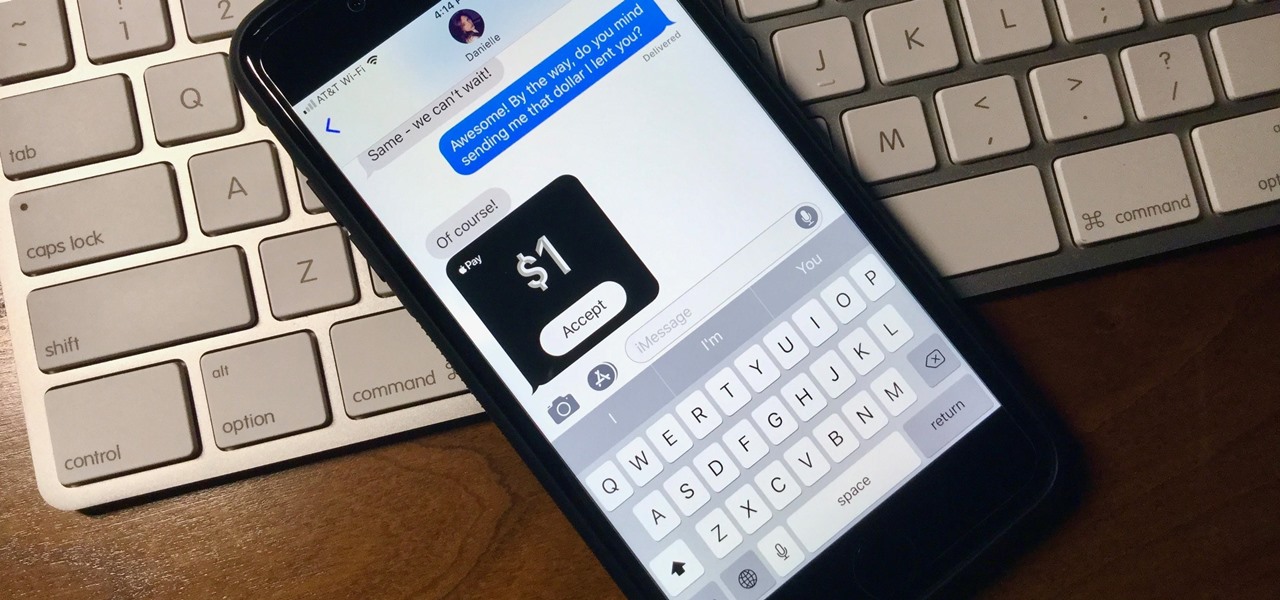
With Apple Pay Cash, you can easily and securely pay your contacts directly in your iPhone's Messages app. While you can always use the normal method of paying someone with Apple Pay Cash, there's actually a faster way, as long as your contact asks you for money in an iMessage.

What happens when somebody sends you Apple Pay Cash inside of an iMessage? Do you have to add it to your Apple Pay Cash card on your iPhone manually or does it miraculously appear there automatically?