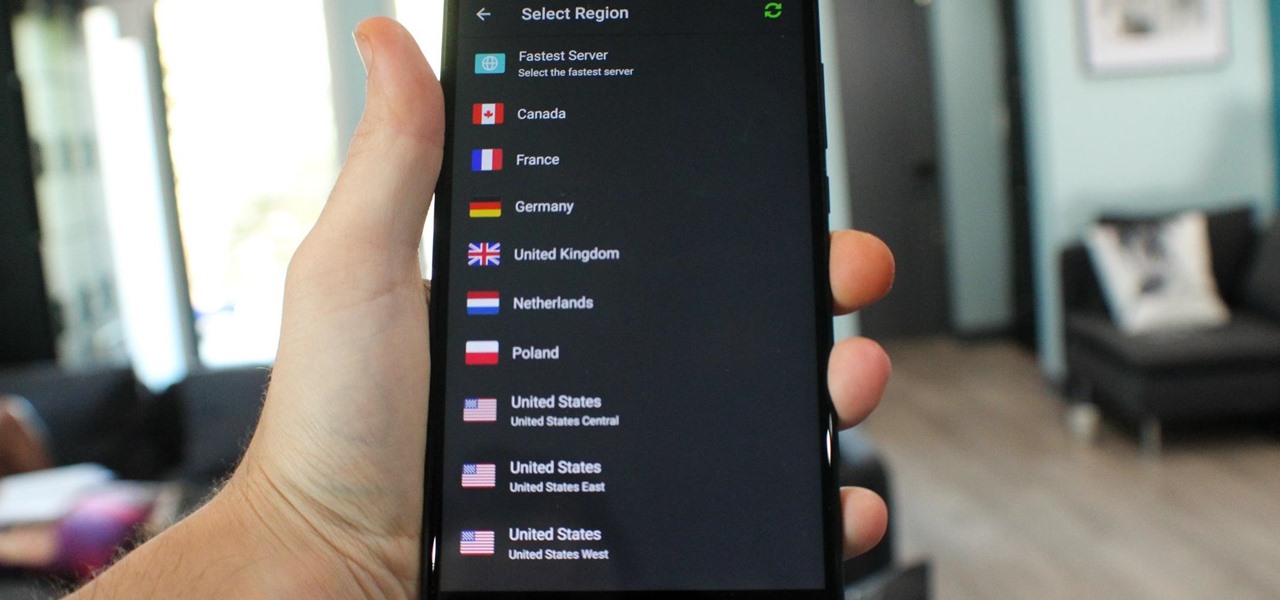
What you see when you open the Play Store is completely dependent on your country settings. Search results and top charts are specific to each region and there are lots of popular apps and games that simply won't show up unless your Play Store country matches up.

On Friday, the release date for her new album, Queen, Nicki Minaj is already grabbing headlines for the track "Barbie Dreams," where she disses Drake and a host of other rappers.

Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the device. As an alternative, we'll use the lesser-known Tcl shell which can handle abrupt backdoor disconnections.

With the rise of website encryption (TLS), sniffing passwords from network activity has become difficult. However, it's still possible to quietly exfiltrate a target's network traffic in real time to extract passwords and sensitive information. Pertaining to macOS, there are two methods for retrieving traffic from a backdoored Mac.

Regal Cinema's augmented reality magazine Moviebill enjoyed a big debut in April and it has its sights set on an even bigger (virtually) outing with its next edition.

We're all aware that Google collects a notable portion of our data. Thanks to the increasing awareness, Google has added a number of privacy controls to limit data collection. But Google doesn't just collect personal data for no reason — many of your favorite apps will use this info to improve their services and add new features.

Google collects an enormous amount of personal data. While some of this data is used for targeted ads, others tidbits of info such as our location are used to improve our mobile experience. While it is natural for us to distrust Google's intentions, by allowing their data collection, we can add new functionality to our favorite apps.

The latest cosmetics brand to launch its own augmented reality try-on tool is Cover Girl, which introduced its browser-based experience this week.

Super Bowl LII will bring millions of football and non-football fans together to watch the big game on the big screen. But without a cable subscription, this process can be a little daunting. Luckily, the Google Play Store and the iOS App Store offer a few ways to accomplish this — no cable contract required.

With Virtual Network Computing, you don't need to carry a spare keyboard, mouse, or monitor to use your headless computer's full graphical user interface (GUI). Instead, you can connect remotely to it through any available computer or smartphone.

Instagram stories are a great way to share your day-to-day experiences with your followers. However, it can be disappointing to see them go after 24 hours, especially if you shared something really special. Now, Instagram has a way for you and your followers to relive those great stories you've created with a new feature called Story Highlights.

While not specifically an augmented reality conference, IFA 2017 packed a plethora of presentations with AR themes, including devices with AR features from Sony and Motorola, a smartphone-based AR headset from Lenovo, and a new processor from Huawei that will facilitate AR experiences.

If you have a taste for sweets, you have at least one thing in common with mosquitoes. While too much sugar is unhealthy for humans, a new product makes sweets deadly to mosquitoes.

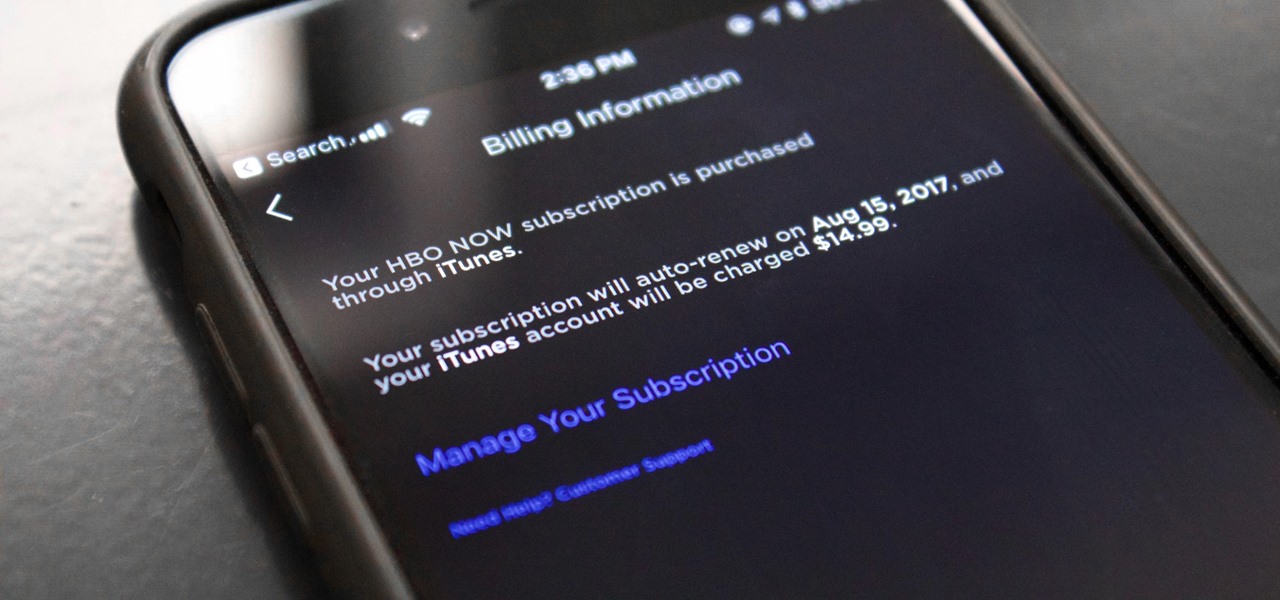
I'm a little biased — I love HBO. I wouldn't want to cancel my subscription, because there are constantly shows I want to watch. But I understand not everyone is like me. Some people might only subscribe to watch, say, Game of Thrones, then cancel their subscription when the show ends. In that case, if you're reading this before July 30th, you'll want to use this information five episodes from now.

Who said sports need parity to be fun? For the third year in a row, the Cleveland Cavaliers are facing off against the Golden State Warriors on the NBA's biggest stage, and basketball fans everywhere couldn't be more excited.

Colorado State University scientists have developed new tech that quickly identifies the presence of Zika virus in mosquito populations — and in human body fluid.

Who likes security? I like security. I lock my doors at night, and so should you! That's why it's exciting to me that Samsung has just announced its May security update. It's like getting a brand new, top-of-the-line lock for free, but for your phone.

At this point in our series on creating a customized hacking container, you should be able to use Docker to save and retrieve customized instances of Ubuntu from your own machine. Make sure to revisit part one and part two if you need a refresher.

Containers are isolated software instances representing applications, servers, and even operating systems—complete with all of their dependencies, libraries configuration files, etc.—and they're taking over the corporate world. The ephemeral, portable nature of containers help them stay current and speedy, and they can work on pretty much any computer, virtual machine, and cloud.

With all of the bare-bones setup out of the way in our Mac for Hackers series, your Apple machine should be ready to run a significant amount of pentesting tools. We can pull tools from GitHub and compile them, we can pull dependencies or tools from Homebrew, we have both Python and Ruby. Everything is ready to go and now it's time to start building a toolbox on our local host.

When Apple announced its new iPhone 7 and iPhone 7 Plus models in San Francisco, one of the biggest new features was an "IP67" water-resistance rating. Couple that with a few official renderings that show the new iPhone covered in water, and you'd probably arrive at one logical conclusion: The iPhone 7 is waterproof.

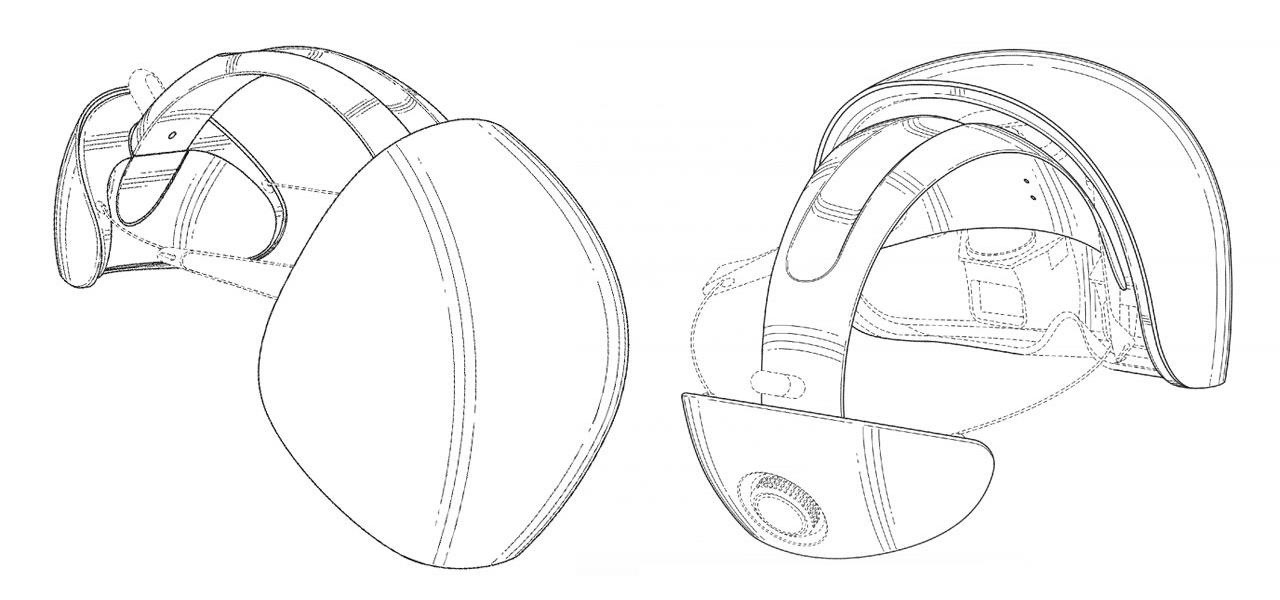
We've experienced the HoloLens, learned a lot about the Meta 2, but almost nobody knows exactly what to expect out of Magic Leap's mixed reality headset. Thanks to a patent dug up by Quartz (which we saw first on Tech Insider), we now might have a better idea.

Don't Miss: Revolutionary Pasta Hacks You Need to Know

Welcome back everyone! It's been awhile hasn't it? Sorry for being so quiet, but my CCNA courses have really picked up recently. In the last article we covered how to import modules and how we can use them. In this article, we'll actually be covering a module that is essential to the hacking aspect of Python, sockets.

Another series I am now starting, might have to slow down on all of these series, but why tf not. What Is CMD?

Welcome back! In the last training session we covered how to write and execute scripts. But today we'll be getting back to the code!

Fewer and fewer Android phones are being released with SD card slots, so it's always a struggle to make sure you have enough free storage space for your photos, videos, and music. Things like app data and cache slowly build up as you use your device, which means your available storage number gradually decreases over time.

If you're reading articles in bed or scrolling through Facebook before trying to fall asleep, you'll spend much less time on your iPhone before drifting off into slumber as long as you're using the right display mode.

Welcome back! In our last training session, we covered some advanced list topics. We'll be going deeper into the advanced list rabbit hole today with lambda and lambda operators! (And I'm not talking about Gordan Freeman)

In the last iteration of how to train your python, we covered basic string manipulation and how we can use it to better evaluate user input. So, today we'll be covering how to take user input. User input is very important to scripting. How can we do what the user says if we can't tell what the user wants? There are multiple ways to take input, we can give the user a prompt and take input from them directly, or we could use flags/switches, and take their input before the script is even execute...

Remember portable MP3 players like the classic iPod? Seems like forever ago that they were all the rage, and I don't think I've seen a real one in the wild for a good 5 years now. These devices died out so quickly as a direct result of the onset of smartphones, which allow us to do everything that an MP3 player could do and then some.

With just a Phillips head screwdriver and this walk-through, you can open and close any bObi robot vacuum. So long as you have a replacement wheel, follow these steps to install it yourself.

Bacon isn't hard to cook on the stovetop, but every cook who's been hit by splattering fat knows it's not the most pleasant kitchen task to tackle. If you're cooking bacon for a lot of people, you can avoid this by cooking it in the oven on a roasting rack, DIY or otherwise.

Welcome back, my hacker novitiates! Eluding and evading antivirus software and intrusion detection systems is one of the most critical tasks of the hacker. As soon as a new exploit is developed and discovered, the AV and IDS developers build a signature for the attack, which is then likely to be detected and prevented.

Mirror, mirror on the wall, who is the fairest of them all? Besides being one of the most notorious misquotes of all time (the line is "Magic Mirror on the wall, who is the fairest of them all"), it's a question that men and women probably have asked themselves more than once.

You've unlocked your bootloader and rooted your HTC One running KitKat, but there's still one lingering aspect of security you've yet to rid yourself of—S-On—the extra security measure HTC implemented into Sense.

Flavored extracts may seem like they'd be complicated to make, but there's a lot less to them than you'd think, and will cost you less in the long run.

Microwave popcorn promises so much—a tasty, relatively healthy snack that's ready in minutes—yet it rarely delivers. Most of the time you'll end up with a scorched bagful or a bunch of stubborn un-popped kernels, but it doesn't have to be that way. With a few simple tricks, it's easy to get perfectly fluffy, tender-crisp popcorn every time.

Applying for jobs can be a truly miserable experience. Sending out endless résumés, filling out those janky online applications, and creating cover letters can really wear a person down. So, any suggestions that make that process easier are always welcome.