A recently confirmed polio outbreak in Syria is connected to low levels of vaccination, worsened by conflict. It is the first confirmed incidence of polio in Syria since 2014. Before 2013, the last case of polio in Syria was in 1999.
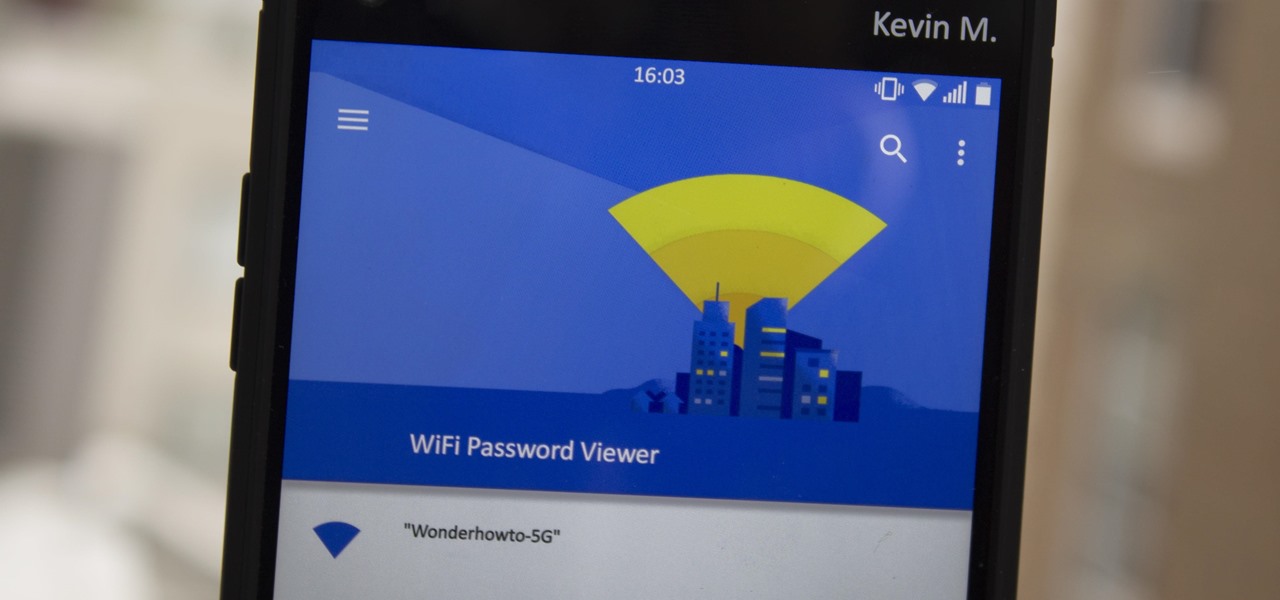
Have you ever gone to a friend's house and not asked for the Wi-Fi password? Probably not, and the same can likely be said of any friends that come over to your place. But the actual act of sharing Wi-Fi passwords is still incredibly clunky, and it's particularly hard if you have a nice and secure password with uppercase and lowercase letters, numbers, and symbols.

Disney is gearing up fully autonomous vehicles that will shuttle you and your family from the parking lot to the amusement park, stress-free. Well, as stress-free as you can get while introducing grandma to the concept of a car with no driver. No, grandma, Satan is not "steering this contraption." At least, we don't think he is ...

Every party has a pooper, and that's why you're reading this article. We don't mean to be a downer on such a fun day as 4/20, but it's important to make sure you know about the source of your pot, especially if you're one of the 2,299,016 people who use medical marijuana in the US.

Here's another workday distraction for all you social media lovers out there: Pasted, launching out of beta today on iOS, is a simple collage and photo editing app mixing iconic '90s imagery with a love of the The Shins.

Google, the company that rules the internet, is now testing a method to leverage its machine learning with its ubiquitous presence on mobile devices. The new model they're employing is called Federated Learning, and it hopes to apply artificial intelligence to Google's services on Android without compromising user privacy.

Oh, Waze—you know, that Google-owned traffic navigation app that tempts drivers into stopping at local food joints like Dunkin' Donuts and Taco Bell? Well, now you can even order a large iced coffee through the app before you even arrive at a fast food hotspot.

Amazon has been toying with the idea of opening physical retail stores for some time now, even opening old-fashioned bookstores in select locations and teasing cashier-less convenience stores. But the online retailer has some new ideas in the works, including implementing virtual and augmented reality into retail home stores.

Some Montana inhabitants have been making impassioned pleas to legalize raw milk this week. The debate took place during a hearing on House Bill 325, which was held by the Senate Agriculture, Livestock, and Irrigation Committee on Tuesday, March 21.

Google Assistant has introduced tappable shortcuts on the Google app for Android, iOS, and Google.com this week.

China just confirmed a sixth avian flu outbreak since October. On Tuesday, the Ministry of Agriculture stated that there had been another instance of bird flu in the Hubei province, of the H5N6 influenza virus. The outbreak occurred in the city of Daye, which is home to some 900,000 people, but hasn't been linked to human infections yet.

ProtonMail has long been the favorite of journalists and security-conscious professionals, with Edward Snowden the most famous example. But these days, everyone cares about anonymity, so it's no surprise that ProtonMail currently has over 2 million users. And now the service is even better.

Magic Leap, the mysterious Florida-based mixed reality start-up, announced on Wednesday that it would be opening a 260,000 square-foot expansion in Florida, and bringing along with it 725 new jobs over a five-year period. To make this happen, they will be making an $150 million capital investment, with government incentives, of course.

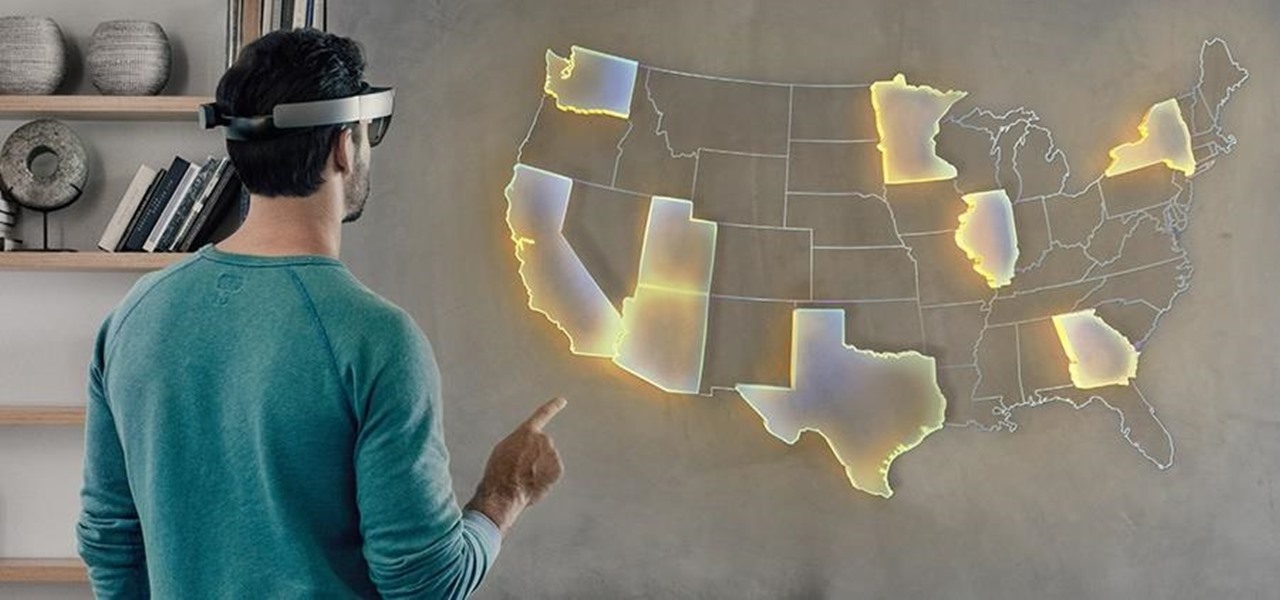
The HoloLens is the world's first untethered holographic head-mounted computer, which Microsoft has been rather proud of—and they have every reason to be. Of course, as soon as we developers get adjusted to the idea of keeping the scope of our projects inside the bounds of the HoloLens' processing power, Microsoft hits us with the Holographic Remoting Player.

With some of the groundwork out of the way in getting a Mac set up for hacking, it's time to start looking at toolboxes. Our first toolbox is Git, which will be used throughout future tutorials.

When you're on the road, the last thing you need to be doing is fumbling around with your phone. But with online radio services like Spotify and Google Play Music, you almost have to use your phone to play music through your stereo, because the in-dash head units on most cars lack the ability to connect to these services.

Mixed reality (MR) feels like an amazing, almost mind-blowing futuristic technology—but only once you've experienced it for yourself. Words, images, and even videos simply cannot describe the experience in full. If you want to really peer into the future and experience MR for yourself, you can sign up and just go in many cities.

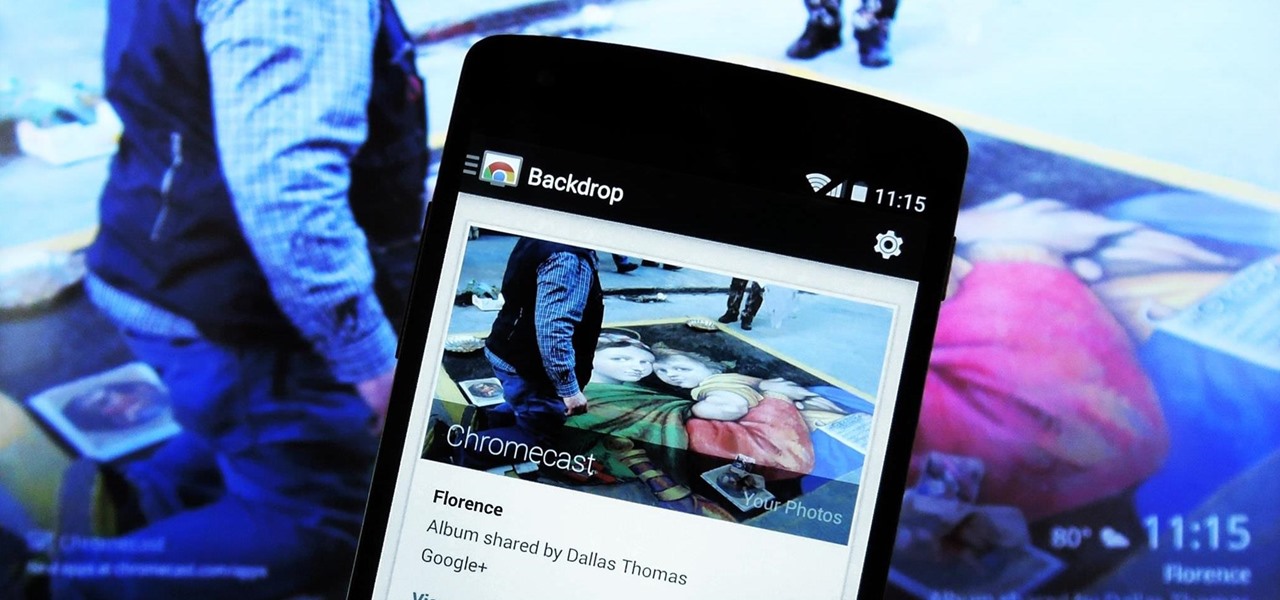
Much like the Chromecast, Android TV devices such as the Nexus Player and Nvidia Shield TV have always had those beautiful background images as their default screensaver. However, unlike the Chromecast, these "Backdrop" images, as they're called, weren't always customizable on Android TV.

In this series you will learn how to use PHP to perform attacks, gather information, and setup backdoors. Along with performing attacks you will learn how to protect yourself from them. In this part you will learn about PHP as well as install Apache and PHP. What you'll need for this series

This video will show you How to Remove The Front Bumper Cover on a 05-07 Audi A4

When performing something such as a mass mailer attack on a company, sending executables usually isn't the best option. That's why, in this tutorial, I'll be teaching you how to code a VBA script macro into a Word document in order to compromise a system. Combined with a little social engineering, this can be a very effective technique.

A lot of people think that TOR services are unhackable because they are on a "secure environment", but the truth is that those services are exactly the same that run on any normal server, and can be hacked with the same tools (metasploit,hydra,sqlmap...), the only thing you have to do is launch a transparent proxy that pass all your packets through the TOR network to the hidden service.

With the explosive popularity of both Thor himself and The Avengers, Thor is an obvious good choice for a Halloween costume. But you don't have to opt for one of the pricey, pre-made costume choices found in every Halloween store in every city. Instead, craft your own in just a few steps, saving yourself money in the process.

welcome back my masters , teachers and classmates , in this second part of this 0-day series we will learn the basic of fuzzing, and i bought some gift for nullbyte(a 0 day vuln that will be released today exclusively on null-byte) .

Step aside, vodka—whiskey will soon be the best-selling hard liquor in the United States. The whiskey renaissance has been largely attributed to the current trend for locally- and artisan-produced goods. Local whiskey distilleries are rapidly increasing in number across the nation while bars in every state are including the old-fashioned cocktail on their menus in an attempt to capitalize on the trend (which we can probably thank Mad Men for).

If you've just ditched your Android phone for a new iPhone, you're in luck, because Apple has a way to make your transition as simple as possible with their Move to iOS app for Android. To help make things even easier on you, we've outlined the process of using Move to iOS to transfer images, messages, contacts, mail accounts, calendars, and more over to your iPad or iPhone running iOS 10.

This tutorial is for people who want to try different types of hacks in an environment that is the same for everyone so it will help people to ask questions and learn. This series assumes you know how to run a VM and network them together. This series also assumes that the services running on the Metasploitable machine are needed to be running.

If you've been watching the latest USA TV Series Mr Robot, you will have seen the Raspberry Pi used by Fsoeciety to control the HVAC system. OTW covers this very well here with his take on setup they may of used.

When you go to the grocery store, chances are you're confronted with the usual piles of apples, berries, bananas, and melons. All well and good, right?

bObi has four floor detection sensors on her underside that warn her not to drive over ledges and stop her from falling down stairs.

The bumper for bObsweep Pethair and Standard are installed the same way. It holds the sensors that allow Bob to see any obstacles in his path. If a repair of the wall detection sensors is needed, the steps for replacing the whole bumper are the same when working on either bObsweep model.

Crochet Weave with Xpression Hair takes some proper care. It is just like having your hair relaxed; the hair is that texture.

The basics of how to pack personal gear for a canoe trip. This video doesn't cover food or larger gear like tents and canoes, but the rest is covered. Enjoy!

Welcome back, my neophyte hackers! In previous tutorials, we learned how to steal system tokens that we could use to access resources, how to use hashdump to pull password hashes from a local system, and how to grab password hashes from a local system and crack them.

While honey is one of the most popular ingredients on kitchen shelves the world over, honeybee pollen is still a relatively rare find in most households. It's not hard to guess why: eating pollen just sounds weird... it would probably sell a lot better if it had a more appetizing name, like honey. Furthermore, it looks unlike any other common ingredient, and the smell can be off-putting to some. But it's good, it's healthy, and it's altogether pretty awesome!

This requires a dry hen's egg at room temperature. Hold an egg near a candle flame to cover it with soot. It will need to be completely covered. This is tricky, because if the egg is a tiny bit damp the soot will easily flake off on to your fingers as you turn the egg. Once the egg has a nice black sooty coating, gently immerse it in a bowl of water.

Hi Elite Hackers! Welcome! to my 4th post. This tutorial will explain, how to extend a (hacked) AP's range with a wireless adapter. I made this guide because after hacking an AP it was difficult to connect to it (poor connection) and further exploit it. You can also use this:

One of the best things about talking to other people who love food is that they point you to weirdly beautiful ingredients, like this: No, that's not an escapee from Middle Earth you're seeing. It's one of Mother Nature's best attempts at making fractals come alive into a golden spiral: the Romanesco (sometimes called fractal broccoli, broccoflower, or Romanesque cauliflower). Here's another view: So Just What Is It & What Does It Taste Like?

Who says you have to cook on Thanksgiving? If you need a break, have surprise guests in town, or simply don't want to be in the kitchen cooking all day long, never fear: you have options.

It's been a long-awaited feature since being announced at Google I/O in June, but Backdrop for Chromecast has finally started rolling out. With an update to the Chromecast app for Android and iOS, users will be able to personalize the background images that appear when Chromecast is idle.