There comes a time in many tattooed individuals when they want to remove their tattoos. There are a lot of different ways to remove tattoo but they all cause scar. Dr. Neal Schultz explains only laser tattoo removal will not leave a scar and give a cosmetically-superior result. Laser energy is specifically targets the colored pigment of the tattoo so it only damages the colored pigment. It does not damage any of the surrounding skin. When people are treated for tattoos, it can take 8-12 treat...

It can be hard finding fellow singles in the suburbs but it can be done! Keep your eyes peeled and make sure you are out and about meeting new people in public settings. Don’t forget about your online or in print options.

Two ladies are discussing how to prepare to decoupage a wooden bangle bracelet. They are using a broad wooden bangle crafted from birch wood that can be purchased at a local craft store and printed tissue paper, for example, one in an animal print. This is part one of a three part series.

Pixel Perfect is the "perfect" show to help you with your Photoshop skills. Be amazed and learn as master digital artist Bert Monroy takes a stylus and a digital pad and treats it as Monet and Picasso do with oil and canvas. Learn the tips and tricks you need to whip those digital pictures into shape with Adobe Photoshop and Illustrator. In this episode, Ben shows you how to apply localized correction in Lightroom 2.

Check out this DIY video tutorial from Curbly, the best place to share pictures of your home, find design ideas, and get expert home-improvement advice.
How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

This four-part video tutorial will show you how to make a basic boffer sword for full contact padded weapons fighting and live action role-playing.

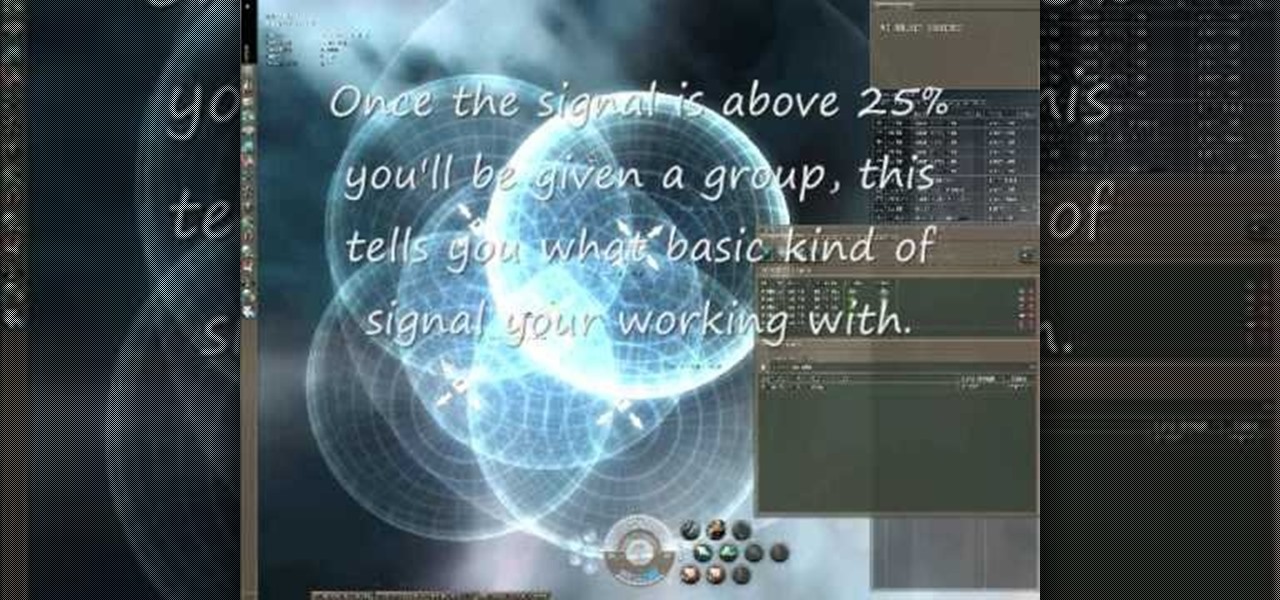
Know what's out there! You can send out probes to explore the area surrounding your ship. This tutorial shows you how to send out five probes and manipulate them in order to quickly and easily scan the local territory.

If you're the designated cook, outdoor BBQs should be fun, not time consuming and tedious. But this is what often happens when you're trying to barbacue beef, pork, or chicken and need to make sure each gets its marinade, the right coal or wood chips, and gets cooked long enough.

Learning the blues isn't an easy task, but this video helps make it a little easier. The song you'll be learning is "Coffee Blues" by Mississippi John Hurt. It's in the key of A and is a typical blues progression, in an alternating bass. It's the chords A, D, and E. If you're yearning to learn the delta blues, this is a great first step.

This video illustrates the quick and easy method to Buy fresh ginger and brew a pot of ginger tea . The process is comprised of the following steps:Step 1: Visit a local store or a vegetable shop and buy some ginger. Identifying whether the ginger is fresh or not is a easy job. Just smell it and judge if the odor is strong. A strong odor indicates that the ginger is fresh.Step 2: Mesh the ginger pieces and peel off it's skin.Step 3: Take small pieces of ginger and add them to boiling tea.Step...

Beets are good source of folacin, vitamin C, and potassium. They also taste super delicious when you roast them in the oven. This video tutorial demonstrates a simple way to roast beets in your oven and shows a tasty vinaigrette serving method.

Purchase a silver XBox 360 faceplate from your local gaming retailer. You can also remove the faceplate currently on your XBox 360.

Transform a piquant herb into a creamy, sweet paste by oven-roasting garlic with the help of these tips.

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast. Search Systm on WonderHowTo for more DIY episodes from this Revision3 show.

You Will Need * A fire extinguisher

Systm presents this detailed tutorial on how to make a custom Star Wars style light saber. Luke, Darth and Obi-Wan's Lightsabers were pieced out of junk piles. David shows you how to build exact replicas and an original design from The Custom Saber Shop. Then he picks a fight with Patrick.

Learn to make your own super effective bass traps and acoustic panels with materials from your local hardware store, just by watching this home audio video tutorial.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

We're glued to the news now more than ever, but our "free press" isn't necessarily free of charge. Cable news outlets like CNN and MSNBC are locked behind expensive cable TV packages and cord-cutting streaming subscriptions such as Sling TV and Hulu + Live TV. Luckily, there are plenty of alternatives to get your TV news fix, free of any payment, account, or commitment.

A lot of time can be wasted performing trivial tasks over and over again, and it's especially true when it comes to hacking and penetration testing. Trying different shells to own a target, and testing out privilege escalation commands afterward, can eat up a lot of time. Fortunately, there is a tool called One-Lin3r that can quickly generate shells, privesc commands, and more.

Location-based gaming company Niantic knows its business model is inextricably tied to the outdoors, so it is in its best interest to help preserve that environment to give players a place to play.

These days, it's easy to cut the cord. Thanks to a new crop of streaming TV apps, you can get the same service offered by a traditional cable subscription at a fraction of the price. After some extensive testing, we believe we've found the absolute best apps for cord cutting.

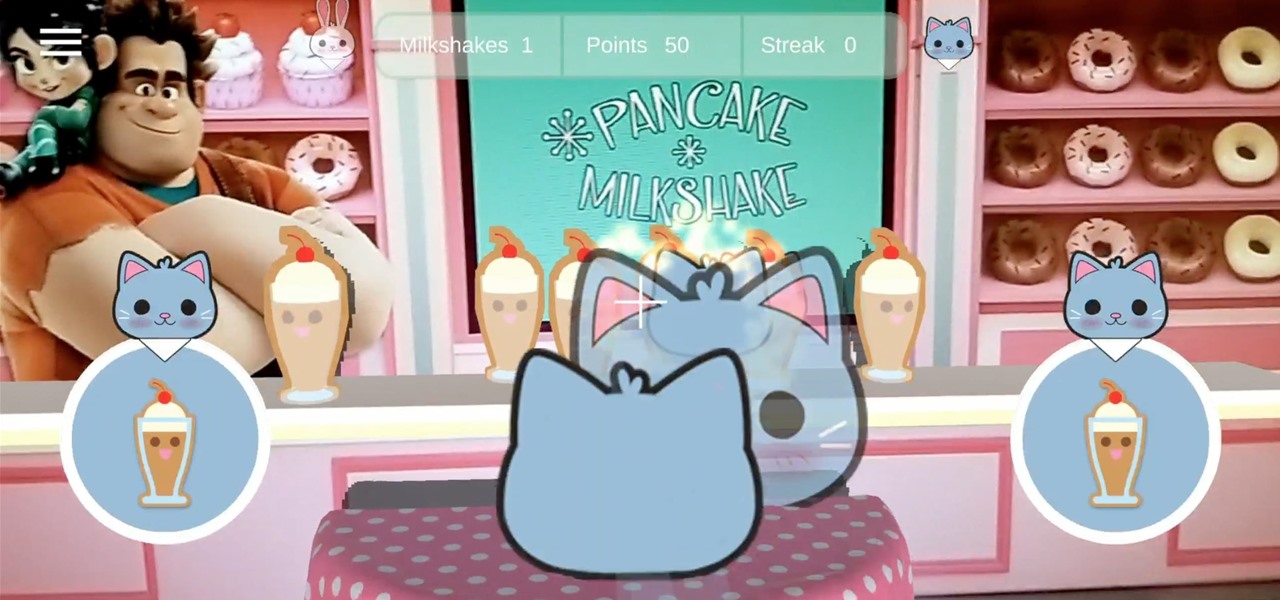
One of the funniest scenes from the teaser trailer for the Wreck-It Ralph sequel is the basis for the new pre-show augmented reality experience via the Noovie ARCade app.

While hackers have taken advantage of numerous vulnerabilities in Adobe's products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that's using the default Preview app. So think twice before double-clicking a PDF open on your MacBook — it might just be a Trojan with a rootkit inside.

We're all aware that Google collects a notable portion of our data. Thanks to the increasing awareness, Google has added a number of privacy controls to limit data collection. But Google doesn't just collect personal data for no reason — many of your favorite apps will use this info to improve their services and add new features.

With over 1 billion downloads on the Play Store alone, Google Maps has become a staple for those traveling. Its popularity is the result of Google consistently improving its accuracy and adding new functionality. And this was only achieved with help of you — specifically, your data.

Local port forwarding is good when you want to use SSH to pivot into a non-routable network. But if you want to access services on a network when you can't configure port-forwarding on a router and don't have VPN access to the network, remote port forwarding is the way to go.

With Virtual Network Computing, you don't need to carry a spare keyboard, mouse, or monitor to use your headless computer's full graphical user interface (GUI). Instead, you can connect remotely to it through any available computer or smartphone.

OpenVAS is a powerful vulnerability assessment tool. Forked from Nessus after Nessus became a proprietary product, OpenVAS stepped in to fill the niche. OpenVAS really shines for information gathering in large networks where manual scanning to establish a foothold can be time-consuming. OpenVAS is also helpful for administrators who need to identify potential security issues on a network.

In late June, the biggest measles outbreak to strike Minnesota since 1990 seemed to be winding down. Today, public health officials announced a new confirmed measles case in the area.

Rabbits have been a persistent problem in Australia for over 150 years. Now the Peel Harvey Catchment Council (PHCC) and Peel-Harvey Biosecurity Group have released a strain of the rabbit haemorrhagic disease virus (RHDV), called RHDV1 K5, to reduce the number of pests in the Murray region of New South Wales.

Antibiotic-resistant infections that usually occur only in hospital settings are spreading in communities, increasing hospital stays—and danger—for young children.

To much of the United States, Zika seems like a tropical disease that causes horrible problems in other countries but is nothing to be worried about stateside. It may make you rethink your beach vacation abroad, but not much more than that. However, if you live in Florida or Texas, the possibility of getting a Zika infection where you live is real — and local outbreaks are more and more a possibility.

If you need to do some hardcore multitasking on your Windows PC, a second monitor can go a long way towards getting things done. If you opt to "extend" your Windows desktop across a dual monitor setup, it's as if you have two computers side by side, with each display getting its own set of windows and programs that can be open simultaneously.

Step aside, Heinz: there's a new ketchup in town. Beetroot ketchup is the rising star of condiments. It's a vibrant, earthy, and sweet topping for summer BBQ burgers and grilled hot dogs, as well as a pretty un-beet-able dip for French fries. There's no corn syrup, it's paleo-friendly, and the beets give it a bright, bold flavor like no other sauce you have ever tasted.

You can now access Google's slick Weather app without having to first open the Google or News & Weather apps. However, you will have to use Google to access the weather the old-fashioned way one more time, but you'll have the option to place a shortcut on your home screen to access the weather directly going forth.

Welcome back, my tenderfoot hackers! One key area on the minds of all hackers is how to evade security devices such as an intrusion detection system (IDS) or antivirus (AV) software. This is not an issue if you create your own zero-day exploit, or capture someone else's zero-day. However, if you are using someone else's exploit or payload, such as one from Metasploit or Exploit-DB, the security devices are likely to detect it and spoil all your fun.

Welcome back, my novice hackers! In this series, we have been exploring how a forensic investigator can find evidence of illegal or illicit activity. Among other things, we have examined the registry and prefetch files for artifacts and have done some rudimentary forensic analysis. For those of you who are seeking career as a forensic investigator or security engineer, this can be invaluable training. For hackers, it might be life-saving.

Welcome back my networking geeks. In this part we are going to keep discussing about IP Addressing and I hope after you finish reading it you will become an IP wizzard.