
How To: 10 Insanely Delicious Pizza Dough Hacks
If I could survive on one food for the rest of my life, it would be pizza. The irresistible smell of baking pizza instantly makes me feel both comforted... and hungry!


If I could survive on one food for the rest of my life, it would be pizza. The irresistible smell of baking pizza instantly makes me feel both comforted... and hungry!

Welcome back, my nascent hackers! In the conclusion of the Mr. Robot television series, Elliot and fsociety successfully completed their mission of encrypting all of Evil Corp's data with AES-128 encryption and destroying the key.

Hello fellow training hackers. I do not know if many of you are familiar with ruby, but since it is a useful scripting language, that hasn't been covered too much here on Null Byte, I thought why not do some How-tos about it now and then.

What's your top pet peeve? Open-mouthed chewing? Nail biting and knuckle cracking? The sound of silverware scraping? Or perhaps it's a bigger behavior, like leaving the toilet seat up?

Hello all, this is my first submission to null byte! I noticed something a little strange, particularly that whenever Meterpreter is discussed, it is virtually always in the context of Windows. Granted, the Windows Meterpreter is more powerful than the version that can run on OS X (it has several more commands/options), but I think it is still worth noting how to do it. I've even seen some people mistakenly say that Meterpreter can only be run on Windows, which is not true. Meterpreter can ea...

If you've ever turned on an episode of Iron Chef or Top Chef, chances are you've seen a contestant in gloves and goggles, yielding a canister that looks far more fit for a chemistry lab than for a kitchen. Wonder what's in the canister? Liquid nitrogen, the go-to tool/ingredient of molecular gastronomy, and one of the trendiest items in many gourmet chefs' kitchens.

Locking your keys inside of your car is frustrating, to say the least, especially if you're in a hurry to get somewhere. You can always call AAA roadside assistance or a locksmith, but you'll probably have to fork over some money, as well as wait for them to get to you. You might even get towed.

Baking is one of life's greatest joys. There's something truly magical about taking a half a dozen humble ingredients, mixing them until they're an odd-colored sludge, tossing them into an oven, and watching them emerge as something elegant and delicious.
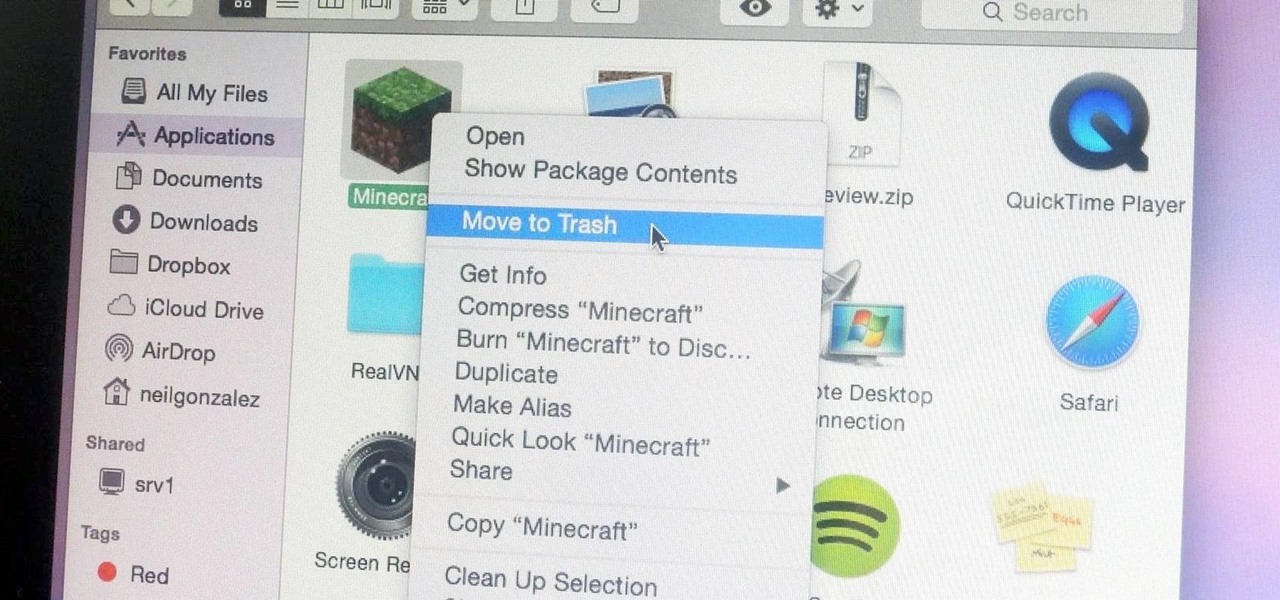
Uninstalling an app on your Mac isn't as straightforward as you would think. When you drag and drop an app into the Trash, then empty it, the main app itself may be gone, but many associated files and folders are left behind. So how do you get rid of them? There are a couple of ways.

Hi nullbytes! I've been recently reading the whole Linux Basics for the Aspiring Hacker series and felt like it was missing some stuff I know, so I felt like sharing it with anyone who might find it useful too.

Welcome back, my greenhorn hackers! Digital forensics and hacking are complementary disciplines. The better you are at digital forensics, the better hacker you are, and the better hacker you are, the better you are digital forensics. Unfortunately, few people in either profession cross these discipline lines.

With only a few days until Apple Watch preorders begin, and just a couple of weeks until its official release, the biggest question in Apple Land seems to be: "Are you going to get an Apple Watch?"

Macarons are a sweet meringue-based confection made primarily from almond flour, sugar, and egg whites. They are usually filled with buttercream, curd, or ganache. A true fat cow cook will tell you that macaron is pronounced (mah-k-uh-rohn). While it's technically not incorrect to call them macaroons (mak-uh-roon), this usually refers to coconut cookies.

If you took a big step back and really looked at the world, you'd see how downright silly our nations look when they put up fences to separate themselves from one another. Creatures big and small roam free while respecting each other's space, but humans create borders and physical barriers to delineate their cultures.
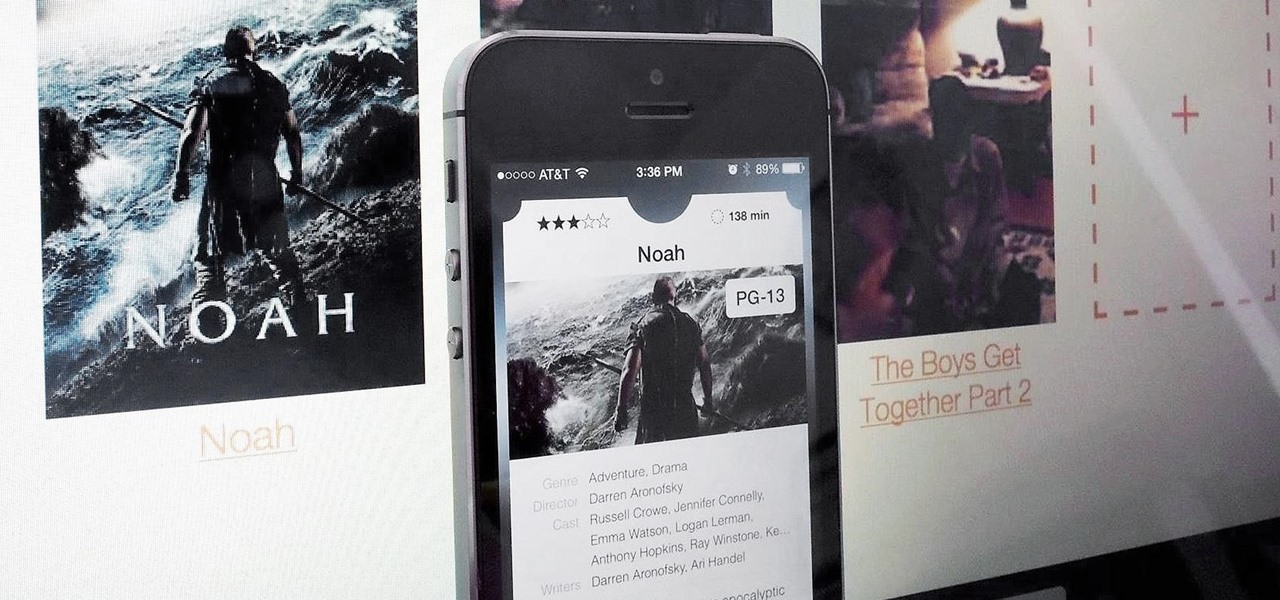
Apple prides itself on simplicity, but the company makes downloading video and music files onto your iPad or iPhone an overly complicated process, requiring iTunes and/or iCloud.
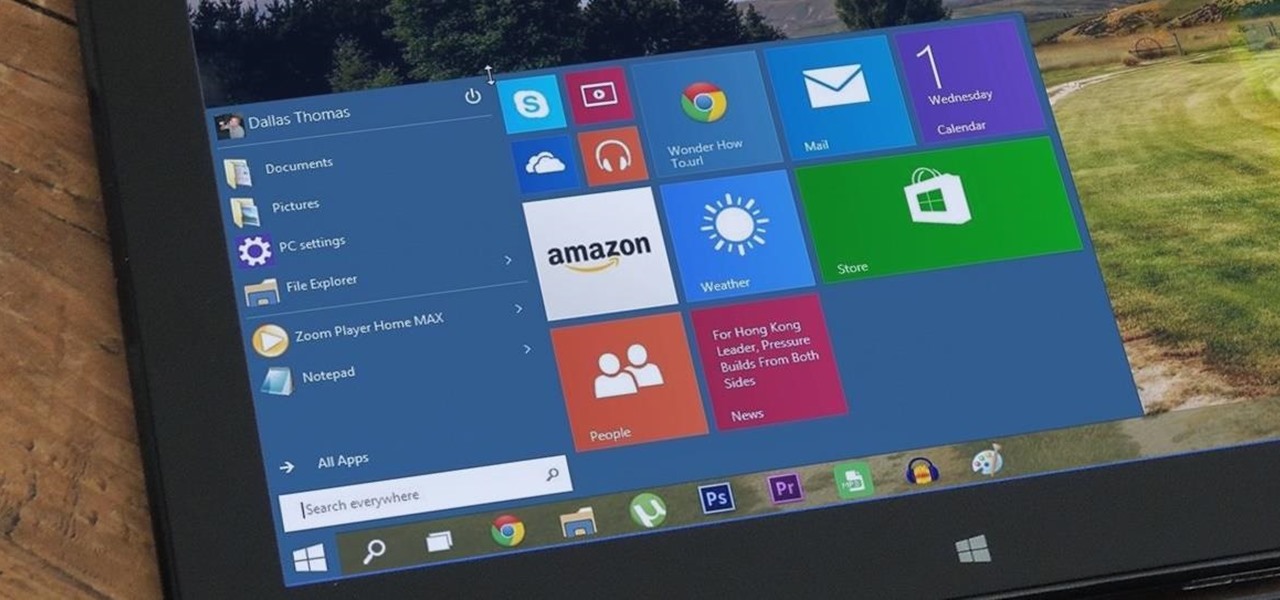
At a closed-door presentation on September 30th, 2014, Microsoft unveiled the latest iteration of its industry-leading operating system. Dubbed Windows 10 (seems as if Redmond isn't too fond of the "9" moniker), this new version brings along with it many UI optimizations and under-the-hood tweaks. With a particular focus on optimizing the interface for traditional mouse and keyboard computers, one of the most noticeable changes is the return of the Start Menu. While touch-optimized devices wi...
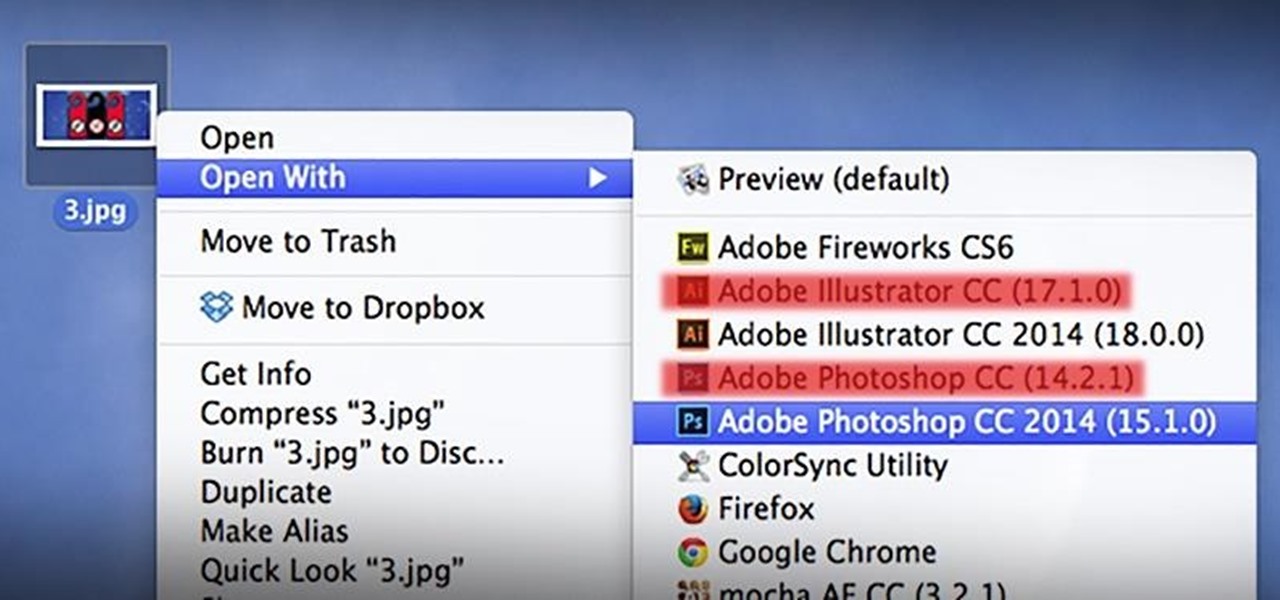
As a regular Mac OS X user, I have a love/hate relationship with the "Open With" contextual menu. Sometimes, it has just what I need. Other times, it's often packed with unnecessary or duplicate items, or missing the app I want to open the file up with the most.

It's common knowledge that certain foods foster brain development, health, and memory. Fish almost always makes the list, as do any foods that are loaded with antioxidants like blueberries, nuts, whole grains, green tea, and dark chocolate. Spices like turmeric are being studied for their ability to prevent Alzheimer's, among other things.

Cold brewing tea and coffee are all the rage, and for good reason: they're idiot-proof. I, personally, am a total dunce at brewing coffee. It either ends up strong enough to peel paint from a car or so weak that you can see through it. Meanwhile, I have friends who inevitably brew green tea to the point where it's painful to drink it.

Welcome back, my aspiring hackers! In recent tutorials, I have made reference to the name and location of the Linux devices in the file system, such as sda (first SATA or SCSI drive). Specifically, I have mentioned the way that Linux designates hard drives when making an image of a hard drive for forensic purposes.

Welcome back, my newbie hackers! Recently, I "upgraded" to Kali as my hacking platform, despite my preference for BackTrack. I did this reluctantly, primarily because new readers here could no longer download BackTrack from their site. I want to point out here that we all must keep in mind that with any software—or for that matter, any product—that is newer is not necessarily better.

Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't get caught.

If you have a good food processor or blender, there's no reason not to make your own nut butters, whether you like almond, cashew, sunflower, or the perennial classic, peanut.

With apps and games getting bigger and more memory-hungry every year, storage space is at a premium. High-definition videos and photos of innumerable pixels certainly don't help the matter, either.

The point of ice in your cocktail is to make it cold, right? Yes and no.

Welcome back, my hacker apprentices! Several of you have written asking me how you can check on whether your boyfriend, girlfriend, or spouse is cheating on you, so I dedicate this tutorial to all of you with doubts about the fidelity of your spouse, girlfriend, or boyfriend.

It's officially the holiday season, which means everyone will soon be traveling home to spend time with loved ones. And anyone who has any knowledge whatsoever of computers knows what else that means—family members left and right asking you to fix their various technical woes.

Welcome back, my greenhorn hackers! Now that we're familiar with the technologies, terminology, and the aircrack-ng suite, we can finally start hacking Wi-Fi. Our first task will be to creating an evil twin access point. Many new hackers are anxious to crack Wi-Fi passwords to gain some free bandwidth (don't worry, we'll get to that), but there are so many other Wi-Fi hacks that are far more powerful and put so much more at risk than a bit of bandwidth.

A spare key is one of those things that never seems like a huge deal until you need it. If you've ever lost your keys, had them stolen, or locked yourself out of your house or car, you know how difficult and embarrassing it can be trying to get your door open.

Here's how to make dry-ice at home, or wherever you feel like it! All you need is a pillow case, and a CO2 fire extinguisher.

TouchDevelop is a browser-based programming tool that allows anyone to build your own Windows 8 apps directly from any touchscreen device, including iPad, iPhone, Windows Phone, Android, PC and Macs. Once the script is created and the app proves to work, it can be placed in the Windows Store for free or purchase.

Many of us in the Steampunk community have pets that we love and cherish, myself included, and we want those pets to share our joy of Steampunk. In reality, they couldn't care less, but for some reason we still love to dress them up. Their reactions usually range from bemused acceptance to temper tantrums, but the awwwws we get from onlookers usually makes it worthwhile.

Apple is notoriously cryptic when it comes to the reveals of its new products, and as usual, they've kept us guessing about the release of the iPhone 5 (or "New iPhone?"). It's expected to be officially revealed on September 12, and rumor has it that sales will begin on the 21st. Though the whole world seems to be anxiously awaiting the announcement, there has also been some controversy surrounding the iPhone 5's production. With the high number of suicides and poor working conditions at Foxc...

In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack.

In the first part of this series, we took a factual and technical look at the history of the Internet. I explained how all of these wires and servers got here in the first place. Obviously, a firm did not just create and build the Internet around 1995! Now that we know how the Internet came to be, we can get into the really fun stuff—what the Internet looks like now! Well, that's not quite the network design I was talking about, but it does show what the Internet looked like back in 2007 befo...

The best chemistry experiments are those you can perform with items already laying around your house. With only some sugar, salt substitute and an instant cold pack, you can make your very own gunpowder! Being able to make homemade gunpowder without a trip to the store can be a lifesaver, no matter if it's just for testing out a Civil War-era musket, blowing up stubborn tree stumps, or preparing for battle when imperialists overrun your country.

Ready to try and sew-in your own weave? It's a big decision. As with everything that concerns our hair, we struggle with the pros and cons and often dwell on what could go wrong. Pixie cut. Perm or not? New shade (of pink, purple, or blue). These are all major decisions because ... well, it's our hair, and hair is such a big part of our style. To get a weave or not calls for careful consideration, and to sew one in yourself, that's an even bigger internal debate.

It's no secret that Apple's Notes app supports attachments such as photos, videos, and web links, as well as other file types like PDFs, word documents, spreadsheets, locations on a map, and audio tracks. While images, videos, and document scans are simple to add on an iPhone or iPad, other file types aren't as easy — at least until you know how.
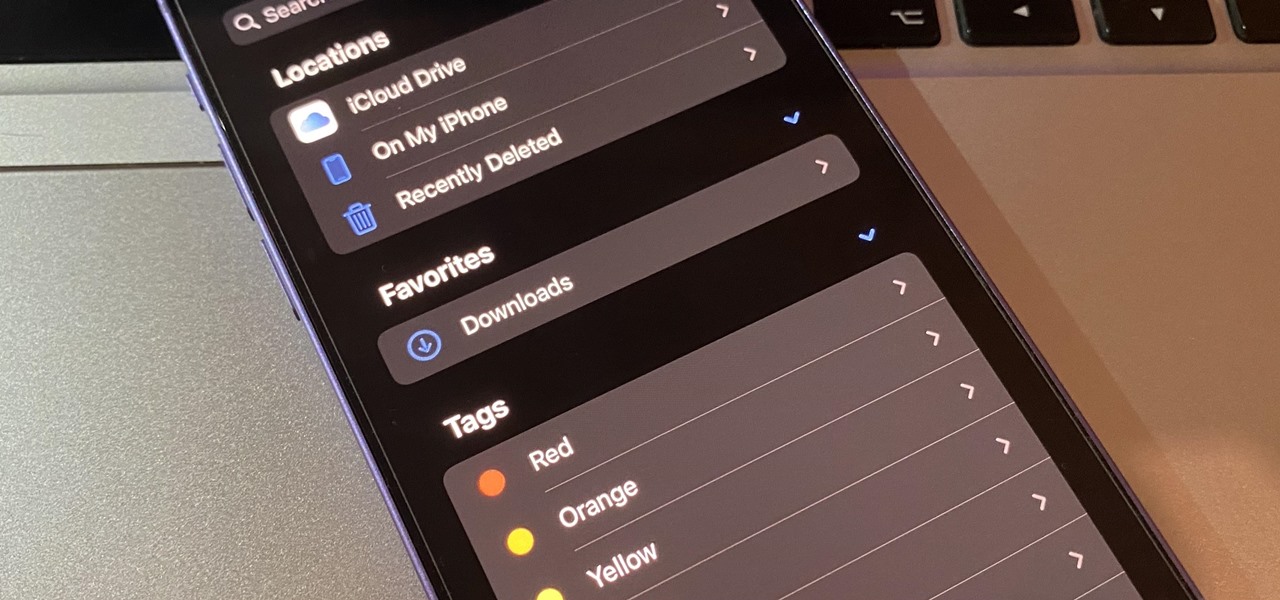
If you're not using your iPhone's Files app yet to manage images, documents, and other files on iCloud, third-party cloud services, or your local storage, it's time to start. Apple's built-in file manager is finally a powerhouse with many tricks up its sleeve in the latest software update.

Spoofed phone calls originate from one source that's disguising its phone number as a different one, and you probably get these calls all the time. Maybe they're numbers from your local area code or for prominent businesses, but the callers are just hijacking those digits to fool you into picking up. Turns out, making a spoofed call is something anybody can do — even you.