On Monday, Apple unveiled its Apple Card, the company's boldest move yet toward becoming a truly mainstream mobile payments company. And the product has vast implications for our augmented reality future, some of which may not be immediately obvious to many.

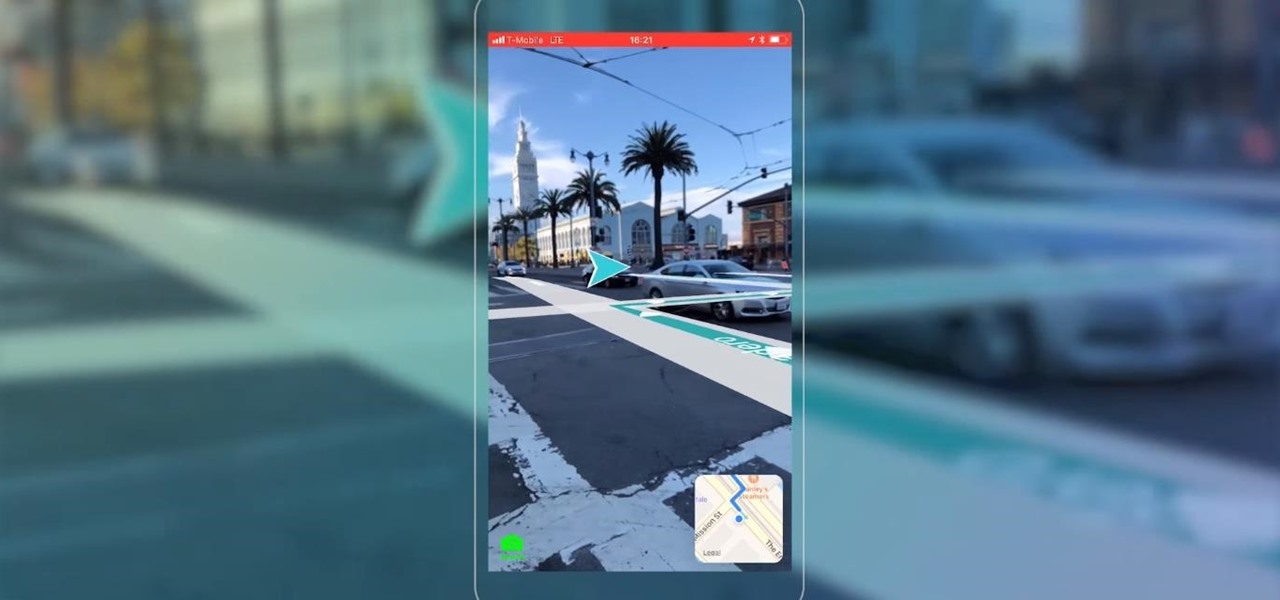
While Google isn't ready to commit to a wide release of the AR walking navigation mode for Google Maps, the company has begun testing the feature with members of its Local Guides crowdsourcing community.

With the number of web applications out there today, it comes as no surprise that there are just as many vulnerabilities waiting for hackers to discover. Finding those vulnerabilities can be a difficult task, but there are plenty of tools available to make the process easier. While it won't help find any zero-days, web scanners such as Uniscan will detect common vulnerabilities.

With Pokémon GO as its cash cow and the forthcoming Harry Potter: Wizards Unite and Niantic Real World Platform promising future revenue streams, Niantic has convinced investors to bet on its flavor of augmented reality

While the technology companies continue to drive forward with autonomous vehicles, Nissan's vision of the future of self-driving automobiles lies in a cooperative experience between human and machine, facilitated by augmented reality.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.

The team at Magic Leap just got a millennial-style boost with the announcement that financial news network Cheddar is coming to the Magic Leap One.

The holiday season is upon us, and that means all the big-box stores are competing against each other to offer the best prices on electronics. What was once a 24-hour period of flash deals the day after Thanksgiving has now become a holiday in and of itself — Black Friday is an event you don't want to miss.

Amid the opulent and historic confines of Paris, Microsoft is now hosting an exhibit at a local museum that brings a historic map of a Normandy tourist destination to life in augmented reality.

One of the best ways to improve your skills as a hacker is to learn to combine different avenues of attack to achieve success. What if it were possible to get a victim to connect to our machine and execute a chosen payload on our behalf? This is indeed possible with the almighty Metasploit and the aid of a technique known as command injection.

The game wizards at Insomniac take pride in diving deep when it comes to world-building, and the same is true for the studio's latest title for Magic Leap One called Seedling.

As penetration testers, we sometimes need to securely store customer data for prolonged periods. Bruteforce-resistant, vault-like containers can be created with just a few commands to protect ourselves from physical attacks and unintended data disclosures.

Just in time for Women's Equality Day on Aug. 26, Treasury Wine Estates is breaking out a line of wines with augmented reality experiences that pay tribute to historically famous women.

Microsoft is adding another important piece to its growing immersive computing arsenal by putting its newest Mixed Reality Capture Studio in the center of the movie business: Hollywood.

Locating and abusing files containing unsafe permissions is an easy and surefire way to elevate shell privileges on a backdoored macOS device. This time around, we'll be more aggressive and attempt to phish a user's login password by prompting a convincing popup message merely asking the target for their password.

When you receive a photo or video from a contact in WhatsApp, after you load it, it's automatically saved to your phone's local storage. That means all received content from WhatsApp is visible to anyone who gains access to your default photo gallery. Luckily, there's a new feature available for the Android version of the app that can prevent this from happening.

After a district judge approved the $85 billion merger between AT&T and Time Warner, we knew AT&T would be quick to reap the rewards of capturing Time Warner's media properties. Today, we get our first look at this with two cellular plans from AT&T. What makes these plans unique is they include a new cord-cutting service called WatchTV.

With the World Cup in Russia fast approaching, you're probably wondering how to keep track of your country (unless that country is the USA). While there are a ton of apps that do just that, there's one that stands above the rest if you're looking for World Cup coverage — and it's not ESPN, Yahoo, or CBS.

The misconception that macOS is more secure than the Windows operating system is far from the truth. With just one small command, a hacker can completely take over a MacBook and control it remotely.

The pending union between Prince Harry and American actress Meghan Markle is almost guaranteed to set the internet ablaze as millions tune in to experience the spectacle and pageantry of such a momentous event. If you've cut the cord and are wondering where you can stream the royal wedding for free, we've got you covered.

Whether due to spotty cellular reception or just data that you want to save, popular navigation apps like Google Maps and Waze offer an offline feature that lets you navigate from one location to another in the absence of internet service. Apple Maps also lets you use its service offline on your iPhone, though the feature is not as straightforward as it is on its competitors.

Using a keylogger to intercept keys pressed on an infected computer can circumvent encryption used by email and secure chat clients. The collected data can often reveal usernames, passwords, and potentially compromising and private information which hackers abuse for financial gain.

With Gboard, Google created a keyboard with more functionality than just inputting words. The app includes features such as GIF search and live text translation, but it gets even better when you let it learn more about you. With this data, Gboard grows from a good keyboard to one that can complete your sentences.

MLB.TV is a great service that lets you watch most Major League Baseball games in North America, as long as you're a subscriber, of course. While I personally love it, blackouts can ruin the ability to watch my favorite teams. Fortunately, MLB At Bat Android users have an easy way to bypass blackout restrictions — and with no root required.

If you're a fan of Gboard, Google's third-party keyboard for iOS, then you can already search Google, YouTube, and Google Maps from any screen you're on. But if you prefer Apple's stock keyboard or another third-party one on your iPhone, you don't have any Google search options ... at least, until now.

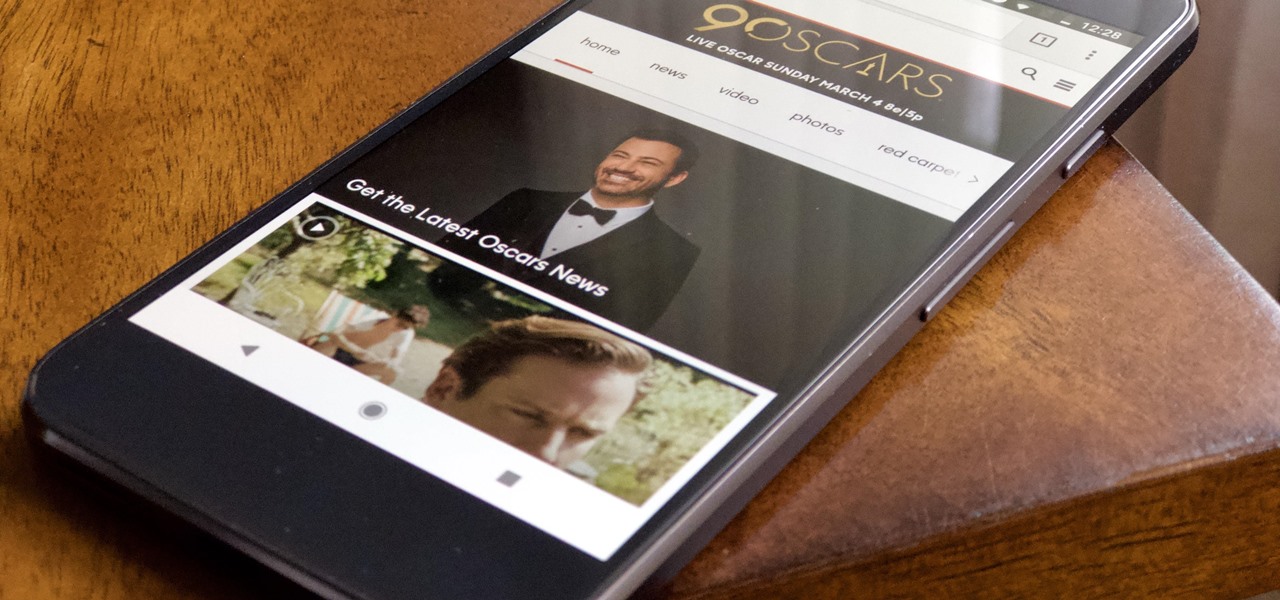
Another year, another Oscars. This year's red carpet coverage kicks off Sunday, March 4, at 6:30 p.m. EST, while the ceremony itself starts at 8:00 p.m. EST. Finding a stream online isn't always the most straightforward endeavor, especially if you want it to be free. To avoid any delays on the night itself, make sure to run through your viewing options here.

The one thing that separates a script kiddy from a legitimate hacker or security professional is the ability to program. Script kiddies use other people's tools, while hackers and security pros write their own tools. To that end, we're going to see how a stack overflow vulnerability allows us to flood a variable with enough input to overwrite the instruction pointer with our own commands.

There's a new macOS vulnerability that hackers within physical reach of your computer can use to gain root access to your system and accounts. Just by using "root" as the username and a blank password on a privilege escalation prompt, someone can install malware on your computer, access hidden files, reset your passwords, and more. Root access gives them the ability to do anything they want.

Mobile AR developer Blippar has achieved a breakthrough by releasing what appears to be the first commercially-available AR navigation app.

You can bet Thor costumes will be prominent among the superheroes seen this Oct. 31. Since the summer, there has been no shortage of coverage for Thor: Ragnarok, and the timing of its November release couldn't be better as a tie-in with the cosplaying holiday known as Halloween. This year, the success of pulling off the Thor costume will rely on how well your new Thor helmet looks, which as it happens, you can DIY at home, using a few simple supplies and perhaps a trip or two to the craft and...

A potentially groundbreaking new app targeting retail financial services hopes to bring augmented reality to your local bank and credit union.

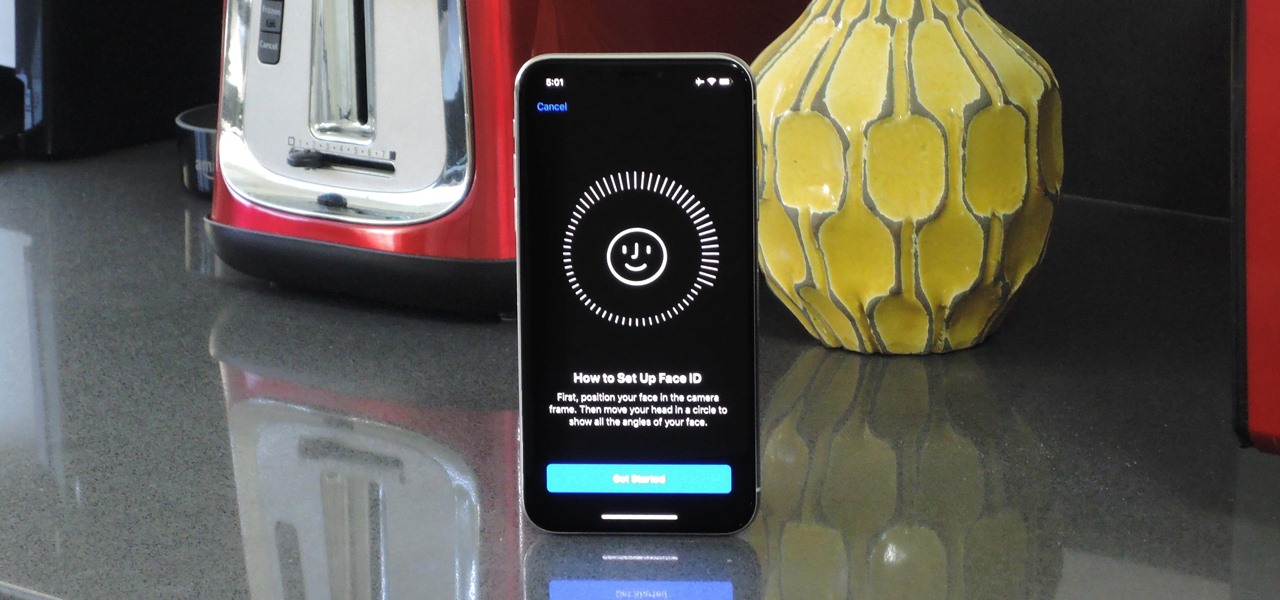
The cutting-edge iPhone X, XS, XS Max, and XR have one-upped their Android competitors when it comes to facial recognition. Apple packed these flagships with an array of front-facing sensors to complement its selfie camera, which allows the new device to more accurately analyze faces, which you need for Face ID, Touch ID's replacement.

The iPhone 8 is just about here. If you're anything like me, you can hardly contain your excitement. Apple has been keeping its 10th-anniversary device — whether you call it the iPhone X, iPhone Edition, or iPhone 8 — as secret as possible, but this past year we've seen a waterfall of leaks. Now that all of the rumors are out of the way, we're finally going to see what's actually in store for Apple's newest iPhone.

On June 11, 2016, an Arizona woman died from what appeared to be several infections, including pneumonia. She likely caught at least one of these from her dog.

Cross-compilation allows you to develop for one platform (like Kali) and compile to run on a different platform (such as Windows). For developers, it means that they can work on their platform of choice and compile their code for their target platform. For hackers, it means we can compile exploit code for Windows from Kali.

The Google Assistant comes in several different flavors. There's the baked-in Google app on Android, the dedicated Google Assistant app on iOS, and the Assistant-powered Google Home smart speaker. But no matter how you access it, your Assistant will only get better if you take some time to personalize things.

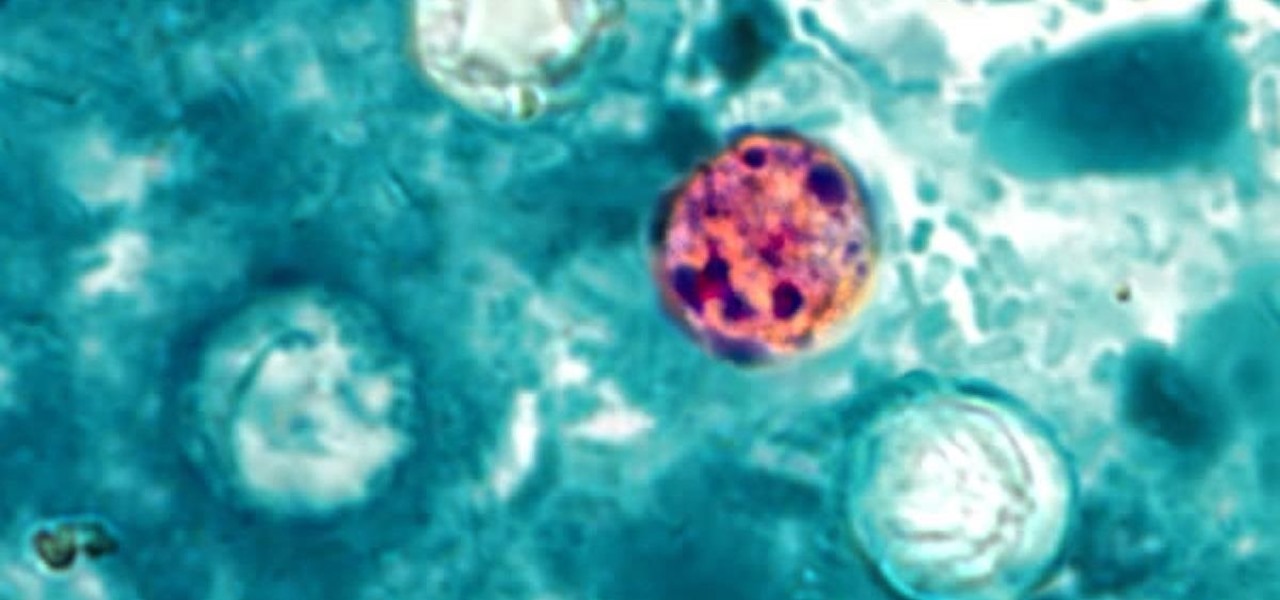
The intestinal parasite Cyclospora cayetanensis has a dramatically increased infection rate this summer, and the source is still unknown, the CDC advised today. 2017 is a good year for Cyclospora looking for homes to start their families and a bad year for those of us who don't like food-stealing tenants living in our bodies.

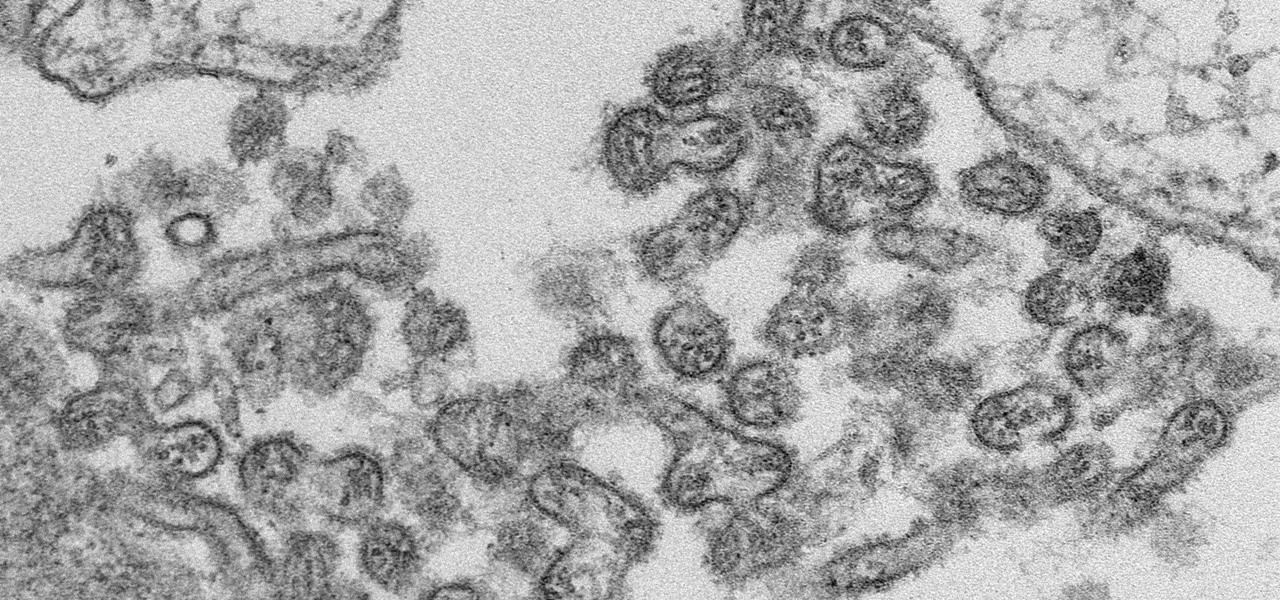
A new case of the still-mysterious Bourbon virus was confirmed in Missouri, likely originating within the state, local authorities said in a June 30 press release.

At Facebook's first Communities Summit, admins from top Facebook groups assembled to discuss tools to better manage and optimize their members. Here, Facebook CEO Mark Zuckerberg announced that these changes fuel the company's shifting focus from connecting the world to uniting it.