Kipkay shows you how to escape from a pair of handcuffs with only a bobby pin just like Harry Houdini did. You peel away the plastic protective covering from the bobby pin and you put the end of the bobby pin in the keyhole of the handcuffs.

Fill your friends spray deodorant with paint and give them a great surprise when they cover their armpits with paint. This is a great dorm prank. Use this as inspiration for one of your April Fools Day pranks!

This tutorial covers how to use layers to composite footage together and then how to keyframe footage layers. The tutorial gives a clear and easy step-by-step breakdown of using compositing and keyframing in Final Cut Pro 6.

From the Sahara Hotel in Las Vegas comes this helpful tutorial video teaching you how to play blackjack. This video covers everything you need to know before ante up.

If you're going to ride a dirt bike, you better learn how to ride it right. With tips and instructions for both the novice and experienced bike rider, this video covers everything from positioning yourself on the bike to riding over obstacles and uphill.

In last week's guide, we covered the best places to purchase digital copies of computer games online. This week we'll cover another type of downloadable content: those available for video game consoles. Every major console out today either has or plans to have a DLC platform, but which one is the best? If you don't like leaving your house and want to play console video games, which console should you get? Below I will break down what the online marketplace offers so you can decide which conso...

In this economy being competitive for a job means your application must stand out above the rest. Here's how to write a cover letter to successfully introduce your resume. Make sure your cover letter follows business letter format. Your name and address must be written at the top left corner. The employer's name and address are written just below. The letter should be addressed to a specific person within the company. Paragraphs in a business letter are not indented, but instead are left just...

This video will cover how to overlay textures using Corel Paint Shop Pro Photo XI.

A lot of time can be wasted performing trivial tasks over and over again, and it's especially true when it comes to hacking and penetration testing. Trying different shells to own a target, and testing out privilege escalation commands afterward, can eat up a lot of time. Fortunately, there is a tool called One-Lin3r that can quickly generate shells, privesc commands, and more.

We love our set of Apple AirPods. The battery could last a little longer, but overall, there's only one gripe we really have: the dirt that builds up inside the case. Whether you stick it in your pocket, a backpack, or your purse, the inside of the case's lid and main base will get dirty in a week, give or take. But there's a way to stop that from happening.

Windows 10 passwords stored as NTLM hashes can be dumped and exfiltrated to an attacker's system in seconds. The hashes can be very easily brute-forced and cracked to reveal the passwords in plaintext using a combination of tools, including Mimikatz, ProcDump, John the Ripper, and Hashcat.

With just one line of Ruby code embedded into a fake PDF, a hacker can remotely control any Mac computer from anywhere in the world. Creating the command is the easy part, but getting the target to open the code is where a hacker will need to get creative.

Just in time for Women's Equality Day on Aug. 26, Treasury Wine Estates is breaking out a line of wines with augmented reality experiences that pay tribute to historically famous women.

While hackers have taken advantage of numerous vulnerabilities in Adobe's products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that's using the default Preview app. So think twice before double-clicking a PDF open on your MacBook — it might just be a Trojan with a rootkit inside.

One of the most successful rock bands still making music has just made augmented reality an integral part of its upcoming tour. Irish rock band U2 has announced a new mobile app experience that allows you to preview the group's live performance in your own home in AR.

With over 1 billion downloads on the Play Store alone, Google Maps has become a staple for those traveling. Its popularity is the result of Google consistently improving its accuracy and adding new functionality. And this was only achieved with help of you — specifically, your data.

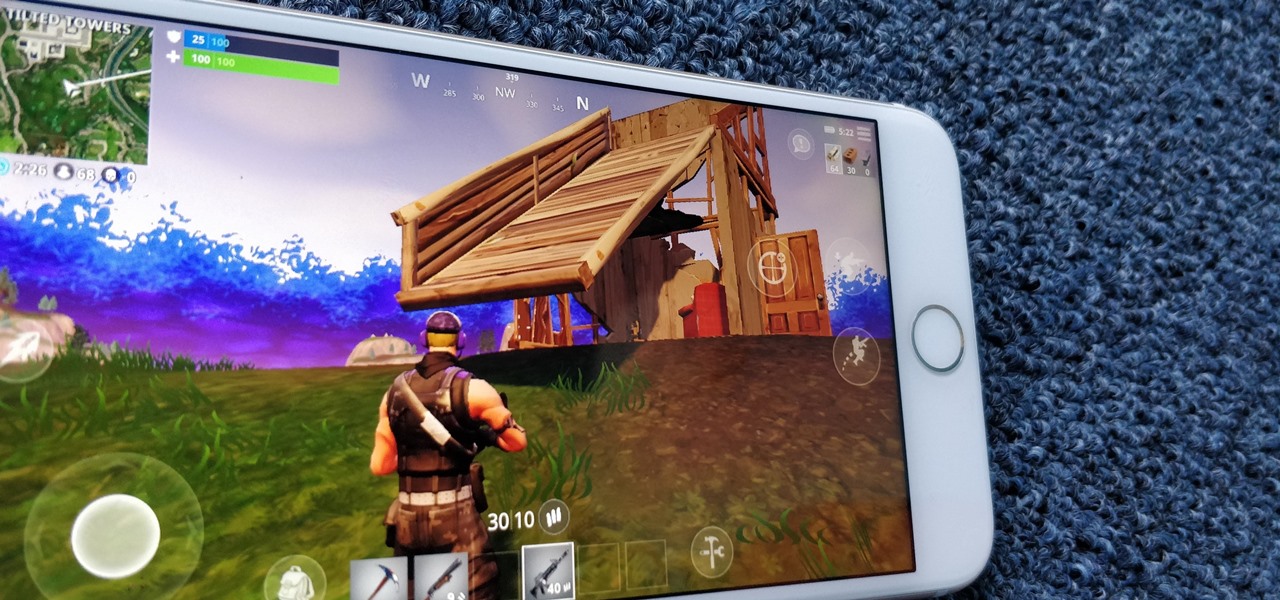
One of the more unique aspects of Fortnite Battle Royale is the ability to create structures. Using in-game materials, players can create walls and ramps for cover and to extend mobility. But creating isn't limited to just the basic generic structures. To really maximize their benefits, great players edit their creations to fit their needs.

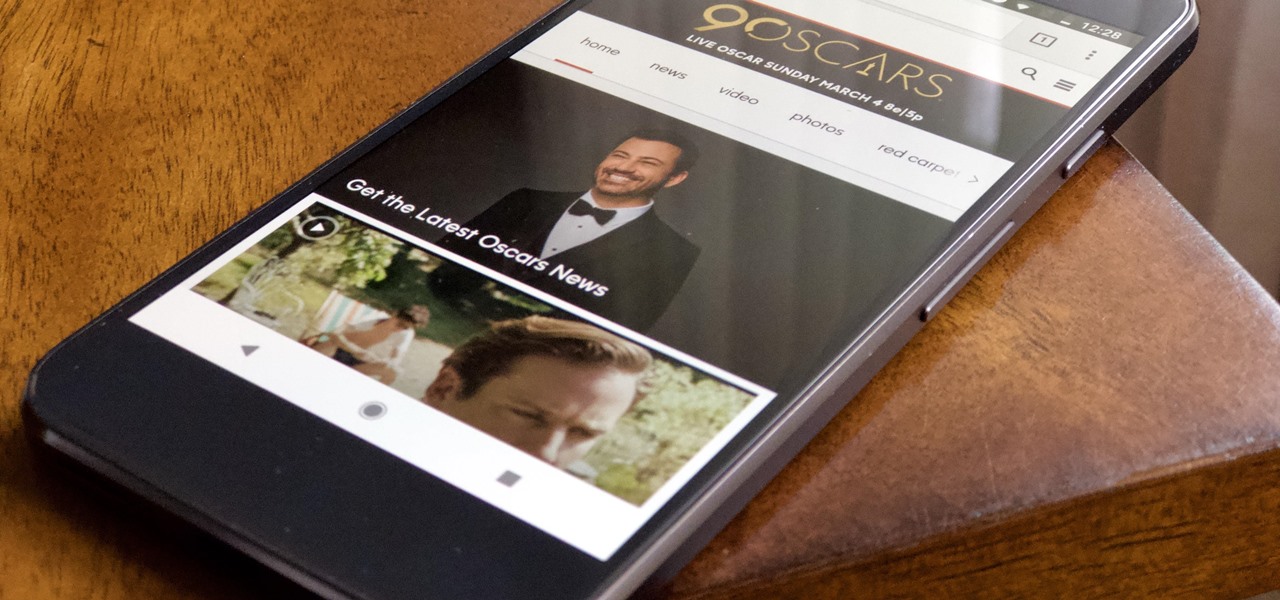
Another year, another Oscars. This year's red carpet coverage kicks off Sunday, March 4, at 6:30 p.m. EST, while the ceremony itself starts at 8:00 p.m. EST. Finding a stream online isn't always the most straightforward endeavor, especially if you want it to be free. To avoid any delays on the night itself, make sure to run through your viewing options here.

Old school media stalwart Sports Illustrated is billing this year's Swimsuit Issue as the "Most Immersive Experience Ever," and it certainly lives up to that statement, as the magazine has added augmented reality and virtual reality experiences to this year's version via Snapchat and the Life VR app.

Local port forwarding is good when you want to use SSH to pivot into a non-routable network. But if you want to access services on a network when you can't configure port-forwarding on a router and don't have VPN access to the network, remote port forwarding is the way to go.

A potentially groundbreaking new app targeting retail financial services hopes to bring augmented reality to your local bank and credit union.

OpenVAS is a powerful vulnerability assessment tool. Forked from Nessus after Nessus became a proprietary product, OpenVAS stepped in to fill the niche. OpenVAS really shines for information gathering in large networks where manual scanning to establish a foothold can be time-consuming. OpenVAS is also helpful for administrators who need to identify potential security issues on a network.

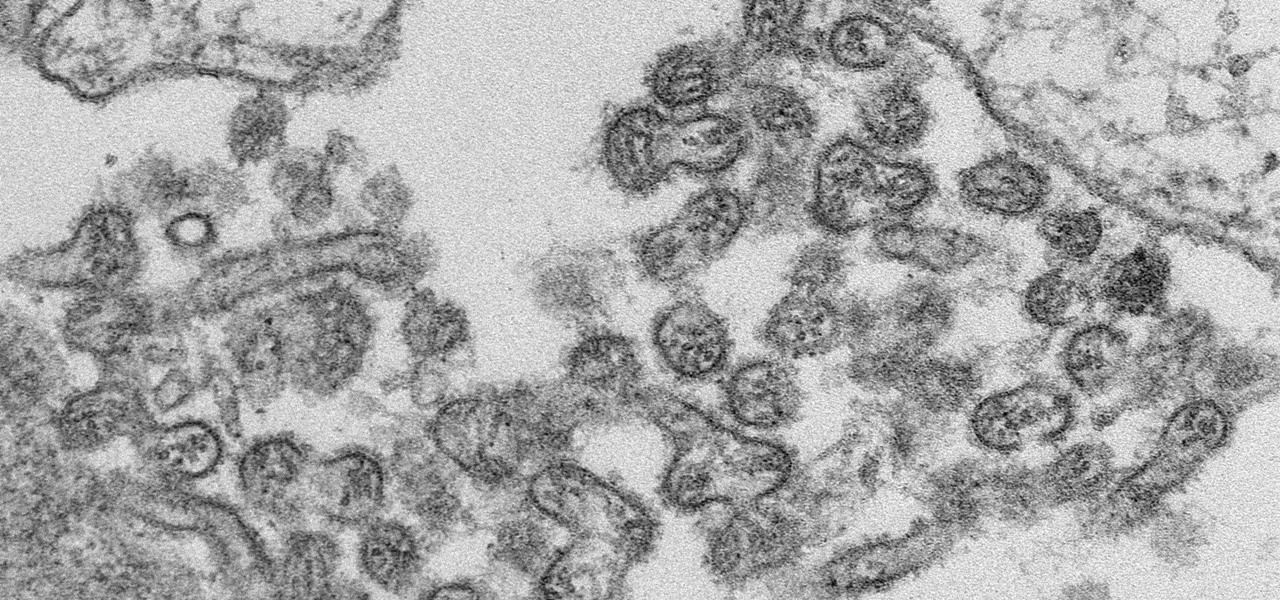
A new case of the still-mysterious Bourbon virus was confirmed in Missouri, likely originating within the state, local authorities said in a June 30 press release.

With chips in four out every five PCs made since 2010, few companies are as pervasive in modern computing as Intel. That's why an advisory released Monday, May 1, confirming a remotely exploitable vulnerability in all non-server business hardware made in the last seven years has sent shockwaves through the technology world.

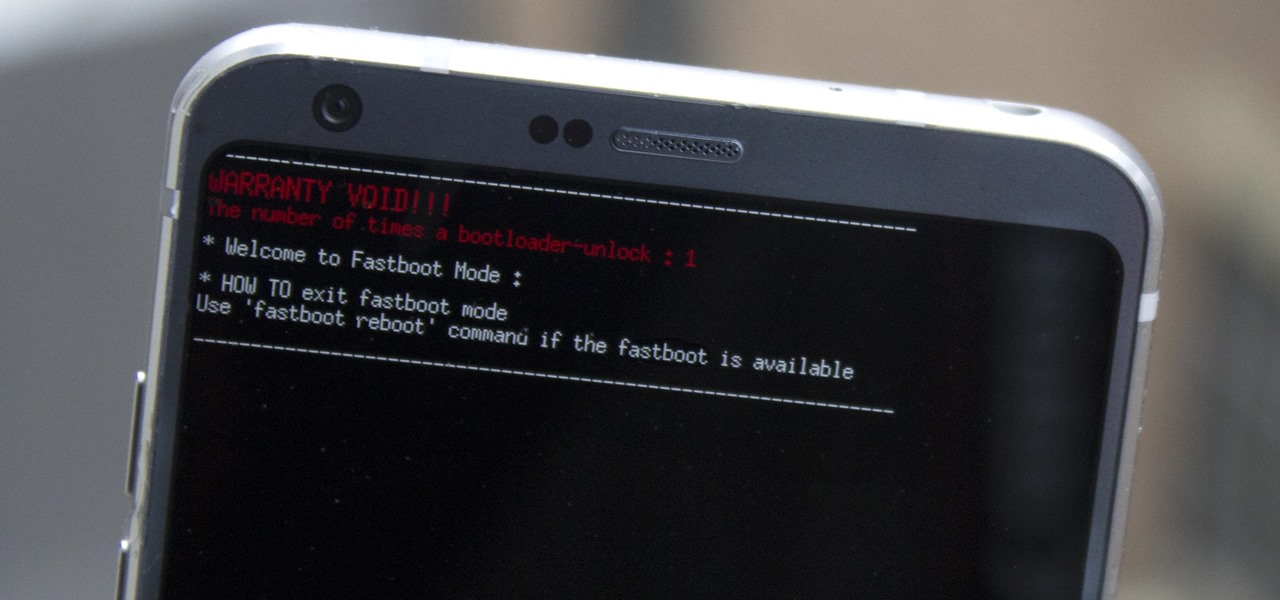
Preorders for the LG G6 have all been fulfilled, and the phone has been up for grabs at local cell phone providers for three weeks now. However, not every LG G6 was created and released equally. The T-Mobile variant of the LG G6 features an unlockable bootloader, while most other North American variants come with a tightly locked down bootloader, which effectively limits the full potential of your brand new fairly expensive phone.

Reports of Zika-related birth defects are coming in at shockingly low rates in Puerto Rico. While that might be something to cheer, one former US government official is saying there could be a nefarious reason for the low numbers.

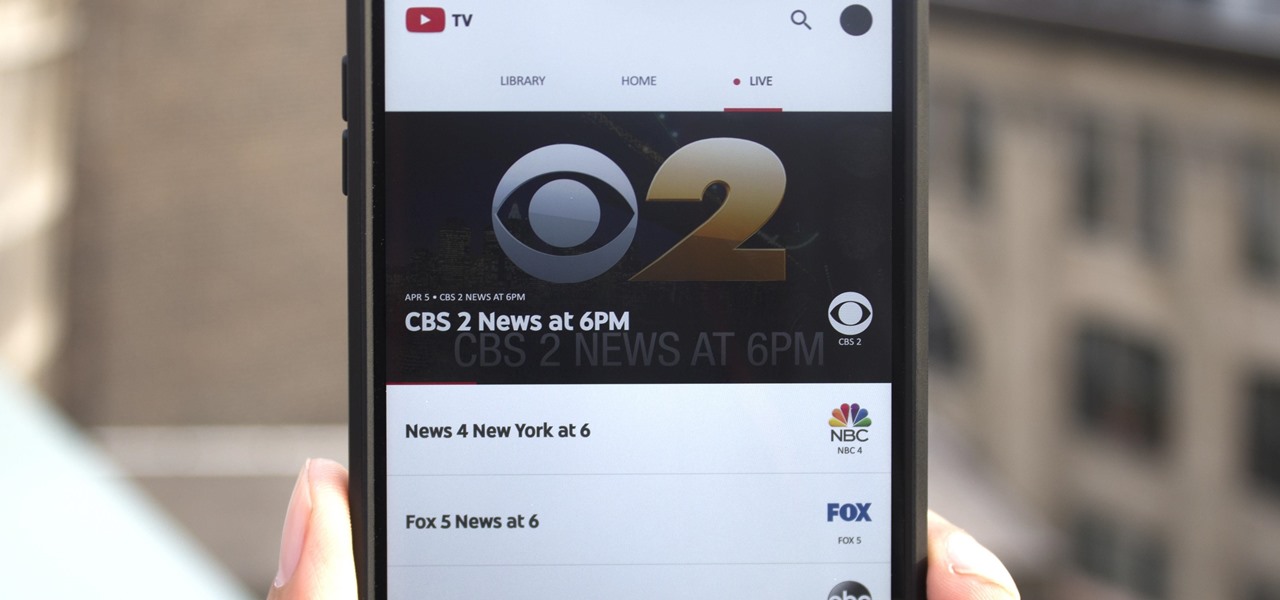
As you may have heard by now, YouTube has launched its own live streaming TV bundle available for users in the select markets of New York, Los Angeles, the Bay Area, Chicago, and Philadelphia. A subscription to the new streaming YouTube TV bundle costs $35 a month, but the service is drawing in users by offering a free 30-day trial.

To much of the United States, Zika seems like a tropical disease that causes horrible problems in other countries but is nothing to be worried about stateside. It may make you rethink your beach vacation abroad, but not much more than that. However, if you live in Florida or Texas, the possibility of getting a Zika infection where you live is real — and local outbreaks are more and more a possibility.

Google's new Pixel and Pixel XL smartphones have a feature that puts their fingerprint scanners to use after you unlock your phone—just swipe down on the scanner from any screen, then you'll see your notifications. It keeps you from having to do hand gymnastics to reach the status bar at the top of your screen, and it gives you easy access to quick information, so it's a win-win.

During the summer, fresh strawberries are everywhere: at your neighborhood farmers market and in many desserts like strawberry shortcake and strawberry rhubarb pie, to name just a couple. Bringing home a few baskets of the ruby red fruit always seems like a good idea... until they begin to turn to mush or grow mold only a few days later.

We're on the verge of an amazing evolution of technology where we can work and play in virtual worlds that merge with our own—or let us escape into our imaginations entirely. But creating virtual, mixed, and augmented reality experiences requires resources and hardware that not everyone has access to. If you want to build something awesome with the Microsoft HoloLens (or one of the other awesome platforms), we want to help you do just that.

Music is definitely more immersive when it's accompanied by a bit of visual stimuli, which is why CyanogenMod and other custom ROMs have started integrating music visualizers into elements of the Android system UI. It's a great effect, but it's not necessarily something that's worth replacing your stock firmware over.

Welcome back, my greenhorn hackers! As expected with Null Byte's dramatic growth over the last year, we have added many new aspiring hackers who are still lacking in the basics of networking. In addition, with the new "White Hat" certifications coming out shortly, the exam will require some basic networking skills and knowledge to pass.

Welcome back, my aspiring hackers! In many of my earlier tutorials, I mentioned the complementary nature of hacking and forensics. Both disciplines, hacking and forensics, benefit from a knowledge of the other. In many cases, both disciplines will use the same tool. In this tutorial, we will use another tool that can be used in either discipline—Sysinternals—a suite of tools developed by Mark Russinovich.

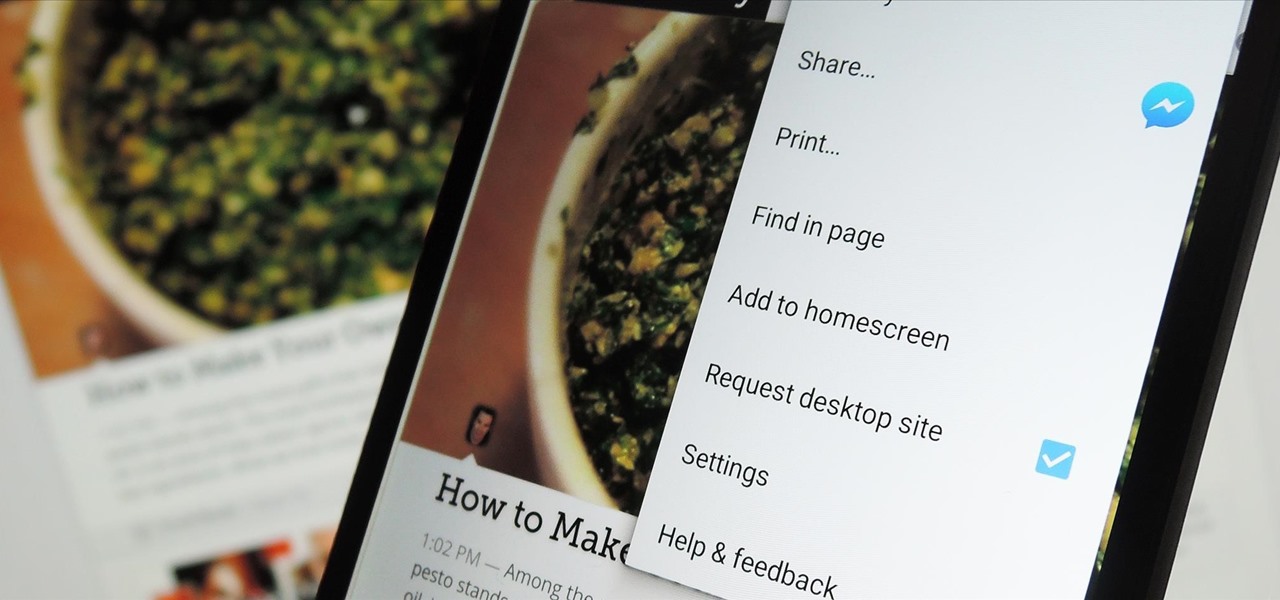
The majority of Android web browsers carry a "desktop mode" feature that makes mobile websites look like normal computer versions. Mobile versions are designed to work faster and more efficiently on smartphones, but sometimes the desktop version looks better on large displays or has additional features not included in the mobile one.

A great Halloween party depends on the right spooky ambience. Having some shrunken heads in strategic locations is an easy, fun way to get your guests in the right (frightened) frame of mind, and they require items you can easily find in your kitchen or at the local grocery store.

Welcome back, my aspiring hackers! In previous tutorials, I have shown you how to scan the globe for vulnerable servers and write simple scripts in BASH and Perl to perform other reconnaissance tasks. In a very recent guide, I taught how to scan vulnerable servers for Heartbleed.

There are a gazillion lock screen apps available on Google Play, but the majority of them are subpar and not worth your time. However, in my opinion, there is definitely one out there worth your time—one that constantly learns and adapts to what apps you use when and where to determine which shortcuts to give you.

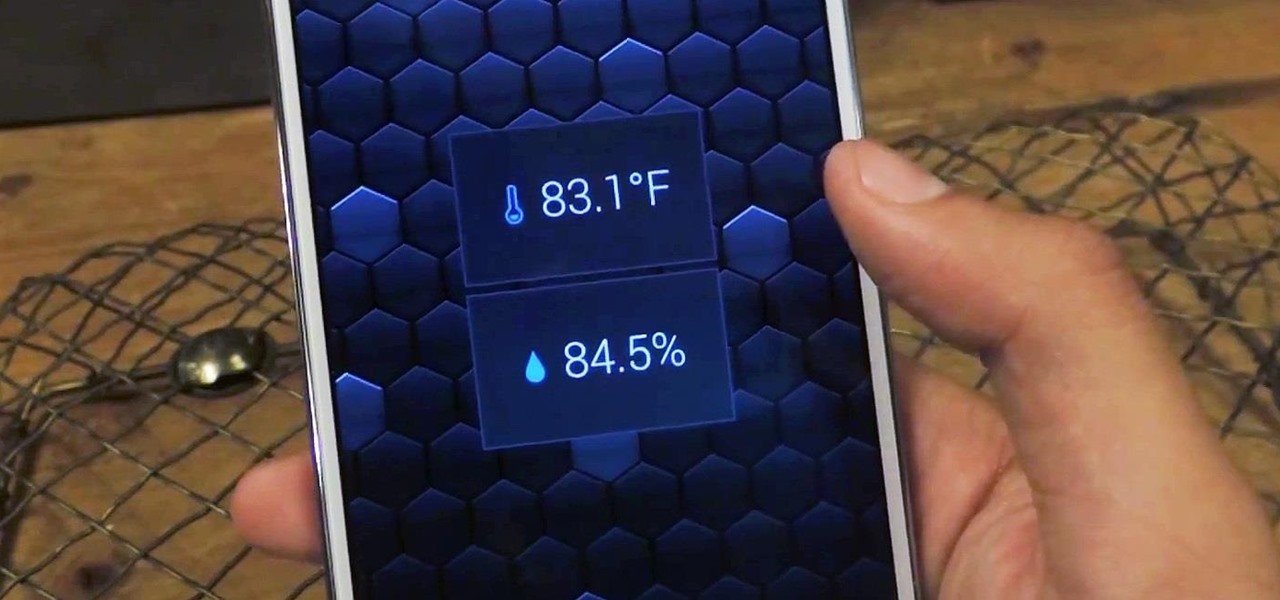
The majority of Android devices have built-in sensors underneath the hood that measure motion, position, and several environmental parameters that provide data needed to monitor your movements and adjust accordingly.

Sometimes the best place to hide something is where people least expect it, so in this project, we're making a super secret safe that only you'll know about.