In this tutorial, we learn how to pass the oral interview to become a police officer. Remember that the officers interviewing you want to see you succeed, so demonstrate your personality while you are being interviewed. When you are getting asked questions, ask for clarity, there is nothing wrong with this. The first type of interview you are going to have is a local focus interview, to know that you are committed to the area you live in. The next type of interview you will have is the behavi...

Have you ever wondered how your grandfather constructed the ship-in-a-bottle on his mantlepiece? Are you frustrated by the poor instructions that came with the kit you bought at your local hobby shop? The people at Storm the Castle certainly were, and so they made this video to show you how to complete your ship-in-a-bottle kit using basic hobby tools, including a very small drill bit, very small clamp, and very small paint brushes. No hobbyist's collection is complete without one of these.
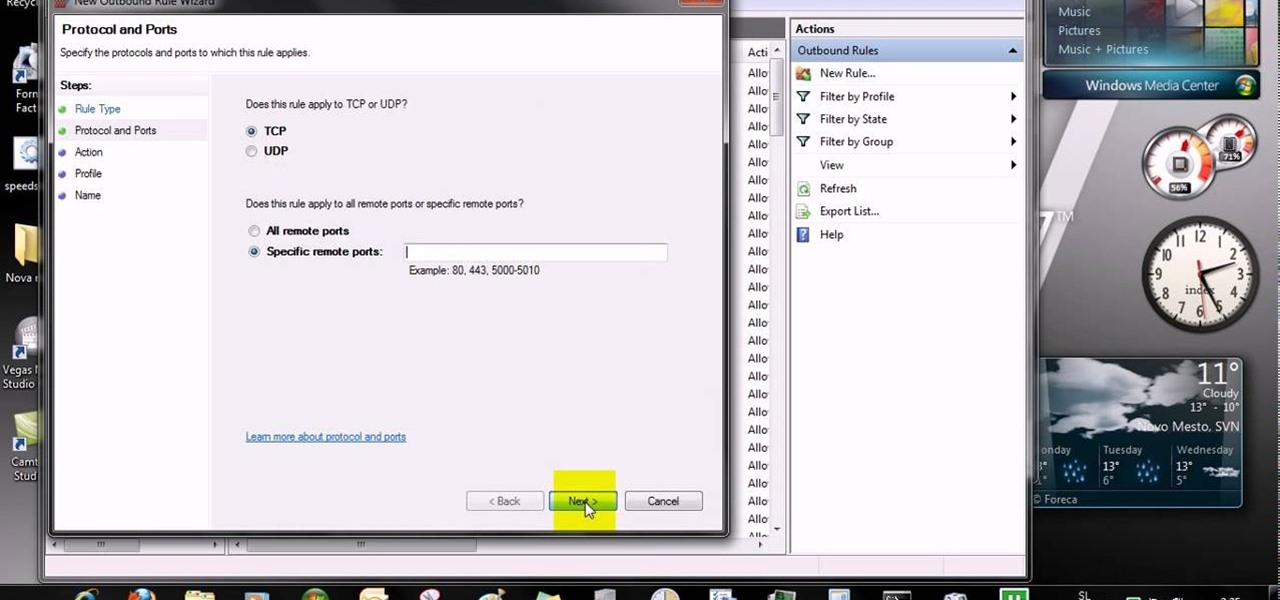
This video tells us the method to open ports in Windows 7. Click on myu icon and go to 'Preferences'. Copy the port number from the resulting window. Go to 'Start', 'Control Panel' and 'System and Security'. Go to 'Windows Firewall' and 'Advanced Settings'. Go to 'Inbound Rules' and 'New Rule'. Click on 'Port' and select 'TCP' and 'Specific Local Port'. Type the port number in the text box. Click 'Next' and 'Allow Connection'. Press 'Next' twice and put the name in the space provided for it. ...

Iphone is a innovative product from Apple, which can be used for many purposes. Some times even when using different applications and having a collection of music in your Iphone you may still be left with some space on it. Now you can use this space to fill it with other files which are not necessarily supported by the phone. Air sharing is a wonderful application which lets you drag and drop files into your Iphone. You can now browse it from any connected computer in your local network. So a...

This video explains how to make an inexpensive compost roller. The video begins with a composed pile shown covered with a tarp to keep rain away from. The materials needed for this project consists of 3" barrel nuts(2), 3" hinges(3) and machine screws(3pk) from a local Wall-Mart. The tools needed for this project consist of an electric drill with drill bit, screw driver, wrench, jig saw or key saw and a heavy duty utility knife. The compost roller made was just a simple plastic drum with a hi...

A low tunnel is a kind of mini-greenhouse for your garden. Growing vegetables in a low tunnel requires proper ventilation. In this tutorial, you'll learn how to provide the right ventilation for your low tunnel, keeping your plants happy and healthy.

Garlic is great for spicing up your meals (and keeping vampires away!) and fall is a great time to grow it. In this video tutorial, you'll learn how to grow garlic in your garden. Get some garlic bulbs from a seed catalog, nursery or organic grower, and you'll soon have a garlic crop to be proud of.

Come the fall, your garden is probably going to be looking pretty spare. But it doesn't have to be that way. There are vegetables that will thrive in the fall. In this Growing Wisdom gardening tutorial, you'll learn how to grow vegetables in the cooler months.

Autumn leaves may be beautiful, but they can also be incredibly annoying as they pile up around your garden. But there are things you can do with autumn leaves, like mulching them, composting them and turning them into a living fence. In this episode of Growing Wisdom, Dave Epstein walks you through how to make a leaf fence.

Can't turn silver into gold? Don't worry, at least you can turn an ordinary ivory egg into silver. That's better than nothing, right?

Check out this how to video on carnival games. Some of the local carnies offer tips on how to win the games along the midway at the Lorain County Fair. That doesn't mean you have to go to Lorain though, this applies to all carnival games, including One In Wins, Bust One, The Guesser, 100 Shots, Skee-Ball, and much, mcuh more. Don't know these games? I'm sure you do, just watch and learn, so you can fill your house with large, cuddly, stuffed animals.

While there are a variety of privacy-focused search engines available like StartPage and DuckDuckGo, nothing can offer the complete trust offered by creating one's own search engine. For complete trust and security, Searx can be used as free metasearch engine which can be hosted locally and index results from over 70 different search engines.

File inclusion can allow an attacker to view files on a remote host they shouldn't be able to see, and it can even allow the attacker to run code on a target.

Oh no... your precious iPhone is in shambles. Maybe you shattered your screen after a crazy night of celebrating, or maybe your two-year-old jabbed a toy into your iPhone's charging port, completely destroying it in the process. Now what? Do you take it to a repair shop, or go to an Apple Store to have it fixed? This brief article will help you weigh your options.

When performing something such as a mass mailer attack on a company, sending executables usually isn't the best option. That's why, in this tutorial, I'll be teaching you how to code a VBA script macro into a Word document in order to compromise a system. Combined with a little social engineering, this can be a very effective technique.

Welcome back, my novice hackers! Previously in my "Spy on Anyone" series, we used our hacking skills to turn a target's computer system into a bug to record conversations and found and downloaded confidential documents on someone's computer. In this tutorial, I will show you how to spy on somebody's Internet traffic.

Crochet Weave with Xpression Hair takes some proper care. It is just like having your hair relaxed; the hair is that texture.

Video: . How to Make My Famous Spaghetti.

Whether you've just bought a brand new shiny surfboard, or your current wax job is a grimy, slick mess, here's how to get that perfect grip so you don't slip off.

The quickest way to get a gorgeous lawn is to lay sod, uniform patches of grass-covered soil held together by matted roots. It will go more smoothly if you know a few landscaping tricks. Learn how to lay sod for a perfect lawn with this how to video.

Is your neighbor creating a ton of racket? Suffering in anything but silence? It can be hard to approach a noisy neighbor without starting a big riff. Follow these steps to get the quiet you deserve.

Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.

When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.

If you or someone you're shopping for has a newer iPhone model or an Android smartphone like the Galaxy Note 9 or Pixel 3, they come with wireless charging capabilities. Problem is, they don't come with wireless chargers. But there's no better time to snag one than on Black Friday, and we've found the best deals out there for 2018's holiday season.

Transferring hundreds of screenshots, webcam recordings, keystroke logs, and audio recordings between your VPS and a local Kali machine can be tricky. Services like Dropbox don't always have the best privacy policies and suffer data breaches just like any other website. To mitigate these risks, we'll use a secure, open source, and decentralized alternative.

I've called 911 accidentally more than a few times on my iPhone using the Emergency SOS triggers, but it's also just as easy to trigger an unintentional call to emergency services using an Apple Watch. These accidental 911 calls can put a strain on local public-safety answering points, or call centers, as well as local authorities and emergency medical technicians.

When it comes to media players, few are more capable than VLC. With its extensive codec support, VLC is able to play almost any video file. Partly due to its open-source nature, features are constantly added. This trend has continued with a new update that added native Chromecast support.

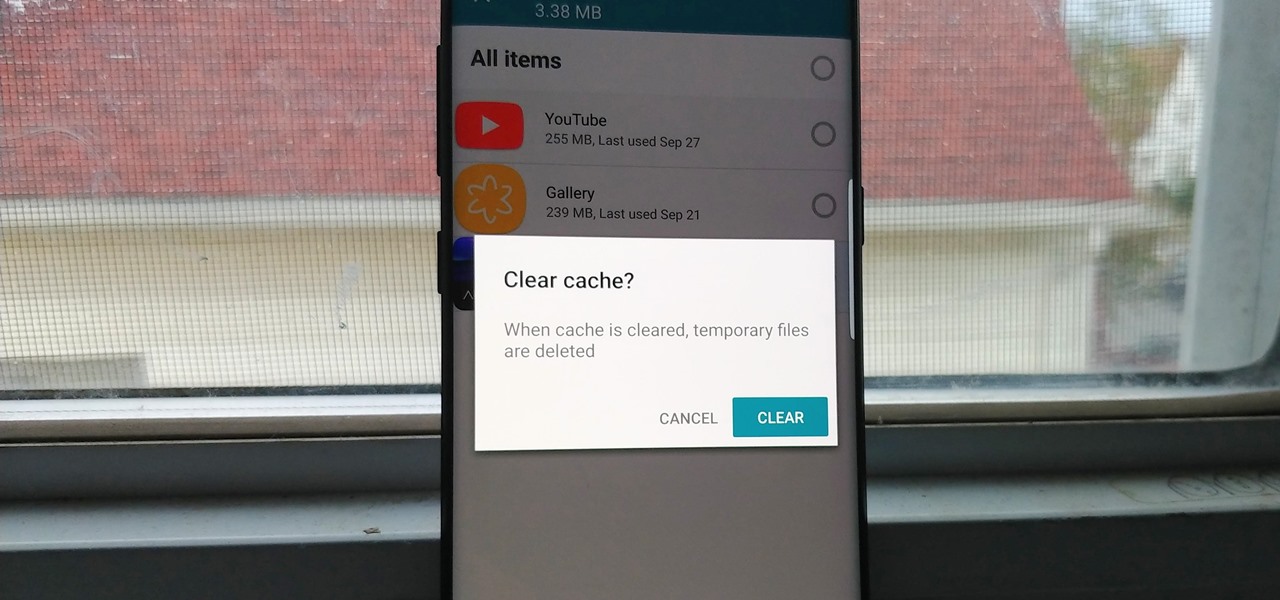
Since the release of the T-Mobile G1, the Play Store has been flooded with apps that claim to improve performance by clearing cache and storage. These apps are typically useless, rarely providing more than a temporary fix which Android undoes immediately. As Android has continued to improve cache and storage management, such apps have become more trivial. However, there are few decent ones out there.

Things aren't looking good for Uber after its driverless experiment in Pittsburgh soured relations with local authorities. Surprised? Me neither.

Onshore, or on a boat, have you ever wondered what swims below in the dark water? Using standard equipment and a new process, marine scientists can now get a good look at what is swimming by—just by analyzing the water.

Pokémon GO made waves as the first augmented reality game to gain popular adoption. In fact, it was so popular that it only took a few days to uncover some the benefits and serious issues with combining physical and digital worlds.

In this series you will learn how to use PHP to perform attacks, gather information, and setup backdoors. Along with performing attacks you will learn how to protect yourself from them. In this part you will learn about PHP as well as install Apache and PHP. What you'll need for this series

A lot of people think that TOR services are unhackable because they are on a "secure environment", but the truth is that those services are exactly the same that run on any normal server, and can be hacked with the same tools (metasploit,hydra,sqlmap...), the only thing you have to do is launch a transparent proxy that pass all your packets through the TOR network to the hidden service.

welcome back my masters , teachers and classmates , in this second part of this 0-day series we will learn the basic of fuzzing, and i bought some gift for nullbyte(a 0 day vuln that will be released today exclusively on null-byte) .

Welcome back, my neophyte hackers! In previous tutorials, we learned how to steal system tokens that we could use to access resources, how to use hashdump to pull password hashes from a local system, and how to grab password hashes from a local system and crack them.

While honey is one of the most popular ingredients on kitchen shelves the world over, honeybee pollen is still a relatively rare find in most households. It's not hard to guess why: eating pollen just sounds weird... it would probably sell a lot better if it had a more appetizing name, like honey. Furthermore, it looks unlike any other common ingredient, and the smell can be off-putting to some. But it's good, it's healthy, and it's altogether pretty awesome!

Hi Elite Hackers! Welcome! to my 4th post. This tutorial will explain, how to extend a (hacked) AP's range with a wireless adapter. I made this guide because after hacking an AP it was difficult to connect to it (poor connection) and further exploit it. You can also use this:

In today's world of ordering food from your PC or hailing a cab with an app, it almost seems archaic when we have to actually use our vocal cords to contact a local business. It sure would be nice if we didn't have to use our smartphones as, well, you know...phones.

Welcome back, my budding hackers! When we are looking for ways to hack a system, we need a specific exploit to take advantage of a certain vulnerability in the operating system, service, or application. Although I have shown you multiple ways to exploit systems here in Null Byte, there are still many more exploits available that I have not yet shown you.

If you've seen ParaNorman or Fantastic Mr. Fox, then you have some kind of idea of what stop-motion animation is. Basically, these artists make objects, or small figures, appear to be moving on their own by manipulating and repositioning them in the smallest increments, then capturing each frame after doing so. When all the frames are compiled together, the final product is something spectacular like The Nightmare Before Christmas, which took roughly 109,440 frames in all.