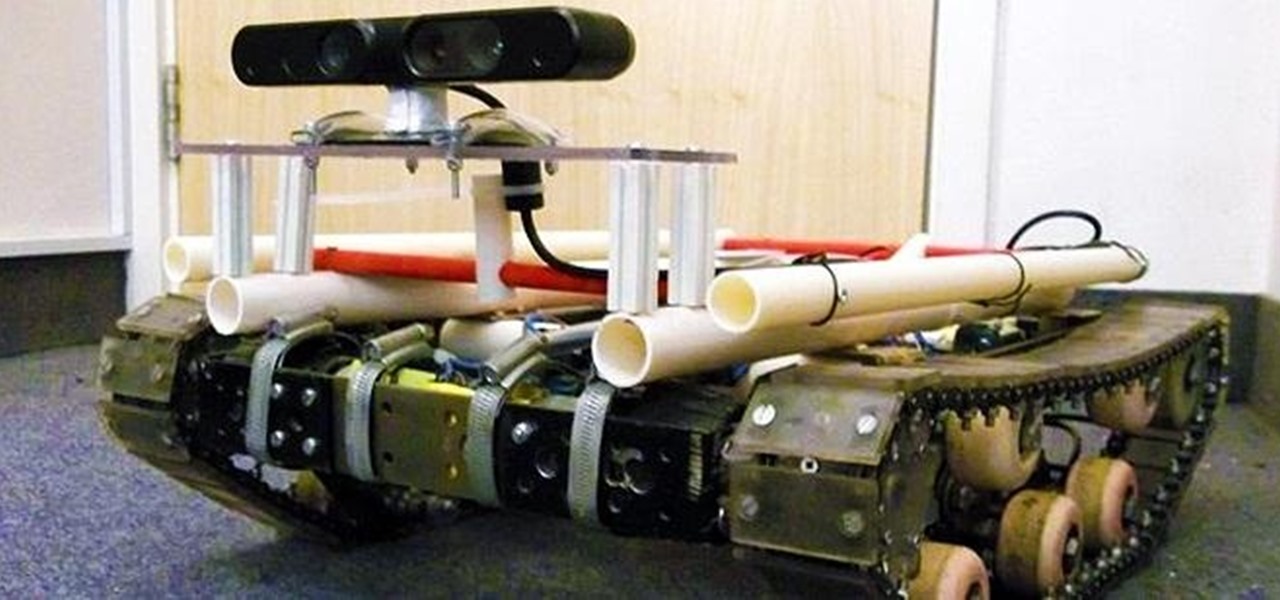
There are plenty of tank robots out there, but how many of them can recognize 3D objects and map their environment? Tanky, the tracked mobile robot, can do all that and more while rolling around on his bicycle chain treads. Created as a Master's thesis project, Tanky is made almost entirely of parts you can find at your local hardware store. It was built in two "layers" with the motors, electronics, and batteries on bottom and the processing unit, a laptop, on top. The motors came from cordle...

Wall Anchors. Drywall Wall Anchors. Plasterboard Wall Anchors. I discovered these plasterboard (drywall) anchors / plugs a few years ago and think they are fantastic. They are ridiculously easy to use and are extremely effective in attaching fixtures to walls. One of the main things to be aware of (as with all things that have fixtures hanging from them) is the recommended maximum weight loading of each size of anchor. What ever the packet says, adhere to it.
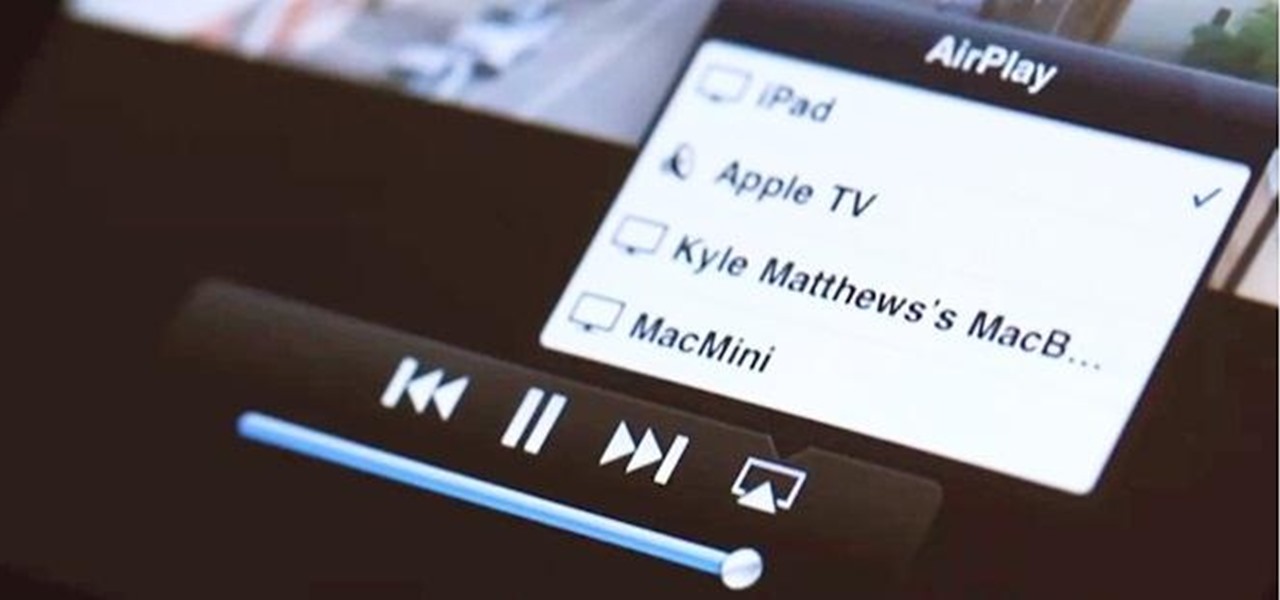
AirPlay is probably one of the most underutilized features in Apple products. It allows users to wirelessly stream photos, music, or video directly from their iPad, iPhone, iPod touch or Mac to their Apple TV or AirPlay-supported speakers. The Apple support page has a complete list of all the supported and needed devices. Mirroring is also available, but only for the iPhone 4S, iPhone 5, and iPad 2, all of which need to be running iOS 5 or later.
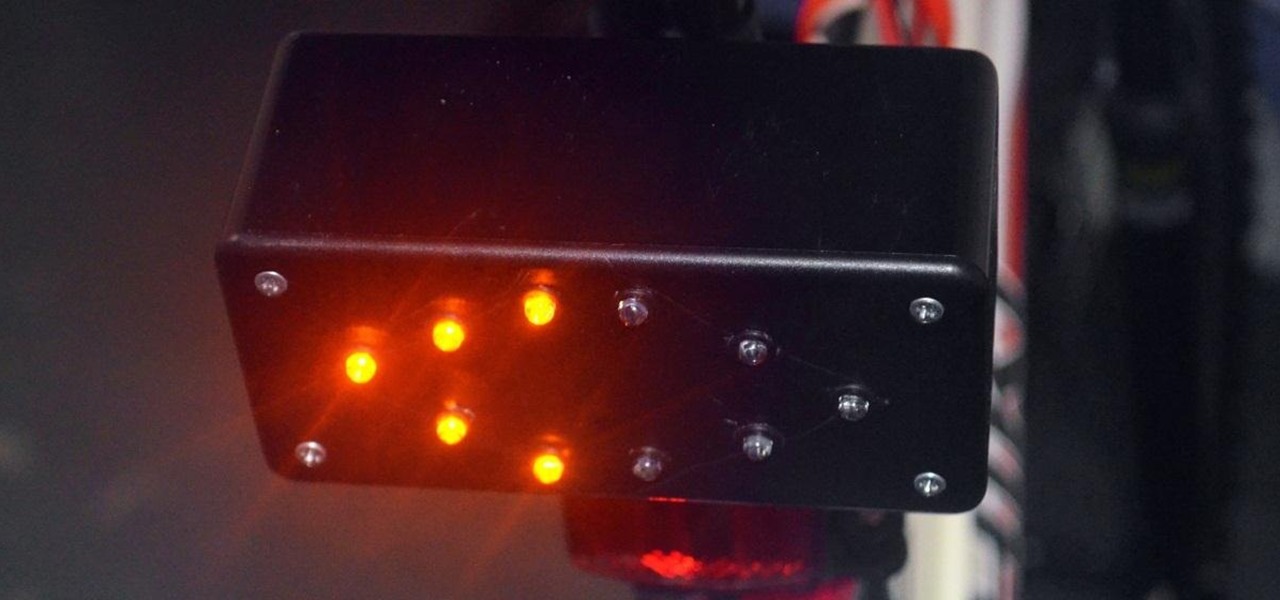
In the past few weeks, you've already learned how to make your bike light up at night with some DIY rim lights and handlebar lights. But how about something a little more functional? Instead of using those tedious hand signals (which drivers don't even understand), spruce up your ride with some do-it-yourself LED turn signals.
Are you getting that nasty "Application access set to not allowed" error on your Nokia 5300 cell phone? Unfortunately, it's a problem for most Nokia 5300 owners, ones who wish to use 3rd party applications on certain carriers, like T-Mobile, who restricts the uses for branding.

In this tutorial, professional referee, James Armstrong teaches you all about two of the most commonly forgotten rules of basketball. In the NBA, you rarely, if ever, see violations for things like traveling and lane violations.

Fish & chips is the most popular fish meal in the country, & you can make it yourself instead of paying a fortune at your local fish eatery. The special ingredient for these fish and chips… beer.

Imagine a game almost anyone can play that combines the best of skee-ball, bowling, and shuffleboard. Welcome to the ancient sport of bocce.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

Have you ever wanted to go into another user's account on your computer but had trouble finding the energy to log out, then log out, only to log back into your own account? Well, here's your solution: XNest will let you log in to another user's account from your account in a virtual way. It's very simple to set up and may just help you with your virtual account crisis!

Benny from askbenny.cn teaches you how to say some local proverbs and sayings in Mandarin Chinese. Part 1 of 2 - How to Say Chinese sayings and proverbs.

Make sure the bike is properly fit to the child. She should just be able to stand over the top bar of the frame without touching.

Elvira, Mistress of the Dark, was created in 1981 by Cassandra Peterson. She was the hostess of a local Hollywood horror movie show that became nationally syndicated. Elvira was the first horror host to be nationally syndicated, first person to be broadcast in 3-D on TV, and first female celebrity to do a national beer campaign and market her own beer.

Would you know what to do if someone ingested poison? Equally important, would you know what not to do?

You already know the mechanics of DJing, but you want to be an international celebrity -- or at least drink for free while showing off your music collection. Here's how to spin your hobby into a career. Watch this video to learn how to become a professional club DJ.

Learn how to choose an indoor plant. You don’t need a green thumb to have houseplants that flourish; you just need to know which ones will thrive in your home.

Download the P2 Step-by-Step Reference Guide. With Avid, editing footage captured with the Panasonic HVX200 camera is fast and easy. Avids system uses the same native file format as Panasonic P2 memory cards, so theres no need for any transcode, capture or file conversion process at all. You can edit directly and immediately from the P2 cards if you like or have Avid Media Composer create a rapid backup of your files. Nothing could be simpler or more immediate.

Learn how to crash a wedding. If you have a free Saturday, we have a way for you to score free food, free cocktails, free dancing—and maybe even a hook-up.

Apple finally unveiled the iPhone 14, 14 Plus, 14 Pro, and 14 Pro Max, and there are a lot of improvements that'll make you want to trade in your current iPhone stat. But I wouldn't be so quick to upgrade because there's one "feature" that will make many of you rethink getting a new iPhone 14 series model.

File permissions can get tricky on Linux and can be a valuable avenue of attack during privilege escalation if things aren't configured correctly. SUID binaries can often be an easy path to root, but sifting through all of the defaults can be a massive waste of time. Luckily, there's a simple script that can sort things out for us.

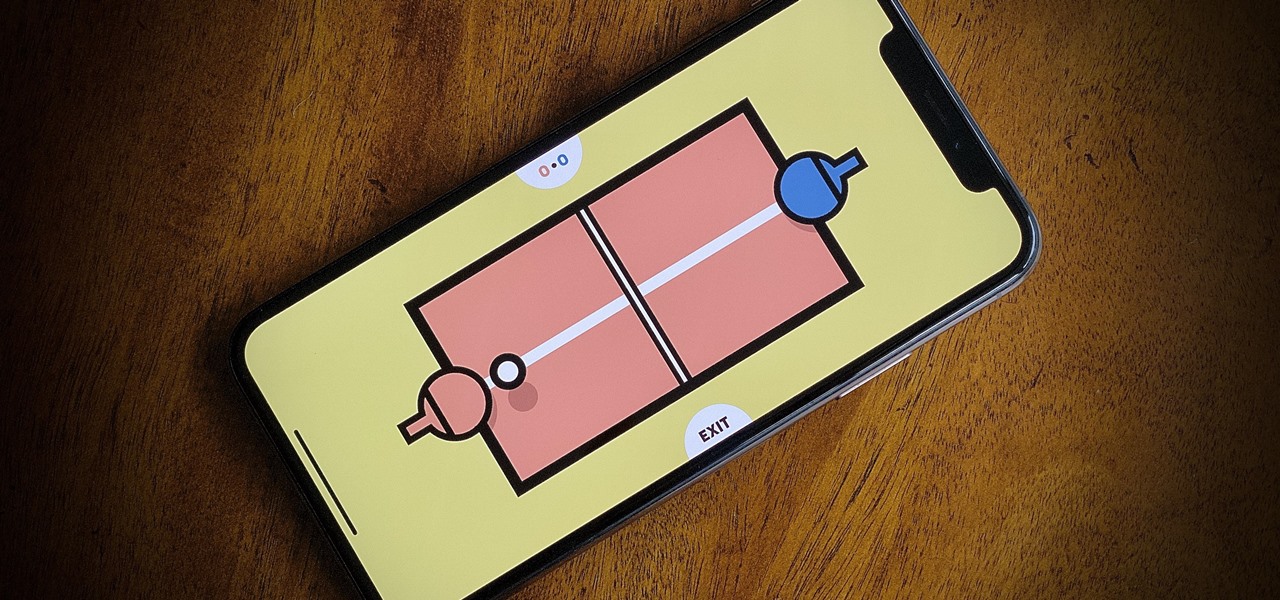
If you're quarantining with other people, consider yourself lucky — but it's not always easy. Staying in one space for so long with too many people can be challenging, so you need to find things to do to make the time go by (and to keep everyone sane). Our advice? Try out these seven free multiplayer games that only require one iPhone or Android device to play.

The "what (blank) are you" augmented reality filters on Instagram have become so popular that more and more Hollywood giants are following the augmented reality-powered social media meme train, with the latest example coming via Snapchat.

After three rounds of beta testing, Apple finally released iOS 13.3.1 today, Jan. 28. It's the latest update to iOS 13, coming exactly seven weeks after the release of iOS 13.3. So, what's new?

Nearly every connection to the internet is dependent on the Domain Name System. DNS, as it's more commonly called, translates domain names like gadgethacks.com into IP addresses, which is what network devices use to route data. The problem with DNS servers is that they don't have your privacy in mind.

Samba can be configured to allow any user with write access the ability to create a link to the root filesystem. Once an attacker has this level of access, it's only a matter of time before the system gets owned. Although this configuration isn't that common in the wild, it does happen, and Metasploit has a module to easily exploit this security flaw.

I've just recently hopped on the AirPods bandwagon, and I can't see myself ever going back to the wired EarPods that Apple includes with every iPhone. The only issue is that I paid full price, but you don't have to with 2019's Black Friday deals, some of which are happening right now.

The next phase of the holographic display is upon us, and Looking Glass is aggressively making sure that it's at the tip of the spear when it comes to leading that charge.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

Particular vulnerabilities and exploits come along and make headlines with their catchy names and impressive potential for damage. EternalBlue is one of those exploits. Originally tied to the NSA, this zero-day exploited a flaw in the SMB protocol, affecting many Windows machines and wreaking havoc everywhere. Here, we will use EternalBlue to exploit SMB via Metasploit.

Things that are supposed to make life easier for developers and users are often easy targets for exploitation by hackers. Like many situations in the tech world, there is usually a trade-off between convenience and security. One such trade-off is found in a system known as Distributed Ruby, which can be compromised easily with Metasploit.

Before you can dive into customizing your OnePlus 6T, you must take the initial step of unlocking the bootloader to gain the ability to install TWRP, Magisk, custom ROMs, and other mods.

If you're hungry for pizza and ordering from Domino's in Australia, you can now see what your pie will look like in augmented reality before placing your order.

If you store important, sensitive information on your iPhone in Notes, you'll want to be more careful. When Notes syncs across your iPad and Mac via iCloud — devices that family members or coworkers may share — you run the risk of having your notes read, edited, and deleted by other people. Such a catastrophe is easily avoided.

The march towards mainstream adoption of eSIM technology got a massive boost with the arrival of the iPhone XS, XS Max, and XR. We're now one step closer to ditching physical SIM cards altogether. If you're on the fence about this new technology, you may be surprised by the benefits it brings to the table.

The road to becoming a skilled white hat is paved with many milestones, one of those being learning how to perform a simple Nmap scan. A little further down that road lies more advanced scanning, along with utilizing a powerful feature of Nmap called the Nmap Scripting Engine. Even further down the road is learning how to modify and write scripts for NSE, which is what we'll be doing today.

With just one line of Ruby code embedded into a fake PDF, a hacker can remotely control any Mac computer from anywhere in the world. Creating the command is the easy part, but getting the target to open the code is where a hacker will need to get creative.

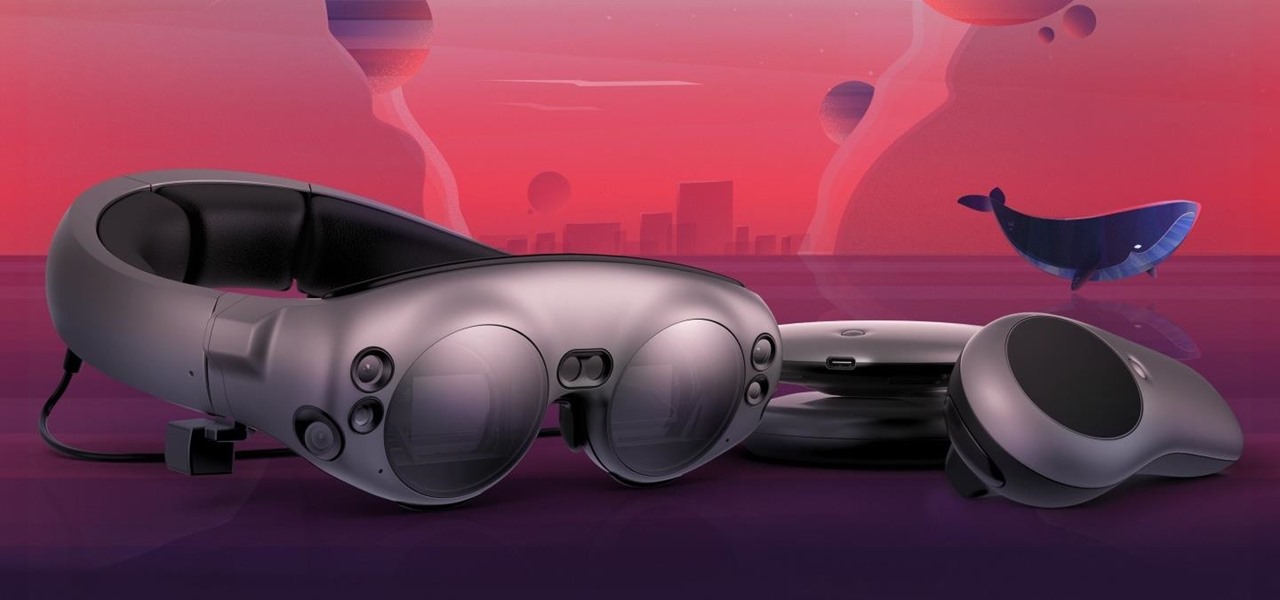
If you subscribe to notifications for Magic Leap CEO Rony Abovitz's Twitter feed, you'd think everyone in the world already has a Magic Leap One. Alas, that is not the case, but those not within the geographic areas of Magic Leap's LiftOff service now have a loophole through which they, too, can join the "Magicverse."

After gaining access to a root account, the next order of business is using that power to do something more significant. If the user passwords on the system can be obtained and cracked, an attacker can use them to pivot to other machines if the login is the same across systems. There are two tried-and-true password cracking tools that can accomplish this: John the Ripper and Hashcat.

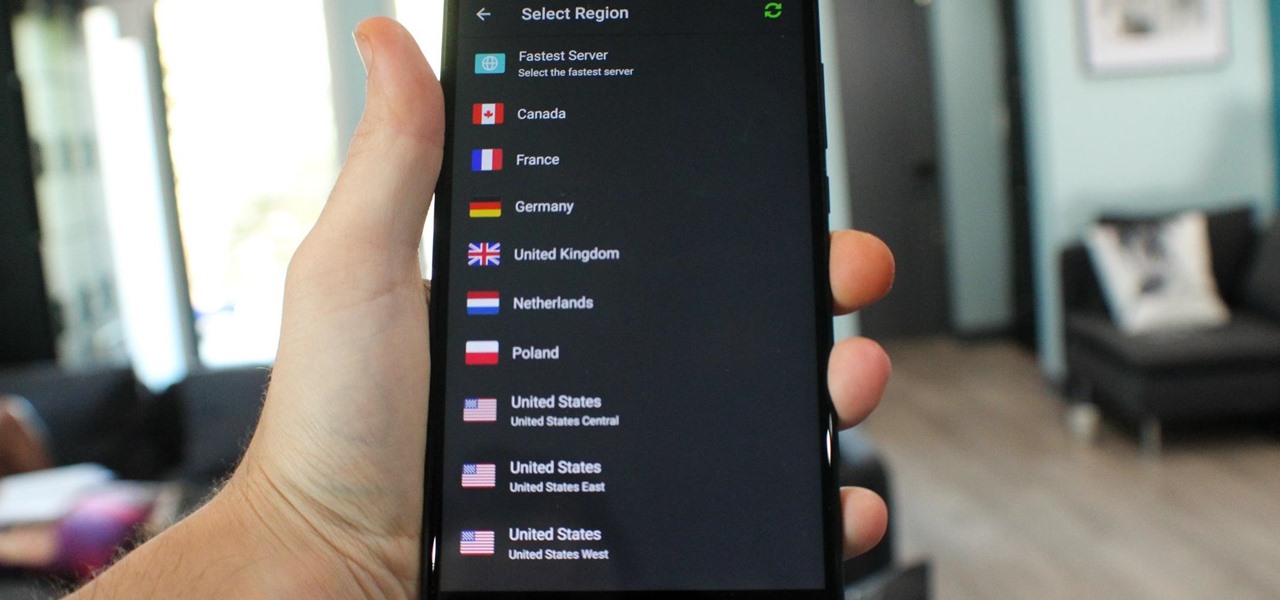
What you see when you open the Play Store is completely dependent on your country settings. Search results and top charts are specific to each region and there are lots of popular apps and games that simply won't show up unless your Play Store country matches up.

The long, long, loooong wait finally ended this week for the augmented reality community as the Magic Leap One was finally released. The Florida-based company has loomed over the industry for years promising something big, and now the AR cat is finally out of the bag. Now we get to see if it will live up to expectations, but early reviews are a bit skeptical.