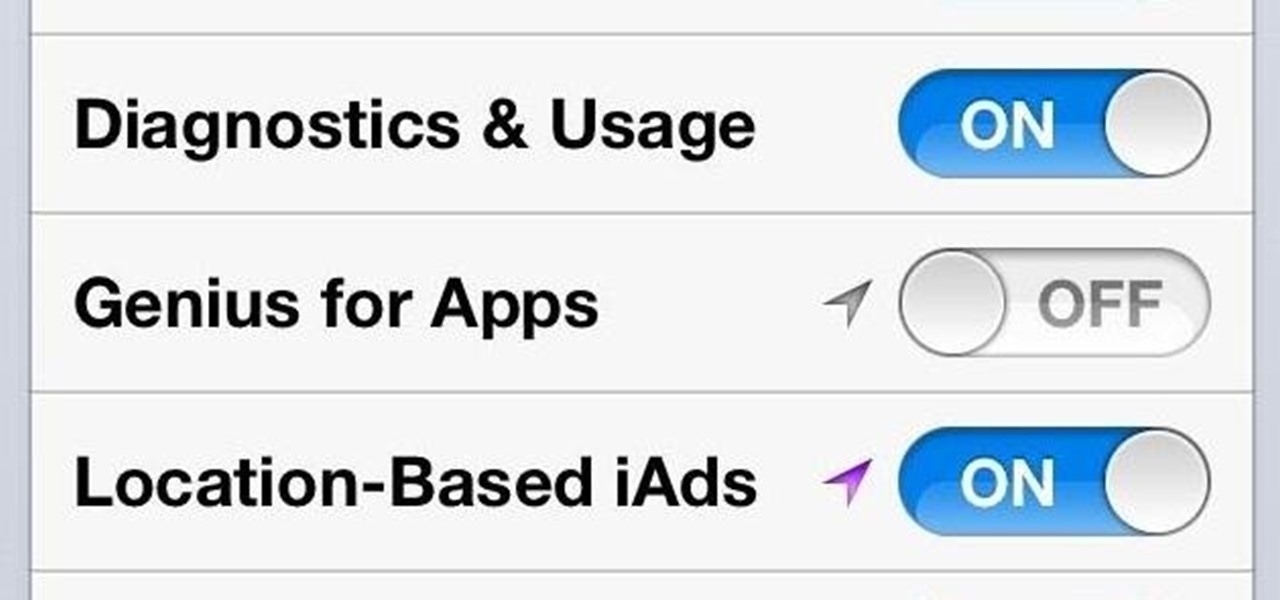
It's been a rough week for Instagram. First they came out with a new terms of service that suggested the right to let companies use people's photos for advertisements without the user's permission. Then everyone started freaking out and debating whether or not to leave the online photo-sharing and social networking service. Now, they've changed the controversial wording saying that the selling of user photos "is not true and it is our mistake that this language is confusing".

Feeling nostalgic for Super Mario Kart, but don't want to fire up the old Super Nintendo? Never fear, with a free Flash-based emulator called SNESbox, you can relive the 90s and play all your favorite games right from your browser, without having to install anything. With 1,861 games, if there's something made for the Super Nintendo that you want to play, they almost certainly have it. Sure, there are tons of emulators you can use, but SNESbox is different in that it gives you the ability to ...

The first album I ever bought with my own money was Nirvana's MTV Unplugged in New York. It featured mainly lesser-known songs and covers, but was on constant repeat on my Walkman. While the whole album was fantastic, there was one song that stood out the most to me—"The Man Who Sold The World." The song (originally written by David Bowie) kept me under a spell, which had me replaying the song over and over and over and over. As I got older, I found myself sharing this relationship with a han...
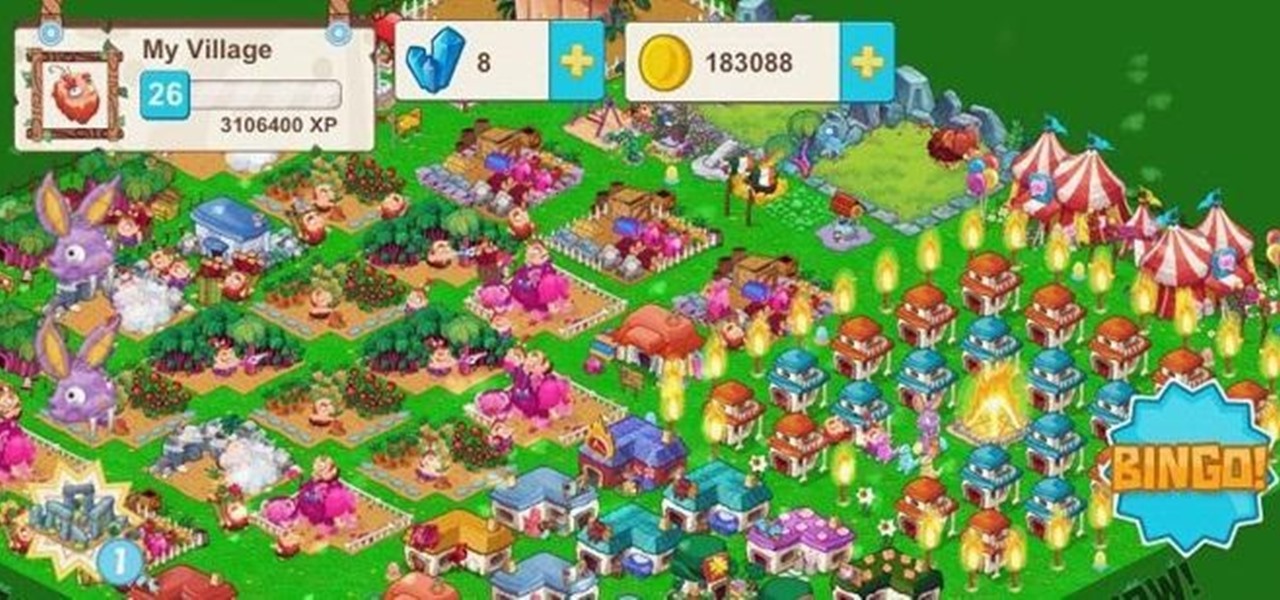
So, you've finally managed to get addicted to one of those free farming games, like Farm Story or Tiny Village. You play the game nonstop now, and the only thing stopping you is that dreaded on-screen notice to come back in 23 hours to finish farming or building. Come back in 23 hours… WHAT?!? Most of these free games will start charging you at this point. Time becomes a luxury. Well, not anymore, thanks to XDA Developer StupidIdea, who made a time-tricking app called GMD Speed Time (that's t...

Keys are on the way out. They're clunky, take up precious space, and slow you down when you have tons of identical-looking gold ones on your keyring. Everything we can open with keys can now also be opened with wireless technology in just a click—so why use keys anymore? Sure, you can pay hundreds of dollars for an automated lock system on your house—but why do that when you can build it yourself!
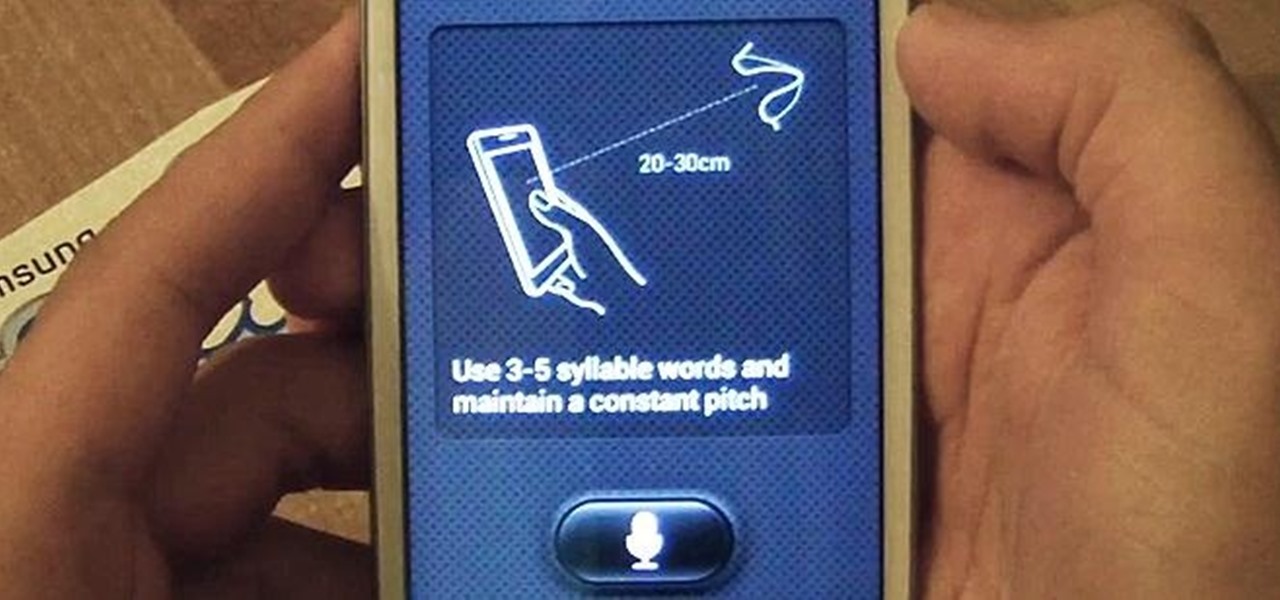
With voice commands becoming conventional on most new smartphones, it's only ideal that their abilities increase as well. Thanks to Apple's Siri, you can do things like update your Twitter account and look up who the president of Costa Rica is.

Wet-plate collodion photography is a process that lets you develop a photo onto a piece of glass. It has some neat applications, but it's not a simple process, and most people use a special camera to do it because the silver nitrate used to process usually ends up leaking, which would ruin a regular camera.

Wall Anchors. Drywall Wall Anchors. Plasterboard Wall Anchors. I discovered these plasterboard (drywall) anchors / plugs a few years ago and think they are fantastic. They are ridiculously easy to use and are extremely effective in attaching fixtures to walls. One of the main things to be aware of (as with all things that have fixtures hanging from them) is the recommended maximum weight loading of each size of anchor. What ever the packet says, adhere to it.

As if iOS 6 wasn't under enough scrutiny, a new issue has surfaced regarding the App Store for iOS 6 on the iPhone and iPad. According to users, the application store is very sluggish and doesn't load properly. Below is a video of just how slow the application store is.

The worst part of moving into a new place is, well...moving. It's tedious, a lot of hard labor, and it can take forever, and don't even get me started on all those labels. It's also one of the only times in your life when everything you own can be stolen at once, since it's sitting in a movable container. Rather than risk losing everything, try this DIY Moving Truck Alarm System by Tim Flint that lets you know when the loading door is opened so you can catch would-be thieves red handed.

Whether you've got an itch for a mini-flamethrower, a shower of burning sparks, or a exploding ball of flames, these little fireworks-producing lighters may be the answer to your pyrotechnic cravings!

Gerridae—you've probably seen these weird bugs gliding across the surface of the water when you're out swimming or fishing. These insects are commonly referred to as water striders, or more cleverly, Jesus bugs, for their ability to "walk on water". It's a pretty cool trick, but what could it do for science, right? Turns out, quite a bit. Photo by felixtsao

Want an electric car without the price tag? You could always build your own, or maybe just hack your old gas guzzler into an eco-friendly electric machine... This weekend at Defcon, security consultant David Brown showed off his "Voltswagon" project, a 1974 Beetle named Shocky that he converted to electric for only $6,000. He removed the old combustion engine, radiator, and a few other unneeded parts to make it lighter. Then he loaded it with batteries front and back, ten Interstate DC-29, 12...

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

Learn how to do hold a squat while doing a power single cable wide pull down. Presented by Real Jock Gay Fitness Health & Life.

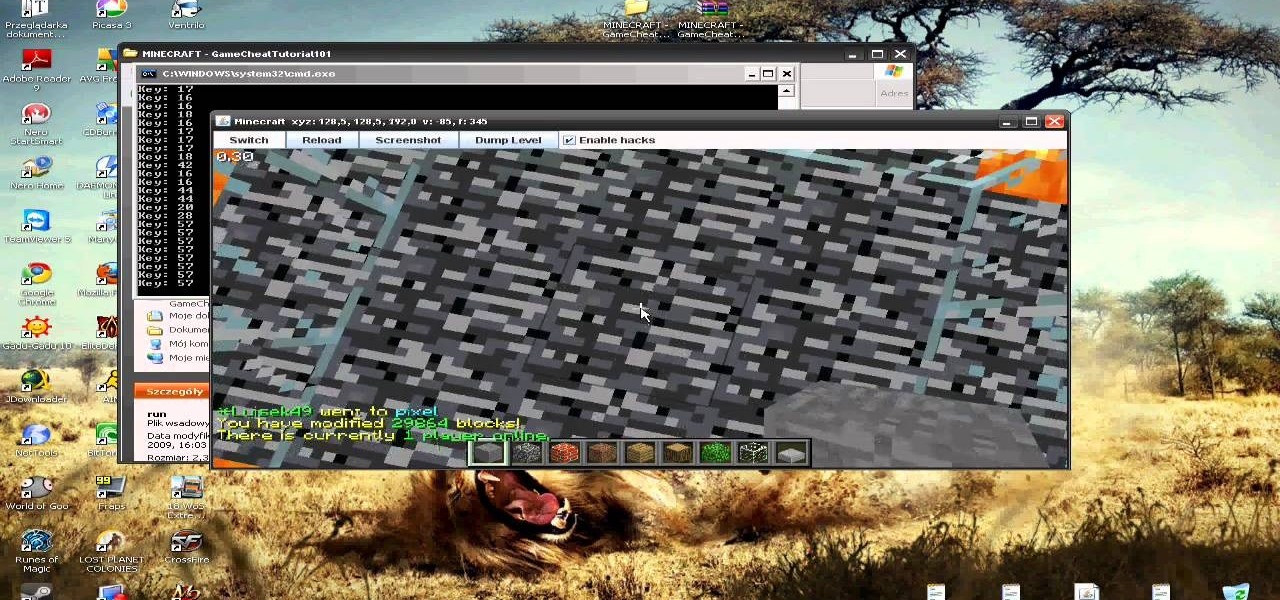
This is a super easy hack that anyone playing Minecraft on a PC can do. Hack a custom client for the game, which will give you access to things like noclip mode and fly jumps. You won't need a broswer loaded to use this, either.

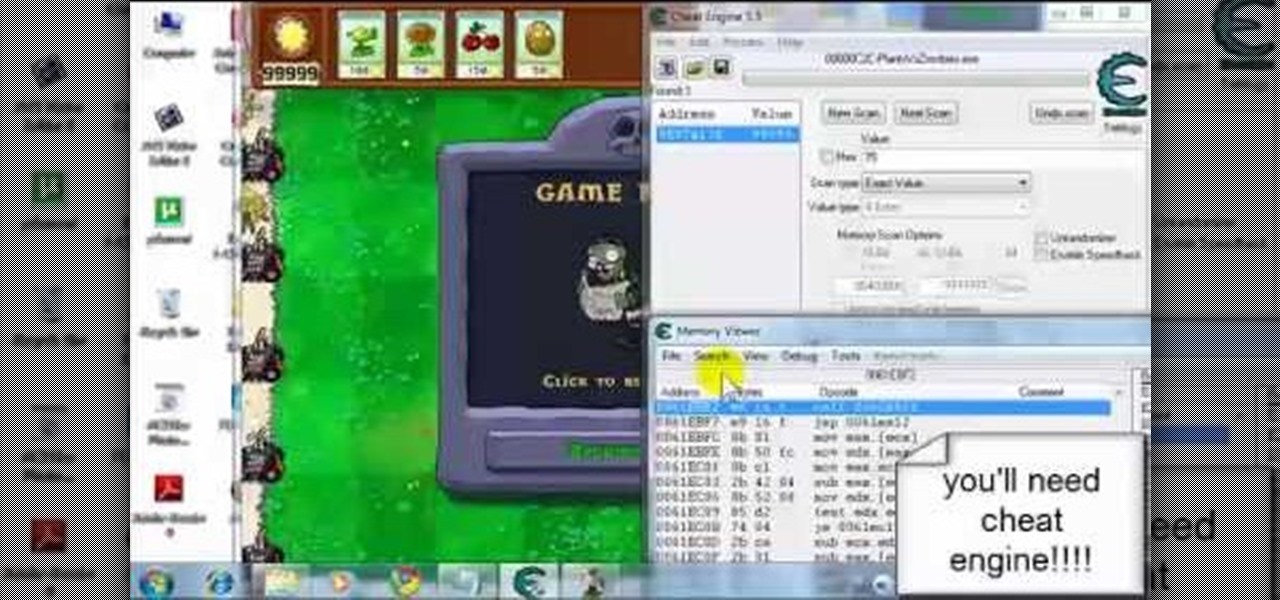
Want to make your next game of Plants vs Zombies much, much easier? You can hack the game to make it happen! Get the latest version of Cheat Engine. Then, use the steps outlined in this tutorial to get infinite sunshine and no loading plants.

When you load Firefox, you're automatically taken to whatever homepage you've set up, or the automatic homepage. But what if you wanted to make a couple home pages? How about three or four? Well, you can, and this video will outline the process of setting up multiple home pages in Mozilla Firefox.

See how you can build a liquid fueled rocket with office supplies, mainly... a Sharpie magic marker and some duct tape. You'll also need some gas duster, the air cleaning can of gas. It's a pretty simple rocket to build, won't take long, and is loads of fun. Except, you'll need to keep buying canned air to propel it into the air multiple times.

Has your Windows computer been sluggish of late? This simple how-to demonstrates how to stop background processes from running automatically on your Microsoft Windows PC without the use of third-party software. Stop unnecessary start-ups with this tutorial.

Learn how to make the MAPAJET (most accurate paper attack jet); loads of office fun! This video origami tutorial shows how to fold an accurate paper airplane.

Join Matt Null (NCA/Millersville/Cheer Excel), Lindsey (Fire and Ice Allstars), Carly (Seton La Salle HS), Greg (Step 1 Allstars) and EJ (IUP) as you learn how to load, set and execute an extension with a cradle dismount. Great tips for the beginning cheer leading coach or cheerleader!

After you've mastered the basics of an extension, you can move on to the extended liberty cheerleading stunt. Join Matt Null (NCA/Cheer Excel/Millersville), Jhana, Dena, and Lauren (Fire and Ice Allstars), and Greg (Step 1 Allstars) as you learn step by step how to do an extended liberty.

How to fix the freezing/crash issues in Grand Theft Auto 4 (GTA IV) during the install, loading, or in game.

This video explains how to properly stack bricks as a part of loading out the job. This is an essential step to do before starting your brick laying.

Watch this video for a basic outline of loading film for an SLR camera, also shows some other features specific to the Olympus OM-1. Most of these things are quite similar for all non autofocus film SLR cameras.

For a quick and easy side dish with an Indian twist, try Bhindi Bhujia. Coarsely chop some ladyfingers (okra), add some coriander seeds, and chopped green chilies and you have a spicy vegetable dish loaded with flavor.

When you think about your Apple Watch, what comes to mind? Fitness tracking? Replying to texts? There are a lot of things Apple Watch is good for, but social media doesn't appear to be one of them based on the App Store. If that's your perception, however, it's time for a reality check because you can start browsing Twitter and Reddit on your Apple Watch right now.

UnrealIRCd is an open-source IRC server that has been around since 1999 and is perhaps the most widely used one today. Version 3.2.8.1 was vulnerable to remote code execution due to a backdoor in the software. Today, we will be exploiting the vulnerability with Metasploit, examining the underlying code to understand it, and creating our own version of the exploit in Python.

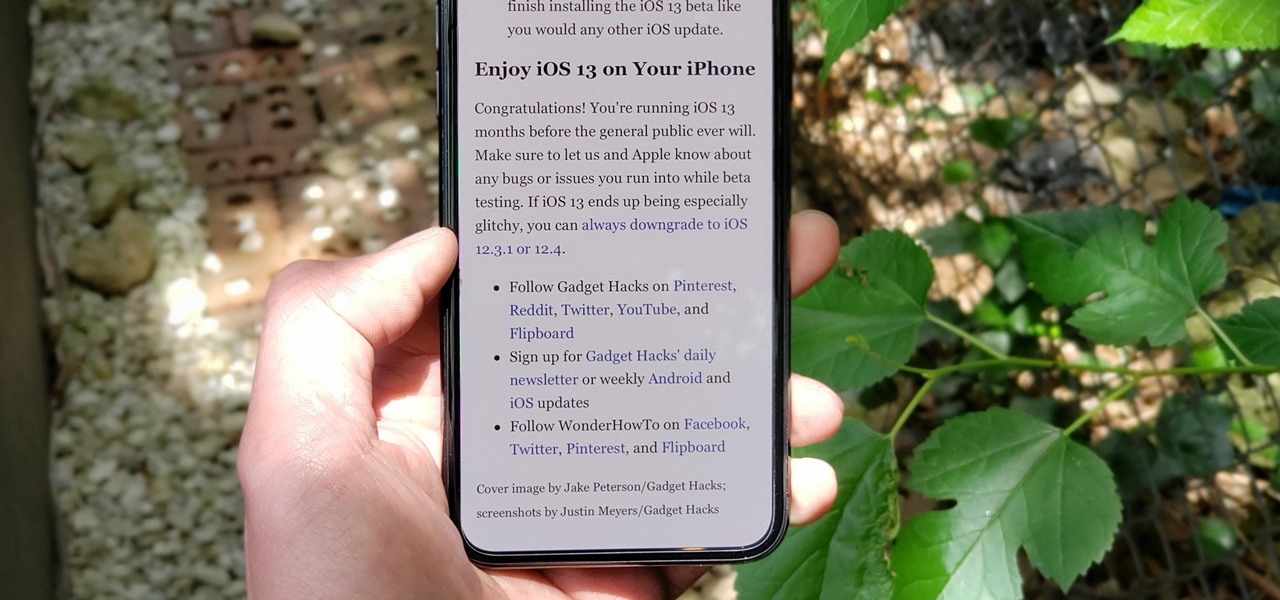
Safari has always done a great job at letting you browse the web, but it has never so much as offered a way to download files locally. Other apps have stepped in to help fill the gap, but they never felt as integrated into the iPhone as a native downloads manager would. They aren't needed anymore though, because Apple added one in iOS 13, pushing Safari on the iPhone closer to its sibling on the Mac.

While modern browsers are robust and provide a lot of functionality, they can be unlocked to do some pretty spectacular things with browser extensions. For hackers and OSINT researchers, these tools can be used to defeat online tracking, log in to SSH devices, and search the internet for clues during an investigation. These are a list of my top ten favorite browser extensions for hackers — and how to use them.

The Reader mode in Safari is a great way to view a webpage on your iPhone in a stripped-down manner, removing unnecessary images, videos, and advertisements for a streamlined experience free of distractions. Apple's iOS 13 improves upon Safari Reader when it comes to choosing which sites you want it to run automatically on, so everything is more accessible with more controls to work with.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

The Raspberry Pi Zero W and Pi 3 Model B+ include integrated Wi-Fi, Bluetooth Low Energy, and more than enough power to run Kali Linux. They sound like perfect all-in-one penetration testing devices, but the lack of support for monitor mode and packet injection usually meant buying a supported Wi-Fi adapter. Now, it's possible to use monitor mode on the built-in Wi-Fi chip with Nexmon.

It's always a good idea to know how an attack works at the very basic level. Manual techniques for exploitation often find holes that even the most sophisticated tool cannot. Sometimes, though, using one of these tools can make things so much easier, especially if one has a solid foundation of how it works. One such tool can help us perform a cross-site request forgery with minimal difficulty.

When you want to post a breathtaking landscape or picture-perfect portrait that you just took with your DSLR camera to Instagram, Facebook, or some other social platform, there's an easy way to do so — even if you don't have a computer handy, which is typical when you're out and about.

Design flaws in many routers can allow hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a strong password. While this tactic used to take up to 8 hours, the newer WPS Pixie-Dust attack can crack networks in seconds. To do this, a modern wireless attack framework called Airgeddon is used to find vulnerable networks, and then Bully is used to crack them.

It won't come as a surprise to hear that your cell phone, tablet, and laptop are loaded with bacteria and other organic material. While most of these bacteria are harmless, there are good reasons to reduce the capability of your mobile devices to infect you—or other people.

Thanks to Project-Infrared, there's now a pretty straightforward way to add motion tracking to the HoloLens: Connect it to a Kinect.