The Geminid meteor shower happens every December and has been observed for over 500 years. It's is also known as Winter's Fireworks because when viewed from the right location, there are enough meteors to light up the whole night sky, and some of them can even be different colors. The shower appears to come from the Gemini constellation, but is actually caused by Earth passing through the tail of dust and debris left behind by the comet 3200 Phaethon.

You may or may not care about this, but sometimes it physically upsets me when I see gears stuck together haphazardly, with no concern for whether their teeth interlock. I mean, what do you do with non-interlocking gears?

Getting a new phone is like getting a pair of new socks—you can't wait to try them on and when you do, they feel totally awesome. Maybe that's just me, but for many customers that have already received their highly anticipated iPhone 5 in the mail, awesome is definitely not the word they are using.

The cost of movie tickets in North America are currently at an all-time high, but with so many great films coming out, just not going doesn't seem like a probable option. Luckily, there's more than a few resources on the Internet to help you mitigate some of those costs.

Here's how to build a sexy looking water-fuel generator that will convert your tap water into an extremely powerful, clean burning gas!

Did you know that there's a way to start a fire by squishing air? In this project, I'll show you how to build a tool that does exactly that—and I'll give you a sneak peak into the principals of how a diesel engine operates!

So, this idea was born from a necessity to save. My household uses tissues a lot. I have two small kids, so they are extremely useful. The problem with tissues is that they seem to disappear in no time. So, whenever we ran out in-between shopping visits, my family would just use toilet paper.

Brushing your teeth is a necessity. You don't want to walk around with yellow teeth and stinky breath, and it's common courtesy to those around you to care about your personal hygiene at least that much.

OSAGYEFO DR. KWAME NKRUMAH (1909-72) Founder and Father of the Nation Osagyefo Dr. Kwame Nkrumah, the first Prime Minister and President of Ghana, stands out not only among the Big Six but also among the greatest statesmen of history. It was he who canalized the discontent of the people of the Gold Coast Colony into the highly organized movement of protest against British rule, and within a relatively short period won political independence for Ghana on March 6, 1957. With Ghana independent, ...

In last week's guide, we covered the best places to purchase digital copies of computer games online. This week we'll cover another type of downloadable content: those available for video game consoles. Every major console out today either has or plans to have a DLC platform, but which one is the best? If you don't like leaving your house and want to play console video games, which console should you get? Below I will break down what the online marketplace offers so you can decide which conso...

Recycling your garbage is noble and, in many places, mandatory. But it also can be very confusing. This guide will clear up the rules.

There's no shortage of ice cream recipes out there, but one ice cream shop in London has found a unique recipe to sell to its customers, and of course it's controversial—breast milk ice cream.

Email accounts can quickly get out of control, and important emails can easily get lost if you don't have time to look at them right away. In Apple's Mail app, there's a simple way to be reminded of emails you want to read later, whether it's an email with tasks you need to complete, upcoming event details, or a message you need to reply to, and it works no matter the email account.

There's a quick way to see who you or somebody else has been chatting with the most in the Messages app for iOS and iPadOS. More specifically, it shows which conversations have the most attachments, such as photos and videos, giving you an idea of which chats are the most active visually.

In the tech world, our data is always under attack. When you download and install a new app, it can be difficult to know what information the app is actually accessing. Thankfully, a new emphasis on privacy in iOS 14 changes the game, exposing more of what your apps want access to — and even changing some behavior along the way.

Secure Shell is one of the most common network protocols, typically used to manage remote machines through an encrypted connection. However, SSH is prone to password brute-forcing. Key-based authentication is much more secure, and private keys can even be encrypted for additional security. But even that isn't bulletproof since SSH private key passwords can be cracked using John the Ripper.

The Pi-hole project is a popular DNS-level ad blocker, but it can be much more than that. Its DNS-level filtering can also be used as a firewall of sorts to prevent malicious websites from resolving, as well as to keep privacy-killing trackers such as Google Analytics from ever loading in the browser. Let's take a look at setting a Pi-hole up and customizing a blacklist to suit your needs.

Anything from work or a missed flight to a worldwide pandemic (COVID-19, anyone?) can make it difficult or nearly impossible to see your loved ones. You can make phone calls or send iMessage, text, or email messages, but nothing compares to seeing family and friends right in front of you. That's where FaceTime comes in.

Compromised uTorrent clients can be abused to download a malicious torrent file. The malicious file is designed to embed a persistent backdoor and execute when Windows 10 reboots, granting the attacker remote access to the operating system at will.

Despite some of the biggest players in tech still lagging in terms of offering smartglasses options, there are nevertheless a number of smartglasses makers, including North and Vuzix, with consumer-grade smartglasses on the market right now.

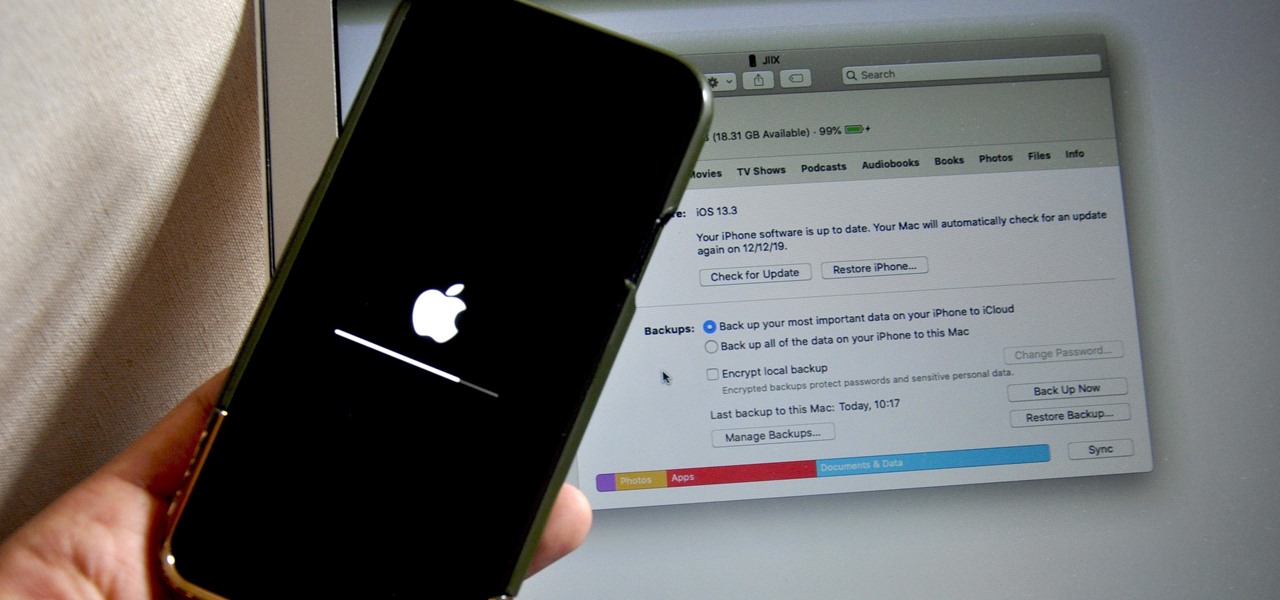
Restoring your iPhone from a previous backup is still a simple process using your Mac, but the way it works has changed since Apple killed off iTunes with the macOS Catalina update. Now you must use Finder to both back up and restore your iPhone, which can take a little getting used to.

Apple said goodbye to iTunes with the release of macOS Catalina, breaking up music, videos, and podcasts into their own respective apps, Music, TV, and Podcasts. But without iTunes, what app's in charge of interfacing with your iPhone? That would be Finder, and you use it to sync your iPhone, as well as back it up and archive backups for emergency restores.

In iOS 13, Apple added an important new feature to its HomeKit smart home ecosystem called HomeKit Secure Video. With it, you have a secure, private way to store and access recordings from your smart home IoT cameras.

Apple's Gatekeeper security software for macOS (Mac OS X) is vulnerable to remote attacks up to version 10.14.5. An attacker that's anywhere in the world can exploit MacBooks and other Mac computers by sharing a single ZIP file.

Smartphones are now indispensable when traveling. Domestic and overseas travel alike require food, navigation, translation, and so much more to make work or vacation successful. Gone are the days of lugging multiple tourist books around with you everywhere you go — you need to let your smartphone handle the dirty work.

What if you could easily visualize which access point every Wi-Fi device nearby is connected to in a matter of seconds? While programs like Airodump-ng can intercept this wireless information, making it easy for hackers to use and understand is another challenge. Fortunately, a tool called Airgraph-ng can visualize the relationships between Wi-Fi devices from only a few seconds of wireless observation.

It's easier than you might think to hack into Wi-Fi routers using just one unrooted Android phone. This method doesn't require brute-forcing the password, a Windows OS for converting PowerShell scripts into EXE format, a reliable VPS for intercepting hacked Wi-Fi passwords, or Metasploit for post-exploitation tricks.

It only takes a few commands to manipulate a MacBook's secure HTTPS traffic and pluck login passwords out of the encrypted data. Let's take Facebook and Gmail hacking to the next level by intercepting Safari and Google Chrome web traffic in real time.

The newest version of macOS has arrived. While everyone's mind is being blown by Mojave's groundbreaking new Dark Mode, we'll be taking advantage of its insecure file permissions to establish a persistent backdoor with a self-destructing payload that leaves little evidence for forensics.

There's actually more to the dialer screen on your OnePlus than meets the eye. Besides its obvious purpose of calling people, there's a vast array of secret codes that you can input to troubleshoot your device, in addition to revealing important information, making anonymous phone calls, and so much more.

While the security behind WEP networks was broken in 2005, modern tools have made cracking them incredibly simple. In densely populated areas, WEP networks can be found in surprising and important places to this day, and they can be cracked in a matter of minutes. We'll show you how a hacker would do so and explain why they should be careful to avoid hacking into a honeypot.

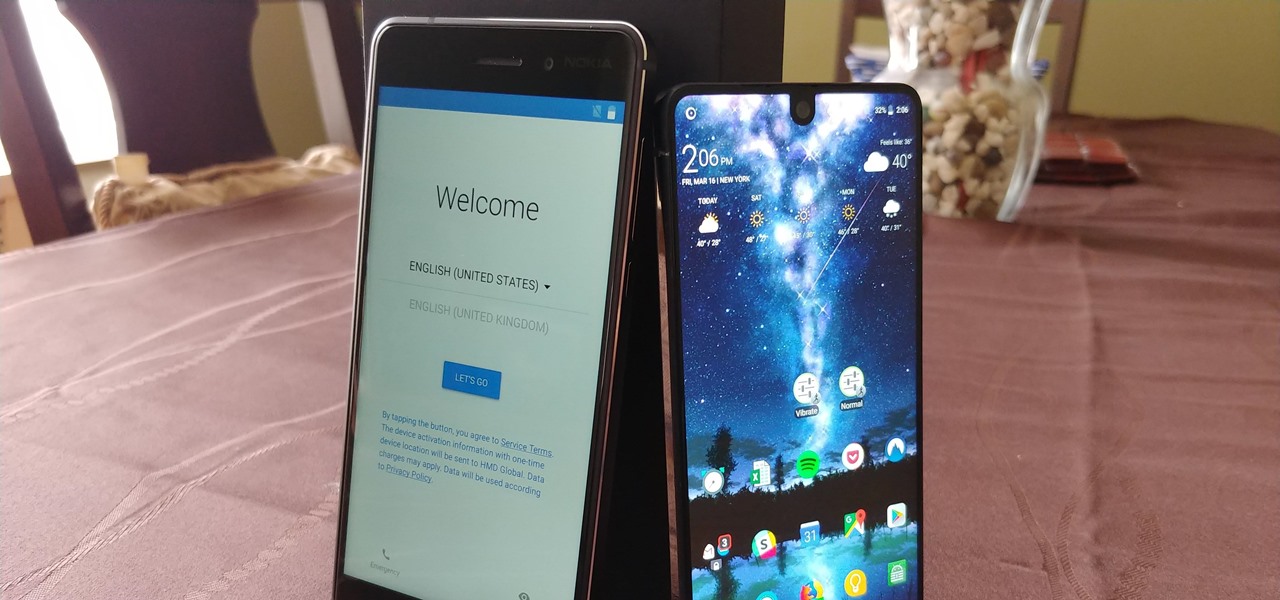
Setting up a new Android phone can be a pain. Although Google has some automated features, it does not restore everything. When it comes to transferring certain types of data like files and SMS logs, it's even trickier. By following our steps, you can be sure that you all your data will follow you to your new device.

With the addition of the OpenSSH client and server in the Windows 10 Fall Creators Update, you no longer have to rely on third-party programs to open an SSH server and connect to a Windows machine. While still a beta feature, this represents a long-overdue update fulfilling a promise made back in 2015.

Being able to write your own hacking tools is what separates the script kiddies from the legendary hackers. While this can take many forms, one of the most coveted skills in hacking is the ability to dig through the binary files of a program and identify vulnerabilities at the lowest level. This is referred to as binary exploitation, and today we're going to check out a tool known as Protostar.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

There are more than 2 billion Android devices active each month, any of which can be hacked with the use of a remote administration tool, more commonly known as a RAT. AhMyth, one of these powerful tools, can help outsiders monitor a device's location, see SMS messages, take camera snapshots, and even record with the microphone without the user knowing.

"I'm Rey." That's what a lot of people will be saying again this Halloween, as Rey costumes are sure to be another favorite of trick-or-treaters and cosplayers. Yes, on Oct. 31 we all have a chance to be the scavenger of Jakku who just so happens to be the "new hope" for a Jedi renaissance.

Tor is an excellent obfuscation network for web traffic, and while instant messaging over the network is very useful, it can be relatively difficult to configure. In this guide, we'll look at two synchronous communications platforms (instant messengers) which can be routed over the Tor network, Ricochet and XMPP.

Bluetooth Low Energy (BLE) is the de facto wireless protocol choice by many wearables developers, and much of the emerging internet of things (IoT) market. Thanks to it's near ubiquity in modern smartphones, tablets, and computers, BLE represents a large and frequently insecure attack surface. This surface can now be mapped with the use of Blue Hydra.

It's no secret that devices leak data, but sometimes they do so in ways you may not expect. Your phone, laptop, printer, and IOT devices leak Wi-Fi information that can (and is) used to track you.